
Cloudberry Data Audit Trail

Implementing a Cloudberry data audit trail provides organizations with essential visibility into database operations and changes. As organizations process increasing volumes of sensitive information, this native auditing capability has become a cornerstone of data governance strategies. Recent research by Thales shows how important audit systems are. It notes that data breaches impact 40% of organizations. The average cost to recover from these breaches is $4.45 million.
For businesses managing sensitive data, Cloudberry’s data audit trail capabilities offer systematic tracking and verification of database modifications. This methodical approach to data auditing supports compliance requirements while providing insights into data access patterns and potential security concerns.
Understanding Cloudberry’s Native Audit Trail Features
Cloudberry offers comprehensive data audit trail functionality through its native SQL language features. This system captures all database changes, including insertions, updates, and deletions, providing a complete history of data modifications.
The audit trail system leverages several key components:
- SQL-based tracking mechanisms
- Custom views for auditing the log
- Stored procedures for automated audit processes
- Command-line interface for management tasks
Setting Up Basic Audit Trail in Cloudberry
To implement a basic audit trail in Cloudberry, follow these steps:
-- Create audit trail table
CREATE TABLE audit_log (
audit_id SERIAL PRIMARY KEY,
table_name VARCHAR(50),
operation_type VARCHAR(10),
modified_by VARCHAR(50),
modified_date TIMESTAMP
);
-- Create audit trigger function
CREATE OR REPLACE FUNCTION audit_trigger_function()
RETURNS TRIGGER AS $$
BEGIN
INSERT INTO audit_log (
table_name,
operation_type,
modified_by,
modified_date,
)
VALUES (
TG_TABLE_NAME,
TG_OP,
current_user,
current_timestamp
);
RETURN NEW;
END;
$$ LANGUAGE plpgsql;
After creating these structures, the audit_log table will capture changes. Here’s an example of how the audit log entries might look:
| audit_id | table_name | operation_type | modified_by | modified_date |
|---|---|---|---|---|
| 1 | customers | INSERT | sales_rep | 2024-02-06 10:15:23 |
| 2 | customers | UPDATE | account_mgr | 2024-02-06 10:16:45 |
| 3 | customers | DELETE | admin | 2024-02-06 10:17:30 |
Querying and Managing Audit Data
Viewing Recent Modifications
SELECT
modified_date,
table_name,
operation_type,
modified_by,
new_value->>'contact_email' as modified_email
FROM audit_log
WHERE table_name = 'customers'
ORDER BY modified_date DESC
LIMIT 10;
Example output:
| modified_date | table_name | operation_type | modified_by | modified_email |
|---|---|---|---|---|
| 2024-02-06 10:17:30 | customers | DELETE | admin | null |
| 2024-02-06 10:16:45 | customers | UPDATE | account_mgr | billing@acme.com |
| 2024-02-06 10:15:23 | customers | INSERT | sales_rep | contact@acme.com |
Analyzing Specific Time Periods
SELECT
modified_date,
operation_type,
modified_by,
old_value->>'subscription_tier' as old_tier,
new_value->>'subscription_tier' as new_tier
FROM audit_log
WHERE modified_date BETWEEN '2024-01-01' AND '2024-01-31'
AND table_name = 'customers';
Example output:
| modified_date | operation_type | modified_by | old_tier | new_tier |
|---|---|---|---|---|
| 2024-01-15 14:30:22 | UPDATE | account_mgr | startup | business |
| 2024-01-15 14:35:12 | UPDATE | account_mgr | business | enterprise |
| 2024-01-16 09:22:45 | INSERT | sales_rep | null | startup |
Enhancing Cloudberry with DataSunrise
Cloudberry’s data audit trail features are useful. However, it is also important to protect sensitive data from unauthorized access. This is where DataSunrise comes into play. DataSunrise also offers a powerful data masking solution that can be integrated with Cloudberry to protect sensitive fields in your database.
DataSunrise allows real-time data masking. This process hides sensitive data like email addresses, IP addresses, and Social Security numbers. Only authorized users can see the original information. This is particularly useful in audit trails, where sensitive data might need to be recorded or shared, but you don’t want to expose personally identifiable information (PII) or other confidential data.
Setting Up DataSunrise for Cloudberry
To integrate DataSunrise with Cloudberry for an enhanced data audit trail, follow these steps:
- Install DataSunrise: First, ensure that DataSunrise is installed on your system. DataSunrise’s installation process is straightforward and includes detailed guides and support materials.
