
Aurora PostgreSQL Audit Tools

Introduction
In today's security-conscious environment, database audit capabilities are no longer optional but essential components of any data governance strategy. With increasing regulatory requirements like GDPR, HIPAA, PCI DSS, and SOX, organizations must implement robust audit mechanisms for their Amazon Aurora PostgreSQL databases.
According to Verizon's 2024 Data Breach Investigations Report, system intrusions and unauthorized access remain significant threats across industries. This underscores the importance of implementing comprehensive audit solutions for your database environments.
This guide explores the various audit tools available for Amazon Aurora PostgreSQL, comparing their features, implementation approaches, and best use cases.
Native Aurora PostgreSQL Audit Tools
Out of the box, Aurora PostgreSQL does provide several built-in audit tools to track database activity. In this section, we'll briefly go over each of them.
Standard PostgreSQL Logging
Aurora PostgreSQL inherits the core logging capabilities of PostgreSQL, which offer basic auditing features through configuration parameters:
-- Common audit-related PostgreSQL parameters
log_statement = 'all' -- Log all SQL statements
log_connections = on -- Log all connection attempts
log_disconnections = on -- Log when a session ends
log_duration = on -- Log the duration of statements
log_min_duration_statement = 0 -- Log all statement durations
These parameters can be configured through the AWS RDS Parameter Group associated with your Aurora PostgreSQL cluster.
Limitations of Standard Logging
While useful, standard PostgreSQL logging has several limitations:
- Limited granularity and filtering options
- Performance impact at higher logging levels
- No built-in separation of duties
- Limited compliance capabilities
pgAudit Extension
The PostgreSQL Audit Extension (pgAudit) significantly enhances the native audit capabilities of PostgreSQL by providing detailed session and object audit logging.
Key Features
- Session audit logging (user statements)
- Object audit logging (operations on specific objects)
- Customizable audit classes
- Support for object-level and statement-level logging
Implementation
As detailed in the AWS Database Blog, implementing pgAudit involves:
Enable the extension in your parameter group:
shared_preload_libraries = 'pgaudit'Create the extension:
CREATE EXTENSION pgaudit;Configure audit settings:
-- Instance level (via parameter group) pgaudit.log = 'DDL,ROLE,WRITE,READ' -- Database level ALTER DATABASE your_database SET pgaudit.log = 'DDL,ROLE'; -- Role level ALTER ROLE your_role SET pgaudit.log = 'WRITE,READ';
Sample Audit Log
2024-02-24 15:27:43.154 UTC:[15432]:LOG: AUDIT: SESSION,25,1,WRITE,INSERT,TABLE,public.customer,"INSERT INTO customer (id, name) VALUES (1, 'John Smith')",<not logged>
AWS Database Activity Streams
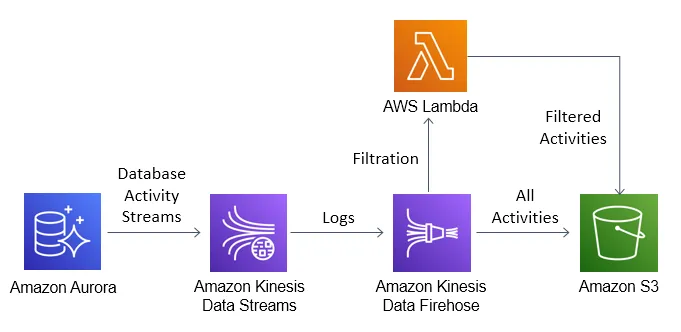
Key Features
- Near real-time activity monitoring
- Integration with AWS services (Kinesis, Lambda, etc.)
