
CockroachDB Database Activity History

CockroachDB Database Activity History provides organizations with essential tools for monitoring and securing their data environments. The World Economic Forum’s 2024 Global Cybersecurity Outlook shows that database security is a major concern for organizations. About 43% of cyber leaders are focused on preventing unauthorized access.
As organizations manage increasingly complex data environments, maintaining detailed activity history has become a fundamental aspect of database administration. This guide examines how CockroachDB approaches activity tracking and auditing, offering insights into both native capabilities and integration with specialized security tools.
Understanding Database Activity History for CockroachDB
Database activity history means tracking all actions done on a database system. This includes queries run, records added or deleted, and changes to system settings. This audit trail is crucial for ensuring data integrity, compliance with regulatory requirements, and identifying potential security threats. For CockroachDB, this can be done through native features, external tools, or a combination of both.
CockroachDB has built-in tools for tracking database activity. These tools help monitor SQL operations. They are important for compliance and security. These features include views, stored procedures, and CockroachDB’s command-line interface (CLI). Together, these components provide the necessary functionality to track changes, perform diagnostics, and identify irregularities in the database.
Exploring CockroachDB’s Native Database Activity History
1. SQL Language Features for Monitoring Database Activity
One of the most fundamental ways to track database activity in CockroachDB is by using SQL language features. CockroachDB has system tables and views that hold information about database activity. Users can query these views to gain detailed insights into the operations done on the database.
Example of System Views:
CockroachDB provides a set of system tables that can be used to monitor database activity, such as crdb_internal.statement_statistics and crdb_internal.transaction_statistics. These views let users check database activity. They can see how many queries were run, how long they took, and if any errors happened.
Here’s an example SQL query to view query statistics:
SELECT * FROM crdb_internal.statement_statistics;
This view shows statistics about the queries run on the database. It includes execution count, errors, and average execution times.
2. Using CockroachDB’s Stored Procedures
Stored procedures in CockroachDB are another way to track database activity. Stored procedures allow for more fine-grained control over database operations. By writing stored procedures, you can encapsulate specific database logic and track the execution of certain actions.
For example, you could create a stored procedure to log changes made to sensitive data:
CREATE PROCEDURE log_changes() LANGUAGE SQL AS $$ INSERT INTO audit_log (change_time, user_id, action) VALUES (now(), current_user, 'update'); $$;
You can call this procedure before or after important tasks. It helps create a record of any changes to the database.
3. Using CockroachDB CLI for Activity History
CockroachDB provides a command-line interface (CLI) that can also be used to monitor and log database activity. The CLI allows for various administrative tasks, such as querying system tables, managing clusters, and inspecting database states.
To use the CLI for viewing activity history, you can query the system tables directly:
cockroach sql --insecure --execute="SELECT * FROM crdb_internal.statement_statistics;"
This will show the query statistics right in your terminal. This makes it easy to see what is happening in your database.
