Aurora MySQL Data Governance
Managing sensitive data in Amazon Aurora MySQL requires a robust governance framework. Organizations must ensure real-time audit capabilities, dynamic data masking, security compliance, and data discovery to mitigate risks and adhere to regulations. This article explores best practices and technologies that enhance Aurora MySQL data governance.
Real-Time Audit for Continuous Monitoring
Real-time auditing is crucial for tracking database activity and detecting unauthorized access attempts. Aurora MySQL supports native audit logging through the MySQL Audit Plugin Audit Logs and third-party tools like DataSunrise.
Configuring MySQL Audit Plugin
To enable MySQL auditing on Aurora, use the following SQL command:
CALL mysql.rds_set_configuration('binlog retention hours', 24);
CALL mysql.rds_set_configuration('general_log', 1);
CALL mysql.rds_set_configuration('audit_log', 'ENABLED');
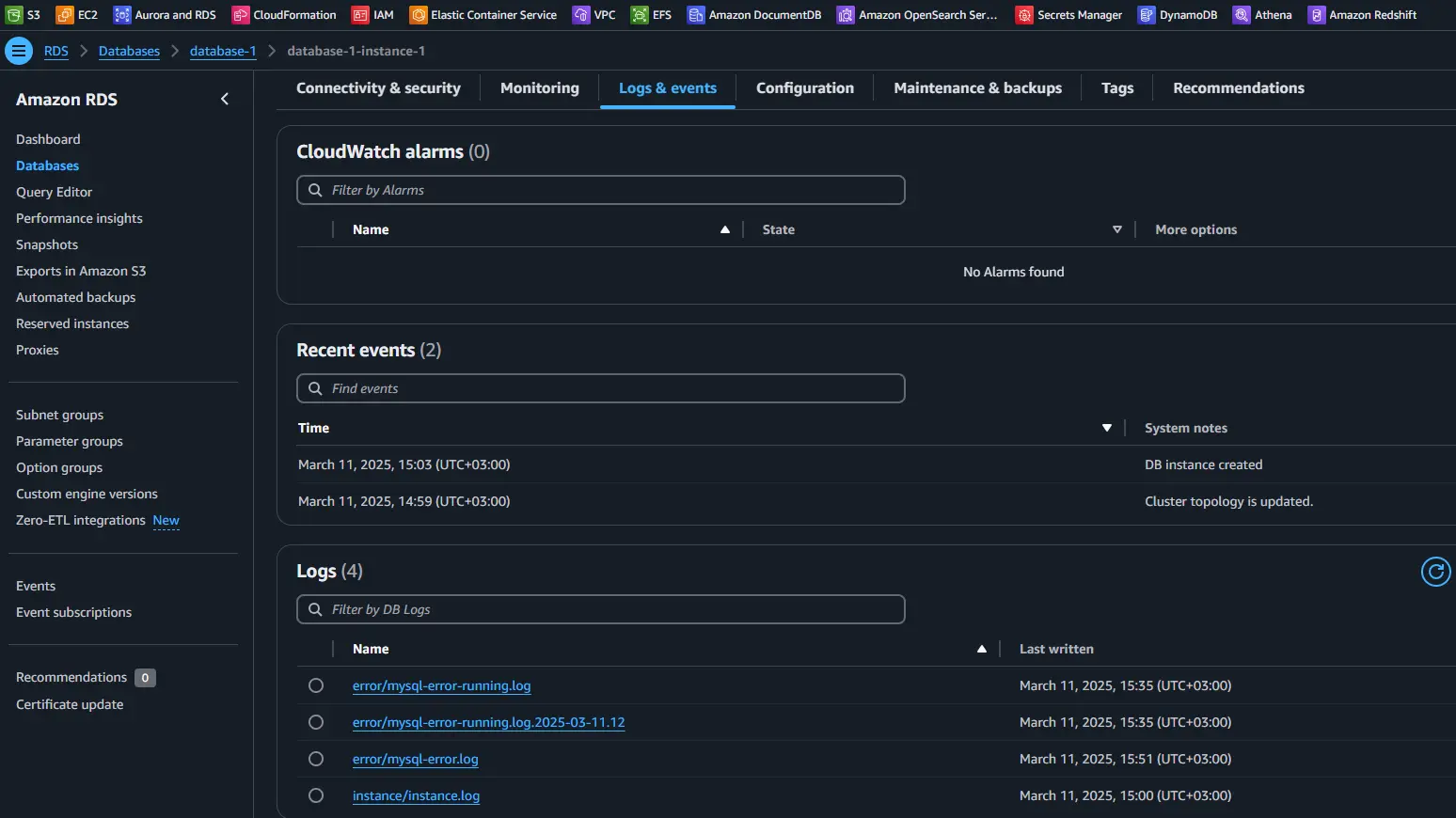 For detailed setup, refer to AWS MySQL Audit Plugin Documentation.
