Apache Impala Audit Log
Introduction
Apache Impala provides high-performance SQL analytics on Hadoop data. As organizations use Impala for sensitive data processing, implementing robust audit log is essential for security and compliance.
With data breaches costing an average of $4.45 million in 2023 according to IBM's report, effective audit logging in Impala serves as a vital security control providing visibility into data access and potential security incidents.
Understanding Apache Impala Audit Log
Impala audit logs record user activities, SQL operations, and system events within the query engine. The native audit logging system includes:
- Audit Event Logger: Captures events directly from the Impala daemon
- Log Storage: Records events in files or forwards to centralized systems
- Events Captured: Authentication, query execution, metadata operations, data access, and privilege changes
Configuring Native Apache Impala Audit Log
Enable Audit Logging
Configure the Impala daemon according to the official documentation:
# Edit the Impala configuration file
sudo vi /etc/default/impala
# Add or modify parameters
--audit_event_log_dir=/var/log/impala/audit
--audit_log_level=full
The audit_log_level parameter supports three values as described in the configuration guide:
- minimal: Basic query details only
- basic: Standard execution information
- full: Comprehensive query data and context
Configure Log Format and Rotation
Set output formats and rotation policies as per the log management documentation:
# Set JSON format for easier analysis
--audit_log_format=json
# Configure rotation parameters
--max_audit_log_file_size=500MB
--max_audit_log_files=10
Example Audit Log Entry
A typical JSON-formatted log entry contains:
{
"timestamp": "2023-10-20T14:32:15.432Z",
"user": "analyst_user",
"database": "customer_data",
"query": "SELECT customer_id FROM transactions WHERE purchase_date > '2023-09-01'",
"status": "OK",
"duration_ms": 1250
}
Centralized Logging Integration
For enterprise environments, integrate Impala audit logs with centralized logging systems as recommended in the administration guide:
- Configure log forwarders (Flume, Logstash, Filebeat)
- Implement aggregation using ELK stack or similar tools
- Stream logs to Kafka for real-time processing
Analyzing Apache Impala Audit Log
Command-Line Analysis
For quick investigations:
# Find queries from a specific user
grep -r '"user":"data_scientist"' /var/log/impala/audit/
# Identify failed queries
grep -r '"status":"ERROR"' /var/log/impala/audit/
SQL-Based Analysis
As suggested in the Impala SQL reference, use Impala to analyze its own logs:
-- Create an external table for JSON audit logs
CREATE EXTERNAL TABLE audit_logs (
timestamp STRING,
user STRING,
database STRING,
query STRING,
status STRING,
duration_ms BIGINT
)
ROW FORMAT SERDE 'org.apache.hive.hcatalog.data.JsonSerDe'
LOCATION '/var/log/impala/audit/';
-- Analyze top users by query volume
SELECT user, COUNT(*) AS query_count
FROM audit_logs
GROUP BY user
ORDER BY query_count DESC
LIMIT 10;
Limitations of Native Impala Audit Logging
Native Impala audit logging has several limitations:
- Limited contextual information
- No built-in analytics or alerting
- Manual storage management
- Sensitive data may appear in logs via query text
