
Cloudberry Database Activity History

Recent research from Code42 indicates that 42% of organizations encountered data exfiltration incidents in 2024. Cloudberry Database Activity History addresses this challenge by providing detailed tracking and analyzing of database operations. Organizations can use this functionality to monitor access patterns, track changes, and maintain audit trails across their database environments. This systematic approach to activity monitoring helps maintain data integrity while supporting compliance requirements across various regulatory frameworks.
Understanding Cloudberry’s Native Database Activity History
Cloudberry‘s native Database Activity History feature delivers powerful insights into database operations through SQL language features, dedicated views, and stored procedures. This built-in functionality allows organizations to maintain detailed audit trails without additional software installation.
Core Features of Native Activity Tracking
The native tracking system captures several critical data points:
- Query execution timestamps and durations that help identify performance bottlenecks and unusual activity patterns in your database operations
- User identification details including connection information and IP addresses, enabling precise tracking of who accessed what data and when
- Complete SQL statement logging that provides transparency into exact database operations performed during each session
- Resource utilization metrics that help optimize database performance and identify potential issues before they impact operations
Accessing Activity History Through Command Line
Cloudberry provides comprehensive command-line tools for accessing and analyzing Database Activity History. Users can get detailed activity logs using the CLI. It has strong filtering and output formatting options for easy log analysis.
Implementing Native Database Activity History
Setting Up Activity Tracking
To enable comprehensive activity tracking, you’ll need to configure several system views and stored procedures. Here’s a basic example:
CREATE VIEW database_activity_log AS
SELECT
session_id,
user_name,
action_timestamp,
operation_type,
affected_objects,
query_text
FROM system_audit_log
WHERE timestamp >= DATEADD(day, -7, GETDATE());
Example output:
| session_id | user_name | action_timestamp | operation_type | affected_objects | query_text |
|---|---|---|---|---|---|
| CB-45678 | john.doe | 2025-02-11 09:15:22 | SELECT | customer_records | SELECT * FROM customer_records WHERE region = ‘WEST’ |
| CB-45679 | sarah.analyst | 2025-02-11 09:16:45 | UPDATE | financial_data | UPDATE financial_data SET status = ‘VERIFIED’ WHERE id = 123 |
| CB-45680 | system_audit | 2025-02-11 09:17:30 | INSERT | audit_logs | INSERT INTO audit_logs (event_type, details) VALUES (…) |
| CB-45681 | admin_user | 2025-02-11 09:18:15 | DELETE | archived_records | DELETE FROM archived_records WHERE date < '2024-01-01' |
Using the Cloudberry CLI
The Cloudberry Command Line Interface provides powerful tools for managing activity history:
cloudberry-cli activity-history list \
--from-date "2025-02-01" \
--to-date "2025-02-11" \
--format json \
--filter "operation_type=SELECT" \
--sort-by timestamp \
--limit 100
Example CLI output:
| timestamp | user | action | database | table | details |
|---|---|---|---|---|---|
| 2025-02-11 10:00:01 | john.doe | SELECT | sales_2025 | customer_orders | Retrieved Q1 sales data for Western region |
| 2025-02-11 10:45:22 | admin_user | ALTER | security_db | user_permissions | Modified role permissions for analyst group |
| 2025-02-11 11:00:05 | etl_service | INSERT | analytics_db | daily_metrics | Loaded daily performance metrics |
Advanced Audit Capabilities
Building on the native Database Activity History, Cloudberry offers advanced audit features that provide deeper insights into database operations. These capabilities work seamlessly with the basic activity tracking system while offering enhanced monitoring options.