- Encrypted with AWS KMS
- Separation of duties between DBAs and security personnel
Implementation
Enabling Database Activity Streams involves:
Configure prerequisites:
- Set up NAT gateway in your VPC
- Configure AWS KMS endpoint
- Set up appropriate IAM permissions
Enable the feature:
AWS Console > RDS > Databases > [Your Aurora Cluster] > Actions > Start database activity streamConfigure stream processing:
- Create Kinesis Data Firehose delivery stream
- Set up Lambda for processing
- Configure S3 for storage
- Set up alerting via CloudWatch and SNS
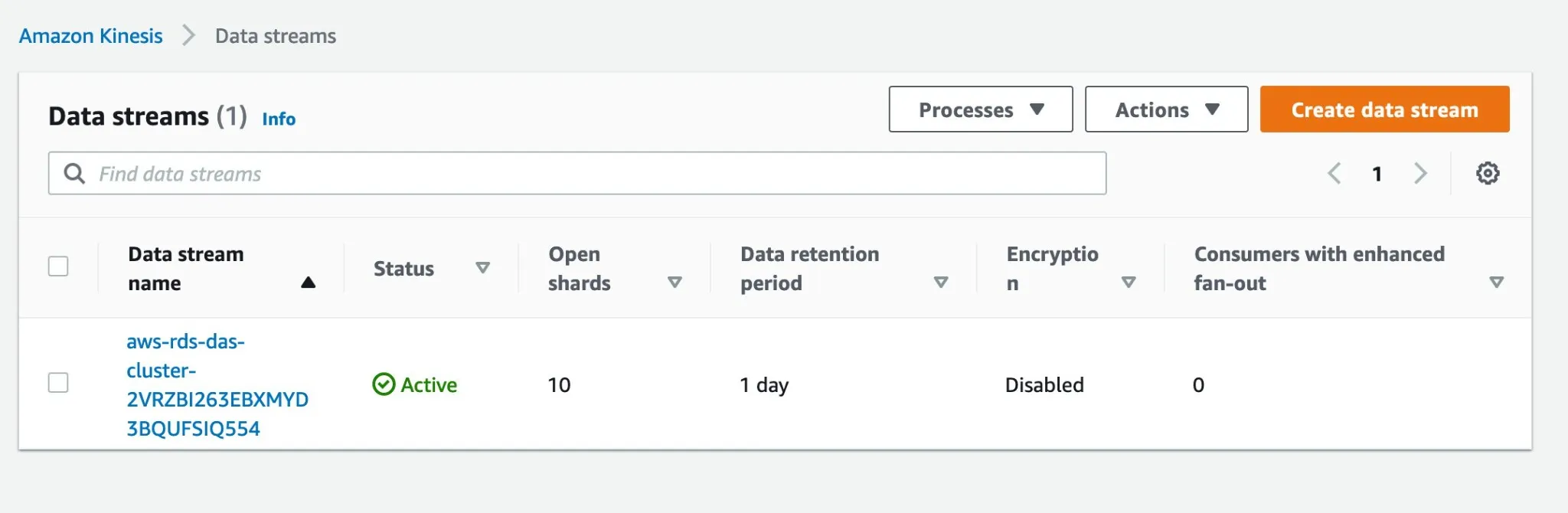
Integration Example
For a detailed implementation guide, see AWS's step-by-step tutorial which covers:
- Creating Lambda functions to process and alert on stream data
- Setting up S3 buckets for long-term storage
- Configuring CloudWatch and SNS for alerting
DataSunrise Audit Solution
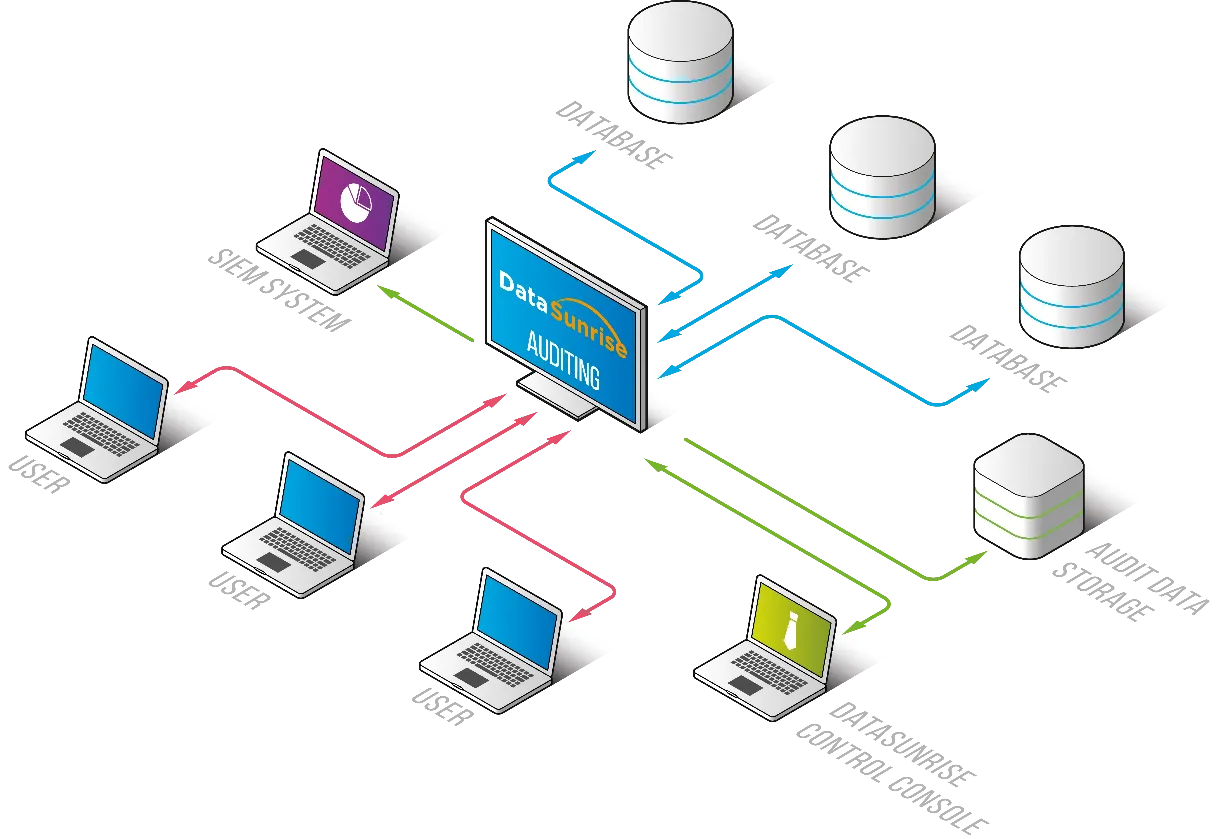
For organizations requiring advanced audit capabilities beyond native tools, DataSunrise offers a comprehensive third-party solution.
Key Features
- Centralized audit management across database platforms
- Advanced filtering and rule-based auditing
- Compliance reporting and alerting
- Behavior analytics and anomaly detection
- Integration with SIEM solutions
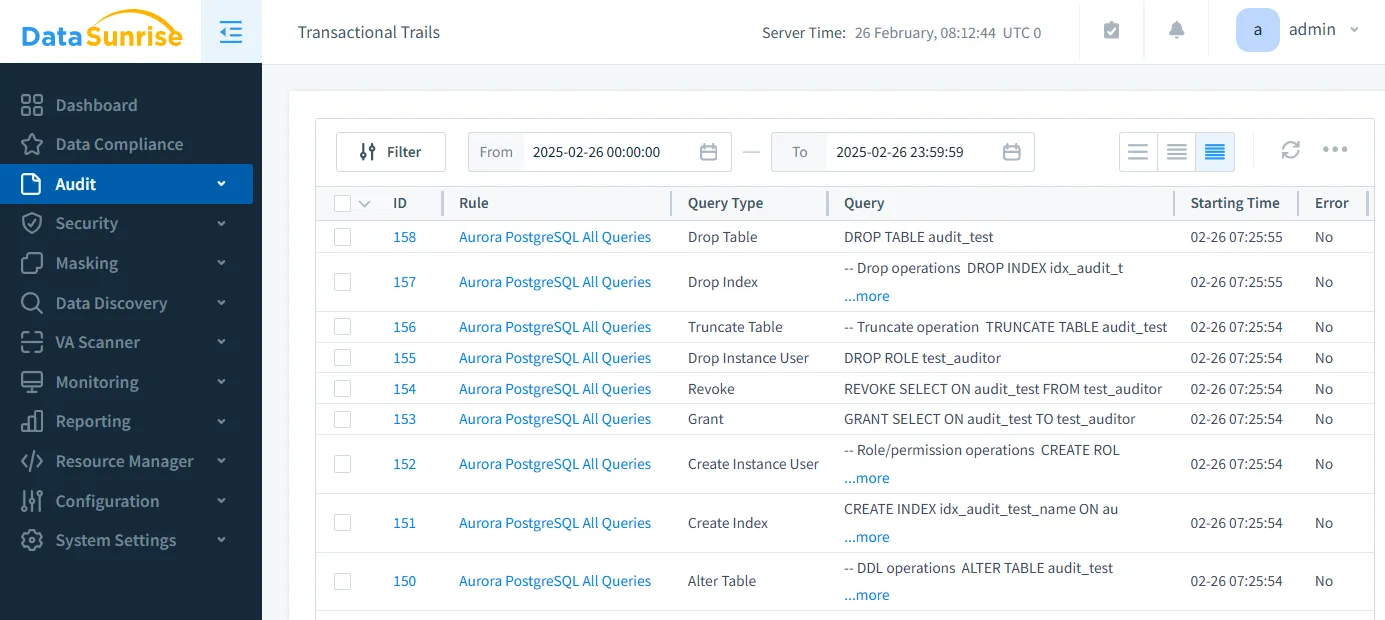
Advanced Features
DataSunrise extends beyond basic auditing with:
- User Behavior Analysis for detecting anomalies
