
Best Practices for Managing Access Logs and Enhancing Security

Introduction
Access logs are an important tool for monitoring and securing your databases and applications. They provide a detailed record of who accessed your systems, when, from where, and what actions they took. This data is invaluable for troubleshooting issues, identifying suspicious activity, and meeting compliance requirements.
Important factors to think about when using access logs with different data sources include. We’ll also look at some examples of access logs in action.
What’s Inside an Access Logs?
A typical access log entry contains several key pieces of information:
- Timestamp – when the access occurred
- User – who accessed the system (username, user ID, etc.)
- Source – where the access originated from (IP address, hostname, etc.)
- Action – what the user did (query executed, record accessed, login/logout, etc.)
- Status – whether the action was successful or not
- Additional details – query text, affected tables/records, access method, etc.
The exact contents may vary depending on the configuration of the access logging. Here’s a simple example of what a web server access log entry might look like:
127.0.0.1 - jane [21/Apr/2023:13:05:11 -0700] "GET /index.html HTTP/1.1" 200 2326
This shows a successful request for the index.html page by the user “jane” from the IP address 127.0.0.1.
Database access logs usually contain more detailed information. Here’s an example from a PostgreSQL log:
2023-04-21 13:28:17.159 PDT [2347] jane@mydb LOG: statement: SELECT * FROM users;
In this case, we can see the user “jane” executed a SELECT query on the “users” table in the “mydb” database.
Why Are Access Logs Important?
Access logs serve several important purposes:
- Security monitoring – Logs can help identify suspicious activity like failed login attempts, unauthorized access, or unusual query patterns. This is crucial for preventing breaches and minimizing damage.
- Troubleshooting – When issues arise, access logs are often the first place to look. They can help pinpoint the source of errors, performance problems, or unexpected behavior.
- Auditing & compliance – Many regulations require detailed logging of database activity. Access logs provide an audit trail to help meet these requirements.
- Analyzing usage – Access data can offer valuable insights into how users are utilizing your systems and data. This can inform capacity planning, feature development, and more.
Working with Multiple Data Stores
Modern applications often rely on multiple databases and data stores, each with their own logging mechanisms. This can create challenges when trying to consolidate and analyze access data.
Some key considerations:
- Centralized logging – Forward logs from all data stores to a central location. This could be a dedicated log management system or a cloud storage bucket.
- Consistent format – Ensure log entries from different sources use a consistent format. This may require pre-processing or transformation.
- Time synchronization – Make sure timestamps are consistent across all systems. This is critical for correlating events and identifying patterns.
- Retention & archiving – Determine how long to keep access logs and establish an archiving strategy for compliance and analytics purposes.
Various tools and platforms can help streamline collecting and analyzing multi-source access logs. We’ll explore some examples in the next sections.
Access Logs Architecture
To better understand how access logs can be managed and utilized in a multi-source environment, let’s take a look at a possible example of an access logs architecture:
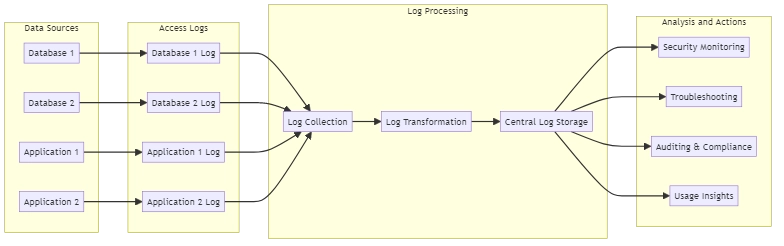
Data Sources: Various databases and applications generate access logs.
Access Logs: Each data source produces its own access log, capturing user activities, queries, and other relevant information.
Log Processing:
- Log Collection: Access logs from different sources are collected and centralized.
- Log Transformation: Logs are processed to ensure a consistent format and structure.
- Central Log Storage: Transformed logs are stored in a central location for further analysis.
Analysis and Actions:
- Security Monitoring: Logs are analyzed to identify suspicious activities and potential security threats.
- Troubleshooting: Logs are used to investigate and resolve issues or errors in the system.
- Auditing & Compliance: Logs are maintained to meet regulatory requirements and support audits.
- Usage Insights: Logs are analyzed to gain insights into user behavior, system usage, and performance.
Access Logs in Action
Let’s examine a few examples of how we can use access logs with different databases and applications.
Example 1: Monitoring Failed Logins in MySQL
Suppose you want to monitor failed login attempts on your MySQL database server. First, ensure that you have enabled the appropriate logging in the MySQL configuration file.
[mysqld] log-error=/var/log/mysql/error.log log-warnings=2
This will log all connection errors to the specified file. The log-warnings setting captures failed logins.
Now, you can periodically scan the log for failed attempts. For example, to see a summary of failed logins in the past hour:
bash
grep "Access denied" /var/log/mysql/error.log | grep -oP '\d{6} \d{2}:\d{2}:\d{2}' | uniq -cThis uses grep to find “Access denied” messages, extracts the timestamp, and provides a count of unique timestamps. The result might look something like:
14 230421 13:00:07
27 230421 13:15:23
9 230421 13:45:42This indicates there were three clusters of failed login attempts in the past hour. You could then investigate further to determine the source and take appropriate action.
Example 2: Analyzing Query Patterns in PostgreSQL
Access logs can also provide valuable information about query patterns and database usage. In this example, we’ll look at identifying the most frequent queries in a PostgreSQL database.
First, enable query logging by setting the log_statement parameter in postgresql.conf:
log_statement = 'all'
This will log all queries to the standard PostgreSQL log file. Using this can slow down performance and occupy storage space, so we advise against using it for production purposes.
Next, you can use a tool like pgbadger to analyze the log and generate a report. For example:
bash
pgbadger /var/log/postgresql/postgresql-11-main.log
This will create an HTML report with various statistics and insights. One section will show the most frequent queries, which might look something like:
Rank | Query | Calls
------|-----------------------------------------------------------------------------|-------
1 | SELECT id, name FROM users WHERE email = ? | 3492
2 | UPDATE products SET price = price * 1.1 WHERE category_id = ? | 2841
3 | SELECT * FROM orders WHERE user_id = ? AND status = ? ORDER BY created_at | 2239This can help find queries that need improvement, understand usage patterns, and make database design better.
Access Logging Best Practices
Here are a few best practices to keep in mind when working with access logs:
- Enable logging judiciously: Capture enough detail to be useful, but not so much that it impacts performance or becomes unmanageable.
- Secure log data: Access logs can contain sensitive information. Make sure authorized personnel securely store and access them.
- Automate log analyzing: With large volumes of log data, manually analyzing is impractical. Use tools and scripts to parse, filter, and analyze logs.
- Act on insights: The value of logs comes from the actions you take based on the information they provide. Have processes in place to respond to issues and opportunities surfaced by log data.
Summary and Conclusion
Access logs are a vital tool for managing and securing databases and applications. They offer detailed records of system access and usage for security monitoring, troubleshooting, auditing, and other purposes.
Managing access logs from various data stores can be difficult. However, using tools and following best practices can help simplify the process of organizing and analyzing the data. By properly leveraging access logs, you can gain valuable insights into your systems and data.
Looking for a comprehensive solution for managing logs and database security? Visit our website for an online demo to see how DataSunrise can help you secure and optimize your databases.
