
Cloud Security
Contents:
- Navigating Challenges in Cloud Security
- Shared Responsibilities: Ensuring Cloud Security
- Innovative Approaches to Cloud Security
- DataSunrise: Enhancing Cloud Security
- Safeguarding Data in Transit
- Ensuring Encryption: SSL Keys for Frontend and Backend connections
- Exploring SSL Algorithms: Enhancing Security Measures
- Conclusion
Navigating Challenges in Cloud Security
Imagine a scenario where every piece of data you store or share online is vulnerable to unauthorized access and potential misuse. In today’s digital age dominated by cloud systems, this scenario is not just a possibility but a genuine concern. Cloud computing offers immense benefits in terms of convenience and connectivity, but it also brings along significant security challenges.
Securing cloud-based systems is all about protecting data in transit and at rest. Encryption is key to preventing unauthorized access during communication and storage. Yet, as cloud adoption grows, managing security becomes more complex. Threats evolve rapidly, urging both providers and users to stay alert and bolster defenses.
Cloud security involves various policies, technologies, and controls. It’s a joint responsibility of providers and users to maintain data integrity, confidentiality, and availability. Database administrators need to continuously exert efforts to tackle new vulnerabilities and emerging threats.
Regulatory bodies have introduced and reviewed multiple standards in recent years to accommodate the evolving market and establish new regulatory frameworks. However, you must ensure that the service you use complies with the regulations. What’s even more important is that customers still retain responsibility for data storage in cloud-based infrastructure. DataSunrise provides tools to enhance data security in such cases.
Shared Responsibilities: Ensuring Cloud Security
Shared responsibility in cloud computing is crucial as cloud services gain popularity. It clarifies security obligations between providers and users. Providers secure the infrastructure, while users protect data, applications, and access controls. This collaborative approach ensures comprehensive security across all cloud service levels, adapting to evolving threats and regulations.
This list includes the most famous general cloud platforms offering data storage:
Microsoft Azure (Shared Responsibility in the cloud)
Amazon Web Services (Shared Responsibility Model)
Google Cloud (Shared Responsibilities and Shared Fate on Google Cloud)
IBM Cloud (Shared Responsibilities for Using IBM Cloud Products)
Oracle Cloud Infrastructure (iaas, saas)
Digital Ocean (Shared Responsibility Model)
Alibaba Cloud (Shared Security Responsibility Model)
Each of these platforms provides a variety of services, including data storage options for businesses of all sizes. They offer both Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) solutions, with a range of pricing models, including free tiers and credits for new users. For specific shared responsibility descriptions, you can visit their official websites. The listing above provides the links.
Innovative Approaches to Cloud Security
Sometimes, data services offer enhanced shared responsibility, as is the case with Snowflake. This platform utilizes major general cloud platforms under the hood, operating on the platform concept. Limited infrastructure management elevates Snowflake’s security maintenance responsibility. AWS, Azure, and Google Cloud are popular platforms. They offer IaaS and PaaS solutions, giving users more control over their virtual infrastructure and applications. Consequently, users on these platforms enjoy greater autonomy but also bear more responsibility for configuring and securing their environments, including managing access controls, network security, and data encryption.
Understanding Snowflake’s Shared Responsibility Model
Some service providers do not construct their own cloud infrastructure. Instead, they rely on the security models of general cloud platforms. For instance, Neo4j runs on Google Cloud and Amazon Web Services. This essentially means that services like Neo4j Aura rely on the shared responsibility of Google Cloud and Amazon Web Services.
Cloud Data Security for Graph-Based Applications | Neo4j Cloud Security
The concept of shared responsibility extends to cloud subsystems or services such as Athena (for S3 querying with SQL) and Lambda (for code execution in response to triggers). With Lambda, securing the code against vulnerabilities and meticulously managing function permissions are crucial. The user has key responsibilities in controlling access to query data for Athena and securing the S3 buckets where data is stored and accessed from.
Cloud-based specific products may have a more precise shared responsibility model without the need for a matrix containing all variants of IaaS, PaaS, and SaaS. For example, VMware Cloud on AWS implements a shared responsibility model in a single table. It’s worth noting the common rule: the narrower the functionality and the more specific the cloud-based solution, the less responsibility falls on the user.
DataSunrise: Enhancing Cloud Security
DataSunrise helps protect data while working with cloud provider SaaS, IaaS, and PaaS in several ways:
Data Protection and Firewall: DataSunrise acts as a proxy between users and the server, ensuring the integrity and confidentiality of data by protecting against both internal and external threats.
