
Dynamic Data Masking
Introduction
Dynamic data masking protects sensitive information in real time by concealing specific fields during query execution according to user roles, session parameters, or application policies. This technique secures regulated data—like credit card details, email addresses, and other personal identifiers—without altering the original records or interrupting regular operations. Authorized users can view complete values, while others see masked or partially obscured data. By reducing data exposure, dynamic masking strengthens compliance and bolsters overall database security.
Organizations subject to GDPR, HIPAA, or PCI DSS are increasingly adopting this approach to strengthen zero-trust access strategies. Industry studies, such as the NIST Privacy Framework, emphasize the importance of minimizing data exposure through real-time protection methods. This article compares dynamic and static masking, highlights native capabilities of leading databases, and explains how DataSunrise enables dynamic masking without requiring schema alterations or application code changes.
Static vs Dynamic Data Masking
What is Dynamic Data Masking?
Dynamic data masking is a real-time technique for hiding sensitive data during query execution. Unlike static methods, it protects live production data by returning masked results to unauthorized users—without modifying the source database.
| Feature | Static Data Masking | Dynamic Data Masking |
|---|---|---|
| How it Works | Generates a masked copy of the database for non-production use | Masks query results in real time based on user or context |
| Original Data | Replaced permanently in the masked dataset | Remains unchanged in the source system |
| Primary Use Cases | Testing, development, vendor handoff | Live production environments, compliance, zero-trust |
| Flexibility | Hard to modify once applied | Policy-driven and easy to update |
| Compliance Fit | Good for data minimization | Excellent for access control and audit logging |
Why Dynamic Masking Outperforms Static in Live Environments
While static masking is effective for non-production scenarios such as development or testing, it becomes inefficient and brittle in live, multi-user environments. Each policy modification requires regenerating, revalidating, and redeploying masked datasets—an error-prone and time-intensive process that can introduce inconsistencies and downtime. In contrast, dynamic masking applies data protection rules on the fly, automatically adapting to user roles, query contexts, and access levels. For example, a developer may see partial or pseudonymized data, while a customer support agent only views fully redacted fields—all from the same live database, without the need for duplicate datasets or synchronization overhead.
By enforcing policies in real time, dynamic masking not only streamlines compliance but also minimizes the risk of data leakage through human error or outdated copies. When integrated with detailed activity logging, contextual filters, and audit-ready reporting, it provides organizations with both flexibility and traceability. This makes it the optimal approach for production systems handling regulated or confidential data—where access varies across departments and compliance requirements demand continuous, adaptive protection.
Built-in Support in Popular Databases
Several platforms provide native or plugin-based support for masking. For example:
- PostgreSQL: View-based masking or extensions like pg_maskdata
- Oracle: Data Redaction for role-based masking
- SQL Server: Built-in dynamic masking for certain fields
Here’s an example of PostgreSQL simulating masking with a view:
CREATE OR REPLACE VIEW masked_users AS
SELECT
id,
name,
CASE
WHEN current_user = 'auditor' THEN 'XXXX-XXXX-XXXX-' || RIGHT(card_number, 4)
ELSE card_number
END AS card_number,
email
FROM users;
While effective in simple setups, this approach becomes difficult to scale across multiple databases or dynamic roles. That’s exactly where DataSunrise simplifies implementation—masking results across environments without altering SQL or schemas.
