
Identify Application Users with DataSunrise
DataSunrise provides tools for data masking, database security, and activity monitoring. Our approach is to ceaselessly follow the needs of our current and potential customers to make a product that meets the requirements of modern IT environment. That’s why DataSunrise Database Security Suite includes the application user identification functionality.
It is a common practice in present-day environments that an application uses connection pools to communicate with a database. In other words, instead of creating a new connection each time an application user logs in, application server uses one of the reusable connections from the pool. So, the application uses only one database user to connect to the database. Connection pooling helps to significantly increase the application performance but it has some disadvantages when it comes to auditing of database transactions or restricting access to certain end-users.

As the application uses a single database user for all application user transactions, it is difficult to identify the end user who executed a certain statement. However, strict regulations in some environments demand to manage access to sensitive data for some application users. It is also necessary for companies complying severe audit requirements of HIPAA and SOX.
If you have the same problem, DataSunrise gives you the solution. DataSunrise Database Security Suite uses algorithms to identify mapped application users so that you always know who exactly queried your database. You can also configure security rules to block certain queries from unwanted end-users.
How DataSunrise Identifies End-Users
When a user communicates with a database through an application using connection pools, the application must keep track of who initiated the query so that it can return the query response to exactly the same user. The challenge of DataSunrise is to catch the “traces” of the end-user among various types of data sent by the application.
The traces of an application user can be found in various types of data extracted from the application. DataSunrise is able to use simultaneously several techniques listed below:
- Query-based detection. Extracting application user names from SQL statements. When a client enters his credentials, the application sends an SQL request to the web-server in order to check whether there is such a user. DataSunrise catches that query and identifies the end-user.
- ResultSet-based detection. Extracting application user names from the result of an SQL query execution.
- Bindings-based detection. Identifying applications users according to the specified regular expression pattern for SQL query bindings.
- Detection by session parameters. Identifying application users according to the specified regular expression pattern for parameters of the session.
- SAP ECC (for SAP HANA, SAP Sybase, Oracle, IBM Db2). Detection of end users by the set of built-in patterns for parameters of the session.
- Oracle EBS. Built-in detection of end users.
- Bizagi Cloud Platform. Built-in detection of end users.
Let’s review the basic principle on the example of a query-based detection. Let’s assume that a client wants to log into his online bank account. When the client enters credentials, the web application sends a SELECT query to the web server to check whether there is a user account that matches specified credentials.
To configure DataSunrise to capture that kind of queries, you need to set the regular expression pattern for required SQL queries in the settings of the database instance (Configurations – Databases – Actions – Application User Settings in the DataSunrise Web Console).
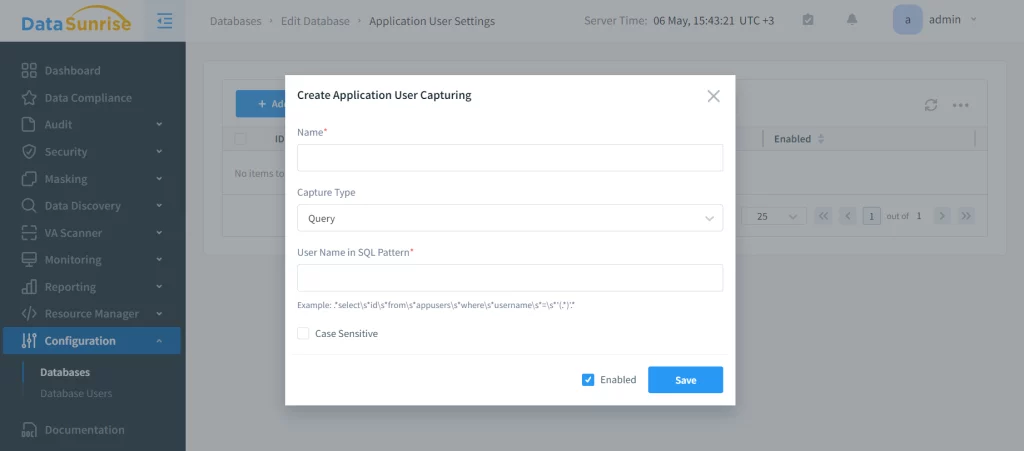
As soon as the user enters his credentials, the application will send the SELECT query containing the application user login to the web server. DataSunrise will catch that query, identify the end-user login, and bind it with consecutive queries until the specified pattern is matched again with another application user login.
With this functionality, DataSunrise provides a solution to the problem of identifying application end users associated with database activity in cases when the application uses connection pools.
For detailed instructions on how to configure application user identification, refer to Capturing of Application Users section of the DataSunrise Database Security User Guide.