Continuous Auditing: It performs continuous auditing of database activity, which is crucial for investigating potential data leaks and ensuring that all access and actions are monitored.
Dynamic Data Masking: DataSunrise offers dynamic data masking, which obscures sensitive data in real-time, ensuring that unauthorized users cannot view sensitive information even if they have access to the database.
24/7 Suspicious Behavior Monitoring: The system provides round-the-clock monitoring of database activity, ensuring that any suspicious behavior is detected and can be responded to immediately.
Data Compliance: DataSunrise helps organizations comply with various regulatory standards such as PCI-DSS, SOX, and HIPAA, which is essential for maintaining data security and privacy.
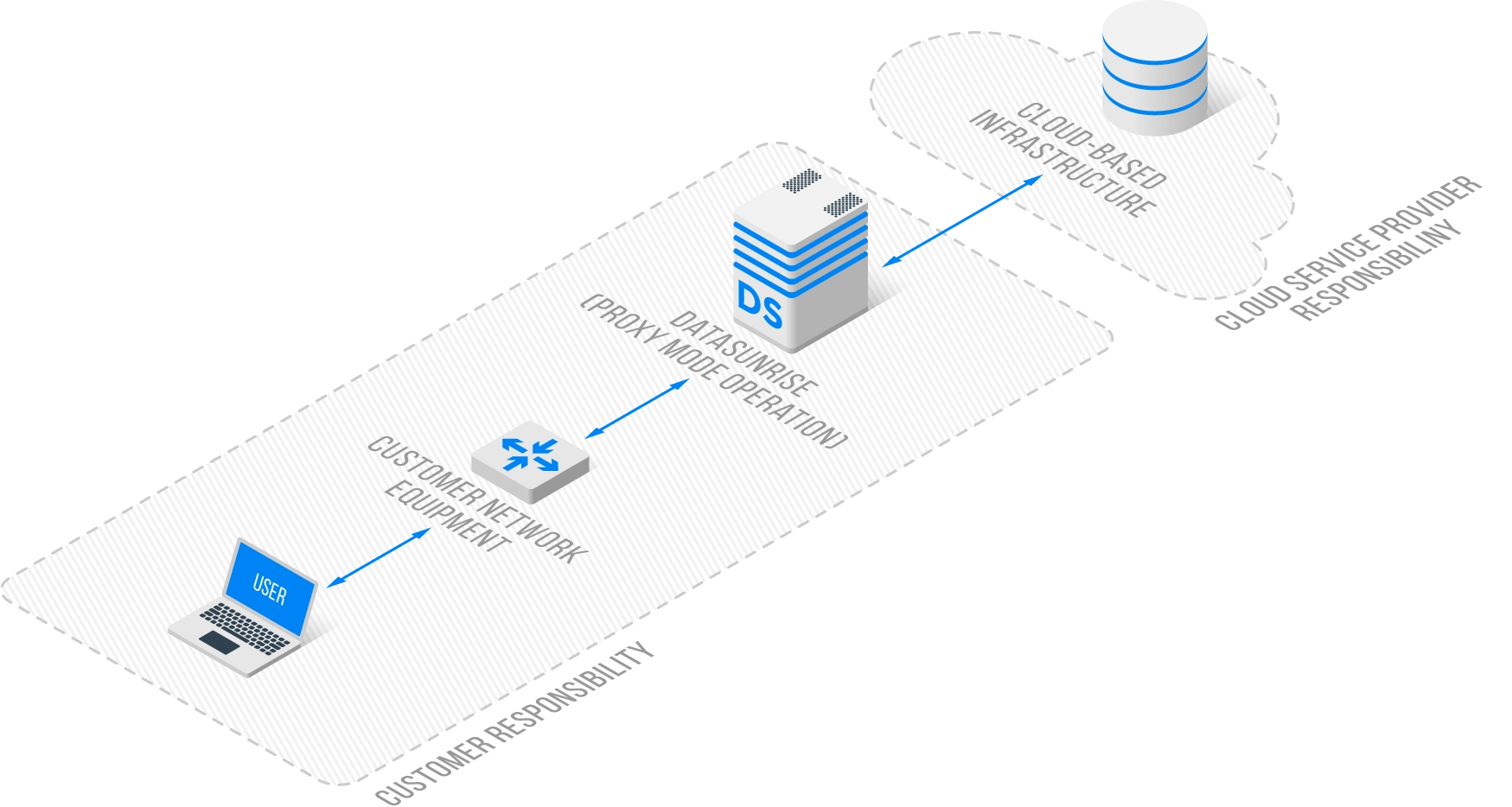
Non-Intrusive Deployment: The solutions provided by DataSunrise can be added to existing architectures, databases, or applications without requiring significant changes, allowing for a seamless integration of security measures. The DataSunrise is safe for the existing database in either of the three possible Operation Modes (Sniffer, Proxy and Audit).
