Azure SQL Audit Trail
In today’s complex cybersecurity landscape, implementing robust audit trails has become essential for organizations managing sensitive data in cloud environments. According to Cybersecurity Ventures’ 2024 Annual Cybercrime Report, global cybercrime costs are projected to reach $10.5 trillion annually by 2025, highlighting the critical importance of comprehensive database monitoring solutions for platforms like Azure SQL.
As organizations migrate their database workloads to the cloud, maintaining detailed activity history through Azure SQL audit trails provides essential visibility into database operations. Microsoft Azure SQL Database offers native auditing capabilities that enable organizations to track and monitor database activities effectively, supporting both security monitoring and compliance requirements.
This article explores Azure SQL’s native audit trail features and examines how third-party solutions can enhance these capabilities for enterprise environments requiring advanced security monitoring.
Understanding Azure SQL Audit Trail
An Azure SQL audit trail is a chronological record of database operations that documents who accessed what data, when they accessed it, and what changes were made. This comprehensive activity log serves multiple critical functions:
- Security Monitoring: Detecting unauthorized access attempts and suspicious activities
- Compliance Documentation: Meeting regulatory requirements for data governance (GDPR, HIPAA, SOX, etc.)
- Incident Investigation: Providing forensic evidence in case of security breaches
- Operational Insights: Understanding database usage patterns and optimizing performance
Unlike traditional on-premises databases that often require extensive configuration, Azure SQL Database provides built-in auditing functionality that can be enabled with minimal setup, offering a streamlined approach to database activity monitoring.
Native Azure SQL Audit Trail Capabilities
Azure SQL Database includes robust native auditing features that allow organizations to implement comprehensive audit trails without third-party tools. These capabilities are available through the Azure portal, PowerShell, REST API, or T-SQL commands.
1. Types of Auditing in Azure SQL
Azure SQL offers two primary auditing types:
SQL Database Auditing: Records database events to Azure Storage, Log Analytics workspace, or Event Hub.
SQL Server Audit (Extended Events): More granular auditing using SQL Server’s extended events architecture.
2. Enabling Azure SQL Auditing
Enabling auditing in Azure SQL can be accomplished through several methods:
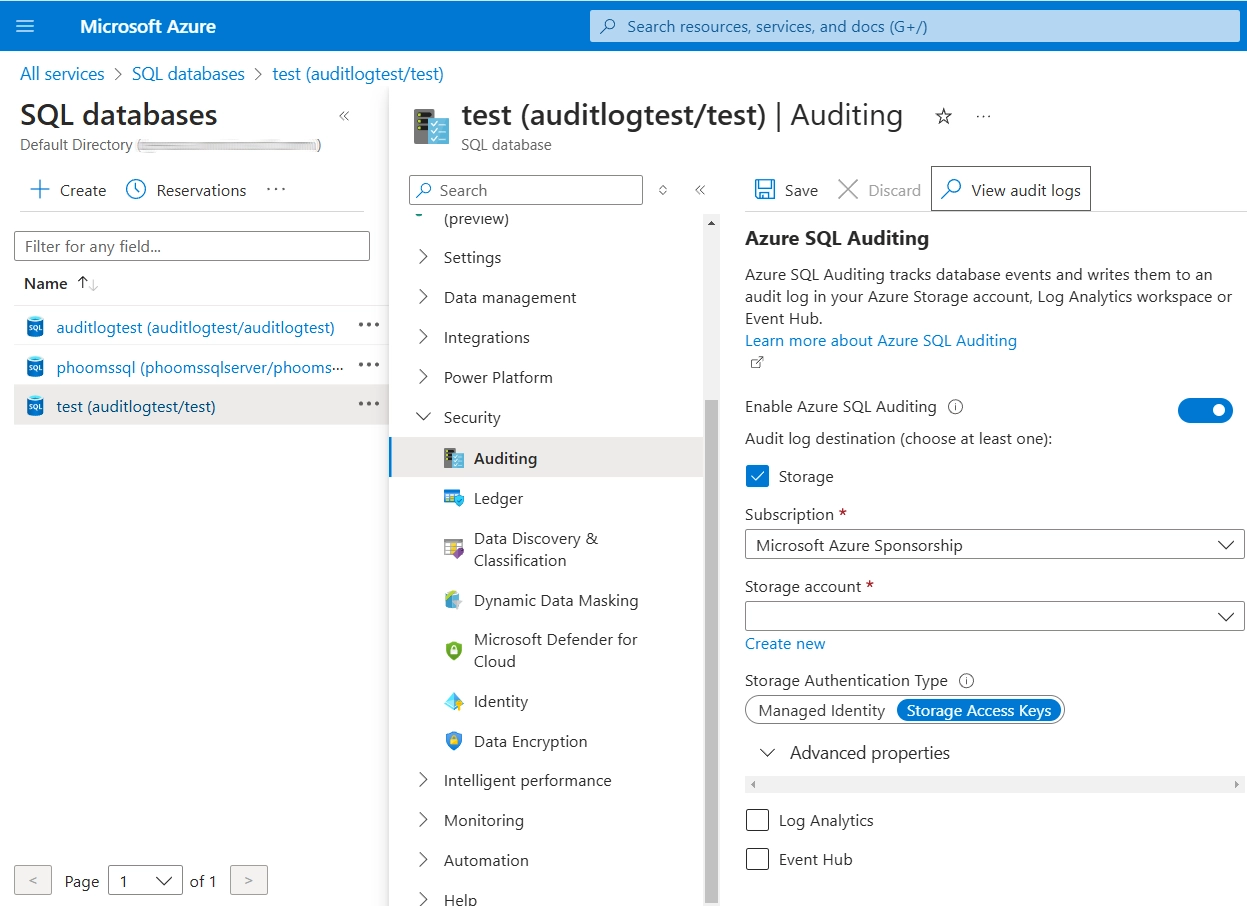
Azure Portal Configuration:
- Navigate to your Azure SQL database in the Azure portal
- Select “Auditing” under the Security section
- Set “Auditing” to “ON”
- Choose a storage destination (Azure Storage, Log Analytics, or Event Hub)
- Configure audit log retention period
- Save the configuration
PowerShell Example:
# Enable auditing for an Azure SQL database
Set-AzSqlDatabaseAudit -ResourceGroupName "myResourceGroup" `
-ServerName "myServer" `
-DatabaseName "myDatabase" `
-State Enabled `
-StorageAccountName "myStorageAccount" `
-RetentionInDays 90
3. Key Audit Event Categories
Azure SQL Database can audit various event categories, including:
