CockroachDB Audit Tools
In today’s data-driven landscape, organizations face increasing pressure to protect their database assets. According to the 2024 Ponemon Institute Database Security Report, 78% of surveyed organizations experienced at least one database breach in the past two years, with 42% attributing inadequate audit capabilities as a contributing factor.
For organizations using CockroachDB, implementing robust audit tools is critical for maintaining data security, achieving regulatory compliance, and ensuring data integrity. This article explores CockroachDB’s built-in audit functionalities and examines how third-party tools like DataSunrise can enhance your database security posture.
Native CockroachDB Audit Tools
CockroachDB provides several built-in mechanisms for auditing database activities. These native tools offer fundamental capabilities for tracking user actions, query execution, and system events.
1. System Tables and Event Logs
CockroachDB maintains internal system tables that capture valuable audit information. The system.eventlog table records significant events like cluster membership changes, schema alterations, and privilege modifications:
-- Query recent schema changes SELECT timestamp, "reportingID", info FROM system.eventlog WHERE event_type = 'schema_change' ORDER BY timestamp DESC LIMIT 5;
2. SQL Statistics Tables
CockroachDB maintains detailed statistics about query execution through its internal crdb_internal.statement_statistics view:
-- Examine recent SQL statement execution SELECT application_name, query_summary, execution_count, mean_service_latency, max_retries FROM crdb_internal.statement_statistics ORDER BY last_execution_timestamp DESC LIMIT 5;
| application_name | query_summary | execution_count | mean_service_latency | max_retries |
|---|---|---|---|---|
| DBeaver | SELECT * FROM users WHERE… | 42 | 15.3ms | 0 |
| psql | UPDATE orders SET status=… | 18 | 22.7ms | 1 |
| tableplus | INSERT INTO customers… | 76 | 12.1ms | 0 |
| app_backend | DELETE FROM temp_records… | 3 | 5.4ms | 0 |
| cockroach | EXPLAIN ANALYZE SELECT… | 7 | 145.2ms | 2 |
3. Custom Audit Tables with Triggers
For more comprehensive auditing, database administrators can implement custom audit tables with triggers:
-- Create audit table
CREATE TABLE audit_events (
id UUID DEFAULT gen_random_uuid() PRIMARY KEY,
event_time TIMESTAMPTZ DEFAULT current_timestamp(),
username STRING NOT NULL,
action STRING NOT NULL,
table_name STRING,
query_text STRING,
row_data JSONB
);
-- Create function for audit logging
CREATE FUNCTION log_table_changes() RETURNS TRIGGER AS $$
BEGIN
INSERT INTO audit_events (username, action, table_name, query_text, row_data)
VALUES (
current_user,
