
Amazon Aurora MySQL Audit Trail
Protecting sensitive information is crucial in a data-driven world. Auditing ensures compliance, uncovers unauthorized access, and tracks database activities. Amazon Aurora MySQL, a managed relational database service, includes native audit trail capabilities for improved security and traceability. This article explains how to configure and use these features, along with tools like DataSunrise for advanced management.
Native Audit Trail in Amazon Aurora MySQL
Overview
The native Amazon Aurora MySQL audit trail enables organizations to monitor database activities directly within the database system. Leveraging advanced auditing features, administrators can capture crucial events like user logins, data modifications, and query executions, helping answer questions about who accessed or modified data, when changes occurred, and whether actions complied with organizational policies.
Setting Up the Audit Trail
To enable auditing in Amazon Aurora MySQL, follow these steps:
Step 1: Create a Custom Parameter Group
Begin by accessing the Amazon RDS console and navigating to the parameter groups section. Create a new parameter group by selecting the family type, such as aurora-mysql5.7, and providing a suitable name and description. After saving your changes, the parameter group will be ready for association with a database instance.
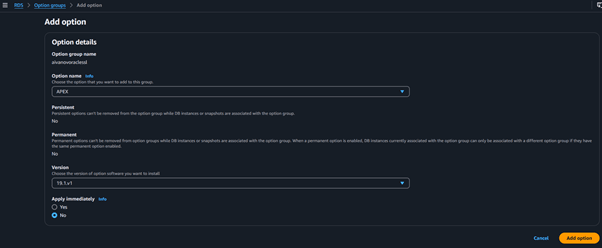
Step 2: Associate the Parameter Group
Head to the databases section in the RDS console to find your Aurora instance. Modify its settings to include the new parameter group under the additional configuration section. Applying changes immediately ensures that the configuration takes effect, though this may require a database restart.
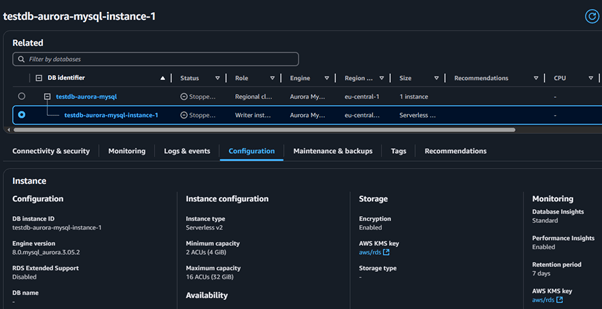
Step 3: Configure Audit Events
Next, edit the newly created parameter group to specify which audit events to track. Adjust the server_audit_events parameter to log events such as connections, queries, and table accesses. These modifications define what database activities will be recorded.
Step 4: Verify Configuration
Finally, confirm the auditing setup by connecting to the database using a MySQL client. Execute the SHOW VARIABLES LIKE ‘%server_audit%’; command to ensure the server_audit_logging setting is active and the desired events are listed.
Example Usage
Here’s a practical example of auditing DML queries:
CREATE DATABASE audit_log;
USE audit_log;
CREATE TABLE user_activity (id INT AUTO_INCREMENT PRIMARY KEY, action VARCHAR(255), timestamp DATETIME DEFAULT CURRENT_TIMESTAMP);
INSERT INTO user_activity (action) VALUES ('User Login');
UPDATE user_activity SET action = 'Data Modified' WHERE id=1;
DELETE FROM user_activity WHERE id=1;Audit logs for these activities can be accessed through the Logs section in the RDS console under audit/audit.log.
Enhancing Auditing with DataSunrise
While the native audit trail in Amazon Aurora MySQL is powerful, integrating tools like DataSunrise enhances audit management by providing centralized and advanced database security features such as fine-grained auditing, user activity monitoring, and compliance reporting.
Configuring DataSunrise for Amazon Aurora MySQL
Step 1: Create a DataSunrise Instance
To get started, deploy a DataSunrise instance on a suitable server or cloud platform. Access its web interface at http://<DataSunrise-IP>:11000 and complete the initial configuration using the setup wizard. This step establishes the foundation for further configurations.