Working with Test Data
Let’s examine how activity tracking works with sample data:
CREATE TABLE user_activity AS
SELECT
u.first_name,
u.last_name,
u.email,
a.ip_address,
a.action_timestamp,
a.operation_type
FROM users u
JOIN activity_log a ON u.id = a.user_id;
Sample output from user_activity table:
| first_name | last_name | masked_email | masked_ip | action_timestamp | operation_type | database_name |
|---|---|---|---|---|---|---|
| John | Doe | j***@company.com | 192.xxx.xxx.100 | 2025-02-11 11:00:00 | SELECT | sales_analytics |
| Sarah | Smith | s***@company.com | 192.xxx.xxx.101 | 2025-02-11 11:15:00 | UPDATE | customer_data |
| Michael | Johnson | m***@company.com | 192.xxx.xxx.102 | 2025-02-11 11:30:00 | INSERT | product_catalog |
| Emma | Wilson | e***@company.com | 192.xxx.xxx.103 | 2025-02-11 11:45:00 | DELETE | archived_data |
Enhanced Security with DataSunrise Integration
While Cloudberry’s native Database Activity History provides robust monitoring capabilities, organizations requiring additional security measures can benefit from DataSunrise‘s comprehensive security suite. DataSunrise offers advanced data masking capabilities specifically designed for Cloudberry environments.
Setting Up DataSunrise for Cloudberry
To begin using DataSunrise’s advanced features:
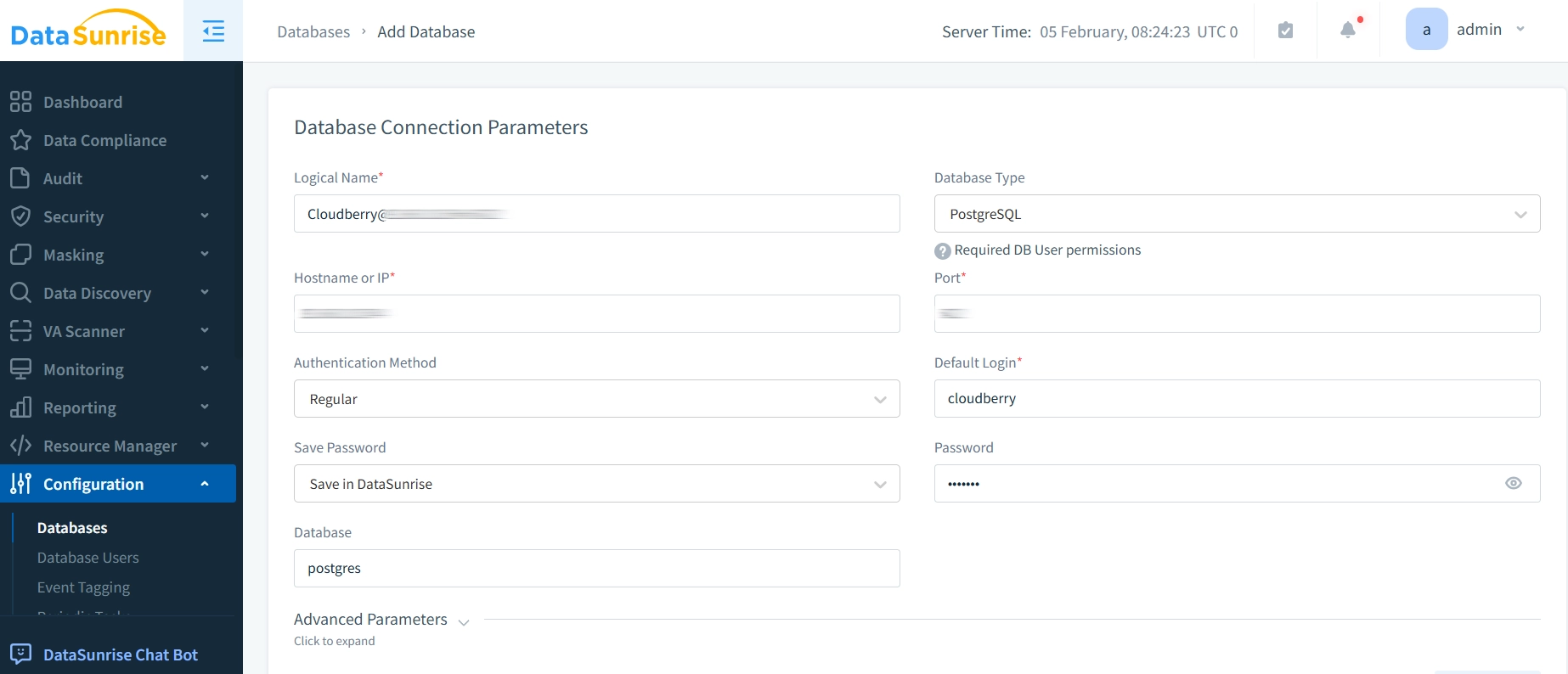
- Access your DataSunrise dashboard
