
Cassandra Database Activity History: Auditing, Compliance, and Security Best Practices

The need for stringent tracking and monitoring of sensitive data activities has never been greater, especially in modern distributed systems. Apache Cassandra, known for its scalability and reliability, provides robust mechanisms to oversee and audit database activities. Leveraging these capabilities ensures compliance, fortifies security, and offers valuable operational insights.
In this article, we will explore the features of Cassandra Database Activity History, detailing the setup process, native capabilities, and Python-based approaches for auditing. Furthermore, we will delve into the advantages of integrating third-party solutions like DataSunrise to elevate database auditing and security.
Native Auditing Capabilities in Cassandra
Cassandra’s built-in auditing functionality allows organizations to track database activities, ensuring compliance and security. By enabling native audit logging, administrators can gain insights into access patterns and operational changes across the database.
Steps to Enable Auditing
To configure auditing in Cassandra, you need to adjust the cassandra.yaml file.
Here’s a fresh example of audit logging setup:
audit_logging_options: enabled: true logger: FileAuditLogger included_keyspaces: \"user_data_keyspace\" excluded_keyspaces: \"system,system_distributed\" included_categories: \"DDL,DML\" excluded_categories: \"TRACE\" audit_logs_dir: \"/var/log/cassandra/user-audit-logs\" roll_cycle: \"HOURLY\" max_queue_weight: 262144000 max_log_size: 4294967296 block: false
Key Points:
- Enabled Logging: Activates auditing for specified keyspaces like transactions_keyspace.
- Operation Scope: Monitors DDL and DML operations while excluding system-level activities.
- Log Storage: Logs are saved in /var/log/cassandra/audit-logs for easy access.
Example Log Entry: SELECT Query
After enabling logging, the audit system captures detailed records of each operation. Here’s a sample log entry for a SELECT query:
INFO [Native-Transport-Requests-2] 2024-12-24 14:45:10,432 BinaryAuditLogger.java:57 - user:report_user host:/192.168.1.12:9042 source:/127.0.0.1 port:60134 timestamp:1735041910432 type:SELECT category:READ ks:transactions_keyspace scope:orders operation:SELECT * FROM orders WHERE order_date > '2024-01-01';
Interpreting Audit Data
- User: report_user—the individual executing the query.
- Action Type: SELECT query accessing the orders table.
- Timestamp: Exact time of the database operation.
Real-Time Monitoring of Audit Logs
Administrators can monitor activity logs in real-time using tools like tail:
tail -f /var/log/cassandra/audit-logs/audit.log
This approach provides immediate visibility into ongoing database operations for timely analysis and issue resolution.
Python Integration for Cassandra Auditing
Python offers an efficient way to automate and analyze Cassandra audit logs. Below is an example of using Python to interact with Cassandra and verify audit logs programmatically.
Installing Required Libraries
Ensure the Cassandra Python driver is installed:
pip install cassandra-driver
Script: Performing Database Operations
from cassandra.cluster import Cluster
from cassandra.query import SimpleStatement
# Connect to the Cassandra cluster
cluster = Cluster(["127.0.0.1"])
session = cluster.connect("audit_db")
# Execute a DDL operation
query = SimpleStatement("INSERT INTO user_logs (user_id, action, timestamp) VALUES (uuid(), 'login', toTimestamp(now()))")
session.execute(query)
print("Operation completed. Check audit logs for details.")
cluster.shutdown()Analyzing the Logs
After running the script, navigate to the audit logs directory and use command-line tools for analysis:
grep 'SELECT' /var/log/cassandra/audit-logs/audit.log
This ensures clear tracking of automated operations and supports auditing compliance goals.
Enhancing Cassandra Auditing with DataSunrise
DataSunrise extends Cassandra’s auditing capabilities by providing advanced monitoring, customizable security controls, and streamlined compliance solutions. Its centralized platform ensures all database activities are tracked and managed efficiently.
