Audit Trails in YugabyteDB
Introduction
As enterprises increasingly adopt distributed SQL databases like YugabyteDB for mission-critical applications, implementing a comprehensive audit trail has evolved from being merely a compliance requirement to becoming an operational necessity.
The Growing Need for Audit Trails
According to 2023 IDC research, 78% of organizations now operate under multiple data compliance regulations. Consequently, as regulatory frameworks become more complex, businesses must ensure their databases maintain a verifiable record of data access and modifications.
How YugabyteDB Supports Enterprise Auditing
By leveraging YugabyteDB’s native capabilities alongside strategic enhancements, enterprises can establish a robust solution for tracking data activity history across distributed architectures. However, successfully implementing an audit trail requires addressing key enterprise needs.
Why Implement an Audit Trail in YugabyteDB?
A well-implemented audit trail in YugabyteDB fulfills three critical enterprise needs:
- Security Incident Investigation: Enables tracing of
unauthorized access patterns across nodes.
- Regulatory Compliance: Ensures data integrity and
adherence to GDPR, HIPAA,
and SOC 2.
- Operational Analytics: Helps identify performance bottlenecks through query pattern analysis.
However, the distributed nature of YugabyteDB presents unique challenges. Specifically, maintaining audit log consistency across nodes while preserving performance can be complex.
Overcoming Challenges in Distributed Auditing
To address this challenge effectively, enterprises must leverage a combination of YugabyteDB’s built-in tools and additional enhancements. The following sections explore both native capabilities and external solutions that together create a comprehensive audit strategy.
Native Audit Trail in YugabyteDB: Core Implementation Patterns
Configuration and Event Capture
YugabyteDB builds upon PostgreSQL’s battle-tested audit framework while incorporating optimizations for distributed systems.
Setting Up Audit Logging
The native implementation captures events at the node level, while also providing tools for cluster-wide aggregation. To enable granular auditing, configure YB-TServer settings and SQL-level controls as follows:
# yb-tserver.conf
yb_enable_audit_logging=true
pgaudit.log='ddl, dml, role'
pgaudit.log_relation=on
pgaudit.log_parameter=onReal-Time Transaction Auditing
For real-time auditing of financial transactions, define an audit table and trigger:
CREATE TABLE audit.financial_changes (
change_id UUID DEFAULT gen_random_uuid(),
change_time TIMESTAMPTZ NOT NULL,
user_name TEXT,
ip_address INET,
operation TEXT,
before_state JSONB,
after_state JSONB
);
CREATE TRIGGER log_financial_changes
AFTER INSERT OR UPDATE ON transactions
FOR EACH ROW EXECUTE FUNCTION audit.record_change();Distributed Log Management
Because YugabyteDB automatically shards audit logs across nodes, querying cross-node events requires built-in functions.
Querying Distributed Logs
To retrieve relevant audit events, use the following query:
-- Query cross-node audit events
SELECT * FROM yb_audit_log_aggregate
WHERE application_name = 'payment-service'
AND event_time BETWEEN '2024-03-01' AND '2024-03-31';Automating Large-Scale Log Collection
For large-scale deployments, automating log collection is essential:
# Export audit logs from all nodes
yb-admin -master_addresses yb-master1:7100,yb-master2:7100 \
export_audit_logs /srv/audit/export/Retention and Rotation Strategies
To ensure audit logs do not consume excessive storage, implementing tiered retention policies using native partitioning is crucial.
Implementing Partition-Based Retention
CREATE TABLE audit.logs_partitioned (
event_id BIGSERIAL,
event_time TIMESTAMPTZ,
event_data JSONB
) PARTITION BY RANGE (event_time);
CREATE TABLE audit_logs_2024_q1 PARTITION OF audit.logs_partitioned
FOR VALUES FROM ('2024-01-01') TO ('2024-04-01');Automating Log Archival
Automating archival ensures that older logs do not interfere with ongoing database operations:
CREATE EVENT TRIGGER archive_audit_logs
ON SCHEDULE EVERY 1 MONTH
DO
ALTER TABLE audit.logs_partitioned DETACH PARTITION audit_logs_2023_q4;Enhancing Audit Trail Capabilities with DataSunrise
Seamless Integration and Comprehensive Monitoring
While YugabyteDB’s native auditing provides a strong foundation, enterprises often require advanced visualization, real-time alerting, and deeper analytics for audit data.
How DataSunrise Enhances YugabyteDB
DataSunrise enhances YugabyteDB’s auditing capabilities by supporting both the Cassandra and PostgreSQL APIs. Consequently, enterprises benefit from real-time anomaly detection, centralized audit log management, and advanced query analysis.