Dynamic Masking with DataSunrise
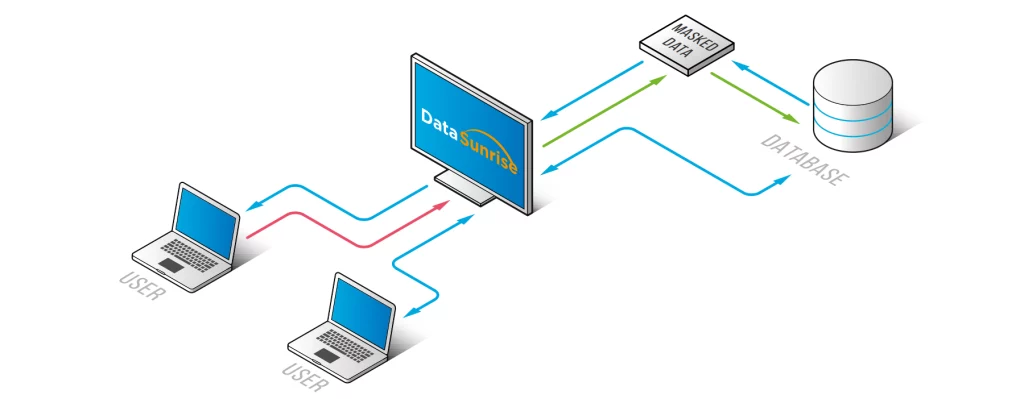
DataSunrise operates as a transparent proxy between your applications and databases. Consequently, it intercepts queries and applies masking rules before data reaches the user. It supports:
The configuration process is handled entirely through a user-friendly interface. More importantly, no code rewrites or schema changes are required.
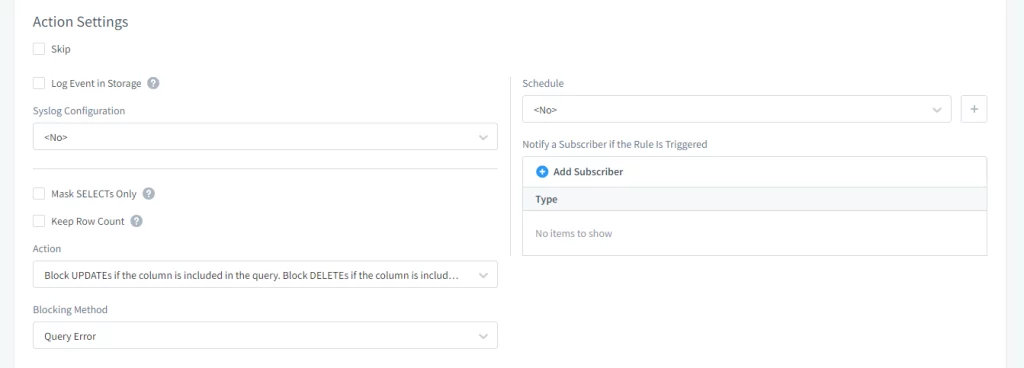
1. Action Settings
Admins can control whether masking events are logged, alerts are triggered, or update operations are blocked on masked fields.
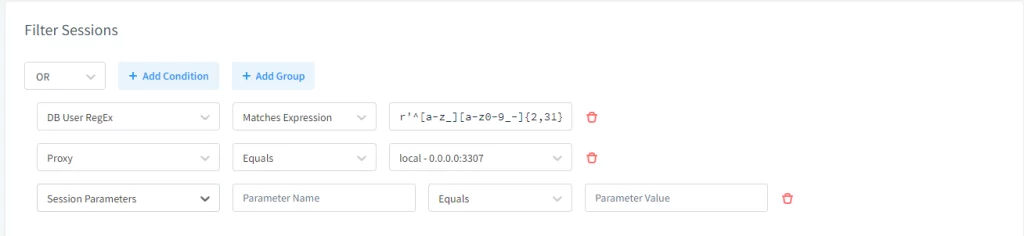
2. Filter Settings
This section defines when and where masking should apply—based on user identity, IP range, source application, or even network routes. Therefore, it enables context-aware enforcement.
