Apache Impala Data Compliance Automation
Introduction
Ensuring compliance for databases like Apache Impala is a crucial yet challenging task. As organizations handle increasingly sensitive data, regulations such as GDPR, HIPAA, and PCI DSS impose strict standards on data protection, auditing, and privacy. Automating compliance processes significantly reduces the risk of human error and streamlines the management of data security and regulatory adherence. This article covers how to automate data compliance for Apache Impala using both native capabilities and DataSunrise's advanced automation tools.
Native Data Compliance Automation in Apache Impala
Apache Impala provides some basic features for managing data compliance, but it requires significant manual configuration and administrative overhead for more complex use cases.
Step 1: Authentication and Authorization Management
Impala supports integration with Apache Ranger to provide role-based access control (RBAC). This ensures that sensitive data is only accessible by authorized users. However, configuring and maintaining these roles manually can be a time-consuming process.
Code Example:
<property>
<name>impala.authentication</name>
<value>kerberos</value>
</property>
This configuration activates Kerberos authentication, which is a critical first step in ensuring that only authorized users can interact with sensitive data.
Step 2: Configuring Audit Logging
Audit logs are an essential part of maintaining compliance, as they provide traceability of all user activities within the database. Impala allows for some basic logging capabilities, but managing and analyzing these logs can become cumbersome, especially when compliance regulations demand detailed and frequent reporting.
Code Example:
<property>
<name>impala.audit.event.log.dir</name>
<value>/var/log/impala/audit</value>
</property>
This snippet configures Impala to store audit logs, enabling organizations to review and monitor database access.
Step 3: Data Encryption
Data encryption is necessary to protect sensitive information, both at rest and in transit. While Impala supports encryption features, the implementation often requires careful planning and frequent updates to ensure that compliance standards are met, particularly in high-volume environments.
Code Example for SSL Encryption:
<property>
<name>impala.ssl.enabled</name>
<value>true</value>
</property>
<property>
<name>impala.ssl.server.cert</name>
<value>/path/to/server-cert.pem</value>
</property>
<property>
<name>impala.ssl.server.key</name>
<value>/path/to/server-key.pem</value>
</property>
This enables TLS/SSL encryption for data in transit, an essential feature for meeting compliance requirements.
Step 4: Basic Data Masking
Impala allows for simple data masking using views to protect sensitive information. However, this method is limited and doesn’t offer dynamic protection for all types of sensitive data.
Code Example:
CREATE VIEW masked_view AS
SELECT id, CONCAT('XXX-XX-', RIGHT(ssn,4)) AS masked_ssn
FROM employee_data;
This SQL query creates a masked version of the ssn column, ensuring that sensitive information is not exposed in certain scenarios. For advanced data masking, refer to Dynamic Data Masking.
Automating Data Compliance with DataSunrise
While Apache Impala’s native features provide a foundation for data compliance, they still require substantial manual effort and lack advanced automation. DataSunrise, however, enhances Impala's compliance capabilities by providing a unified, automated solution that reduces administrative overhead and ensures continuous compliance.
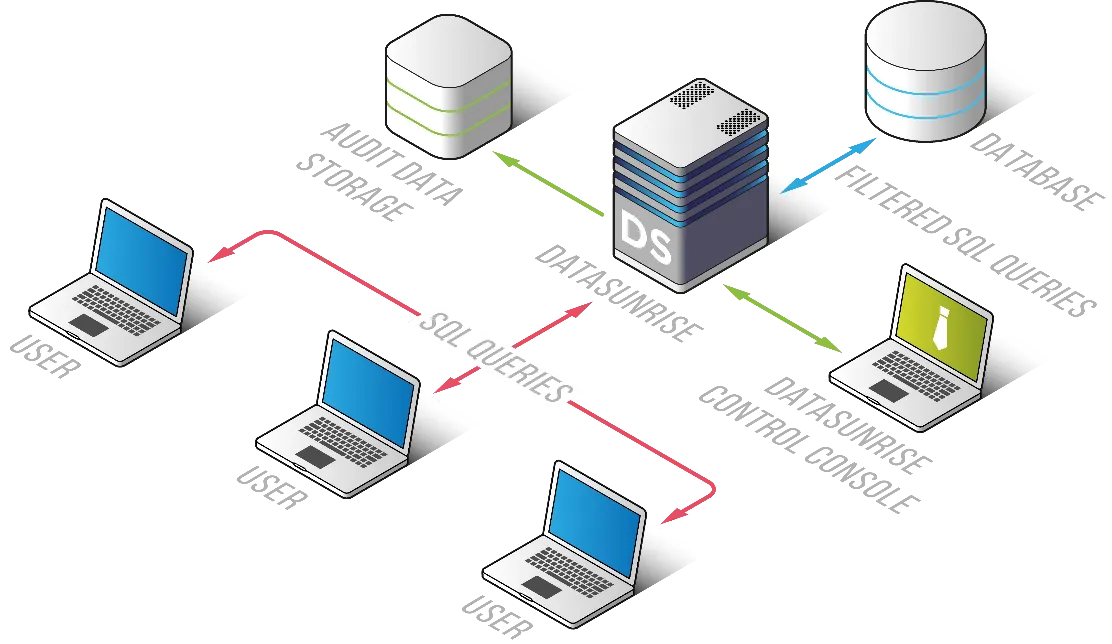
Step 1: Zero-Touch Data Discovery and Masking
DataSunrise enables zero-touch deployment with automatic discovery of sensitive data across various environments, including databases, data lakes, and file systems. Sensitive data is automatically detected and masked in real-time, significantly streamlining the process of meeting privacy regulations.