- Automated Compliance Reporting for regulatory requirements
- Dynamic Data Masking for sensitive information
- Integration with over 40 data platforms for unified security
Comparison of Aurora PostgreSQL Audit Tools
| Feature | Standard Logging | pgAudit | Database Activity Streams | DataSunrise |
|---|---|---|---|---|
| Implementation Complexity | Low | Low | Medium | Medium |
| Detail Level | Basic | High | High | Very High |
| Performance Impact | Medium | Low-Medium | Low (Async) | Low |
| Real-time Monitoring | No | No | Yes | Yes |
| Separation of Duties | No | No | Yes | Yes |
| Compliance Reporting | Manual | Manual | Manual | Automated |
| Cost | Free | Free | AWS Service Costs | License |
| Integration with AWS | Native | Native | Native | Third-party |
| Multi-database Support | No | No | No | Yes |
Implementation Strategy and Best Practices for Aurora PostgreSQL Audit Tools
A comprehensive audit strategy often employs multiple tools in combination:
- Base Layer: Enable standard PostgreSQL logging for general troubleshooting
- Detail Layer: Implement pgAudit for detailed SQL-level auditing
- Security Layer: Use Database Activity Streams for real-time security monitoring
- Compliance Layer: Consider DataSunrise for advanced compliance requirements
Performance Considerations
- Monitor CPU and I/O impact of audit logging
- Use appropriate filtering to limit audit scope
- Consider asynchronous modes where available
- Implement log rotation and archiving strategies
Security Best Practices
- Implement separation of duties for audit logs
- Encrypt audit data at rest and in transit
- Use least-privilege principles for audit access
- Establish regular audit log review procedures
Regulatory Compliance
Different audit tools support various compliance requirements:
| Regulation | Key Requirements | Recommended Tools |
|---|---|---|
| GDPR | Access tracking, Data protection | pgAudit + DataSunrise |
| HIPAA | Access controls, Activity monitoring | Database Activity Streams + DataSunrise |
| PCI DSS | User tracking, Change monitoring | pgAudit + Database Activity Streams |
| SOX | Change control, Access verification | Database Activity Streams + DataSunrise |
Conclusion
Selecting the right audit tools for your Amazon Aurora PostgreSQL environment depends on your specific requirements for security, compliance, and operational monitoring. For many organizations, a multi-layered approach combining native PostgreSQL logging, pgAudit, Database Activity Streams, and third-party solutions like DataSunrise provides the most comprehensive coverage.
By implementing the appropriate audit tools and following best practices, organizations can ensure they meet regulatory requirements while maintaining visibility into their database environments. To see how DataSunrise can enhance your Aurora PostgreSQL audit strategy, schedule a demo today.