Real-Time Threat Alerts and Subscribers: It provides real-time alerts for threats such as SQL injections, unauthorized access attempts, DDOS, and brute-force attacks.
Authentication: This feature adds additional layers of security by verifying user identities. Authentication in conjunction with TLS support provides the security of the data while it passes the interface parts of the architecture or when it is transferred over the Internet.
Obviously, most of the features above are common to any database, whether it is cloud-based or not. The specifics of the cloud infrastructure lie in remote access and remote storage. The key questions are as follows: Is my data safely stored? Is my data safely transmitted?
Safeguarding Data in Transit
Cloud-based solutions need data protection during transit. This means encrypting sensitive information to prevent interception and ensure confidentiality and integrity. This protection is crucial for compliance with data privacy regulations and for building trust with customers who expect secure management of their data. Additionally, securing data in transit helps to prevent potential data breaches and cyber attacks, which can have significant financial and reputational consequences for organizations.
DataSunrise ensures encryption of the data moving between the client and the server, providing a secure channel for data transmission and preventing unauthorized access or eavesdropping.
Ensuring Encryption: SSL Keys for Frontend and Backend connections
DataSunrise uses SSL Key Groups to store SSL certificates and private keys. Groups also contain other parameters for managing SSL connections. This lets DataSunrise treat all group elements as a single unit. SSL Key Groups facilitate the management of encryption keys and certificates. They ensure secure communication between clients and databases.
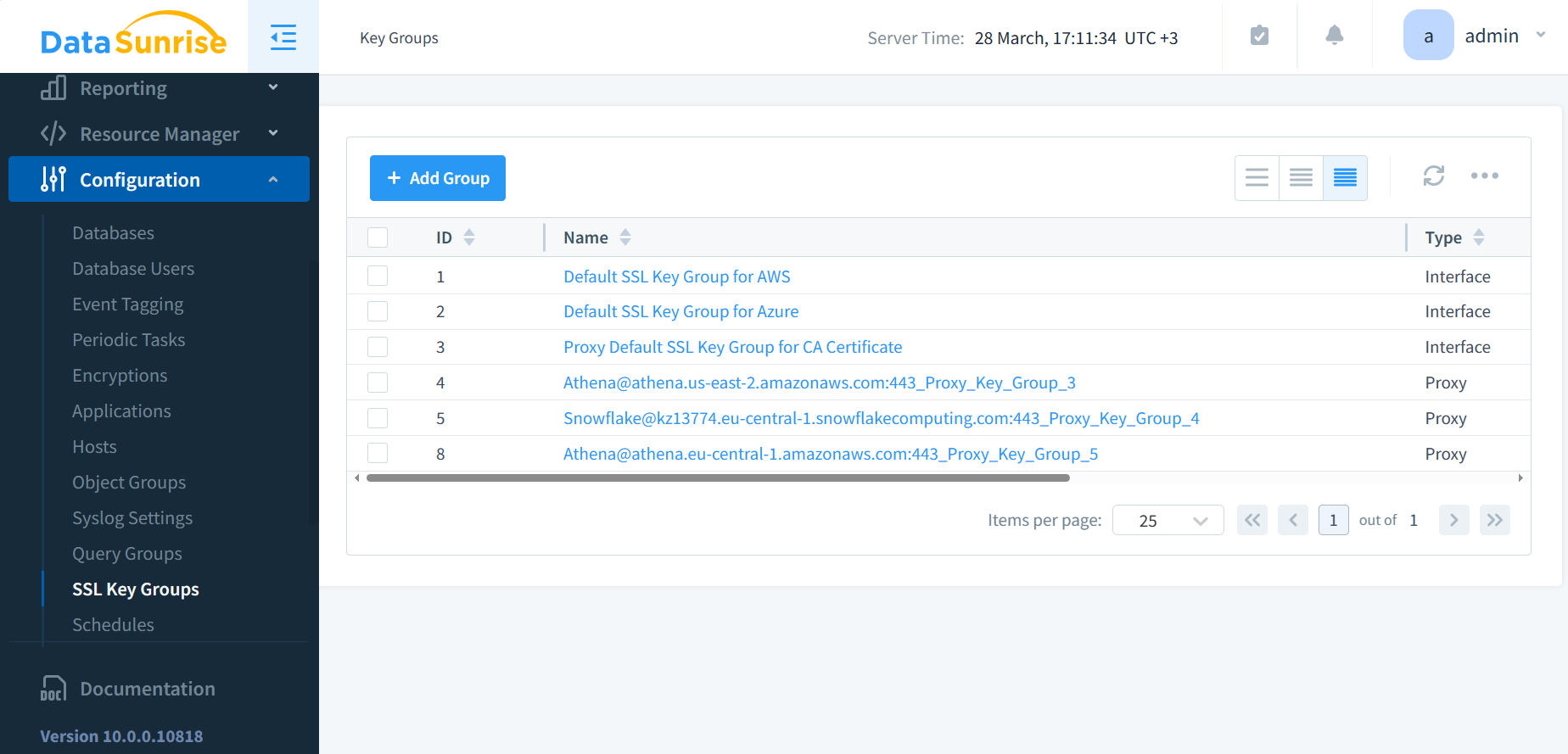
Figure 1: SSL Key Groups. DataSunrise enhances cloud security by safeguarding data during transit. When you create database Instances in the DataSunrise configuration, users have the option to create new SSL keys or reuse existing ones for communication with new proxies for those Instances.
The two types of keys, Interface and Proxy, serve different purposes within DataSunrise’s security framework:
Interface Key: This key is for a specific network interface within DataSunrise. You use it to identify and manage the network interface configurations that DataSunrise uses to communicate with the database instances. The Interface key ensures that the correct network settings are applied when DataSunrise interfaces with the database, which can include IP addresses, ports, and other network parameters.
