
Azure SQL Data Audit Trail

In today’s data-driven landscape, implementing robust audit trails for Azure SQL Database has become essential. The IBM Cost of a Data Breach Report 2024 indicates organizations with proper audit logs identify breaches 75 days faster, reducing costs by up to 31%. Microsoft’s Security Intelligence Report shows database-targeted attacks increased by 67% in the past year, emphasizing the need for comprehensive database activity monitoring solutions.
This article explores Azure SQL Database’s native audit trail features and how these capabilities can be enhanced with specialized tools like DataSunrise to provide enterprise-grade security monitoring.
Understanding Azure SQL Data Audit Trail
An Azure SQL data audit trail records database activities, showing who accessed what data, when, and what actions they performed. These logs support security monitoring, compliance documentation, forensic investigation, and performance optimization.
Azure SQL Database offers streamlined auditing that can be enabled with minimal setup while providing comprehensive activity tracking.
Native Azure SQL Data Audit Trail Capabilities
Azure SQL Database includes built-in auditing features configurable through the Azure portal, PowerShell, Azure CLI, or T-SQL commands.
1. Types of Auditing in Azure SQL
- SQL Database Auditing: Records events to Azure Storage, Log Analytics, or Event Hub
- SQL Server Audit (Extended Events): Offers more granular auditing with customizable filtering
2. Enabling Azure SQL Data Audit Trail
Azure Portal Configuration:
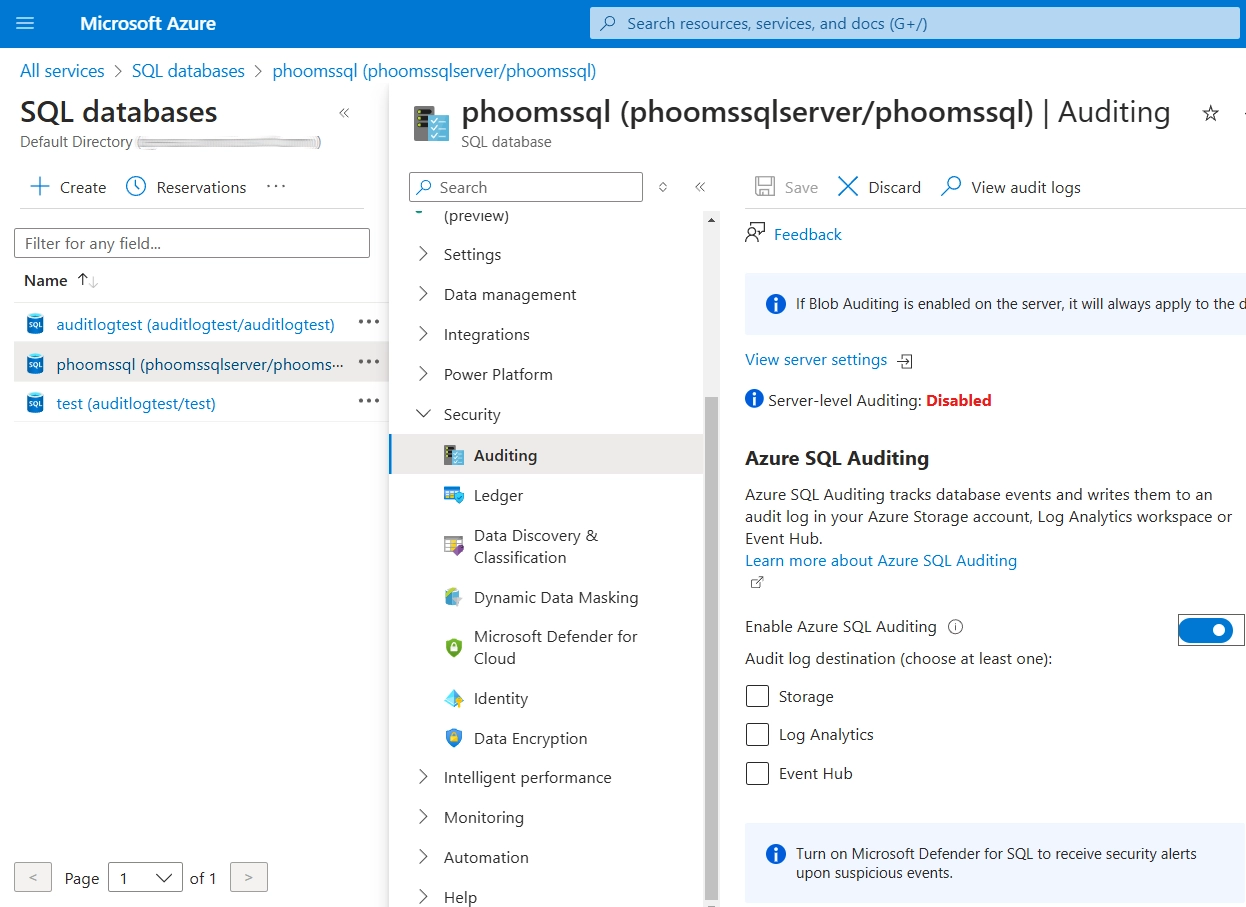
- Navigate to your Azure SQL database
- Select “Auditing” under Security
- Toggle “Enable Azure SQL Database auditing” to “ON”
- Choose your preferred audit log destination
- Configure audit log retention and actions to monitor
Azure PowerShell Example:
# Enable auditing for an Azure SQL database Set-AzSqlDatabaseAudit -ResourceGroupName "DataResourceGroup" ` -ServerName "sql-server-east" ` -DatabaseName "CustomerDatabase" ` -State Enabled ` -StorageAccountName "auditstorage" ` -RetentionInDays 90
Example output:
| ResourceGroupName | : DataResourceGroup |
| ServerName | : sql-server-east |
| DatabaseName | : CustomerDatabase |
| AuditState | : Enabled |
| StorageAccountName | : auditstorage |
| StorageKeyType | : Primary |
| RetentionInDays | : 90 |
| AuditActionsAndGroups | : {SUCCESSFUL_DATABASE_AUTHENTICATION_GROUP, FAILED_DATABASE_AUTHENTICATION_GROUP, BATCH_COMPLETED_GROUP} |
| IsStorageSecondaryKeyInUse | : False |
| IsAzureMonitorTargetEnabled | : False |
3. Key Audit Event Categories
Azure SQL can audit various events including authentication, data access, data modification, schema changes, permission changes, and administrative actions.