For detailed setup, refer to AWS MySQL Audit Plugin Documentation.
Dynamic Data Masking for Secure Data Access
Dynamic Data Masking (DDM) helps prevent unauthorized users from viewing sensitive information. Aurora MySQL integrates with DataSunrise's Dynamic Data Masking to apply real-time obfuscation.
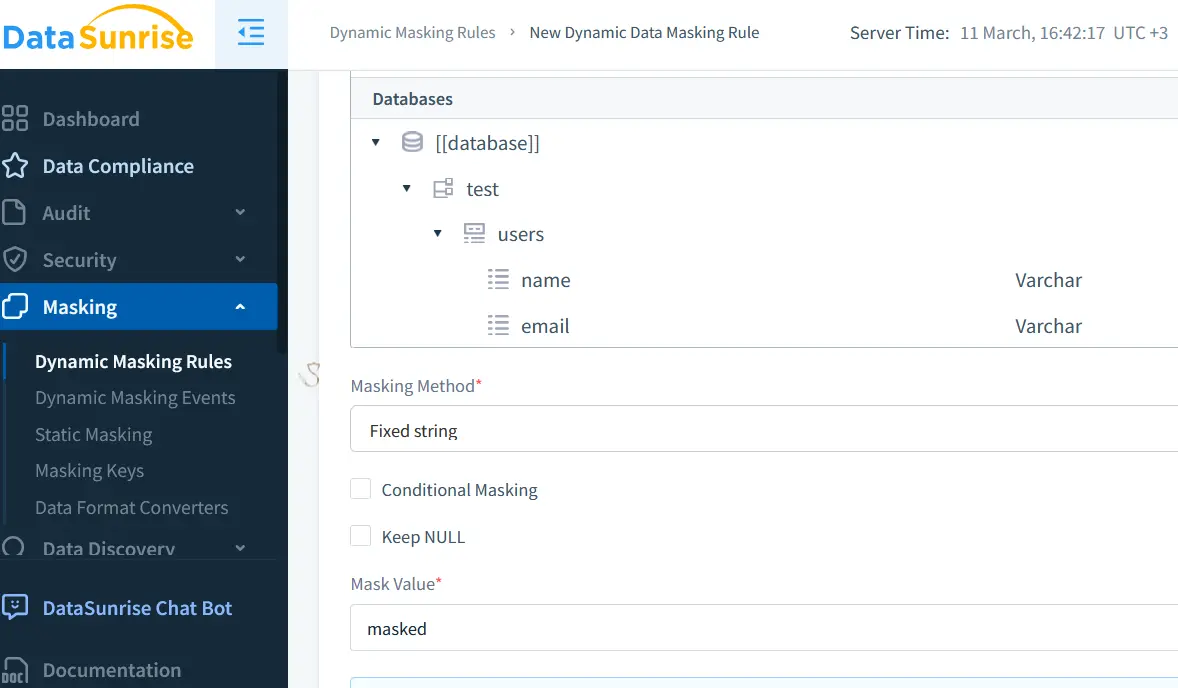
Example: Masking Credit Card Information
SELECT credit_card_number, MASKED(credit_card_number, 'XXXX-XXXX-XXXX-####') FROM customers;
This ensures that only authorized users see full credit card numbers while others receive masked data.