Proxy Key: The Proxy key is for the proxy functionality of DataSunrise, which acts as an intermediary between the client and the database. This key ensures that the proxy can securely handle and inspect the database traffic, applying security rules, auditing, and potentially modifying queries.
Having separate keys for interfaces and proxies allows DataSunrise to distinctly manage network interfaces and proxy instances, providing granular control over different aspects of database traffic management and security.
Exploring SSL Algorithms: Enhancing Security Measures
The SSL Key Groups for proxy keys include ‘Diffie Hellman Parameters’ and ‘Elliptic Curve Diffie Hellman Parameters’ fields. These fields support different types of encryption algorithms that clients connecting to the proxy may utilize. Diffie-Hellman (DH) and Elliptic Curve Diffie-Hellman (ECDH) are key exchange protocols enabling secure communication over a public network. They allow the creation of a shared secret between two parties without transmitting it over the network. Including these parameters in the SSL Key Groups allows DataSunrise to accommodate a wider range of clients using these encryption methods, ensuring compatibility and secure connections.
Some SSL types don’t use DH or ECDH parameters. These types rely on other key exchange methods. Examples include RSA or pre-shared key mechanisms. If your applications or SSL configurations don’t use these suites, you don’t need DH or ECDH parameters.
The HTTPS connection with port 11000 for the DataSunrise Web UI utilizes TLSv1.2. This version of the SSL/TLS protocol secures the transmission of data between the client’s web browser and the DataSunrise Web Console. Users have the option to configure DataSunrise with either a self-signed certificate or a certificate from a Certificate Authority (CA) to establish a secure HTTPS connection on port 11000.
Conclusion
In conclusion, navigating the complex landscape of cloud security demands a proactive approach and a clear understanding of shared responsibilities. As cloud adoption surges, so does the imperative for robust security measures. Collaboration between providers and users remains pivotal, ensuring the integrity, confidentiality, and availability of data. Solutions like DataSunrise offer comprehensive protection against evolving threats, emphasizing the critical role of security technologies in safeguarding cloud environments. With diligence and innovation, organizations can fortify their defenses and mitigate risks, fostering trust and resilience in the realm of cloud security.
To learn more about DataSunrise’s solutions and see them in action, we invite you to connect with our team for an online meeting and live demo. Experience firsthand how DataSunrise can enhance your cloud security strategy.