- Add a new Cloudberry database connection
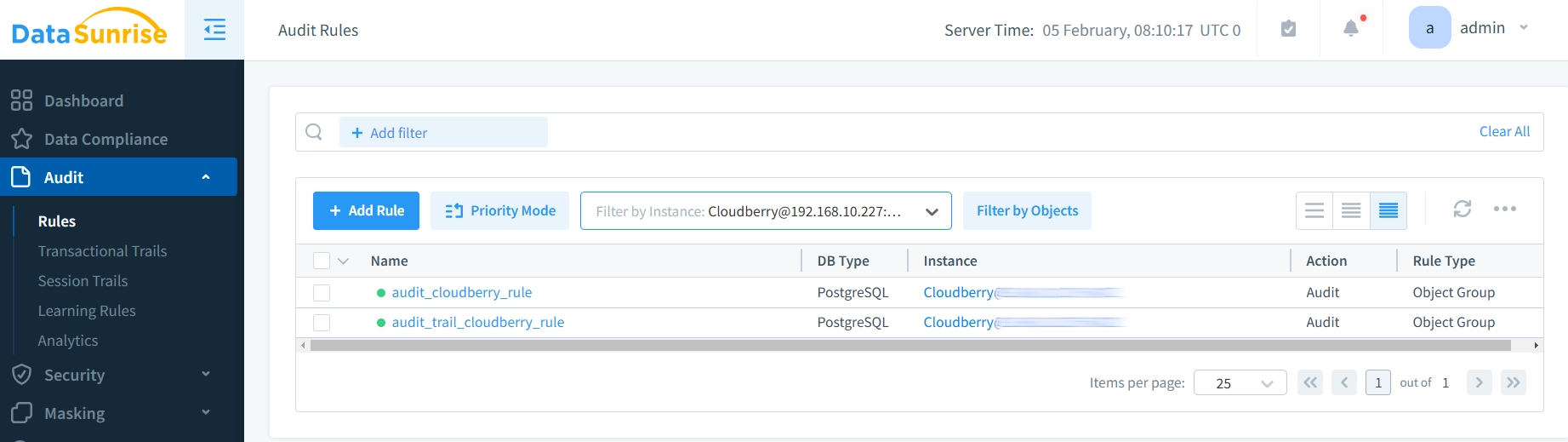
- Configure audit rules based on your security requirements
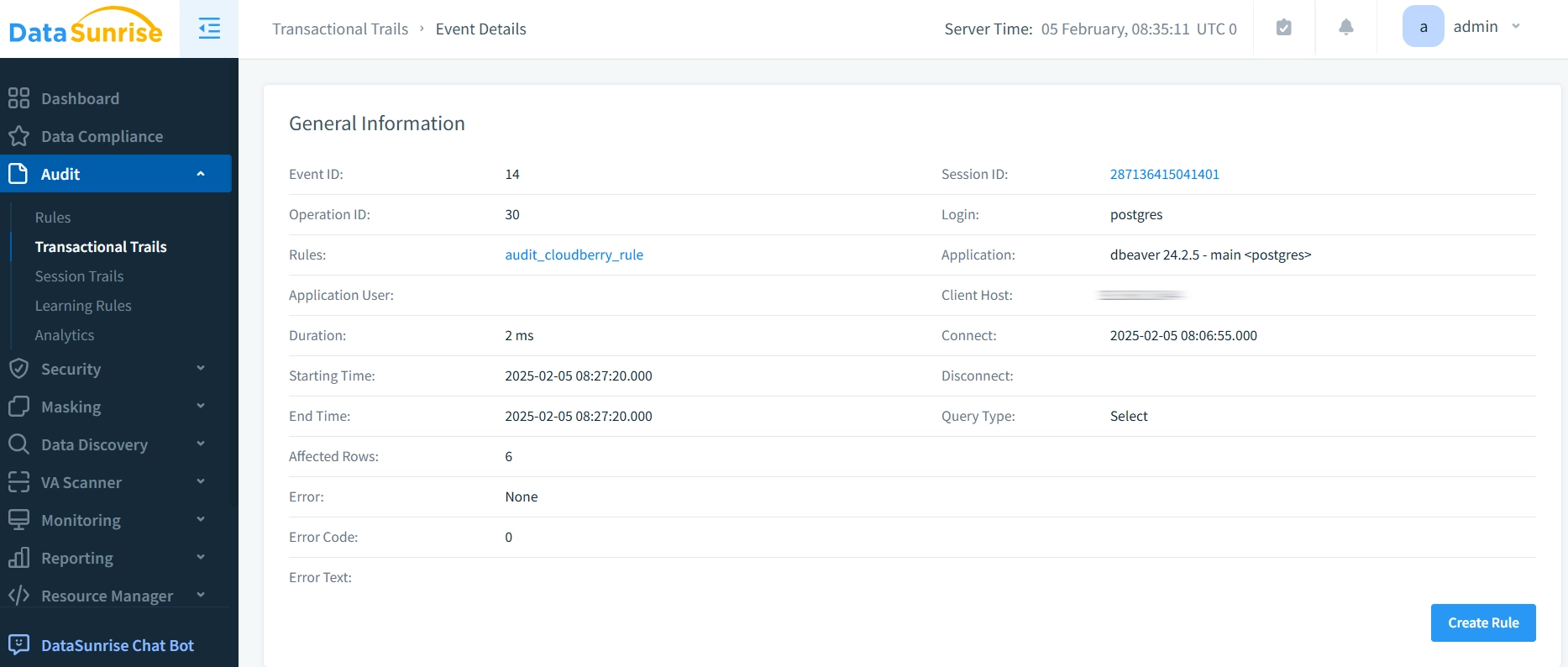
- Check audit events by clicking them in the “Transactional Trails” tab
Benefits of DataSunrise Integration
DataSunrise enhances Cloudberry’s native capabilities by providing:
- Centralized management of audit rules across multiple databases and platforms
- Advanced data masking features that protect sensitive information
- Real-time threat detection and automated response capabilities
- Comprehensive compliance reporting tools for various regulatory frameworks
Optimizing Database Activity Monitoring
Performance balance is fundamental for effective database activity monitoring. Organizations should evaluate their logging requirements periodically to ensure they capture necessary information while minimizing system overhead. Regular review and refinement of audit rules helps maintain optimal system operation while ensuring comprehensive coverage.
Third-party integration often provides additional security layers. Many organizations use Cloudberry Database Activity History with tools like DataSunrise. These tools provide advanced features. They include real-time alerts, automated responses, and centralized audit management for multiple database instances.
Documentation and compliance require systematic attention. Teams should keep clear records of audit settings. This includes the reasons for specific rules and any changes made over time. This documentation proves invaluable during security audits and helps maintain consistency across database environments.
Data analyzing and pattern recognition drive continuous improvement. Regular analysis of collected data helps identify potential security issues and opportunities for system optimization. Setting up automated analysis tools can help process large volumes of audit data efficiently, flagging unusual patterns for further investigation while maintaining system performance.
Conclusion
Database Activity History for Cloudberry provides essential visibility into database operations, helping organizations maintain security and compliance. While the native capabilities offer robust monitoring features, organizations with advanced security requirements can benefit from DataSunrise’s comprehensive security suite.
For organizations interested in enhancing their database security and audit capabilities, DataSunrise offers flexible, cutting-edge tools that complement Cloudberry’s native features. Visit the DataSunrise website and schedule an online demo to discover how our advanced security solutions can strengthen your data protection strategy.