- Limited compliance reporting capabilities
Enhanced Impala Audit Logging with DataSunrise
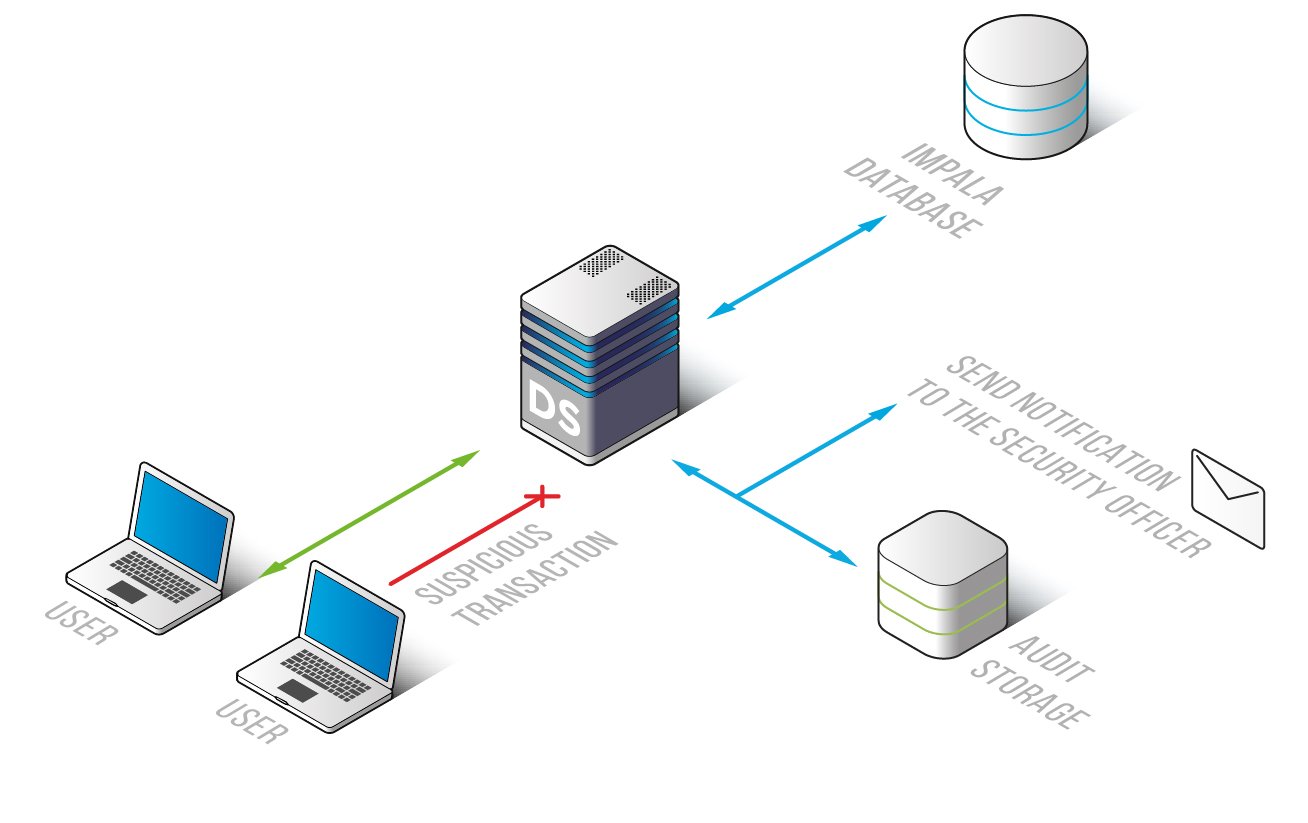
DataSunrise addresses native limitations with comprehensive audit capabilities:
Centralized Management
- Unified interface for managing audit policies
- Granular rules based on databases, tables, users, and query types
- Consistent policy enforcement across environments
Advanced Features
- Rich Context: Captures data classification, application context, and user details
- Real-Time Alerts: Configurable notifications for security events
- Behavioral Analytics: Analyzes user patterns to detect anomalies
- Automated Compliance: Streamlined reporting for GDPR, HIPAA, PCI DSS, and SOX
Best Practices for Apache Impala Audit Log
Based on industry experience and recommendations from the Impala security documentation, here are key best practices for implementing effective Impala audit logging:
1. Implement a Tiered Audit Strategy
Structure your audit logging approach to balance security needs with system performance:
- Standard Tier: Basic logging for routine operations
- Enhanced Tier: Detailed logging for sensitive data access
- Comprehensive Tier: Full audit capture for administrative operations
2. Optimize Log Storage and Retention
Implement efficient storage and retention policies:
- Store recent logs (30-90 days) in high-performance storage for quick analysis
- Archive older logs to cost-effective storage for compliance retention
- Implement encryption for stored audit logs to prevent tampering
- Document retention policies in accordance with regulatory requirements
3. Establish Regular Audit Review Processes
Create a structured approach to audit log review:
- Daily review of security alerts and anomalies
- Weekly analysis of access patterns and trends
- Monthly compliance review and reporting
- Quarterly audit effectiveness assessment
4. Correlate Audit Data Across Systems
As recommended in the Impala administration guide, correlate Impala audit data with other security information:
- Hadoop ecosystem logs (HDFS, Hive, HBase)
- Authentication systems (Kerberos, LDAP)
- Network security systems
- Host-based security logs
Business Value of Enhanced Impala Audit Logging and Security
Implementing robust audit logging for Impala delivers significant business value beyond basic compliance:
- Enhanced Threat Detection: Identify potential security incidents before they escalate
- Improved Operational Visibility: Understand usage patterns to optimize resource allocation
- Streamlined Compliance: Reduce the effort required for audit preparation and evidence collection
- Risk Mitigation: Address security gaps before they result in breaches or compliance violations
- Data Governance Support: Enable data stewardship with clear visibility into data usage
Conclusion
While Impala's native audit logging provides essential functionality, organizations with complex requirements benefit from enhanced solutions like DataSunrise, which offers advanced security analytics, compliance automation, and threat detection capabilities.
DataSunrise transforms Impala audit logs into actionable security intelligence with its intuitive interface and enterprise-grade features. Schedule a demo to see how it can strengthen your Impala data security and simplify compliance efforts.