Key Benefits:
- Auto-Discover & Mask: Automatically discovers sensitive data and applies masking, no manual intervention required.
- Flexible Deployment: Works in cloud, on-premises, or hybrid environments with no complex configuration.
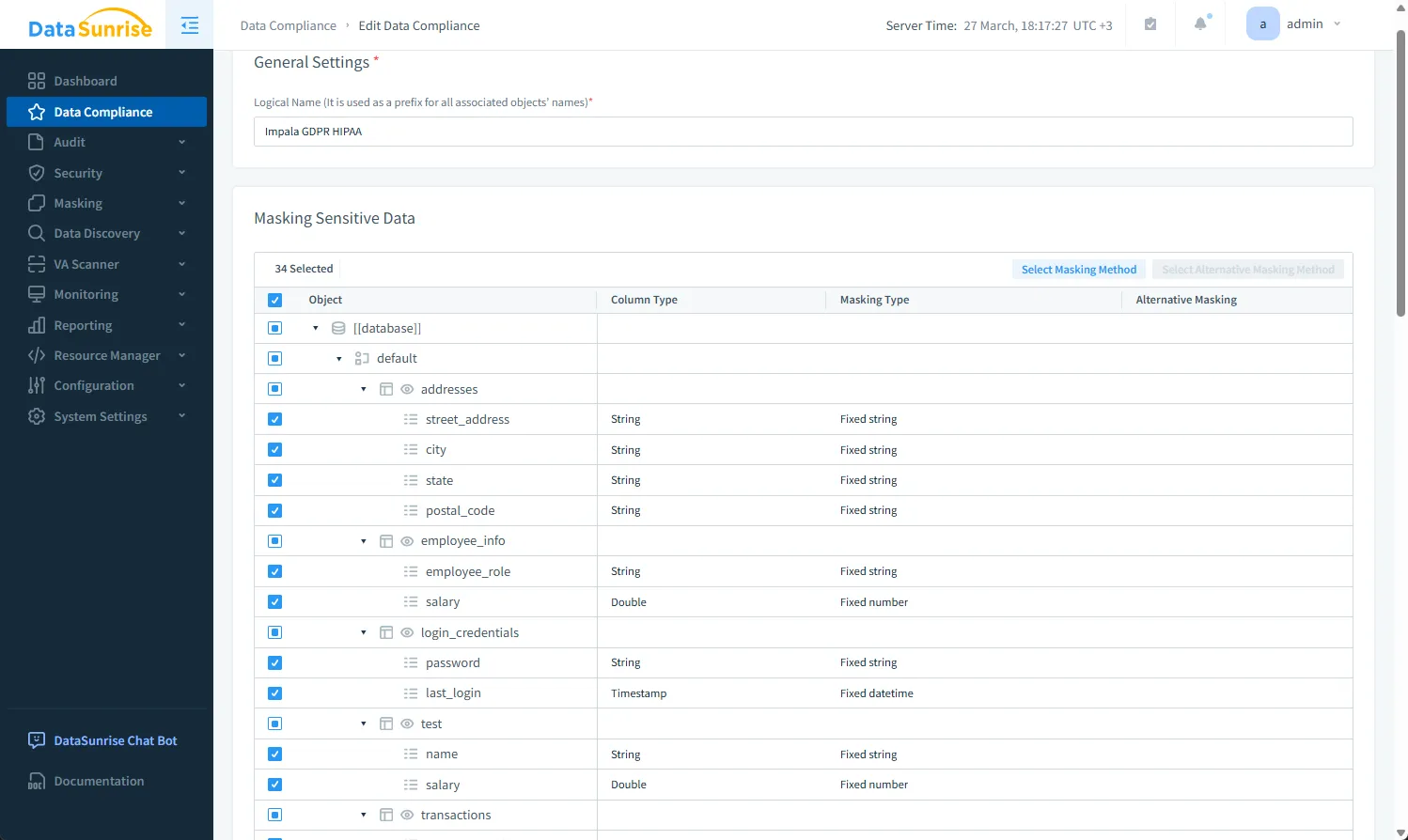
For further guidance, refer to the Data Masking Guide.