TG_OP,
TG_TABLE_NAME,
current_query(),
CASE
WHEN TG_OP = 'DELETE' THEN to_jsonb(OLD)
ELSE to_jsonb(NEW)
END
);
RETURN NULL;
END;
$$ LANGUAGE plpgsql;
-- Apply trigger to sensitive table
CREATE TRIGGER audit_customer_data
AFTER INSERT OR UPDATE OR DELETE ON customer_data
FOR EACH ROW EXECUTE FUNCTION log_table_changes();
4. Using CockroachDB’s Command Line Interface for Auditing
The CockroachDB CLI offers capabilities for extracting and analyzing audit information:
# Export audit records to CSV for analysis
cockroach sql --execute="
COPY (
SELECT
event_time,
username,
action,
table_name,
query_text
FROM audit_events
WHERE event_time > current_timestamp - INTERVAL '7 days'
) TO '/tmp/weekly_audit.csv' WITH CSV HEADER;"
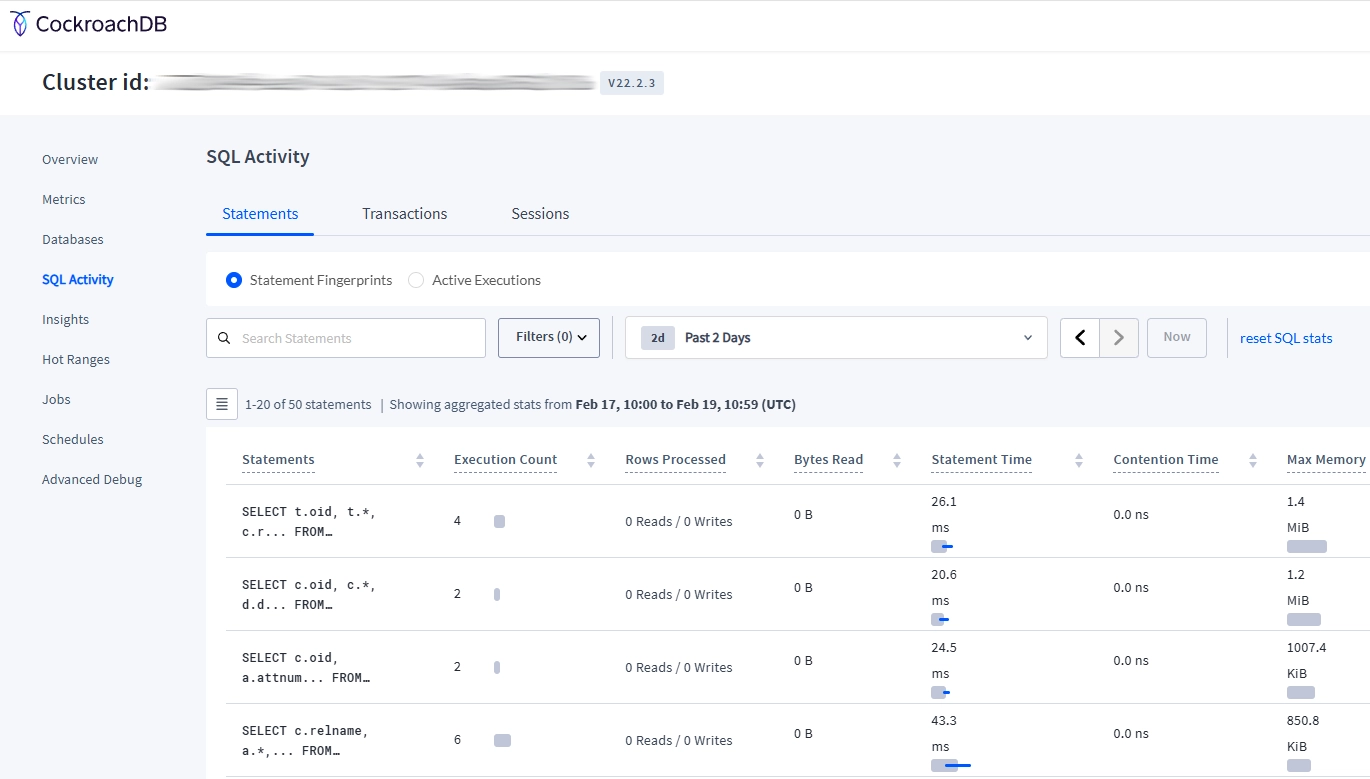
5. CockroachDB Web UI for Monitoring
CockroachDB provides a web-based interface that includes monitoring capabilities for real-time observation of database activities:
- Access the web UI (typically at http://localhost:8080)
- Navigate to the “SQL Activity” dashboard
- Review active sessions, recent queries, and transaction statistics
- Examine the “Statements” tab for comprehensive query analysis
Limitations of Native Audit Tools
While CockroachDB’s native audit capabilities provide essential functionality, they have several limitations:
- Limited Granularity: Native tools may not capture all required details for comprehensive database activity monitoring
- Manual Configuration: Implementing custom audit solutions requires significant effort and maintenance
- Performance Impact: Extensive auditing can affect database performance without careful optimization
- Basic Alerting: Limited real-time notification capabilities for security events
- Compliance Gaps: May not fully satisfy complex regulatory requirements without additional tooling
Enhanced CockroachDB Auditing with DataSunrise
DataSunrise extends CockroachDB’s audit capabilities with advanced security features specifically designed to address these limitations while providing additional protections.
Key Features of DataSunrise for CockroachDB
1. Comprehensive Audit Coverage
DataSunrise provides detailed monitoring of database activities, capturing authentication attempts, SQL queries, schema modifications, data access operations, and administrative activities.
2. Advanced Audit Rule Configuration
DataSunrise enables creation of sophisticated audit rules based on database objects, user roles, client applications, connection sources, and query characteristics.
3. Real-Time Monitoring and Alerts
The platform provides immediate notification of suspicious activities through messaging platforms, email alerts, SIEM integration, and custom webhook notifications.
