
Advanced Persistent Threats: How to Detect and Defend Against Them
An advanced persistent threat (APT) is a type of cyberattack where intruders gain unauthorized access to a system or network and remain undetected for an extended period. Unlike typical cyber attacks which are short-lived, APTs are sophisticated, stealthy, and continuous, with attackers persistently pursuing their objectives. The goal is usually to monitor activity and steal sensitive data rather than cause direct damage to the network.
You can find the Mandiant Report for 2023 interesting as it describes so-called “dwell-time” for investigated cyberattacks. As you can see on the ‘Global Dwell Time Distribution’ plot, the more dwell-time the lower the amount of investigations. Most of the typical attacks are not APT.
APTs often target organizations with high-value information, such as national defense, manufacturing, financial industries and critical infrastructure. Perpetrators may be nation-states or state-sponsored groups with significant resources and skill to carry out such an attack.
The Stages of an APT Attack
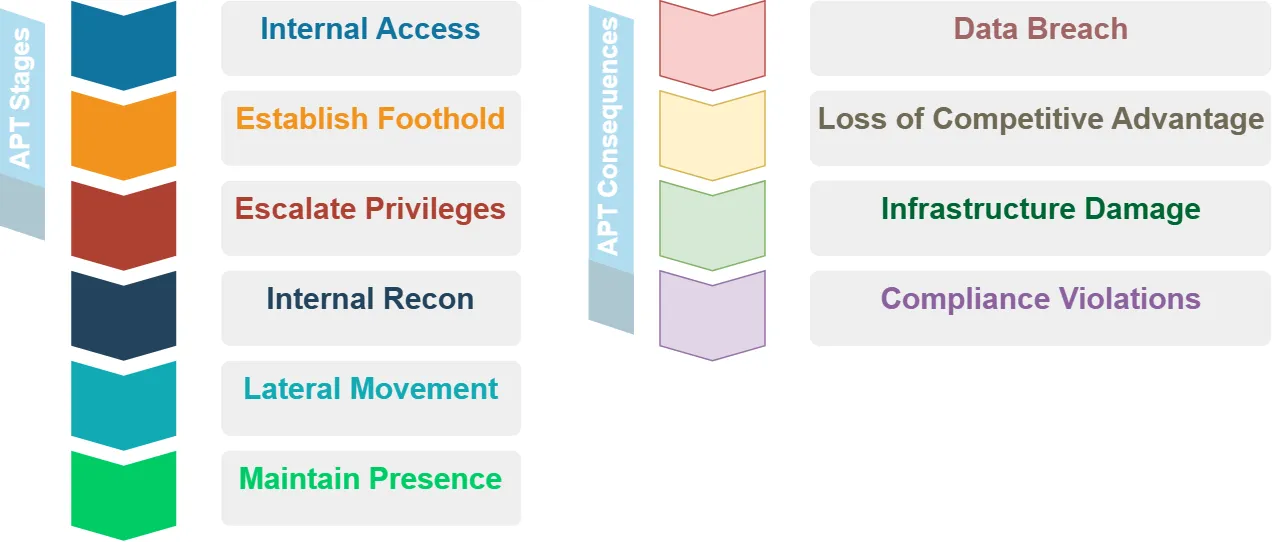
APT attacks typically follow this sequence of stages:
- Initial Access: The attacker gains an entry point into the network, often through targeted malware, zero-day vulnerability exploit, or stolen user credentials via phishing.
- Establish Foothold: Upon gaining access, the attacker establishes a foothold in the environment to maintain persistence. They may install a backdoor or use legitimate credentials to create a reliable access point.
- Escalate Privileges: The attacker then attempts to escalate privileges to gain higher-level permissions. Techniques can include password cracking, exploiting system vulnerabilities, or pivoting to more sensitive systems.
- Internal Recon: The attacker explores the victim’s environment, enumerating users, identifying key servers, and locating valuable data. The goal is to map the internal network and understand the organization.
- Lateral Movement: Using information gathered, the attacker moves laterally to other systems within the network, searching for higher-value targets. Techniques include exploiting software vulnerabilities, using stolen credentials, or deploying more malware.
- Maintain Presence: The attacker ensures continued control over the environment, even if their initial access point is discovered and closed. They use redundant access points, create fake user accounts, and deploy rootkits to hide their activity.
- Complete Mission: The attacker carries out their intended objective, such as data exfiltration, destruction, or manipulation. They may slowly siphon data to avoid detection.
Consequences of an APT Attack
The consequences of a successful advanced persistent threat attack can be severe:
- Data Breach: Sensitive data like customer PII, financial records, intellectual property, and national security information can be stolen. This can lead to identity theft, reputation damage, financial losses, and regulatory fines.
- Loss of Competitive Advantage: Stolen trade secrets and business plans can undermine an organization’s competitive edge and market position.
- Infrastructure Damage: In some cases, attackers seek to manipulate industrial control systems to disrupt or destroy critical infrastructure.
- Compliance Violations: Loss of sensitive data can put organizations out of compliance with regulations like HIPAA, PCI-DSS, and GDPR, resulting in penalties.
Minimizing the Risk of APT Attacks
Organizations can take these measures to minimize the risk of APT attacks:
- Least Privilege Principle: Implement least privilege access, ensuring users have only the permissions essential to their work. This limits the damage an attacker can do with any single compromised account.
- Network Segmentation: Divide the network into smaller, isolated segments or subnets. This contains the impact of a breach and makes lateral movement more difficult.
- Firewalls and Network Monitoring: Deploy firewalls to filter malicious traffic and use intrusion detection/prevention systems to monitor network activity for anomalies. A database firewall is especially important to protect sensitive data.
- Sensitive Data Management: Identify, classify and encrypt sensitive data both at rest and in transit. Use data discovery tools to locate sensitive data across the environment. Minimize the amount of sensitive data stored.
- Patch Management: Keep all systems and software updated with the latest security patches to reduce exploit risk. Remove end-of-life systems that no longer receive updates.
- Employee Training: Train employees on cybersecurity best practices, especially how to identify phishing attempts. Conduct periodic training and simulated phishing tests.
Signs of an APT Attack
Detecting an APT can be challenging given their stealthy nature. However, there are some signs to watch for:
- Large Data Exfiltration: APTs often involve the transfer of large amounts of data outside the network. Monitor for large file transfers, especially to unknown destinations.
- Increased Database Read Volume: Sudden spikes in volume of database reads can indicate an attacker is accessing and preparing to exfiltrate sensitive data.
- Malware Detection: While APTs use techniques to evade detection, sometimes their malware may trigger alerts from endpoint detection and antivirus systems. Investigate any such alerts promptly.
- Unusual Login Activity: Look for logins from unusual locations or IP addresses, at odd hours, or from disabled user accounts. Use of compromised credentials is common in APTs.
- Phishing Emails: Examine email headers, sender addresses, and links in suspected phishing emails. Phishing is a common initial access vector in APTs.
Conclusion
Advanced Persistent Threat attacks pose a significant risk to organizations due to their sophisticated, long-term, and stealthy nature. By understanding the stages of an APT attack, implementing security best practices, and monitoring for signs of compromise, organizations can better protect against this threat. A defense-in-depth strategy with layered security controls is essential.
Effective database security is key to protecting against data breaches from APTs. DataSunrise provides user-friendly and flexible tools for database security, sensitive data discovery (including OCR), database activity monitoring, and compliance. Contact our team for an online demo to learn more.