Configuring Cassandra in DataSunrise
- Access the DataSunrise dashboard and log in with your credentials.
- Navigate to the Configuration section and select Add New Instance.
- Enter the necessary database details, including the hostname, port number, and authentication credentials.
- Enable the auditing feature and save the configuration.
Setting Up Tailored Audit Policies
- Open the Policy Editor under the Auditing tab.
- Define rules to monitor specific operations such as INSERTS, UPDATES, or schema changes.
- Utilize filters to target users, keyspaces, or tables based on business needs.
- Activate the policies and begin tracking database activity.
Accessing and Filtering Audit Logs
Within the Audit Reports section, administrators can:
- View detailed logs of database operations.
- Use filters to sort logs by action type, timestamp, or user.
- Export logs for deeper analysis or compliance documentation.
Advantages of DataSunrise for Cassandra Auditing
DataSunrise enhances auditing capabilities with features like:
- Data Masking: Safeguard sensitive information as an additional layer of protection during audits.
- Security Rules: Define and enforce robust access controls.
- Centralized Audit Management: Streamline audit oversight for distributed systems.
- Data Discovery: Identify sensitive data across Cassandra clusters.
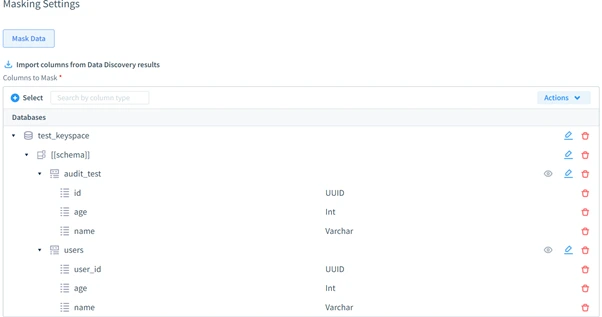
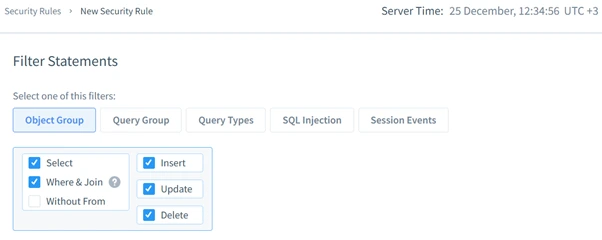
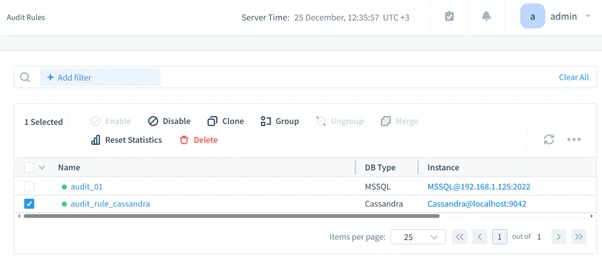
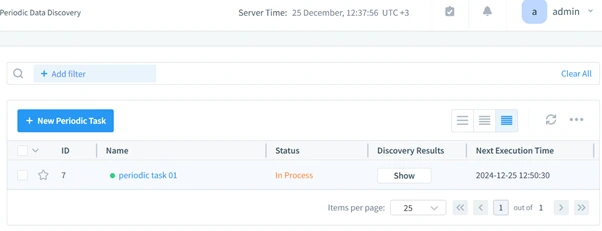
These features simplify compliance processes and elevate database security, making DataSunrise an essential tool for administrators.
Conclusion
Cassandra’s native auditing features provide a solid foundation for tracking database activities. Python integrations further simplify and automate these processes. For enterprises requiring advanced functionality, DataSunrise offers unparalleled tools for centralized management, security, and compliance.
Adopting these practices ensures robust governance over database operations, aligning with both organizational and regulatory standards.
To better understand how DataSunrise improves database security, visit thewebsite. You can explore features or schedule an online demonstration of our strong security suite.