Data Discovery and Classification
Automated data discovery helps organizations identify and classify sensitive data, ensuring compliance with regulations like GDPR and HIPAA. DataSunrise provides Data Discovery capabilities that automatically scan and categorize database contents.
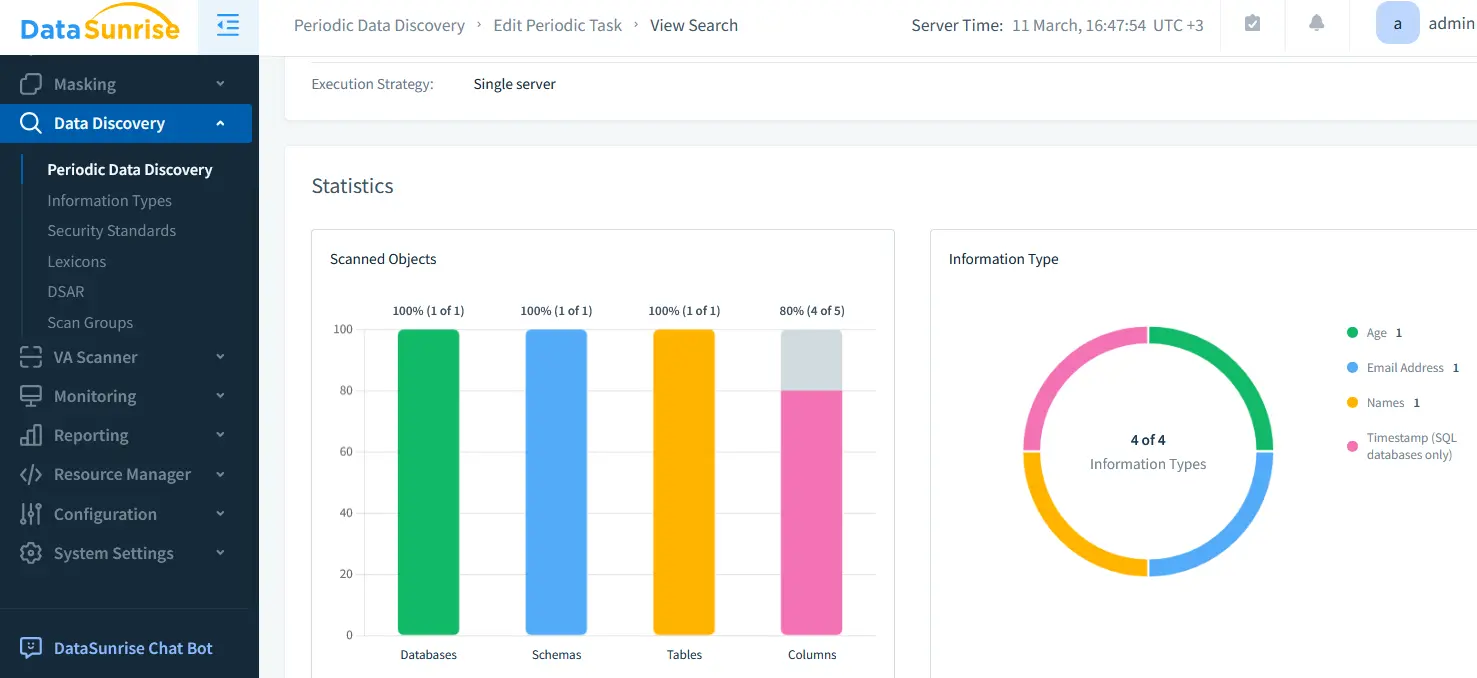
Automated Data Discovery Process
- Step 1: Identify sensitive data columns (e.g., PII, PHI).
- Step 2: Apply tagging for classification.
- Step 3: Enforce access controls based on classification levels.
Security and Compliance Controls
DataSunrise provides a comprehensive security layer for Aurora MySQL, offering features like database firewall, vulnerability assessments, and automated security policies. These functionalities ensure that organizations maintain strict access control and prevent unauthorized data access.