Sample audit log entry:
{
"event_time": "2024-03-15T10:22:36Z",
"action_id": "SELECT",
"succeeded": true,
"server_principal_name": "[email protected]",
"database_name": "FinanceDB",
"statement": "SELECT TransactionID, Amount FROM dbo.Transactions WHERE Amount > 10000"
}
Example audit results for data access queries:
| event_time | action_id | database_name | server_principal_name | object_name | succeeded |
|---|---|---|---|---|---|
| 2024-02-25T14:22:15Z | SELECT | CustomerDB | [email protected] | Customers | true |
| 2024-02-25T14:21:03Z | SELECT | FinanceDB | [email protected] | Transactions | true |
| 2024-02-25T14:15:47Z | UPDATE | CustomerDB | app_service | CustomerAddresses | true |
| 2024-02-25T14:10:32Z | INSERT | SalesDB | sales_app | Orders | true |
| 2024-02-25T14:08:19Z | DELETE | ArchiveDB | [email protected] | OldRecords | true |
4. Viewing and Analyzing Azure SQL Audit Logs
- Azure Portal: View filtered logs through the integrated log viewer
- Azure Storage Explorer: Browse and download log files for offline analysis
- Log Analytics: Use KQL queries to analyze audit data:
// Find failed login attempts in the last 24 hours AzureDiagnostics | where Category == "SQLSecurityAuditEvents" | where TimeGenerated > ago(24h) | where action_id_s == "FAILED_LOGIN"
Example output:
| TimeGenerated | server_principal_name_s | client_ip_s | application_name_s |
|---|---|---|---|
| 2024-02-25T09:12:36Z | [email protected] | 40.113.45.12 | Azure Data Studio |
| 2024-02-25T08:45:22Z | [email protected] | 52.187.30.45 | PowerBI |
| 2024-02-24T23:11:49Z | [email protected] | 104.45.67.89 | SQL Server Management Studio |
| 2024-02-24T19:27:15Z | [email protected] | 13.64.128.23 | SSMS 18.2 |
| 2024-02-24T17:03:52Z | sysadmin | 23.96.34.76 | .Net SqlClient |
5. Limitations of Native Azure SQL Auditing
Azure SQL’s native auditing has limitations in real-time alerting, cross-platform consistency, and advanced analytics. High-volume audit collection can lead to significant storage costs, and generating compliance reports often requires manual effort.
Enhanced Azure SQL Data Audit Trail with DataSunrise
DataSunrise Database Security Suite extends Azure SQL’s native audit capabilities for organizations with advanced security requirements.