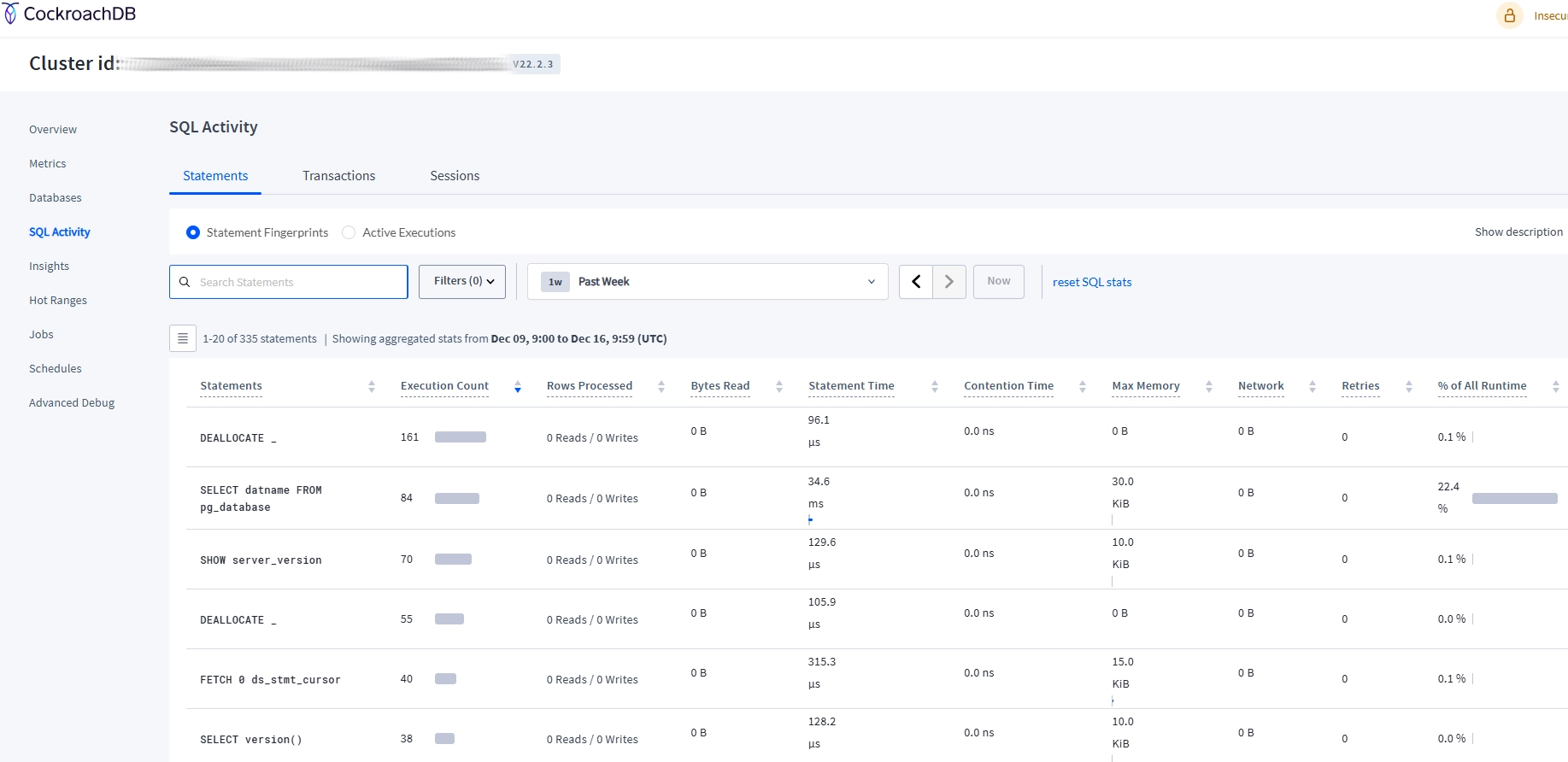
The CockroachDB Web UI for Monitoring Database Activity
The web-based UI for CockroachDB is another powerful tool for monitoring database activity. The CockroachDB Admin UI lets you see and manage the database easily. You can view detailed information about your system’s performance, transactions, and how queries run.
Connecting to the CockroachDB Web UI
To connect to the CockroachDB web UI, you must first have CockroachDB running and access to the cluster. Here’s how to connect:
- Open your browser and navigate to the CockroachDB Admin UI, typically accessible at http://localhost:8080.
- Enter your connection credentials if prompted (username and password).
- Once logged in, you can explore various tabs to monitor database health and activities.
- Click on the “SQL Activity” tab to see information about database activity history.
Integrating with DataSunrise
CockroachDB has built-in tools to track database activity. However, third-party tools like DataSunrise add more monitoring and security. DataSunrise is a complete database security solution. It offers strong auditing features. You can track and monitor database activity. It helps enforce security policies and protects sensitive data.