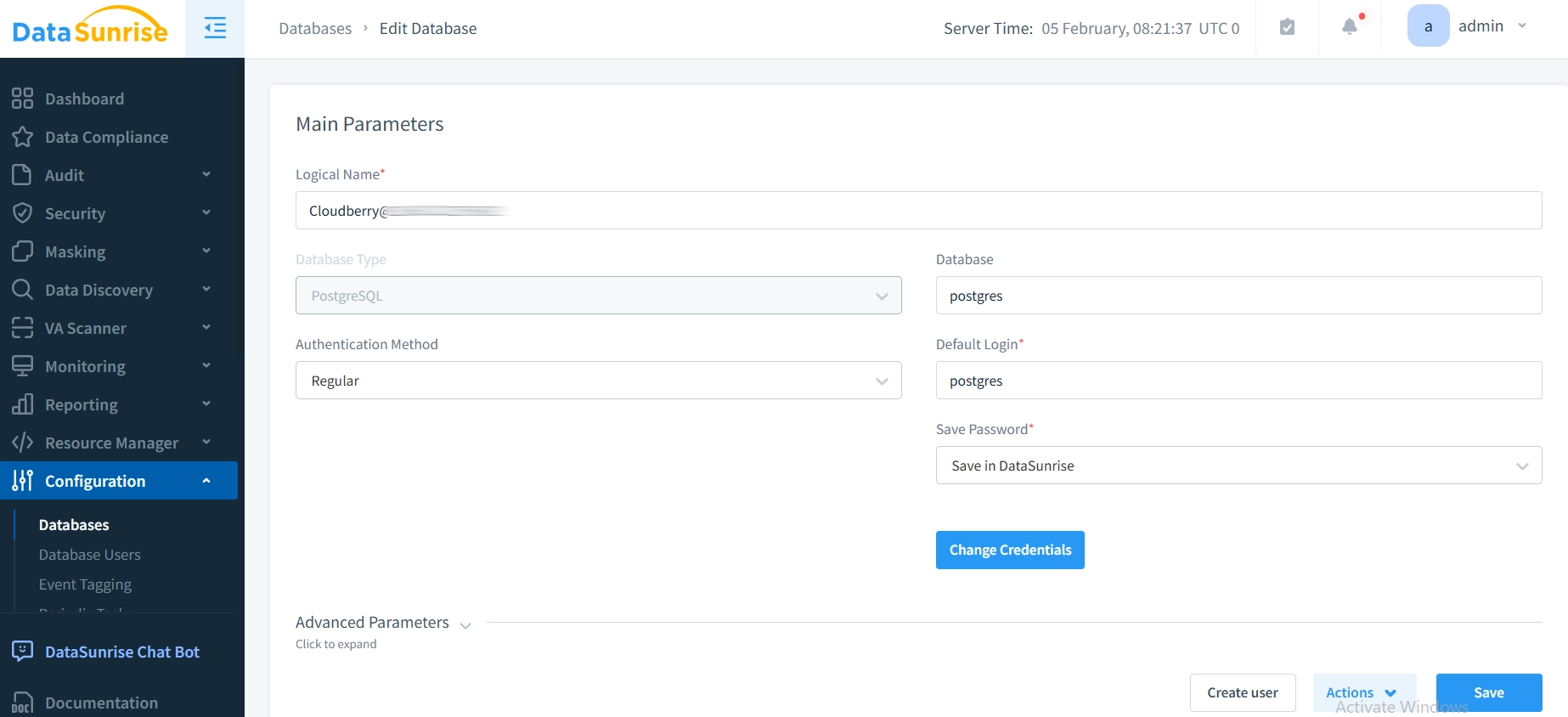
- Configure DataSunrise for Cloudberry: After you install DataSunrise, set it up to work with your Cloudberry database. This involves connecting DataSunrise to your Cloudberry instance and setting up the necessary audit trail parameters.