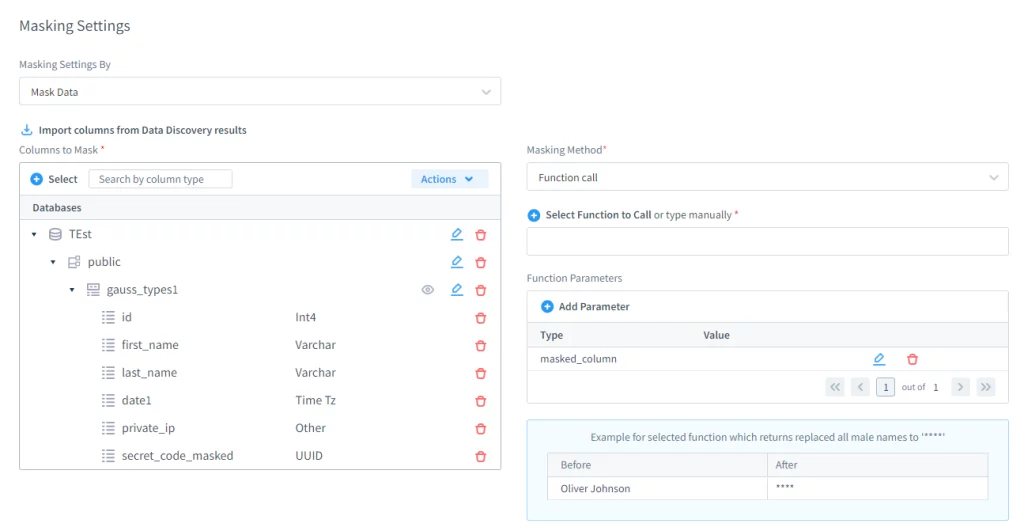
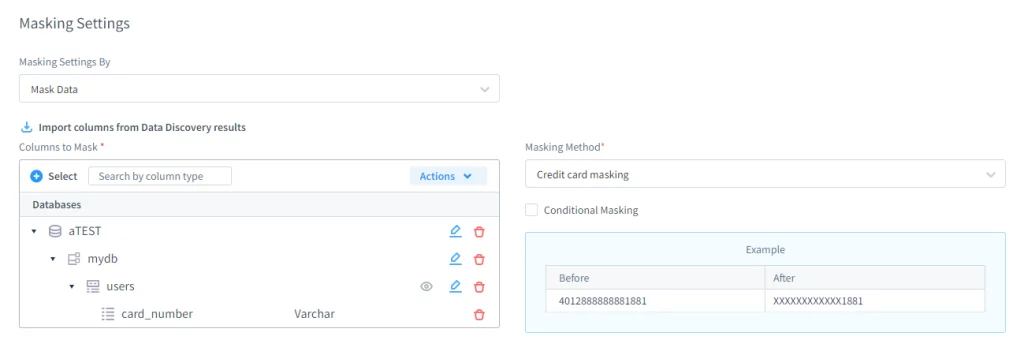
3. Masking Settings
Admins can select specific schemas, tables, and fields to protect. Additionally, they can define masking methods using built-in logic or custom Lua scripts.
4. Masking Logs
When logging is enabled, each masking event is recorded. As a result, organizations gain audit-ready insight into how and when masking was applied.
Common Challenges in Dynamic Masking Deployment
Dynamic data masking is highly effective, but only when configured accurately. Without careful planning, it can create new security and usability issues. Some typical pitfalls include:
- Excessive masking: Restricting access so heavily that legitimate users, analysts, or support teams cannot perform their work because critical contextual data is hidden.
- Poorly scoped rules: Implementing masking policies that are too broad or not role-aware, resulting in inconsistent or inappropriate data exposure across applications and users.
- Coverage gaps: Applying masking only at the database interface while overlooking other access vectors, such as BI dashboards, API responses, backups, or data exports.
DataSunrise addresses these challenges through fine-grained policy control, adaptive masking logic, and comprehensive audit visibility. Administrators can preview and validate masking rules in real time, ensuring the correct balance between security and usability. Additionally, integrated monitoring helps continuously verify that masking is enforced across all access paths, preventing accidental data leakage as systems or user roles evolve.
