
Audit Trails: Ensuring Data Security and Compliance

Introduction
Data breaches often stem from unintentional human errors. In fact, studies show that over two-thirds of data breaches involve non-malicious actions by insiders. This highlights the risk of accidental data exposure and underscores the critical need for robust data protection strategies. Implementing comprehensive audit trails is a key component of such strategies, helping organizations monitor and safeguard sensitive information more effectively.
What is an Audit Trail?
An audit trail is a chronological record of system activities. It captures who accessed the database, what actions they performed, and when these actions occurred. This detailed log serves as a powerful tool for:
- Detecting unauthorized access
- Tracking data modifications
- Investigating security incidents
- Ensuring regulatory compliance
Audit trails play a crucial role in maintaining the integrity and security of your database systems.
Approaches to Database Audit Trails
There are two main approaches to implementing audit trails in databases:
Native Tools
Many database management systems (DBMS) offer built-in auditing capabilities. These native tools provide a straightforward way to enable basic auditing functions. For example, Oracle has its Audit Trail feature, while Microsoft SQL Server includes SQL Server Audit.
Third-Party Tools
Third-party audit trail solutions, like DataSunrise, offer more advanced features and centralized management. These tools often provide:
- Enhanced security controls
- Cross-platform compatibility
- Customizable reporting options
- Real-time alerting capabilities
Example: Audit Trail with pgAudit in PostgreSQL
To view the PgAudit log, you can use the ‘cat’ command as follows (more details here):
cat /var/log/postgresql/postgresql-16-main.log | more
Let’s look at a brief example of what an audit trail might look like using the pgAudit extension in PostgreSQL:
2024-09-17 10:15:23 UTC,AUDIT,SESSION,1,1,READ,SELECT,TABLE,public.users,,,SELECT * FROM users WHERE id = 123;
This log entry shows:
- Timestamp
- Audit type
- Session and user IDs
- Operation type (READ)
- SQL statement type (SELECT)
- Object type (TABLE)
- Schema and table name
- The actual SQL query executed
Native audit capabilities often fall short in advanced features. While they provide basic logging, they typically lack data tagging, built-in analytics, and automated rule application. Transforming raw log files, like the example shown earlier, into actionable insights requires significant additional effort and processing.
Creating a DataSunrise Instance for Audit Trail
Assuming DataSunrise is already installed, here’s how to create an instance and view an audit trail:
- Log in to the DataSunrise web interface
- Navigate to “Instances” and click “+ Add New Instance”
- Configure the connection details for your database. DataSunrise consolidates all database connections in one location.
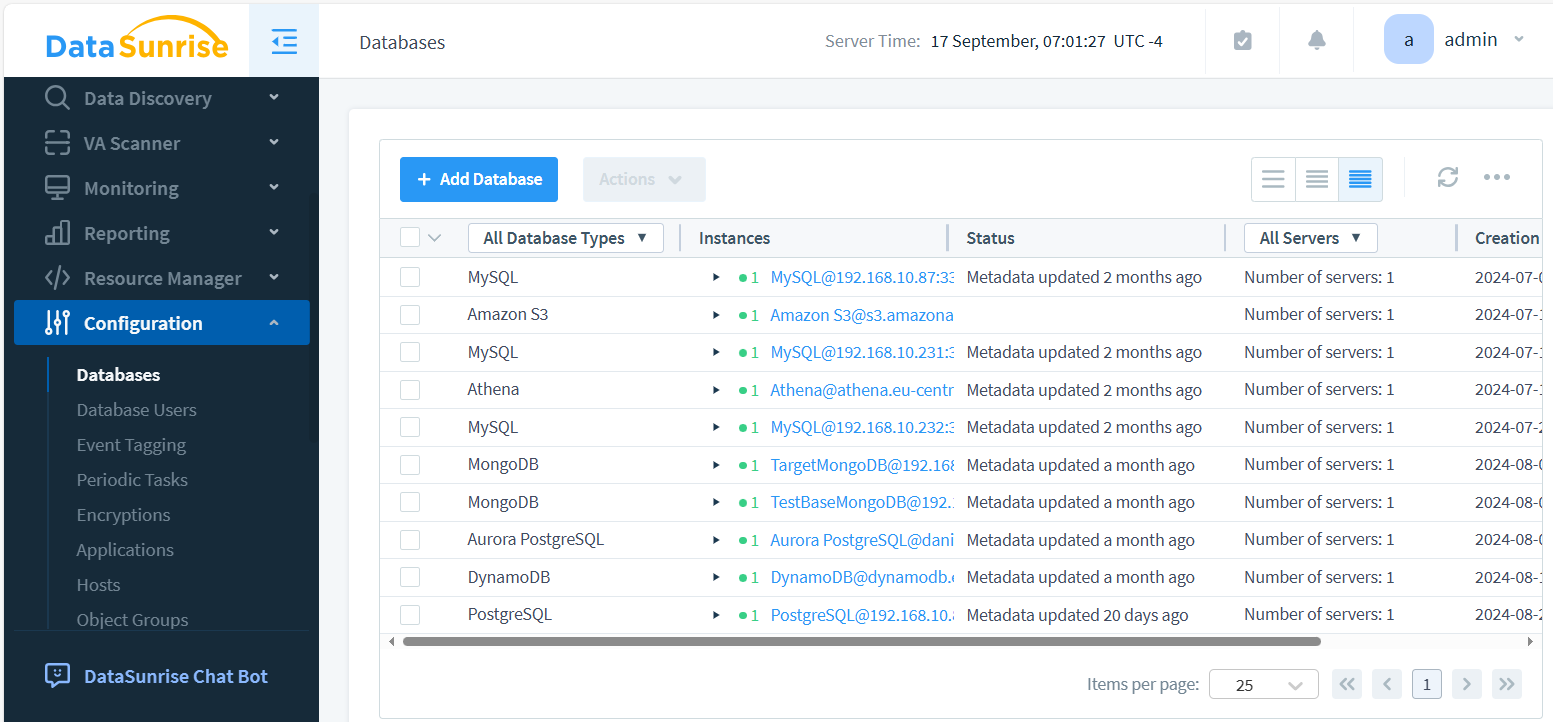
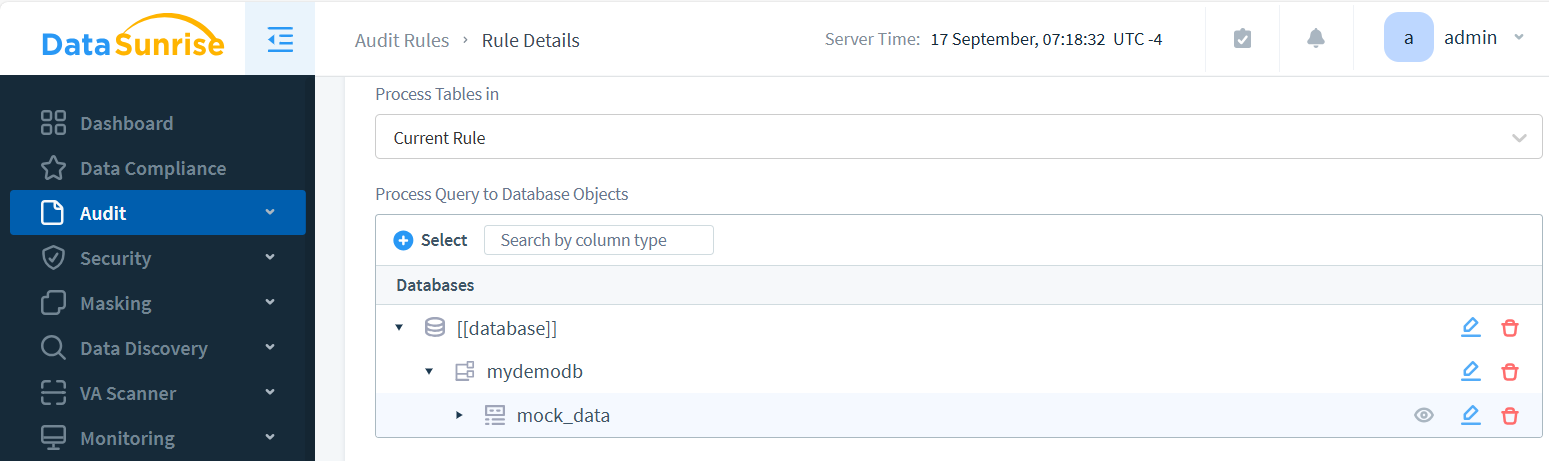
- Create Audit Rule in Audit – Rules and enable auditing for the desired objects.