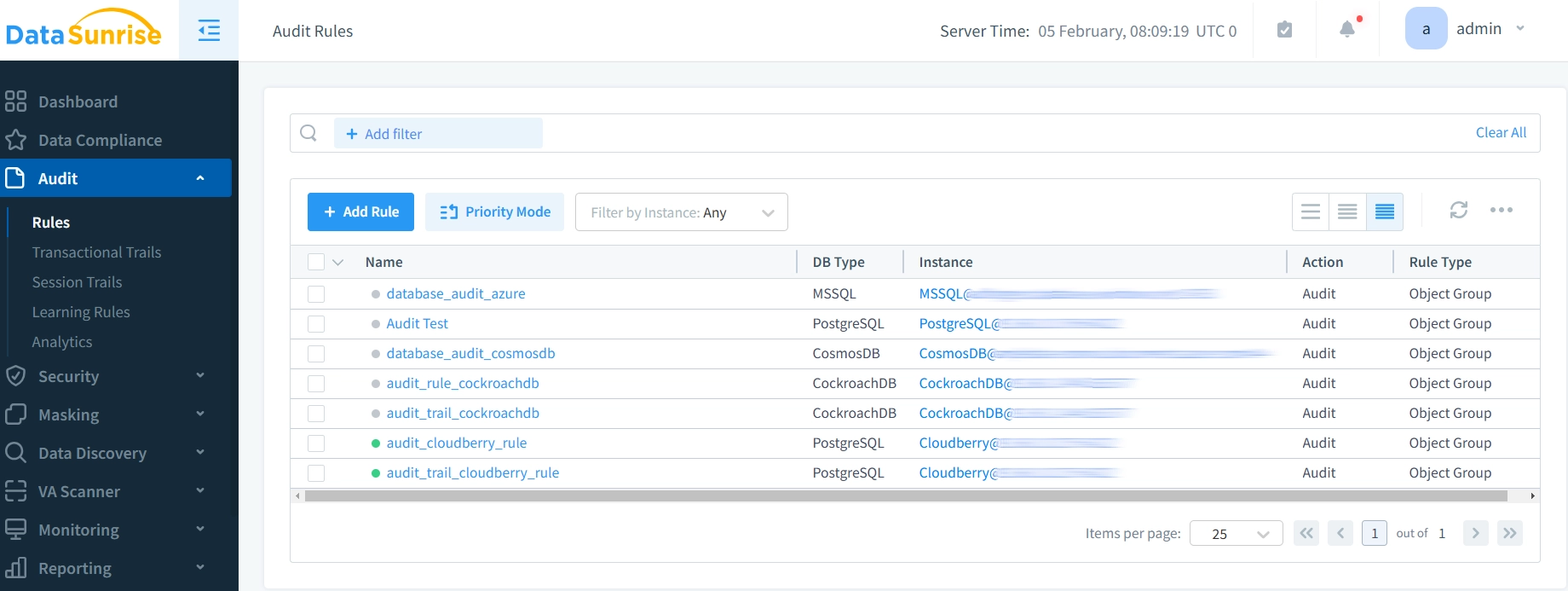
- Set Audit Trail Rules: Define the specific data actions and operations that you wish to track. With DataSunrise, you can set your auditing options to track only the most important data events. This includes changes to sensitive data and access by privileged users.
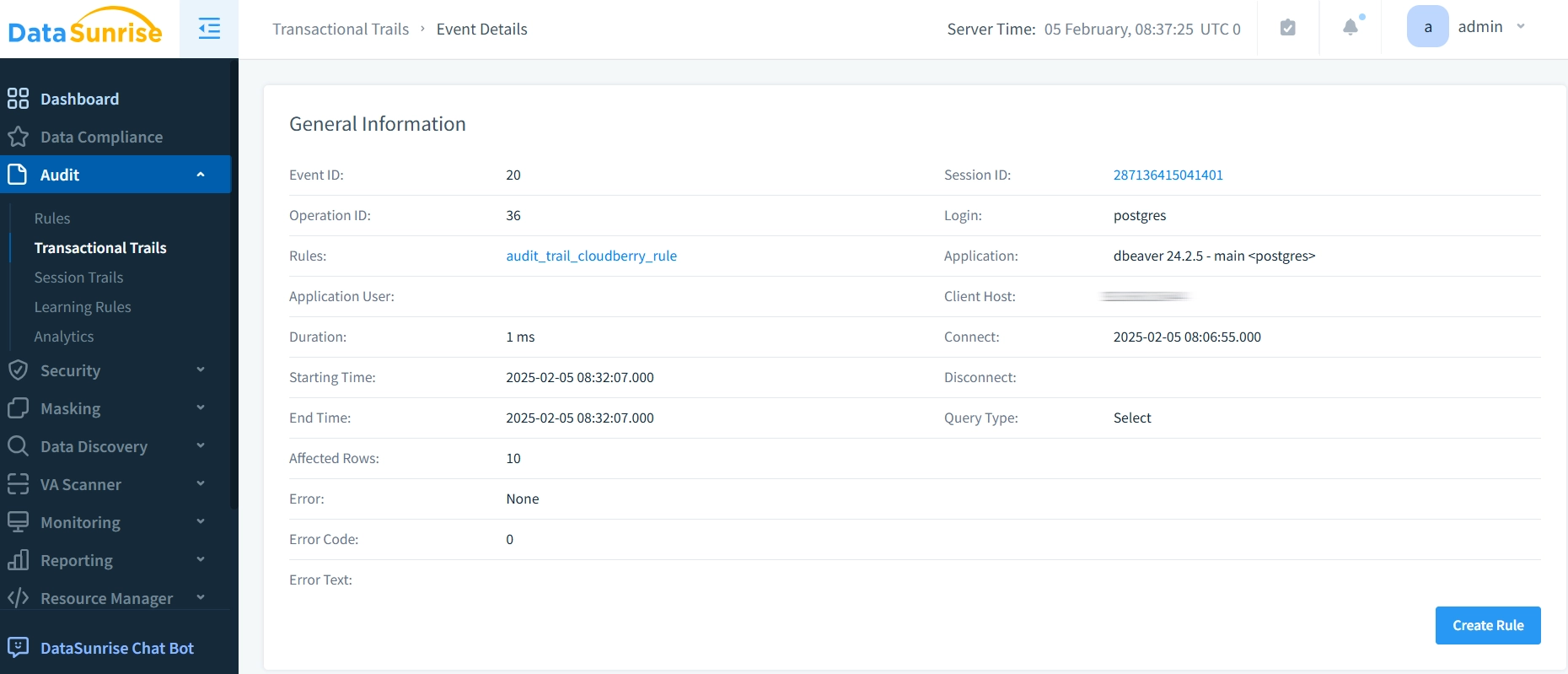
- Review Audit Trails: After configuring the audit trail rule, you can use DataSunrise’s dashboard to access the audit trails. These events will give you clear insights. You will learn how Cloudberry accesses and changes your data.
Benefits of DataSunrise’s Security Suite for Cloudberry
By combining Cloudberry’s native data audit trail capabilities with DataSunrise solution, businesses can enjoy several key benefits:
- Centralized Data Control: DataSunrise allows for centralized management of data masking rules, ensuring uniform protection across the organization.
- Regulatory Compliance: DataSunrise helps companies meet compliance requirements like GDPR and HIPAA by masking sensitive data in real-time.
- Enhanced Security: The combination of Cloudberry’s audit trail features and DataSunrise’s masking functionality offers a robust defense against unauthorized data exposure.
Best Practices for Audit Trail Management
Regular Monitoring and Review. Effective audit trail management requires a systematic approach across several key areas. Organizations should establish consistent schedules for audit log reviews, typically conducting them weekly or bi-weekly depending on data sensitivity and regulatory requirements. These reviews should focus on identifying unusual patterns, unauthorized access attempts, and unexpected data modifications.
