
Cassandra Audit Trail: Secure Your Database with Advanced Monitoring

Data security and compliance are critical concerns for modern databases, especially when sensitive data is involved. Cassandra Audit Trail, introduced in Apache Cassandra 4.0, provides a robust solution for logging and monitoring database activity. This feature enables organizations to meet regulatory requirements, ensure data integrity, and enhance overall security without impacting performance.
In this article, we will explore the native Cassandra Audit Trail, provide Python-based examples for setting up and analyzing audit logs, and briefly discuss the benefits of using DataSunrise for centralized auditing.
Native Cassandra Audit Trail
Overview of Audit Logging
Apache Cassandra’s native audit logging feature records all database activities on a per-node basis. It captures events such as CQL requests, authentication attempts, and authorization checks. Some key highlights include:
- Configurable Limits: Bounded heap memory usage and disk space to avoid performance bottlenecks.
- File-Based Logs: Logs are stored as file-based records in a local filesystem directory.
- Low Latency: Minimal impact on database operation latency.
- Customizable Settings: Configurable via the cassandra.yaml file or nodetool commands.
- Comprehensive Logging: Includes both successful and failed operations.
Configuring Audit Logging
To enable audit logging in Cassandra, modify the cassandra.yaml file under the audit_logging_options section:
audit_logging_options: enabled: true logger: - class_name: FileAuditLogger audit_logs_dir: /cassandra/audit/logs included_keyspaces: my_keyspace excluded_keyspaces: system, system_schema included_categories: AUTH, DDL, DML roll_cycle: HOURLY
After configuring, restart the Cassandra node to apply changes. Alternatively, you can enable logging dynamically using nodetool:
$ nodetool enableauditlog --included-categories AUTH,DDL --included-keyspaces my_keyspace
Viewing Audit Logs
Depending on the logger used, logs can be accessed directly as plain text or converted using the auditlogviewer tool:
$ auditlogviewer /cassandra/audit/logs --roll_cycle HOURLY
Each log entry contains information such as keyspace, operation type, user, source IP, and timestamp.
Python-Based Audit Log Analysis
Connecting to Cassandra
To interact with Cassandra in Python, use the cassandra-driver library:
from cassandra.cluster import Cluster
# Connect to Cassandra cluster
cluster = Cluster(['127.0.0.1'])
session = cluster.connect()
# Set keyspace
session.set_keyspace('my_keyspace')Inserting and Auditing Data
Insert sample data to generate audit logs:
# Create a table and insert data
session.execute("""
CREATE TABLE IF NOT EXISTS audit_test (
id UUID PRIMARY KEY,
name TEXT,
age INT
)""")
import uuid
session.execute("INSERT INTO audit_test (id, name, age) VALUES (%s, %s, %s)", (uuid.uuid4(), 'Alice', 30))Analyzing Logs
Use Python to parse and analyze audit logs:
import os
# Directory containing audit logs
log_dir = "/cassandra/audit/logs"
# Read and process log files
for log_file in os.listdir(log_dir):
with open(os.path.join(log_dir, log_file), 'r') as file:
for line in file:
if 'INSERT INTO' in line:
print("Audit Log Entry:", line)Using DataSunrise for Cassandra Auditing
Configuring DataSunrise
DataSunrise offers an advanced security suite that simplifies auditing for Cassandra. To set up auditing with DataSunrise:
- Create an Instance: Use the DataSunrise interface to add a Cassandra database instance.
- Enable Auditing: Navigate to the auditing section and enable rules for monitoring keyspaces and operations.
- Set Filters: Specify filters for sensitive data categories, users, or operations.