4. Behavioral Analytics for Threat Detection
Advanced analytics identify abnormal access patterns through user behavior profiling, anomaly detection, and machine learning-based threat detection.
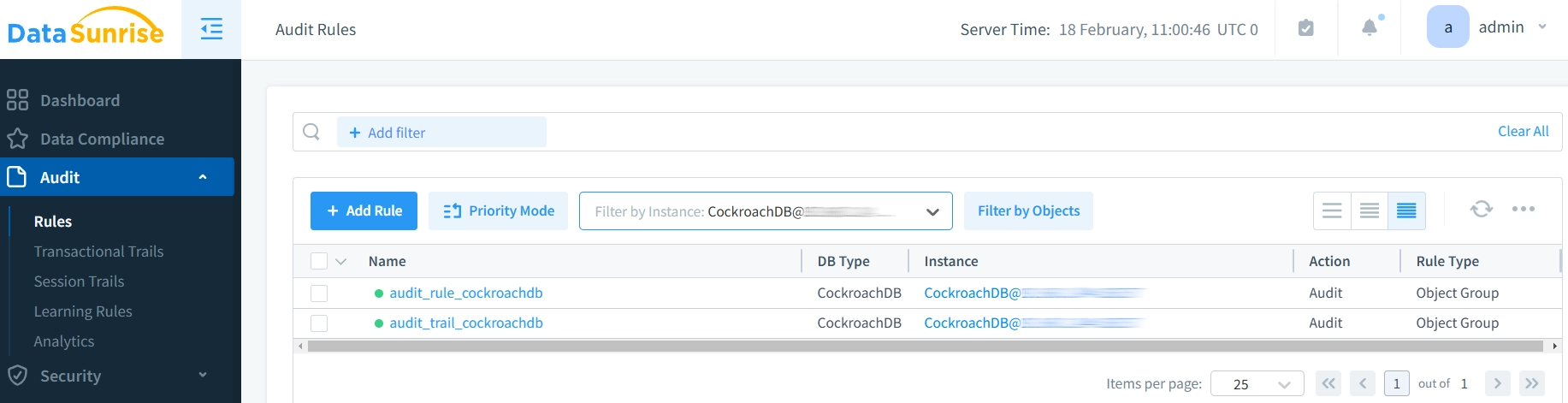
Setting Up DataSunrise for CockroachDB Audit
Connecting to CockroachDB
DataSunrise integrates with CockroachDB through a straightforward setup process that establishes secure monitoring. After installation, administrators simply connect DataSunrise to their CockroachDB instance by providing connection parameters, configure desired audit rules through the intuitive interface, and begin monitoring database activity history in real-time.
Best Practices for CockroachDB Audit Implementation
1. Performance Optimization
- Implement selective auditing based on data sensitivity
- Use appropriate indexing for audit tables
- Schedule regular archiving of older audit logs
- Monitor audit tool performance impact
2. Security Implementation
- Protect audit logs with encryption and access controls
- Implement separate storage for audit data
- Establish clear retention policies
- Configure comprehensive alerting for security events
3. Compliance Management
- Document audit procedures and configurations
- Align retention policies with SOX, PCI DSS, and HIPAA requirements
- Implement regular compliance validation checks
- Create standardized report generation
4. Operational Considerations
- Train database administrators on audit tools
- Establish clear incident response procedures
- Implement regular audit log reviews
- Coordinate audit strategies with broader security initiatives
5. Third-Party Solution Integration
- Implement specialized tools like DataSunrise for comprehensive audit trail management
- Leverage centralized management platforms for unified security policies
- Utilize LLM and ML tools and behavioral monitoring capabilities
- Configure Compliance Manager with pre-built templates
- Implement real-time alerting through integration with notification systems
Conclusion
CockroachDB’s native audit capabilities provide essential monitoring functionality, but organizations with advanced security requirements benefit significantly from specialized tools like DataSunrise. By implementing comprehensive audit solutions, organizations can enhance their security posture, simplify compliance efforts, and gain deeper visibility into data audit trails.
DataSunrise Overview offers a powerful extension to CockroachDB’s native capabilities, providing advanced features for real-time monitoring, sophisticated rule configuration, and automated compliance. Through unified security management, organizations can protect their CockroachDB environments while maintaining optimal performance.
Ready to enhance your CockroachDB security with advanced audit tools? Schedule a demo today to experience DataSunrise’s comprehensive security and compliance capabilities firsthand.