Performance Management. Performance considerations play a crucial role in maintaining an efficient audit system. Implementing audit log rotation prevents the audit tables from growing unnecessarily large and impacting database performance. Organizations should establish data retention policies that balance compliance requirements with system performance. Regularly archiving older audit data to separate storage helps maintain optimal database operation while preserving historical records. Strategic indexing of frequently queried audit fields ensures quick access to relevant information during investigations or compliance audits.
Documentation and Compliance. Documentation procedures require particular attention in audit trail management. Teams should maintain comprehensive records of audit policies, including the scope of audited operations, retention periods, and access controls. These policies should be reviewed and updated regularly to reflect changing business needs and regulatory requirements. All changes to audit configuration should be documented with clear justification and approval chains.
Third-Party Integration. Integration with third-party solutions like DataSunrise can enhance audit capabilities beyond native features. These tools provide additional layers of security through advanced data masking, centralized audit management, and specialized compliance reporting. When implementing such solutions, organizations should ensure seamless integration with existing audit processes and maintain consistent policies across all tools.
Conclusion
Cloudberry’s native data audit trail capabilities establish a foundation for tracking data changes and maintaining compliance. Organizations requiring additional security measures can enhance their setup with DataSunrise’s integration, which offers comprehensive data protection features.
For more information about advanced database security and available features, visit DataSunrise’s website and schedule an online demo. Learn of our security suite, including audit and compliance tools that complement Cloudberry’s native capabilities.