- Access the “Audit – Transactional Trails” section to view and analyze the generated trails.
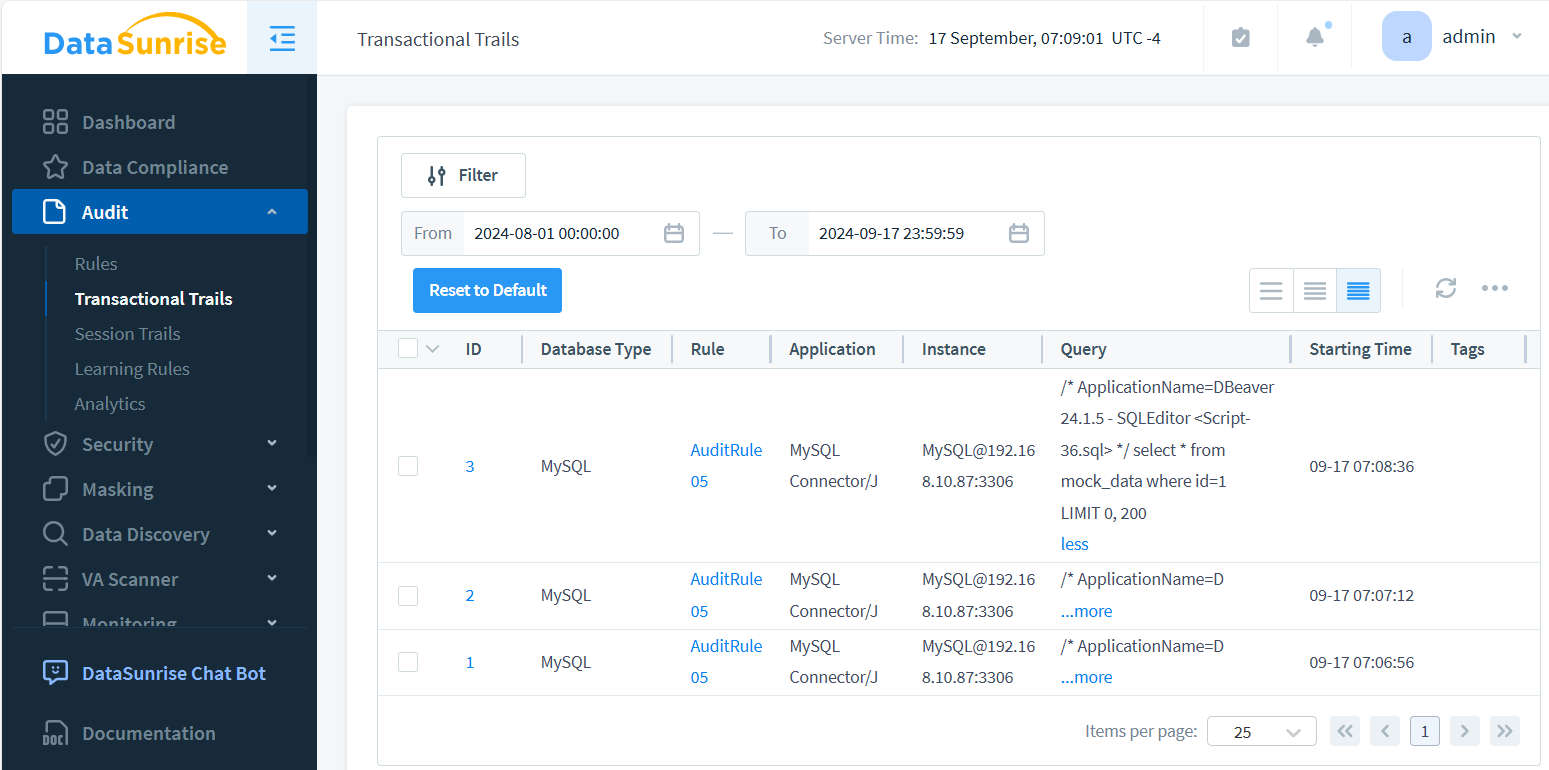
DataSunrise makes it easy to set up comprehensive auditing across multiple database platforms. The image above showcases key audit trail components: instance details, timestamps, and logged queries. Optionally, query results can be captured as well. Each event in the Audit Trail is interactive, allowing users to drill down and view detailed database query outcomes with a simple click.
