
Ensuring Robust Cloud Security: Proven Best Practices
The cloud has revolutionized how businesses operate, offering scalability, flexibility, and access to cutting-edge technologies. But as more sensitive data moves to the cloud, the importance of robust cloud security best practices becomes paramount. This article discusses the basics of cloud data security. It also provides a list of eight important best practices for protecting your data in the cloud.
Understanding Cloud Data Security
Cloud data security involves strategies, tools, and techniques that protect data stored in the cloud from loss, leakage, and theft. Its significance grows as more businesses adopt cloud services. Around 40% of companies had a data breach in their cloud. This shows the importance of strong security measures.
Cloud security controls fall into three main categories:
- Preventive controls: Measures like encryption and access controls that prevent incidents from occurring
- Detective controls: Tools like intrusion detection systems that identify potentially harmful activities
- Corrective controls: Plans like backup and recovery that limit damage and restore operations after an incident
Cloud Security Best Practices You Need to Implement
Encrypt Your Data
Encryption renders data unreadable without a specific key. Always keep data encrypted, both in transit and at rest. Manage encryption keys securely, for example, use AES-256 encryption and store keys in a hardware security module.
Secure Your APIs
APIs enable data flow between cloud services but can be entry points for attacks if not properly secured. Use techniques like encryption, access control, and regular testing. Implement API gateways to centralize security management.
Enforce Strong Access Controls and Identity Management
Restrict data access to authorized users only. Use role-based or attribute-based access controls and multi-factor authentication. Consider identity and access management solutions to automate and centralize these processes.
Conduct Regular Data Audits
Schedule thorough reviews of access controls, encryption standards, and incident response plans. Engage third-party auditors for an unbiased assessment. Make audits a key part of your data security policy to drive continuous improvement.
Prioritize Security Awareness and Training
Empower your staff to recognize and prevent security incidents. Hold regular training sessions, run phishing simulations, and foster a security-focused culture. Remember, human error causes nearly 75% of data breaches.
Implement Robust Backup and Recovery Plans
Protect against data loss with regular, secure offsite backups. Test your recovery plans to confirm that you can restore operations quickly. Make sure to test your recovery plans to minimize downtime in case of an incident. Make sure you test your recovery plans to reduce costs during an incident.
Leverage Advanced Threat Protection
Use tools with machine learning and behavioral analytics to detect sophisticated threats that traditional measures might miss. Integrate these into your security infrastructure for real-time protection against evolving cyber threats.
Assess Your Vendors’ Security Closely review your vendors’ security practices, compliance certifications, and incident response capabilities. Use standardized frameworks like the Cloud Security Alliance’s CAIQ for comprehensive evaluations.
Putting Cloud Security Best Practices into Action
Implementing these cloud security best practices requires a proactive, comprehensive approach. Begin with these key steps to start:
- Develop a clear cloud security strategy aligned with your business goals
- Assign responsibility for cloud security to a dedicated team or individual
- Regularly assess your security posture and make improvements
- Stay informed about the latest cloud security threats and best practices
- Work closely with your cloud service providers to ensure a shared security model
To better understand how cloud security works in practice, let’s take a look at a simplified cloud security pipeline:
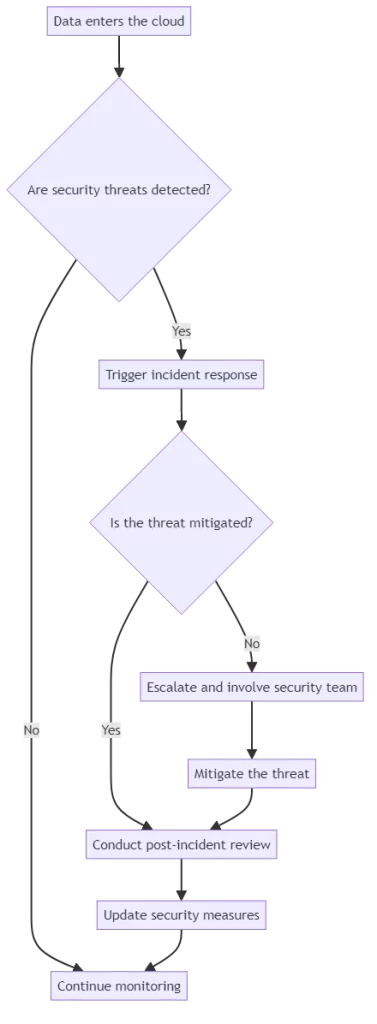
Improve your data security in the cloud by following best practices and being proactive. Remember, as the threat landscape evolves, so too must your approach to cloud security.
The Bottom Line on Data Security
To prevent data breaches, it is crucial to protect data, secure APIs, control access, and monitor for problems. Keeping data safe is essential.
Managing access is crucial. Monitoring for issues is necessary. Training employees and making backup plans can also help prevent costly breaches. Using advanced threat protection and evaluating vendors further decrease the risk of a data breach.
Conclusion
Safeguarding your data in the cloud is a complex and ongoing process that requires a multi-faceted approach. Follow these eight cloud security best practices. This will help lower the risk of a data breach. You will ensure the safeguarding of your most important asset, which is your data.
Remember, cloud security is a shared responsibility between you and your cloud service provider. Choose a provider that prioritizes security and offers robust security features and support.
As you embark on your cloud security journey, consider leveraging a modern solution like DataSunrise. DataSunrise offers a comprehensive suite of tools to secure your data in the cloud, including data discovery, classification, encryption, access control, and monitoring. With DataSunrise, you can always protect, ensure compliance for, and control your data.
Start implementing these cloud security best practices today and give your data the protection it deserves. To witness DataSunrise’s performance, register for a demonstration session. You will learn how DataSunrise can protect your data in the cloud.
