
Tracking and Securing Amazon Aurora MySQL Data Activity History
Understanding data activity history is critical for maintaining the security and integrity of sensitive data. Amazon Aurora MySQL provides robust auditing features to capture database activities. This article delves into the native auditing capabilities of Amazon Aurora MySQL, demonstrates how to configure and use these features, and highlights the complementary advantages of DataSunrise for centralized database security.
Native Amazon Aurora MySQL Data Activity History
Key Features
Amazon Aurora MySQL’s native audit logging tracks database activity comprehensively. It includes detailed event logging for connections, queries, and table modifications. Customizable parameters allow users to selectively audit specific events or users. Integration with AWS tools facilitates the export of logs to Amazon CloudWatch for analysis. These features provide essential insights into who accessed or modified data, when changes occurred, and what queries were executed.
Configuring Native Audit Logs
To enable advanced auditing, follow these steps:
1. Create a Custom DB Cluster Parameter Group
Navigate to the Amazon RDS console, choose “Parameter groups,” and create a new parameter group. Set the parameter group family to aurora-mysql5.7 or the relevant version. Provide a name and description for the group and save it.
2. Associate the Parameter Group
In the “Databases” section of the RDS console, select your Aurora instance and modify its configuration. Under “Additional configuration,” assign the custom parameter group created earlier and apply changes immediately.
3. Configure Audit Parameters
Access the “Parameter groups” section, select your custom group, and modify specific parameters. Turn on server_audit_logging and specify events like QUERY_DML, QUERY_DDL, CONNECT for server_audit_events. Save the changes and restart the database to activate the settings.
4. Verify Configuration
Execute SHOW VARIABLES LIKE ‘%server_audit%’; in your MySQL client to confirm that audit logging is active and the selected events are being tracked.
Example: Tracking DML Activities
After enabling audit logs, perform typical database operations such as creating a database and table, inserting, updating, and deleting records. For example:
CREATE DATABASE audit_test; USE audit_test; CREATE TABLE employees (id INT, name VARCHAR(100)); INSERT INTO employees (id, name) VALUES (1, 'John Doe'); UPDATE employees SET name = 'Jane Doe' WHERE id=1; DELETE FROM employees WHERE id=1;
Access the “Logs” section of your Aurora instance in the RDS console to review the corresponding audit log files for these activities.
Benefits of Native Audit Logging
Native audit logging enhances compliance by meeting regulatory requirements for monitoring data access, strengthens security by identifying unauthorized access or unusual activity, and establishes an audit trail for user accountability.
Enhancing Auditing with DataSunrise
Overview of DataSunrise
DataSunrise enhances database security by offering a suite of advanced tools:
- Audit: Comprehensive activity logging to monitor database interactions in real time, providing actionable insights into user behavior and access patterns.
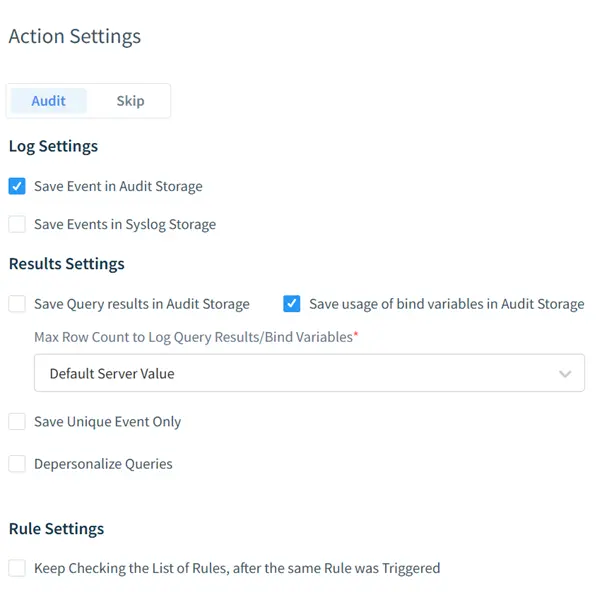
- Security: Real-time threat detection and automated responses to mitigate risks. It includes features like anomaly detection and fine-grained access controls.
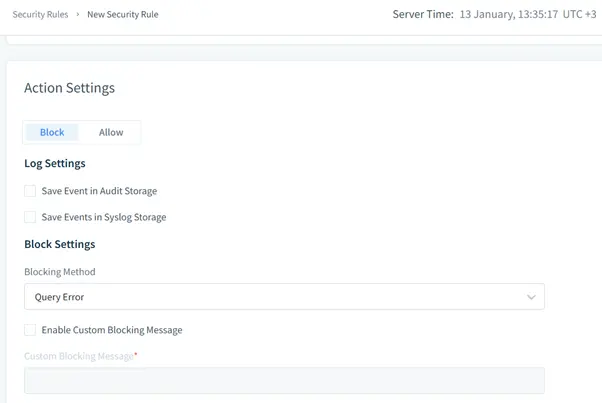
- Masking: Dynamic and static masking options to ensure sensitive data remains protected during operations, effectively preventing unauthorized access.
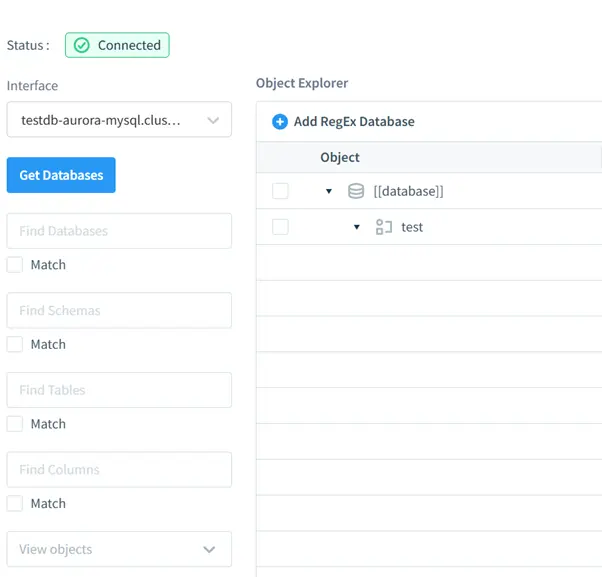
- Data Discovery: Advanced tools for identifying sensitive data within databases, ensuring organizations can maintain compliance and mitigate exposure risks. These discovery tools can identify fields like personally identifiable information (PII), financial details, and other regulated data.
Advanced Capabilities
DataSunrise extends the capabilities of native audit logging with centralized auditing, data masking to protect sensitive information, granular access control through security rules, and automatic discovery of sensitive data.
Setting Up DataSunrise for Aurora MySQL
Launch a DataSunrise instance on AWS or install it on your server. Configure network settings to connect to your Aurora database. Log in to the DataSunrise web interface, create new audit policies to log events like SELECT, INSERT, or DELETE, and access the “Audit Logs” section for detailed insights. Filter logs by event type, user, or time period to analyze data activity.
Benefits of DataSunrise Integration
DataSunrise simplifies scalability for managing multiple Aurora instances, reduces manual effort through automation with predefined rules and templates, and supports compliance reporting for standards like GDPR,SOX,PCI DSS and HIPAA. Additionally, its centralized management ensures consistent policy enforcement across different environments.
Conclusion
Amazon Aurora MySQL’s native data activity history features provide a robust foundation for tracking and auditing database activities. By configuring advanced audit logs, organizations can enhance security, ensure compliance, and maintain accountability.
DataSunrise complements this ecosystem with centralized auditing, data masking, and robust security controls, offering a comprehensive solution for database protection. Visit our website for an online demonstration.