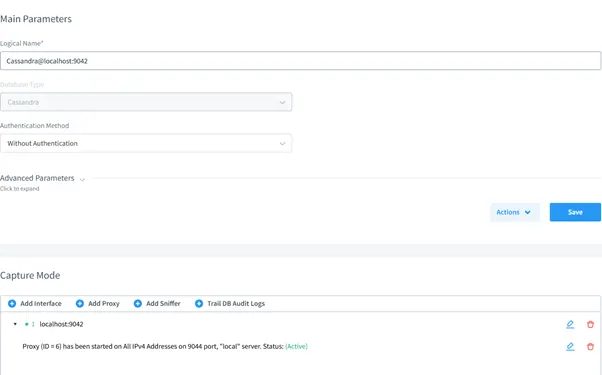
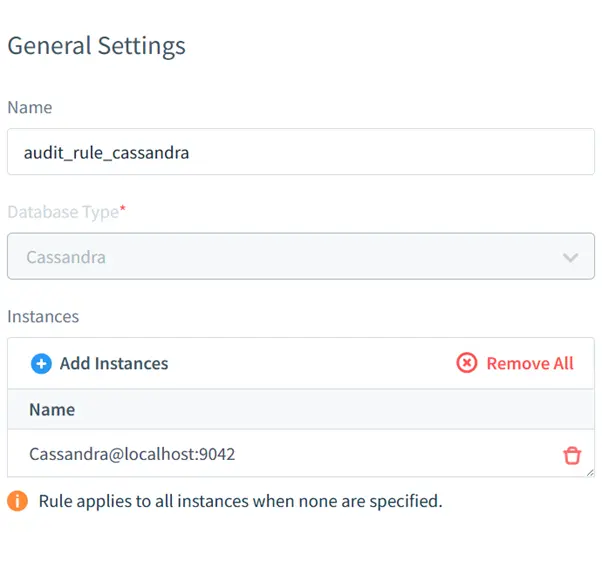
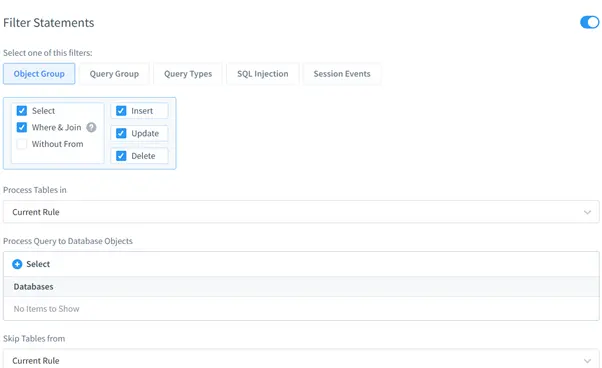
Result of Audit Rule Execution
Audit logs in DataSunrise present the outcomes of applied audit rules, allowing users to view and analyze captured data directly. These logs can also be exported for in-depth analysis and reporting.
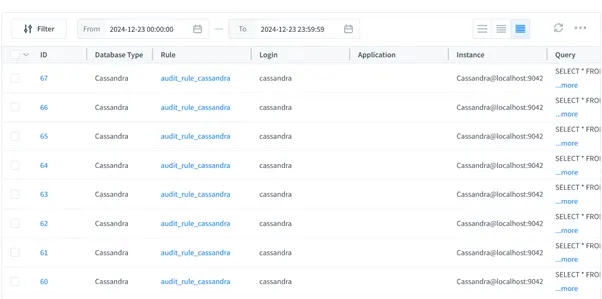
Benefits of DataSunrise
- Centralized Control: Manage audit rules across multiple databases.
- Compliance Ready: Preconfigured templates for regulatory compliance.
- Customizable Reports: Generate detailed reports tailored to organizational needs.
- Performance Optimization: Offloads audit processing from the database to reduce overhead.
Conclusion
The Cassandra Audit Trail is a powerful feature for logging and monitoring database activity, ensuring compliance and bolstering security. While native auditing is highly capable, tools like DataSunrise provide enhanced capabilities for centralized management and in-depth analysis.
Whether you choose native logging or a solution like DataSunrise, implementing a robust audit strategy is essential for safeguarding sensitive data. Visit theDataSunrise site to explore our security tools and schedule a online demonstration.