PostgreSQL Use Case with DataSunrise
A typical use case might involve a users table containing credit card data. With DataSunrise configured, the card number is masked based on user permissions:
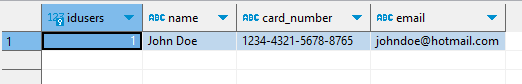
Admins define this behavior through the GUI instead of modifying the schema:
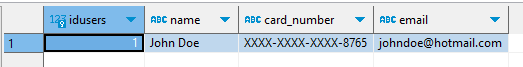
Consequently, users without elevated access see only masked values:
The event is also recorded in the audit logs automatically:
Benefits of Using DataSunrise for Masking
- Protects PII, credentials, and financial data at query time
- Supports cross-platform deployments without rewriting code
- Applies granular policies using roles, filters, and logic
- Provides audit trails for transparency and compliance
Practical Approaches to Dynamic Masking
| Approach | How It Works | Example Scenario |
|---|---|---|
| Role-Based | Mask or reveal fields based on user permissions | Support staff see partial card numbers, while fraud analysts see full values |
| Context-Aware | Adjust masking depending on location, device, or session type | Trusted corporate networks reveal more data than remote logins |
| Time-Limited | Grant temporary access with automatic expiry | Approved users view salary data for a set period, then masking reactivates |
Dynamic masking adapts protection to fit real business contexts instead of applying a single blanket rule.
Quick FAQ: Dynamic Masking
Does masking affect query performance?
Typically minimal when rules are scoped. DataSunrise applies policies at the proxy layer to avoid heavy database rewrites.
Can masking be bypassed via exports or BI tools?
Only if those paths aren’t in scope. Include APIs, exports, and analytics connectors in your masking rules to close gaps.
How do I choose fields to mask?
Start with data discovery to classify PII/PHI/PCI fields, then apply policies by sensitivity and role.
How do I prove compliance?
Use audit logs from masking events plus activity monitoring to show who saw what, when, and under which policy.
Can masking be applied dynamically based on user behavior?
Yes. Adaptive masking rules can tighten or relax visibility depending on risk signals such as unusual query volume, off-hours access, or privilege escalation attempts.
Does masking work with cloud-native databases and distributed systems?
Absolutely. DataSunrise supports dynamic masking across multi-cloud and hybrid environments, including managed services like Amazon RDS, Azure SQL, Google Cloud SQL, and distributed platforms such as Snowflake and BigQuery.
Conclusion
Dynamic Data Masking (DDM) represents a key element of adaptive data security, enforcing the principle of least privilege by hiding sensitive information in real time—without duplicating, altering, or restructuring the original data. Rather than modifying data at rest, DDM dynamically adjusts query outputs based on user identity, role, purpose of access, and contextual risk. This approach ensures that employees, partners, and external applications only see the data they are authorized to view, maintaining full system usability while greatly reducing the risk of accidental or intentional data exposure.
When combined with automated discovery, data classification, and continuous activity monitoring, dynamic masking evolves from a technical control into a holistic data governance framework. Modern implementations allow organizations to enforce consistent protection policies across heterogeneous ecosystems—including on-premises databases, virtualized systems, multi-cloud infrastructures, and SaaS applications. Unified policy management, complemented by detailed auditing and contextual access analytics, provides comprehensive insight into data movement and user behavior.
With solutions such as DataSunrise, Dynamic Data Masking becomes an integral part of a cohesive defense strategy that incorporates real-time anomaly detection, automated compliance validation, and intelligent risk assessment. Extensive audit trails ensure full accountability and transparency for every access attempt. By adopting dynamic masking as a proactive, adaptive control, organizations can not only comply with evolving regulations like GDPR, HIPAA, SOX, and PCI DSS, but also strengthen their overall security resilience—protecting sensitive business data while maintaining operational efficiency and innovation.
Protect Your Data with DataSunrise
Secure your data across every layer with DataSunrise. Detect threats in real time with Activity Monitoring, Data Masking, and Database Firewall. Enforce Data Compliance, discover sensitive data, and protect workloads across 50+ supported cloud, on-prem, and AI system data source integrations.
Start protecting your critical data today
Request a Demo Download Now