| Event Category | Description | Example Events |
|---|---|---|
| Database Management | Database-level operations | CREATE/ALTER/DROP DATABASE |
| Schema Changes | Table and object definitions | CREATE/ALTER/DROP TABLE, INDEX |
| Data Access | Data manipulation operations | SELECT, INSERT, UPDATE, DELETE |
| Security Management | Authentication and authorization | GRANT, DENY, REVOKE, LOGIN FAILURES |
| Administrative Actions | Server configurations | BACKUP, RESTORE, DBCC commands |
Example audit log entry (simplified format):
{
"event_time": "2024-02-20T14:35:21.7411148Z",
"action_id": "SELECT",
"succeeded": true,
"server_principal_name": "user@example.com",
"database_name": "SalesDB",
"schema_name": "Sales",
"object_name": "Customers",
"statement": "SELECT * FROM Sales.Customers WHERE CustomerID = 1000",
"additional_information": {
"client_ip": "198.51.100.5",
"application_name": "Power BI"
}
}
4. Viewing and Analyzing Azure SQL Audit Logs
Azure SQL audit logs can be accessed and analyzed through multiple methods:
Azure Portal: Navigate to your SQL server or database, select “Auditing” under Security, and click “View audit logs” to filter specific events.
Log Analytics and Azure Monitor: For audits directed to Log Analytics, use KQL queries to analyze audit data and create custom dashboards.
PowerShell: Retrieve audit records programmatically for integration with other systems.
5. Limitations of Native Azure SQL Auditing
While Azure SQL’s native auditing capabilities provide essential functionality, they have certain limitations:
- Limited real-time alerting capabilities
- Basic reporting interfaces requiring additional tools for advanced analysis
- Storage costs can increase significantly for high-volume databases
- Limited machine learning-based threat detection
- Configuration complexity when scaling across multiple databases
Enhanced Azure SQL Audit Trail with DataSunrise
While Azure SQL Database provides robust native auditing capabilities, organizations with advanced security and compliance requirements often need additional functionality. DataSunrise Database Security Suite offers enhanced audit trail capabilities specifically designed to complement and extend Azure SQL’s native features.
Key Features of DataSunrise for Azure SQL
1. Comprehensive Audit Rules: Define granular audit policies based on users, queries, objects, and context.
2. Centralized Monitoring: Unified dashboard for monitoring activities across multiple Azure SQL databases and other database platforms.
3. Real-Time Alerting: Immediate notifications about suspicious activities via email, Slack, MS Teams, or custom webhooks.
4. Advanced Threat Detection: AI-powered behavioral analytics to identify anomalous patterns and potential security threats.
5. Automated Compliance Manager: Pre-built templates for GDPR, HIPAA, SOX, PCI DSS, and other regulations.
Setting Up DataSunrise for Azure SQL
- Connect to Azure SQL Database: Add your Azure SQL Database instance to DataSunrise by specifying the connection details and configuring authentication using SQL credentials or Azure AD.
- Create Audit Rules: Define specific tables and operations to monitor, set up custom filters for sensitive data, and configure compliance-specific auditing requirements.
