
CockroachDB Audit Log

In today’s complex data landscape, maintaining comprehensive audit logs, especially through systems like the CockroachDB Audit Log, has become essential for organizations managing sensitive information. According to IBM’s Cost of a Data Breach Report 2024, organizations with properly implemented audit logs identify breaches 74 days faster, thus reducing costs by up to 28%. Undoubtedly, robust audit trails enhance security posture while simultaneously improving compliance readiness.
Though a powerful distributed SQL platform, CockroachDB provides native audit features that nevertheless offer the foundation needed to track database activities and identify suspicious behavior. Furthermore, these features help meet regulatory requirements without complex configuration. Unlike other solutions, this platform achieves this with minimal setup.
Our article explores native audit capabilities in CockroachDB and examines how third-party solutions enhance monitoring and security. Indeed, combining these approaches often yields the most comprehensive protection. Let’s examine the built-in features first.
Native CockroachDB Audit Log Capabilities
Various built-in mechanisms are available to establish audit logging through SQL interface and system tables. Although not as comprehensive as dedicated audit solutions, these native features still provide essential functionality for basic monitoring. Many organizations initially start with these features before eventually exploring advanced options. Understanding the core capabilities remains critical regardless of your implementation approach.
1. System Tables for Audit Logging
Internal system tables within the database capture valuable audit information. Administrators can query these tables to retrieve historical data. Automatic tracking of events occurs without requiring explicit configuration, which is certainly a time-saving benefit. Built-in functionality represents one of the platform’s key advantages:
-- Query recent login attempts SELECT event_timestamp, username, application_name, client_address, session_id FROM system.eventlog WHERE event_type = 'session_log' AND "eventType" = 'CLIENT_SESSION_CONNECT' ORDER BY event_timestamp DESC LIMIT 5;
Example output:
| event_timestamp | username | application_name | client_address | session_id |
|---|---|---|---|---|
| 2024-02-18 15:42:31.523 | admin | cockroach | 192.168.1.100 | 145732 |
| 2024-02-18 15:30:12.892 | analyst | DBeaver | 192.168.1.105 | 145731 |
| 2024-02-18 14:55:08.217 | admin | psql | 192.168.1.100 | 145729 |
| 2024-02-18 13:22:45.981 | reporter | Tableau | 192.168.1.112 | 145725 |
| 2024-02-18 12:10:03.456 | dbadmin | cockroach | 192.168.1.101 | 145720 |
2. Creating Custom Audit Tables
Greater granular control comes from creating custom audit tables populated using triggers. Such an approach provides more flexibility than system tables alone. Custom tables allow storing context crucial for forensic analysis, thereby enhancing investigation capabilities. Additional benefits include tailored retention policies based on data sensitivity:
-- Create audit log table
CREATE TABLE audit_log (
id UUID DEFAULT gen_random_uuid() PRIMARY KEY,
timestamp TIMESTAMPTZ DEFAULT current_timestamp(),
user_id STRING,
action STRING,
table_name STRING,
query TEXT,
old_value JSONB,
new_value JSONB
);
-- Create indexes for performance
CREATE INDEX idx_audit_log_timestamp ON audit_log(timestamp);
CREATE INDEX idx_audit_log_user ON audit_log(user_id);
CREATE INDEX idx_audit_log_table ON audit_log(table_name);
After this structure is in place, you can set up triggers to populate the audit log. These triggers execute whenever data changes occur. Any modification automatically generates a corresponding audit entry. Overall, this approach provides comprehensive monitoring without requiring application changes:
-- Example trigger function for audit logging
CREATE OR REPLACE FUNCTION log_data_changes()
RETURNS TRIGGER AS $$
BEGIN
IF (TG_OP = 'INSERT') THEN
INSERT INTO audit_log (user_id, action, table_name, query, new_value)
VALUES (current_user, 'INSERT', TG_TABLE_NAME, current_query(), to_jsonb(NEW));
ELSIF (TG_OP = 'UPDATE') THEN
INSERT INTO audit_log (user_id, action, table_name, query, old_value, new_value)
VALUES (current_user, 'UPDATE', TG_TABLE_NAME, current_query(), to_jsonb(OLD), to_jsonb(NEW));
ELSIF (TG_OP = 'DELETE') THEN
INSERT INTO audit_log (user_id, action, table_name, query, old_value)
VALUES (current_user, 'DELETE', TG_TABLE_NAME, current_query(), to_jsonb(OLD));
END IF;
RETURN NULL;
END;
$$ LANGUAGE plpgsql;
3. SQL Audit Views for Analysis
Creating views simplifies audit log analysis for security use cases. Views enable filtering of complex audit data and focus on high-risk activities. Sharing with security teams becomes possible without granting access to underlying tables. Security layers form naturally through views themselves. Most implementations align this approach with least-privilege security principles:
-- View for suspicious activities
CREATE VIEW suspicious_audit_events AS
SELECT
timestamp,
user_id,
action,
table_name,
SUBSTRING(query, 1, 50) AS query_preview
FROM
audit_log
WHERE
(action = 'DELETE' AND table_name IN ('users', 'roles', 'permissions'))
OR (action = 'UPDATE' AND table_name = 'user_roles')
OR (user_id NOT IN (SELECT username FROM authorized_users) AND table_name IN ('sensitive_data', 'financial_records'));
4. Using CockroachDB CLI for Audit Log Management
Command-line interface allows querying and managing audit logs with powerful automation capabilities. Despite its text-based nature, CLI excels at scheduled tasks. Tools can be incorporated into scripts for regular reporting. Seamless integration with existing operational workflows becomes possible through this approach:
# Extract recent audit events to a CSV file
cockroach sql --execute="
COPY (
SELECT timestamp, user_id, action, table_name, query