Data security in Aurora MySQL relies on multi-layered protection, including encryption, role-based access control, and automated policy enforcement. 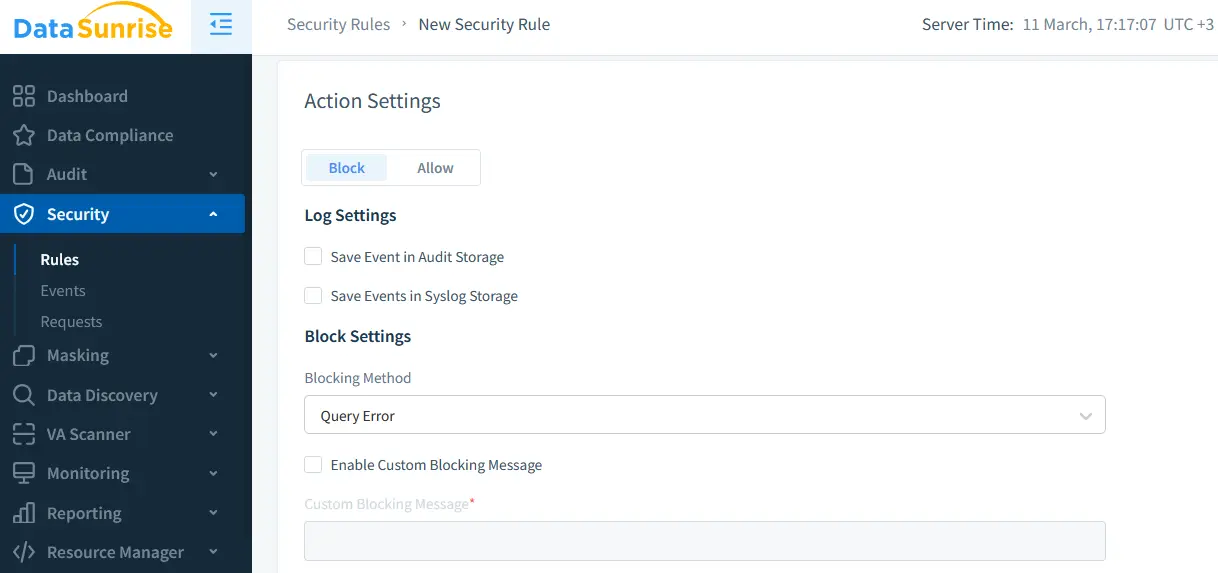
Role-Based Access Control (RBAC)
DataSunrise enhances Aurora MySQL’s RBAC capabilities by allowing administrators to define granular access rules. These rules can be applied dynamically, adjusting access privileges based on user roles and real-time behavior analytics. More on RBAC.
Compliance with Global Regulations
DataSunrise’s Compliance Manager automates compliance validation by continuously scanning Aurora MySQL databases for regulatory adherence. It provides:
- Automated reports for auditors.
- Real-time alerts for compliance deviations.
- Pre-configured templates for GDPR, HIPAA, and PCI DSS.
Aurora MySQL must comply with various regulatory frameworks, such as:
Using automated policy enforcement tools, like DataSunrise’s Compliance Manager, simplifies regulatory adherence.
Real-Time Security Threat Detection
DataSunrise employs AI-driven security analytics to detect anomalies in real-time. It leverages behavioral analysis and machine learning to identify suspicious activity, such as unauthorized access attempts or unusual data exfiltration patterns.
AI-Powered Threat Detection
- Uses machine learning models to identify deviations from normal database activity.
- Provides instant threat notifications and risk assessment reports.
- Allows integration with SIEM tools for centralized security monitoring.
Aurora MySQL security must include proactive threat detection mechanisms. Behavioral analytics and AI-driven anomaly detection help identify suspicious activities.
Conclusion
Aurora MySQL Data Governance requires a comprehensive approach integrating real-time auditing, dynamic masking, data discovery, and security compliance. Organizations can enhance security and streamline compliance by leveraging automated tools and policy-driven controls.
To see these capabilities in action, request a DataSunrise Demo.
For more information, visit:
