
Cassandra Data Audit Trail: Best Practices for Security and Compliance

Data auditing is a critical feature for managing and securing sensitive data in modern databases. Apache Cassandra, a highly scalable NoSQL database, offers powerful native auditing capabilities that enable organizations to monitor and log activities on their data. This article explores the native Cassandra Data Audit Trail, demonstrates how to use Python for data auditing, and introduces DataSunrise’s advanced auditing tools.
Understanding Cassandra’s Native Audit Trail
Cassandra’s native auditing feature is designed to capture and log activities on sensitive data, ensuring transparency and compliance with security policies. The AuditLogOptions configuration allows you to fine-tune what is logged, including operations, users, and keyspaces. Below is an example configuration:
audit_logging_options: enabled: true logger: - class_name: FileAuditLogger audit_logs_dir: /var/log/cassandra/audit included_keyspaces: my_keyspace excluded_keyspaces: system, system_schema included_categories: AUTH, DDL, DML roll_cycle: HOURLY
Key Configuration Points:
- Enabled: Audit logging is active.
- Categories: Logs Data Definition Language (DDL) and Data Manipulation Language (DML) operations.
- Keyspaces: Focuses on test_keyspace, excluding system keyspaces.
- Logs Directory: audit logs are saved to /var/log/cassandra/audit.
Example: Inserting Data with Audit Logging
When an INSERT operation is executed, the audit log captures essential details:
INFO [Native-Transport-Requests-1] 2024-12-24 07:38:01,753 FileAuditLogger.java:51 - user:anonymous host:/172.17.0.2:7000 source:/127.0.0.1 port:45862 timestamp:1735025881749 type:UPDATE category:DML ks:test_keyspace scope:audit_test operation:INSERT INTO audit_test (id, name, age) VALUES (uuid(), 'Charlie', 35);
This log reveals:
- User and host details.
- Operation category and type.
- The affected keyspace and table.
- The exact query executed.
Implementing Native Audit Trail with Python
Python provides an efficient way to interact with Cassandra for auditing purposes. Below is a step-by-step guide:
Connecting to Cassandra
from cassandra.cluster import Cluster
# Connect to Cassandra cluster
proxy_host = 'localhost'
proxy_port = 9044
username = 'cassandra'
password = 'cassandra'
auth_provider = PlainTextAuthProvider(username, password)
cluster = Cluster([proxy_host], port=proxy_port, auth_provider=auth_provider)
session = cluster.connect()
session.set_keyspace('test_keyspace')
print("Connected to Cassandra")Setting Up Audit Logging
Audit logging is configured in cassandra.yaml with options like AuditLogOptions. To verify the configuration, use Cassandra’s logs:
grep 'AuditLog is enabled' /var/log/cassandra/system.log
Viewing Audit Results
Audit logs can be parsed programmatically:
import os log_dir = "/var/log/cassandra/audit" for file_name in os.listdir(log_dir): with open(os.path.join(log_dir, file_name), 'r') as log_file: for line in log_file: print(line.strip())
Example: Performing an Audited Operation
# Insert operation
session.execute("INSERT INTO audit_test (id, name, age) VALUES (uuid(), 'Alice', 30);")
print("Insert operation performed and logged.")The audit log will record this operation, including details such as the user, keyspace, and query.
DataSunrise: Enhanced Data Auditing for Cassandra
While Cassandra’s native auditing is robust, DataSunrise enhances auditing capabilities with centralized management and advanced filtering.
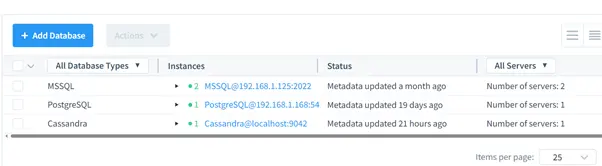
Adding a Cassandra Instance
- Open the DataSunrise Web Interface.
- Navigate to the Instances section and click Add Instance.
- Select Cassandra as the database type and provide connection details.
- Save the configuration.
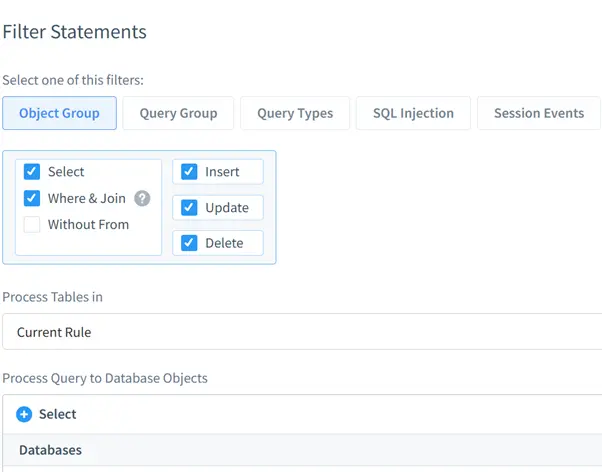
Configuring Audit Filters
DataSunrise offers flexible filters to tailor audits:
- Object Group: Focuses on specific tables or keyspaces.