FROM audit_log
WHERE timestamp > current_timestamp - INTERVAL '24 hours'
ORDER BY timestamp DESC
) TO '/tmp/recent_audit.csv' WITH CSV HEADER;"
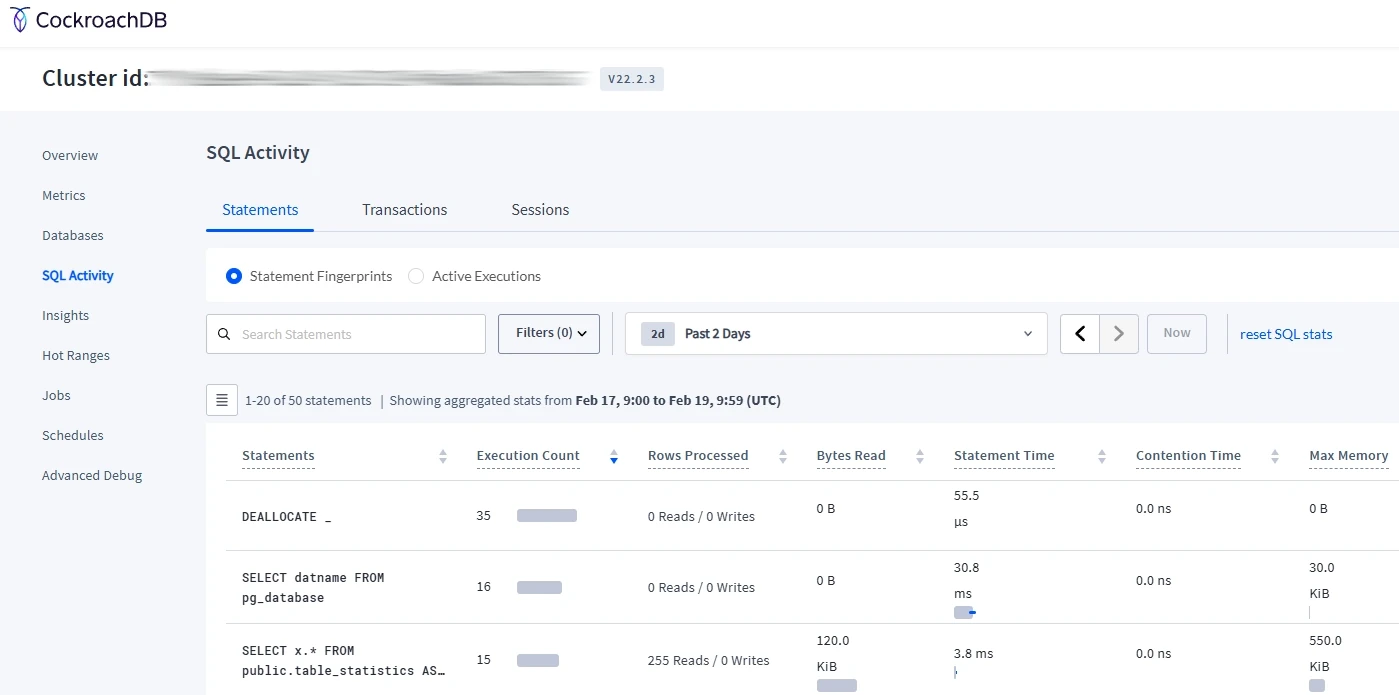
Accessing Audit Logs via CockroachDB Web UI
Web-based administration interface with comprehensive monitoring capabilities comes built into the platform. Users can access visual tools for audit analysis effortlessly due to intuitive design. Many audit tasks are simplified through the web UI, offering the most user-friendly approach to monitoring. Advanced analysis might require exporting data for specialized tools:
- Access the Web UI: Navigate to the CockroachDB Admin UI (typically at http://localhost:8080)
- SQL Activity Dashboard: Review query execution and session information
- Statement Statistics: Analyze query patterns and identify anomalies
- Jobs Page: Monitor background processes and operations
Enhanced Audit Logging with DataSunrise
Native audit capabilities in the database provide basic functionality, yet organizations with advanced requirements typically need more comprehensive solutions. DataSunrise effectively extends these capabilities with features designed for enterprise-grade security. Additional capabilities justify the investment for most organizations given its seamless integration. Positive ROI within the first year is reported by many organizations:
Key Advantages of DataSunrise for CockroachDB Audit Logging
- Real-Time Monitoring: Continuous observation with immediate alerts for suspicious events
- Comprehensive Audit Rules: Fine-grained control over logged activities
- Centralized Management: Unified interface for managing policies across instances
- Behavior Analytics: AI-powered analysis to detect anomalies
- Automated Compliance Reporting: Pre-built templates for regulatory requirements
Setting Up DataSunrise for CockroachDB Audit Logging
Deploying DataSunrise involves connecting your database and configuring rules. Monitoring activity can begin immediately after setup. Setup process typically takes less than an hour, unlike traditional security deployments. Significant advantage comes from this efficiency considering the complexity of other security tools:
1. Connect to Your CockroachDB Instance
First step requires establishing a connection between DataSunrise and your database cluster through the interface. Basic credentials and network information need to be entered afterward. Proper connectivity is absolutely essential for reliable monitoring performance. Connection verification should happen before proceeding to prevent monitoring gaps.
2. Configure Audit Rules
Second step involves creating customized audit rules to specify which activities should be logged in your environment. Rules determine what events get captured during operation. Well-designed rules balance security needs with performance considerations at their core. High-risk operations should be prioritized first to minimize performance impact.
