
Essential Application Security Best Practices for Protecting Your Software and Data

Introduction
In today’s digital world, software applications are the lifeblood of many businesses. From web applications to mobile apps, software helps organizations operate more efficiently and reach more customers. However, with the increased reliance on software comes increased risk. Application security protects software code and data from cyber threats. Important for organizations that create or use software.
Why is Application Security Important?
Application security is important for several key reasons:
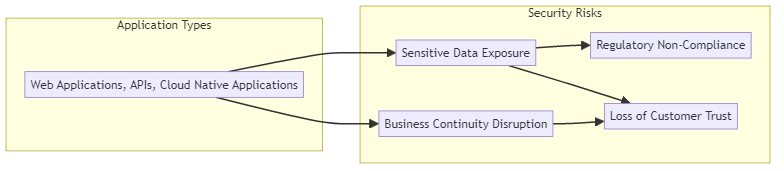
- Protecting sensitive data: Applications often handle sensitive data like customer information, financial records, and intellectual property. A security breach could expose this data, leading to identity theft, financial losses, and reputational damage.
- Maintaining business continuity: If a team has to fix a hacked app, they might have to temporarily shut it down. This downtime can disrupt business operations and lead to lost revenue.
- Complying with regulations: Several industries have rules for protecting data, like GDPR in the EU and HIPAA in healthcare. Failing to secure applications can lead to non-compliance and hefty fines.
- Preserving customer trust: Data breaches can severely damage customer trust. If customers don’t feel their data is safe with a company, they may take their business elsewhere.
Types of Applications that Need Security
Web Application Security
Web applications are software that runs on a web server and is accessible via the Internet. They face a range of vulnerabilities by accepting connections from clients over insecure networks. Web applications that are important for business and have customer data are a top priority for cyber security programs.
OWASP has a list of common web app vulnerabilities called the OWASP Top 10. These include injection attacks, broken authentication, and sensitive data exposure.
Organizations can protect web applications by using tools like web application firewalls (WAF) to stop application-layer attacks.
Website security is a critical aspect of overall application security. Vulnerabilities in web applications can lead to data breaches, identity theft, and other serious consequences. To ensure robust web security, developers must implement secure coding practices, regularly update software and frameworks, and conduct thorough testing.
Input validation, proper authentication and authorization mechanisms, and encryption of sensitive data are essential components of website security.
Additionally, implementing security headers, such as HTTP Strict Transport Security (HSTS) and Content Security Policy (CSP), can help mitigate common web-based attacks like cross-site scripting (XSS) and clickjacking. Regular security audits and penetration testing can identify potential vulnerabilities before they are exploited by attackers.
By prioritizing website security throughout the development lifecycle and staying informed about the latest web security threats and best practices, organizations can protect their web applications and the sensitive data they handle.
API Security
Application Programming Interfaces (APIs) allow different software systems to communicate with each other. They are the foundation of modern microservices architectures and enable the sharing of data and functionality across organizations.
However, APIs can also be a security weak point. Vulnerabilities in APIs can expose sensitive data and disrupt critical business operations. Common API security weaknesses include weak authentication, excessive data exposure, and lack of rate limiting.
Specialized tools exist to identify vulnerabilities in APIs and secure them in production environments.
Cloud Native Application Security
Developers build cloud native applications using technologies like containers and serverless platforms. Securing these applications is complex because of their distributed nature and the ephemeral nature of their components.
In cloud native environments, developers typically define infrastructure as code. This means developers are responsible for building secure configurations, not just secure application code. Automated scanning of all artifacts, especially container images, is crucial at all stages of development.
Security tools for cloud applications can monitor containers and serverless functions, identify security issues, and provide prompt feedback to developers.
Application Security Best Practices
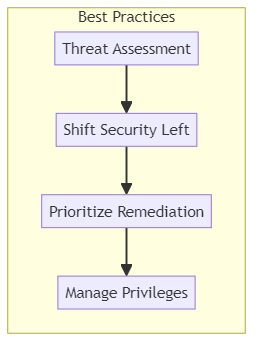
Perform a Threat Assessment
Understanding the threats your applications face is the first step in effective application security. Think about how attackers could hack your apps, what security you already have, and where you might need more protection.
Check if hackers can easily hack your website with SQL injection if it contains important customer information. If your security measures aren’t enough, consider adding input validation or using a web application firewall to improve protection.
Shift Security Left
In the past, developers often left security testing until the end of the development process. However, with the increasing pace of software development, this is no longer feasible. Integrate security testing into the development cycle from the start – developers refer to this process as “shifting security left”.
To achieve this, security teams need to work closely with development teams. They need to understand the tools and processes developers use to seamlessly integrate security. Use automated security testing tools in the CI/CD pipeline to help developers find and fix issues quickly.
For example, developers can analyze static code every time they commit code to receive immediate feedback on potential security vulnerabilities.
Prioritize Remediation Efforts
With the growing number of vulnerabilities, it’s not always possible for developers to address every single issue. Prioritizing is key to ensuring that we fix the most critical vulnerabilities first.
Effective prioritization involves assessing the severity of each vulnerability, often using the Common Vulnerability Scoring System (CVSS). Consider the operational importance of the affected application.
A significant issue on a website for customers is more crucial than a minor problem in an internal tool.
Manage Privileges
The principle of least privilege is a cornerstone of application security. It states that users and systems should only have the minimum level of access necessary to perform their functions.
Limiting privileges is important for two reasons. Firstly, if an attacker compromises a low-privileged account, they will have limited ability to cause damage. Secondly, it reduces the potential impact of insider threats.
For instance, a database application should run with the minimum privileges required to function, rather than as a superuser. If the attacker compromises the application, they will have limited ability to interact with the database in this way.
Summary and Conclusion
Application security is a critical consideration in today’s digital landscape. If you’re making websites, APIs, or cloud apps, it’s important to prioritize securing your code and data.
Effective application security involves understanding the threats you face, integrating security into the development process, prioritizing remediation efforts, and managing privileges. Following best practices helps organizations reduce the risk of data breaches. It also helps them maintain smooth business operations.
Additionally, it helps them comply with regulations. Finally, it aids in gaining the confidence of their customers.
At DataSunrise, we offer user-friendly and flexible tools for database security, data discovery (including OCR), and compliance. Our solutions can help you secure your applications and protect your sensitive data. Contact our team today for an online demo and see how we can help strengthen your application security posture.
Some key takeaways:
- Application security protects software code and data from cyber threats
- Common application types that need security include web apps, APIs, and cloud native apps
- Developers should integrate security into the development process from the start.
- Prioritizing remediation efforts is key to addressing the most critical vulnerabilities first
- Limiting privileges is an important principle in application security
Application security is a complex and ever-evolving field. To protect applications and data, organizations should stay updated on threats, use the right tools, and follow best practices.