Step 2: Continuous Compliance Monitoring and Reporting
DataSunrise offers continuous compliance monitoring, which ensures that any change in the data environment, such as access to sensitive information or modifications to security policies, is automatically flagged and reported. This feature is especially beneficial for organizations that need to adhere to stringent regulations.
Key Benefits:
- Automated Reporting: Automatically generates compliance reports for various frameworks.
- Real-Time Alerts: Send real-time notifications if any compliance violations occur.
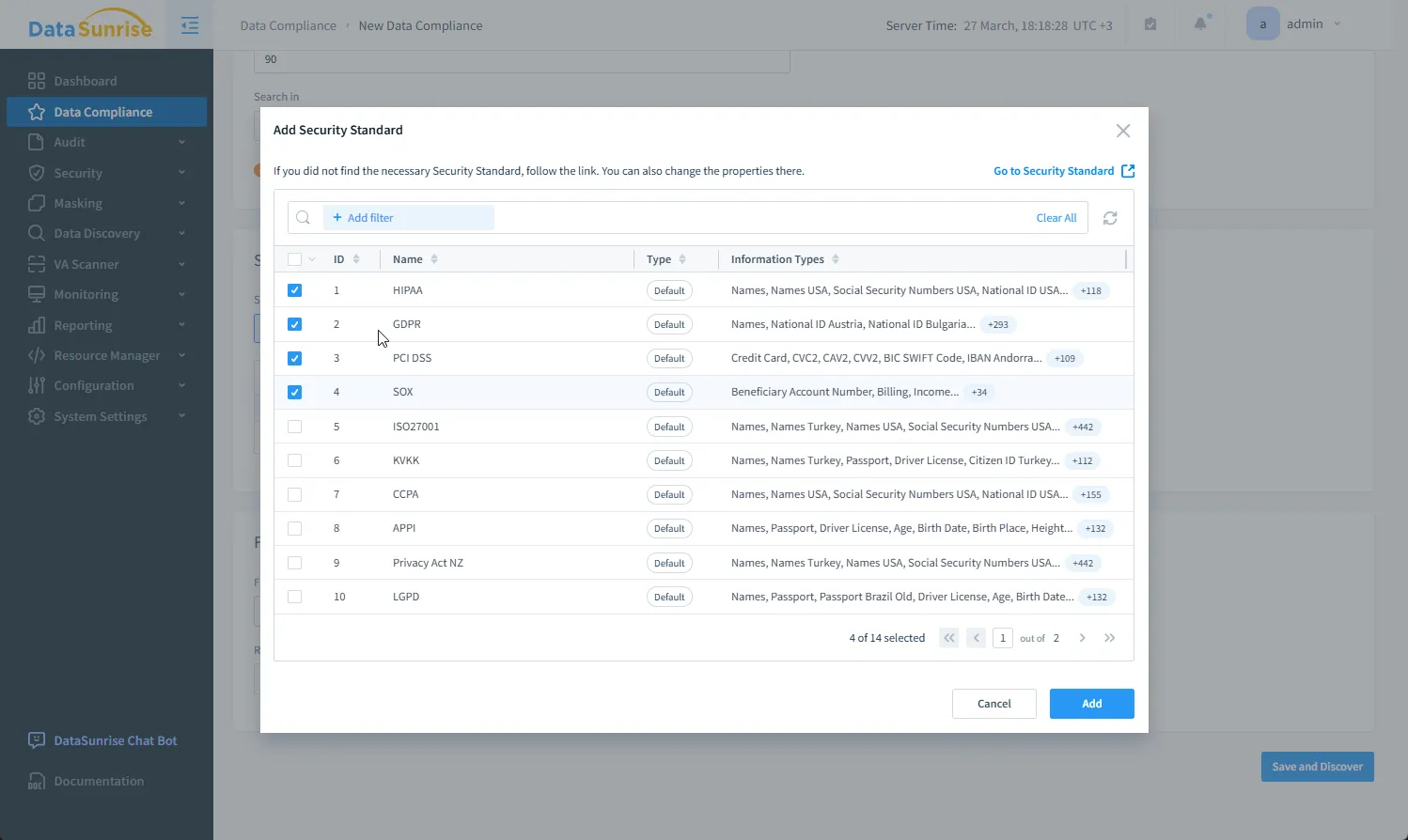
Learn more in the Compliance Manager Guide.