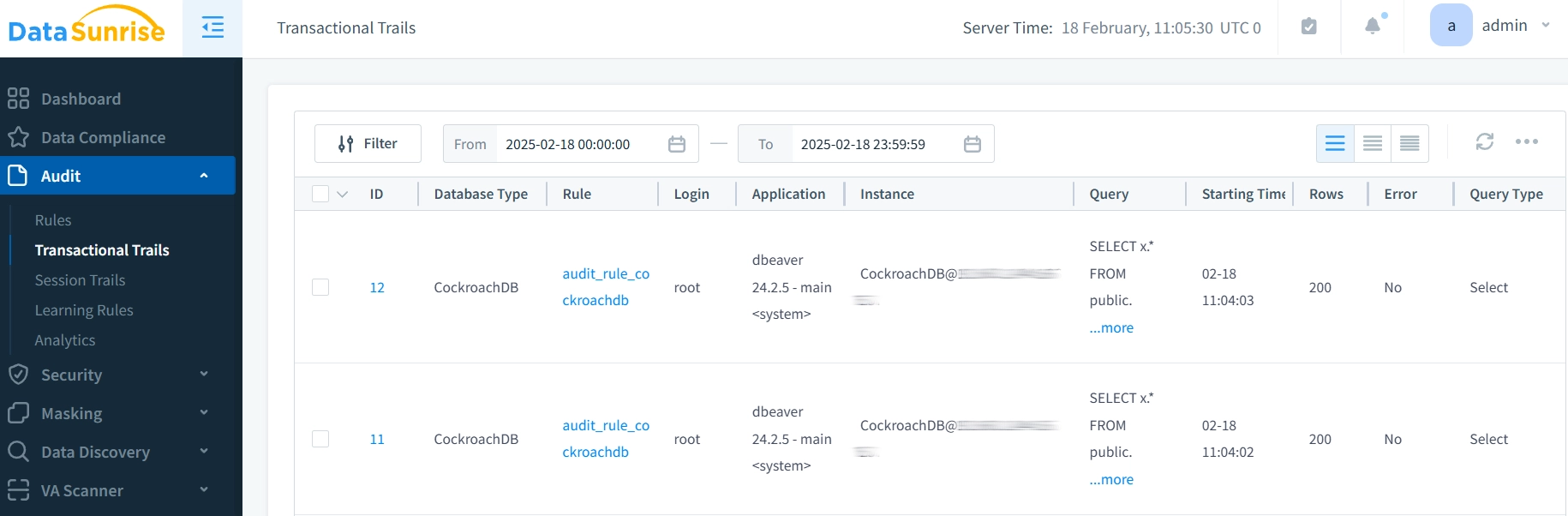
3. Monitor Audit Logs
Last step requires accessing detailed audit logs through the intuitive DataSunrise interface for real-time analysis. Filtering these logs helps identify security incidents or compliance issues. Primary goal focuses on transforming raw audit data into actionable security intelligence. Visual analytics for trend identification are provided alongside reporting capabilities:
Best Practices for CockroachDB Audit Logging
Effective audit logging requires careful attention to several key areas. Organizations should focus on these five critical aspects of implementation. Comprehensive approach almost always yields the best outcomes for security and compliance under these circumstances. Following best practices represent industry standards for optimal results:
1. Performance Optimization
- Selective Logging: Only audit essential activities to minimize impact
- Index Management: Create appropriate indexes for efficient queries
- Log Rotation: Establish automatic archiving of older records
- Storage Planning: Allocate sufficient audit storage based on retention needs
2. Security Implementation
- Access Controls: Restrict access using role-based controls
- Encryption: Protect audit data at rest and in transit through strong encryption
- Tamper Protection: Apply checksums to detect unauthorized modifications
- Backup Strategy: Maintain separate backups of audit logs
3. Compliance Management
- Retention Policies: Define periods based on compliance regulations
- Data Classification: Prioritize logging for sensitive data
- Regular Validation: Test log completeness periodically
- Documentation: Maintain detailed records of procedures
4. Monitoring and Analysis
- Real-Time Alerts: Configure notifications for suspicious activities
- Regular Reviews: Establish scheduled review procedures
- Anomaly Detection: Adopt pattern analysis for unusual behavior
- Reporting: Create visualizations for security metrics
5. Third-Party Solution Integration
- Specialized Tools: Incorporate DataSunrise Database Firewall for enhanced capabilities
- Centralized Management: Utilize platforms to manage security across databases
- Automated Compliance: Leverage compliance manager templates
- Advanced Analytics: Employ threat detection for monitoring activities
Conclusion
Essential functionality for basic monitoring and compliance needs comes from native audit capabilities in CockroachDB. Organizations with advanced security requirements often benefit from integrated solutions like DataSunrise.
Combining this database platform with DataSunrise’s features allows organizations to establish robust monitoring while ensuring SOX compliance. Integrated approach effectively addresses modern database security challenges while maintaining performance. Well-crafted strategy significantly reduces security incidents and greatly simplifies compliance processes.
Ready to enhance your audit capabilities? Schedule a demonstration today to see how DataSunrise can immediately strengthen your security posture.