Enhanced Data Discovery and Compliance Management
Classifying and Securing Sensitive Data
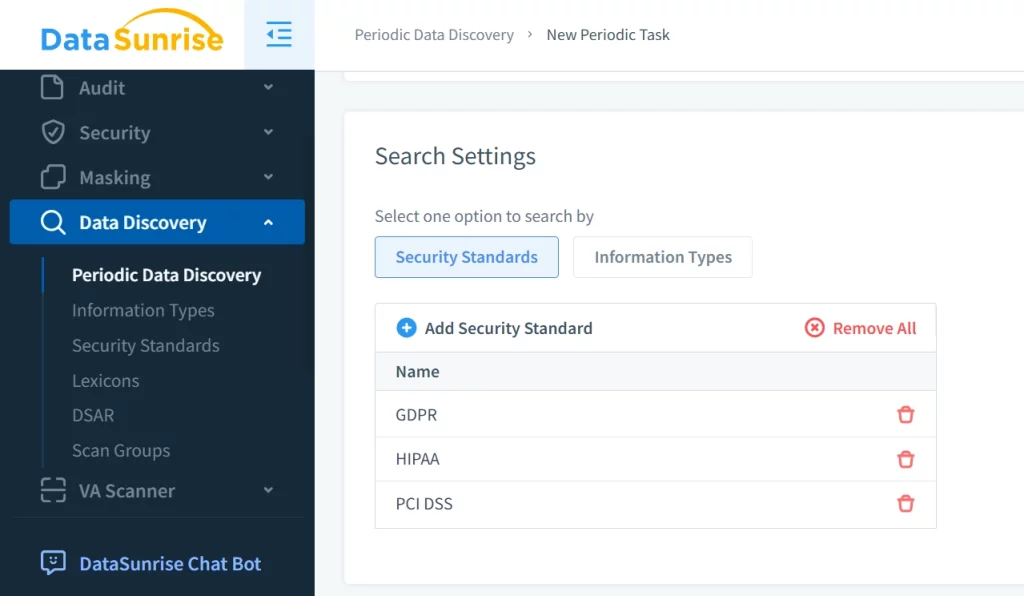
Data discovery plays a key role in helping organizations classify sensitive data and ensure compliance with regulations such as GDPR and HIPAA. With DataSunrise’s automated discovery engine, enterprises can:
- Identify and categorize personally identifiable information (PII)
and financial records.
- Enforce access control policies based on data sensitivity.
- Generate audit reports that align with industry regulations.
Proactive Threat Detection and Security Audits
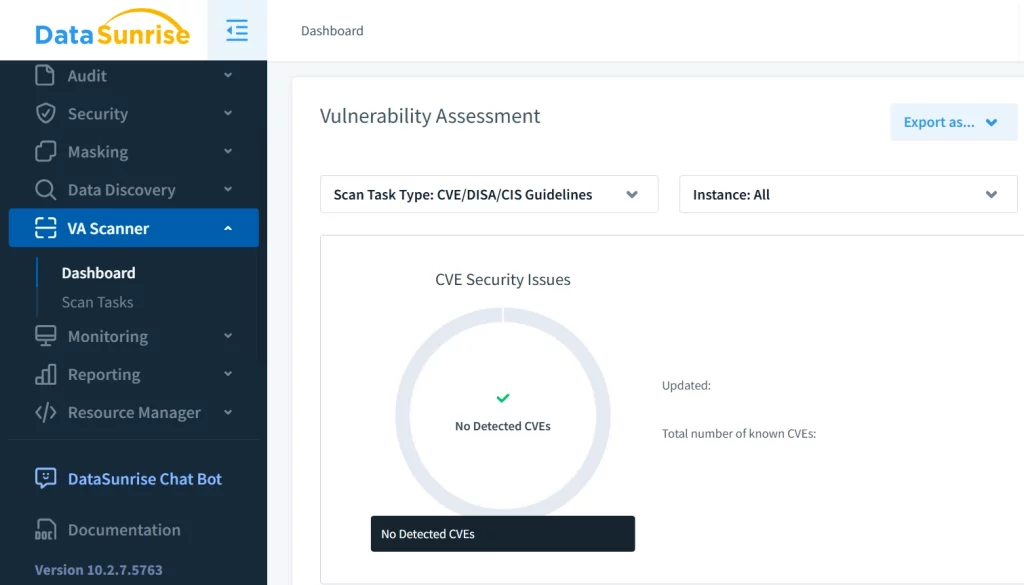
Continuous Risk Assessment with the Vulnerability Assistant
To further strengthen security, the Vulnerability Assistant in DataSunrise continuously scans for misconfigurations, outdated permissions, and suspicious activities within YugabyteDB.
Not only does it detect SQL injection attempts, but it also provides detailed risk assessments, allowing security teams to respond proactively to evolving threats.
Real-Time Security Monitoring
By integrating YugabyteDB with DataSunrise, enterprises can achieve real-time security monitoring, detailed compliance reporting, and proactive threat prevention—making it a valuable addition to any database security strategy.