Benefits of DataSunrise for Centralized Audit Control
DataSunrise offers several advantages for managing audit trails:
- Unified Interface: Control audit rules across various database types from a single dashboard
- Customizable Policies: Create tailored audit policies based on your specific security requirements
- Real-time Monitoring: Detect and alert on suspicious activities as they occur
- Compliance Support: Meet regulatory requirements with pre-configured compliance reports
- Scalability: Easily manage audit trails for large, complex database environments
The Importance of User Behavior Monitoring
Tracking user behavior is critical for maintaining database security. Comprehensive audit trails serve as vigilant watchdogs, helping organizations identify a range of suspicious activities. These include unusual access patterns that deviate from normal user behavior, unauthorized data modifications that could compromise integrity, attempts to escalate privileges beyond assigned roles, and potential insider threats that often go unnoticed. By meticulously analyzing these patterns, organizations can proactively address security risks, implement targeted countermeasures, and effectively protect sensitive data from both external and internal threats.
Best Practices for Implementing Audit Trails
To maximize the effectiveness of your audit trail system, it’s crucial to adopt a comprehensive approach. Start by defining clear auditing objectives that align with your organization’s security goals. Implement least privilege access to minimize potential risks. Regularly review and analyze audit logs to detect anomalies and potential threats promptly. Establish a robust retention policy for audit data to ensure compliance and historical analysis. Safeguard the integrity of your audit trails through secure storage mechanisms. Lastly, conduct periodic audits of the auditing system itself to ensure its reliability and effectiveness. By diligently following these practices, you’ll significantly enhance your overall database security posture and create a more resilient defense against potential threats.
Challenges in Audit Trail Management
While trails are invaluable, they come with challenges:
- Performance Impact: Extensive auditing can affect database performance
- Storage Requirements: Audit logs can grow rapidly, requiring significant storage
- Data Privacy: Audit trails may contain sensitive information, requiring careful handling
- Analysis Complexity: Large volumes of audit data can be overwhelming to analyze
Tools like DataSunrise help address these challenges through efficient log management and advanced analytics capabilities.
The Future of Audit Trails
As data security threats evolve, so too must audit trail technologies. Future trends include:
- AI-powered anomaly detection
- Blockchain-based immutable audit logs
- Integration with threat intelligence platforms
- Enhanced visualization and reporting tools
Staying ahead of these trends will be crucial for maintaining robust database security.
Conclusion
Audit trails are essential components of a comprehensive database security strategy. They provide visibility into user activities, help detect potential threats, and ensure compliance with regulatory requirements. While native database tools offer basic auditing capabilities, third-party solutions like DataSunrise provide advanced features for centralized management and enhanced security control.
By implementing best practices and leveraging powerful audit trail tools, organizations can significantly improve their ability to protect sensitive data and maintain the integrity of their database systems.
DataSunrise offers flexible and user-friendly tools for database security, including comprehensive data activity monitoring and data masking capabilities. To experience the power of DataSunrise’s security suite firsthand, visit our website for an online demo and discover how we can help strengthen your database security posture.