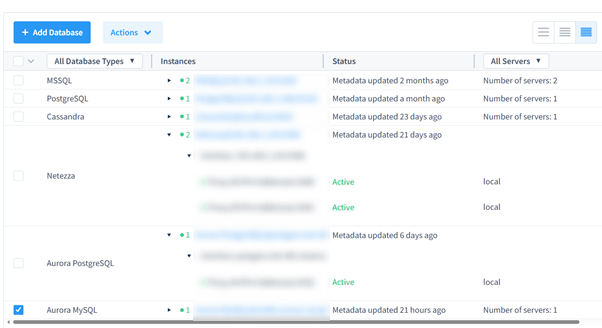
Step 2: Add the Amazon Aurora MySQL Database
Within the DataSunrise dashboard, locate the databases section and initiate the process to add a new database. Enter the Aurora endpoint details, including the port, database name, and credentials. Configure auditing options like activity logging and event monitoring to tailor the system’s functionality to your needs.
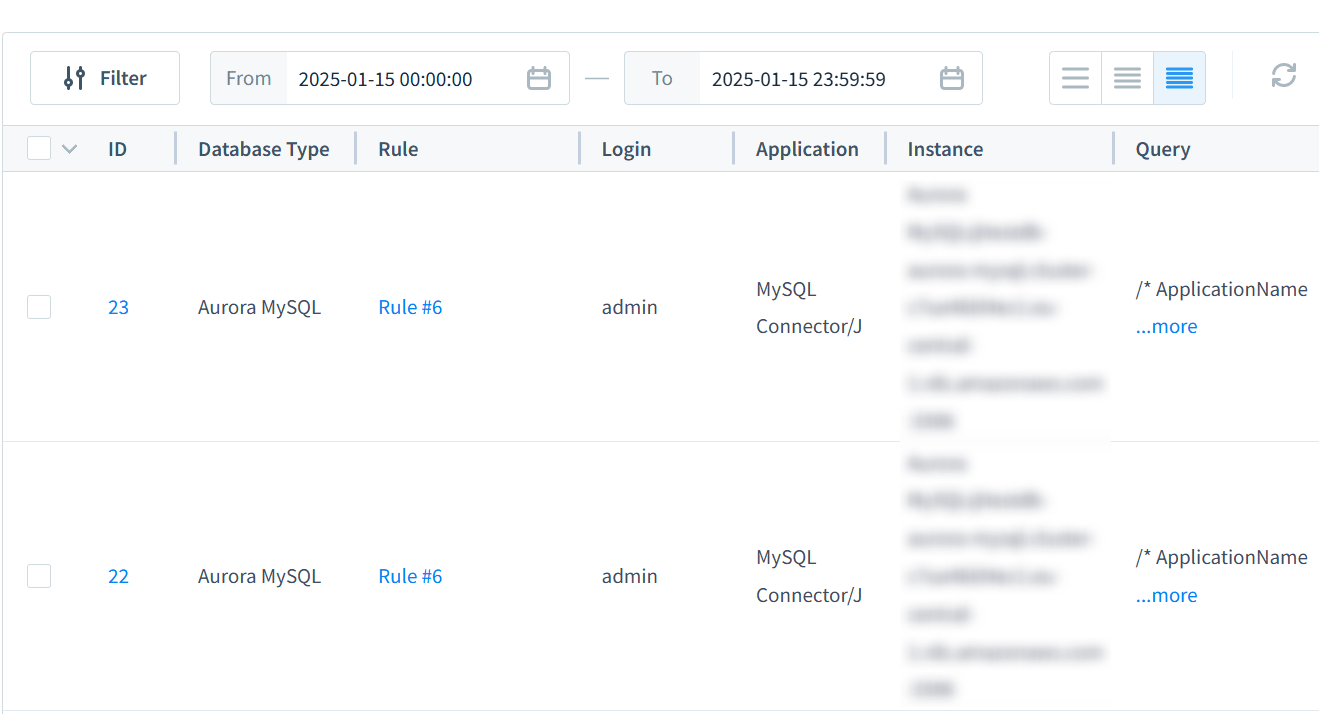
Step 3: View Audit Logs
Access the audit logs section in DataSunrise to analyze database activities. Utilize filtering options based on criteria such as database name, user, or event type to obtain detailed insights into system operations.
Benefits of DataSunrise
DataSunrise acts as a robust centralized management system, streamlining the consolidation of auditing rules and logs from various databases. It strengthens compliance efforts by adhering to key standards like GDPR,SOX,PCI DSS and HIPAA. Additionally, the platform elevates database security by offering real-time monitoring to detect and restrict unauthorized access attempts.
Conclusion
Amazon Aurora MySQL’s native audit trail offers a robust solution for monitoring and securing sensitive data. By configuring advanced auditing features, organizations can track database activities effectively. Integrating tools like DataSunrise further elevates auditing capabilities with centralized control, granular monitoring, and compliance support.
For more information on DataSunrise’s comprehensive security suite, visit our website for an online demonstration.