Setting Up DataSunrise for Azure SQL
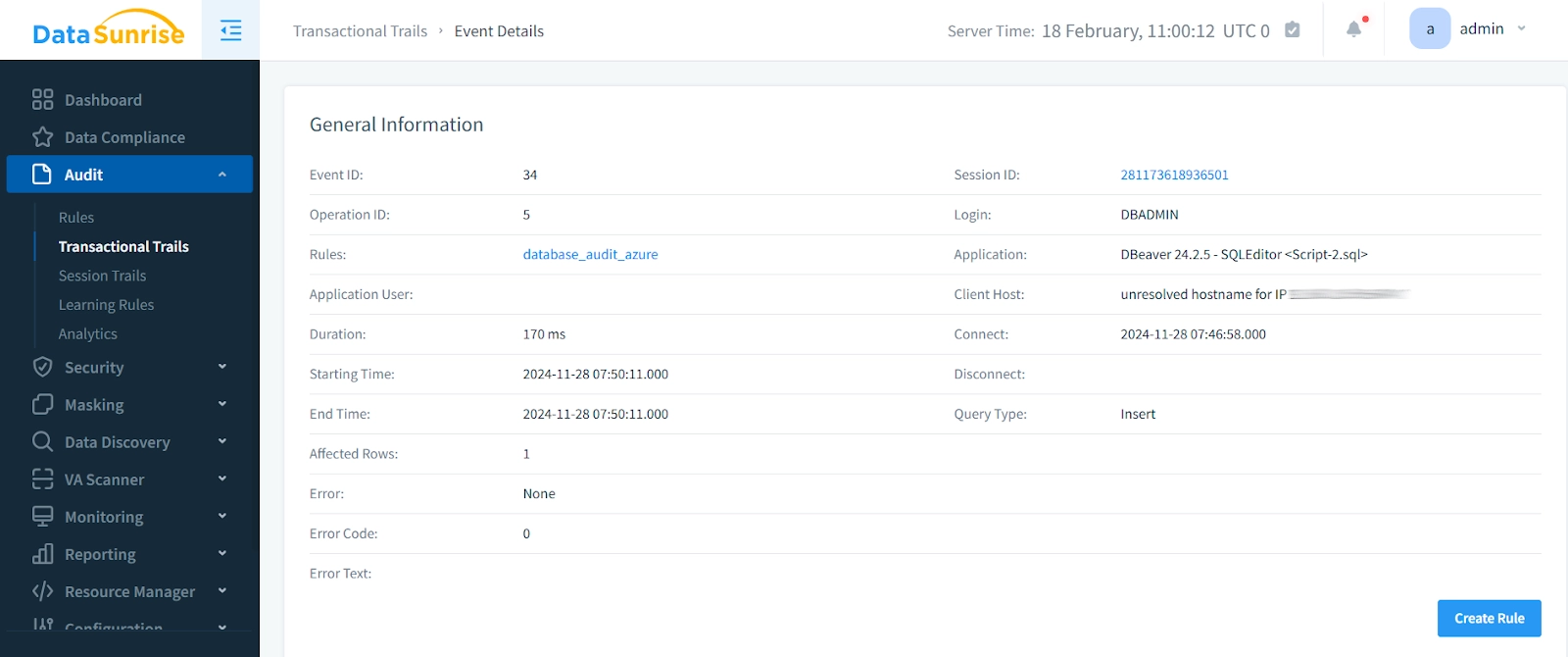
- Connect to your Azure SQL Database
- Create custom audit rules for specific tables and operations
- Monitor audit trails through the centralized dashboard
Key Advantages of DataSunrise for Azure SQL
1. Real-Time Monitoring and Alerting
DataSunrise provides immediate notifications about suspicious activities through customizable channels including email, Slack notifications, and MS Teams, with threshold-based alerting for anomalous patterns.
2. Advanced Security Analytics
The platform uses AI-powered behavioral analytics to establish baselines and detect anomalies, identifying sophisticated attack vectors that might go unnoticed in traditional systems.
3. Comprehensive Compliance Framework
Pre-configured templates for major regulations (GDPR, HIPAA, SOX, PCI DSS) simplify compliance, with automated reporting and gap analysis capabilities.
4. Dynamic Data Protection
Context-aware data masking adapts to user roles, while sensitive data discovery tools identify potential risks within databases.
5. Unified Management Console
Centralized control simplifies management across multiple database environments with consistent policy application.
Best Practices for Implementation
1. Performance Optimization
- Focus on auditing high-risk operations rather than all activities
- Allocate appropriate resources for audit collection and storage
- Optimize indexes on audit tables when using custom repositories
- Regularly review query performance to minimize system impact
2. Security Implementation
- Ensure audit administrators operate with minimum required permissions
- Implement end-to-end encryption for audit logs
- Configure immutable storage with write-once-read-many capabilities
- Establish strict access controls for audit log repositories
3. Compliance Management
- Maintain detailed documentation of audit configurations
- Align retention policies with regulatory requirements
- Regularly validate audit coverage and effectiveness
4. Monitoring and Analysis
- Establish scheduled audit log review procedures
- Create baselines for normal operations
- Develop protocols for investigating unusual patterns
5. Third-Party Solutions
- Consider specialized tools like DataSunrise for enhanced monitoring
- Leverage unified platforms for centralized security policy management
- Implement AI-driven analytics for threat detection
- Utilize automated compliance reporting capabilities
Conclusion
A well-implemented Azure SQL data audit trail is essential for security, compliance, and operational excellence. While Azure SQL’s native features provide a solid foundation, solutions like DataSunrise extend these capabilities with real-time monitoring, intelligent analytics, and automated compliance reporting.
By combining native capabilities with specialized tools, organizations can create a comprehensive audit ecosystem that addresses modern security threats while supporting regulatory compliance requirements.
To learn more about implementing advanced data audit solutions for your database environment, consider exploring DataSunrise’s demo to see these capabilities in action.