Step 3: Role-Based Access Control (RBAC) and Fine-Grained Security Policies
DataSunrise extends Impala’s role-based access control capabilities with advanced policy automation. These policies can be fine-tuned to meet specific compliance requirements, such as restricting access to certain data or actions based on the user role.
Key Benefits:
- Automated Security Policies: Automatically enforce access control policies based on user roles and data sensitivity.
- Seamless Integration: Easily integrates with existing Impala infrastructure, reducing the need for complex manual setups.
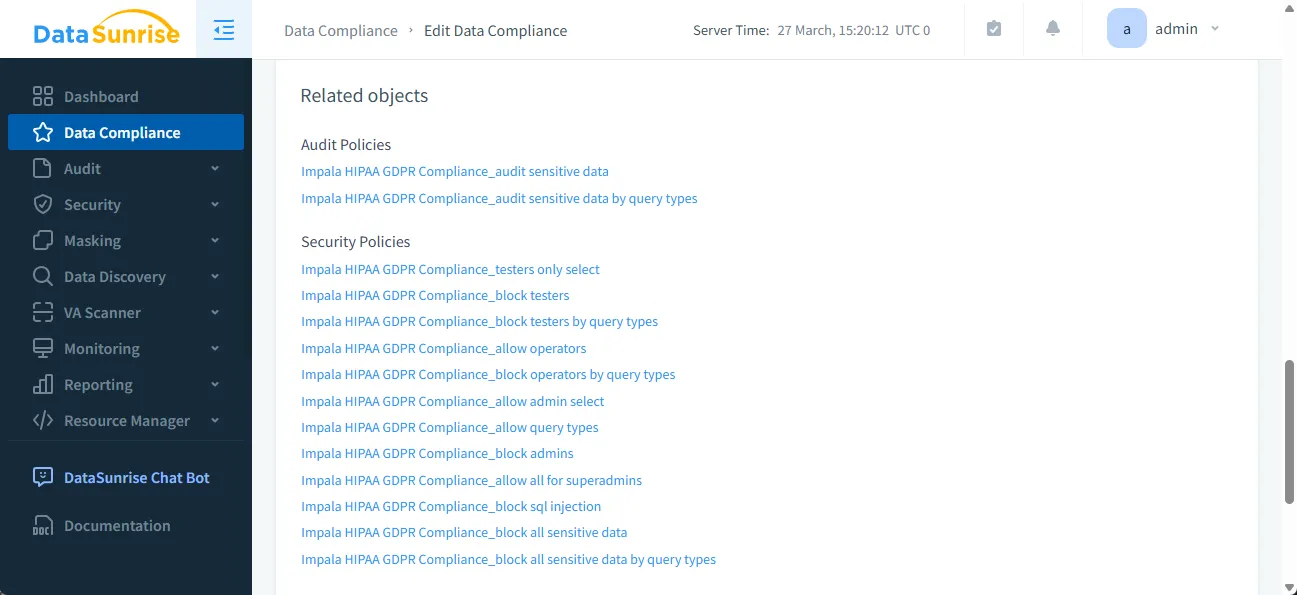
Learn more about the Security Guide for detailed instructions.
Conclusion
While Apache Impala provides some basic capabilities for data compliance, organizations need more comprehensive automation to manage complex regulatory requirements. DataSunrise offers advanced solutions for automating compliance processes, including zero-touch data discovery, real-time monitoring, automated policy enforcement, and ML-driven governance.
By integrating DataSunrise, organizations can achieve continuous compliance, reduce administrative workload, and ensure robust security without manual intervention.
Explore DataSunrise’s Demo to see how our compliance automation features can elevate your data security and regulatory adherence strategy.