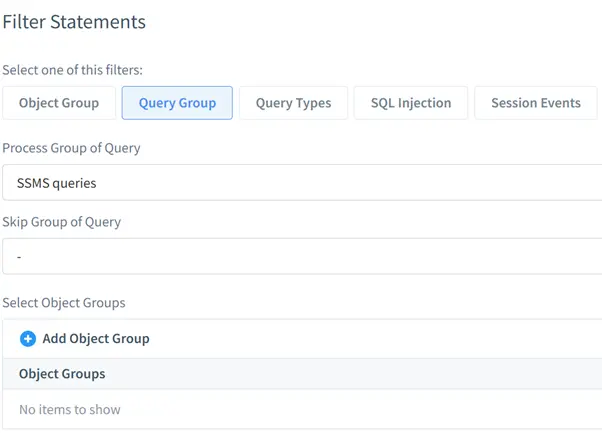
- Query Group: Captures queries matching defined patterns.
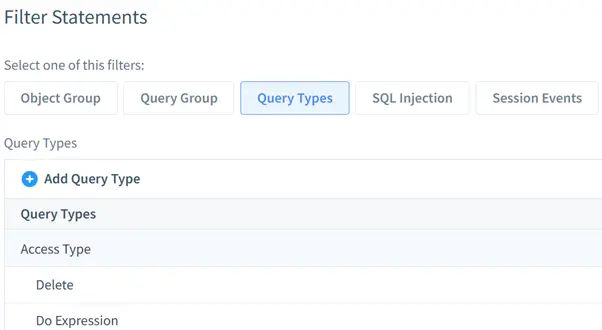
- Query Types: Logs DDL, DML, or both.
- SQL Injection: Identifies malicious query patterns.
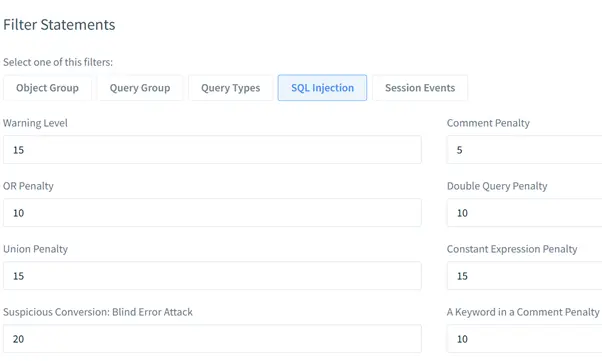
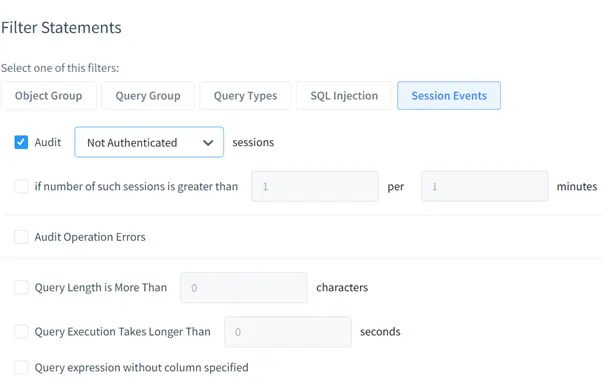
- Session Events: Tracks login and logout events.
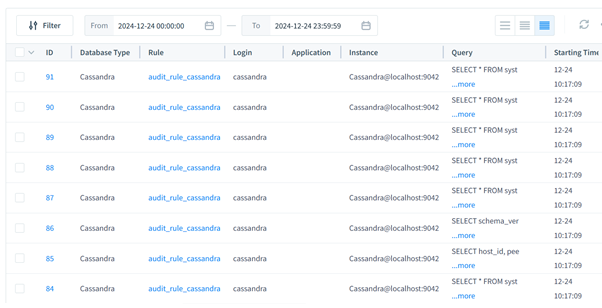
Viewing Audited Data
Audited data is accessible through the DataSunrise transactional trails page:
- Navigate to the Audit Logs section.
- Apply filters to refine log views.
- Export logs for further analysis.
Benefits of DataSunrise for Data Auditing
DataSunrise’s auditing suite offers:
- Centralized Control: Uniform management of audit rules across databases.
- Advanced Security: Detects anomalies and potential threats.
- Compliance Support: Helps meet regulatory requirements with detailed logs.
Conclusion
Auditing sensitive data is essential for database security and compliance. Cassandra’s native Data Audit Trail provides foundational tools for logging activities, while DataSunrise’s suite adds advanced features for centralized and flexible auditing. Together, they ensure robust data monitoring and security.
Discover more about DataSunrise’s capabilities and schedule an online demonstration on the official website.