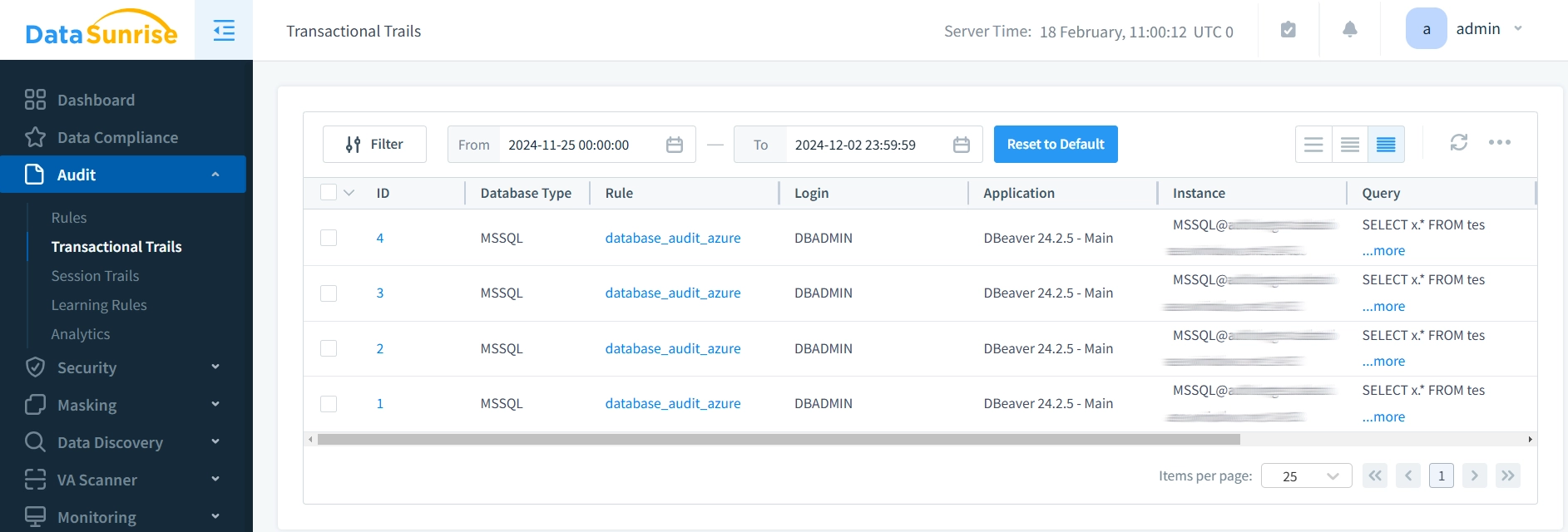
- Monitor Audit Trails: Access the “Transactional Trails” dashboard to view detailed event information, filter logs based on various criteria, and generate reports.
Advanced DataSunrise Capabilities
Dynamic Data Masking: Unlike Azure SQL’s built-in data masking which is static, DataSunrise provides context-aware dynamic masking that adapts based on user roles, location, and query patterns.
User Behavior Analytics: DataSunrise employs machine learning algorithms to establish baselines of normal user behavior and detect anomalies that might indicate compromised credentials or insider threats.
Cross-Platform Consistency: Organizations using multiple database platforms alongside Azure SQL benefit from DataSunrise’s ability to apply consistent security policies across diverse environments.
Best Practices for Azure SQL Audit Trail Implementation
1. Performance Optimization
- Selective Auditing: Audit only essential activities to minimize performance impact
- Storage Tier Selection: Choose appropriate storage tiers based on access frequency and retention requirements
- Partition Management: Implement partitioning for large audit datasets to improve query performance
2. Security Implementation
- Secure Storage: Ensure audit logs are stored in secured locations with appropriate access controls
- Database Encryption: Implement encryption for audit data both at rest and in transit
- Separation of Duties: Ensure audit administrators cannot modify the logs they oversee
3. Compliance and Documentation
- Retention Policies: Define clear retention periods based on regulatory requirements
- Documentation: Maintain detailed records of audit configurations and procedures
- Regular Validation: Periodically test audit log completeness and accuracy
4. Monitoring and Analysis
- Regular Reviews: Establish scheduled audit log review procedures
- Automated Alerting: Configure real-time alerts for suspicious activities
- Visualization: Create dashboard visualizations for security metrics and compliance status
5. Third-Party Integration
- Enhanced Security Solutions: Implement third-party solutions like DataSunrise for advanced audit capabilities
- SIEM Integration: Connect audit logs to Security Information and Event Management systems
- Multi-Channel Alerting: Configure additional alert channels for security events
Conclusion
A well-implemented Azure SQL audit trail is essential for maintaining database security, ensuring regulatory compliance, and supporting operational excellence. While Azure SQL’s native auditing features provide a solid foundation, organizations with advanced requirements benefit from specialized solutions that enhance these capabilities.
DataSunrise offers flexible, cutting-edge database security tools that extend beyond basic auditing. With features like dynamic data masking, AI-powered behavioral analytics, and automated compliance reporting, DataSunrise provides comprehensive protection against both external threats and insider risks across multiple database environments.
Visit the DataSunrise website today to schedule an online demo and discover how our advanced security solutions can strengthen your Azure SQL database protection strategy.