Setting Up DataSunrise Integration
Assuming DataSunrise is installed, to get started with DataSunrise for CockroachDB you first need to set up an instance. Here’s a basic walkthrough:
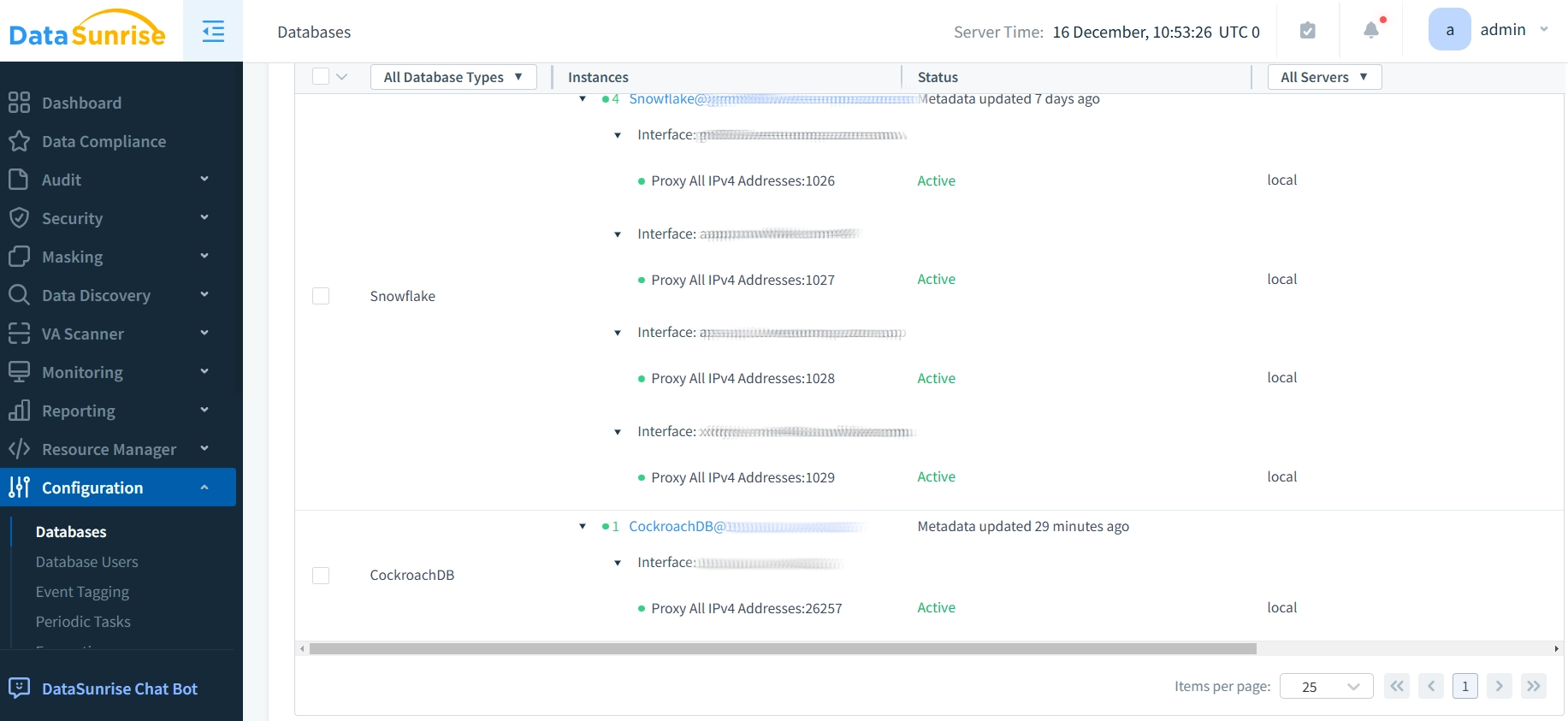
- Open DataSunrise dashboard, select “Add New Database” and input your CockroachDB connection details. You can see your instance in the “Databases” tab
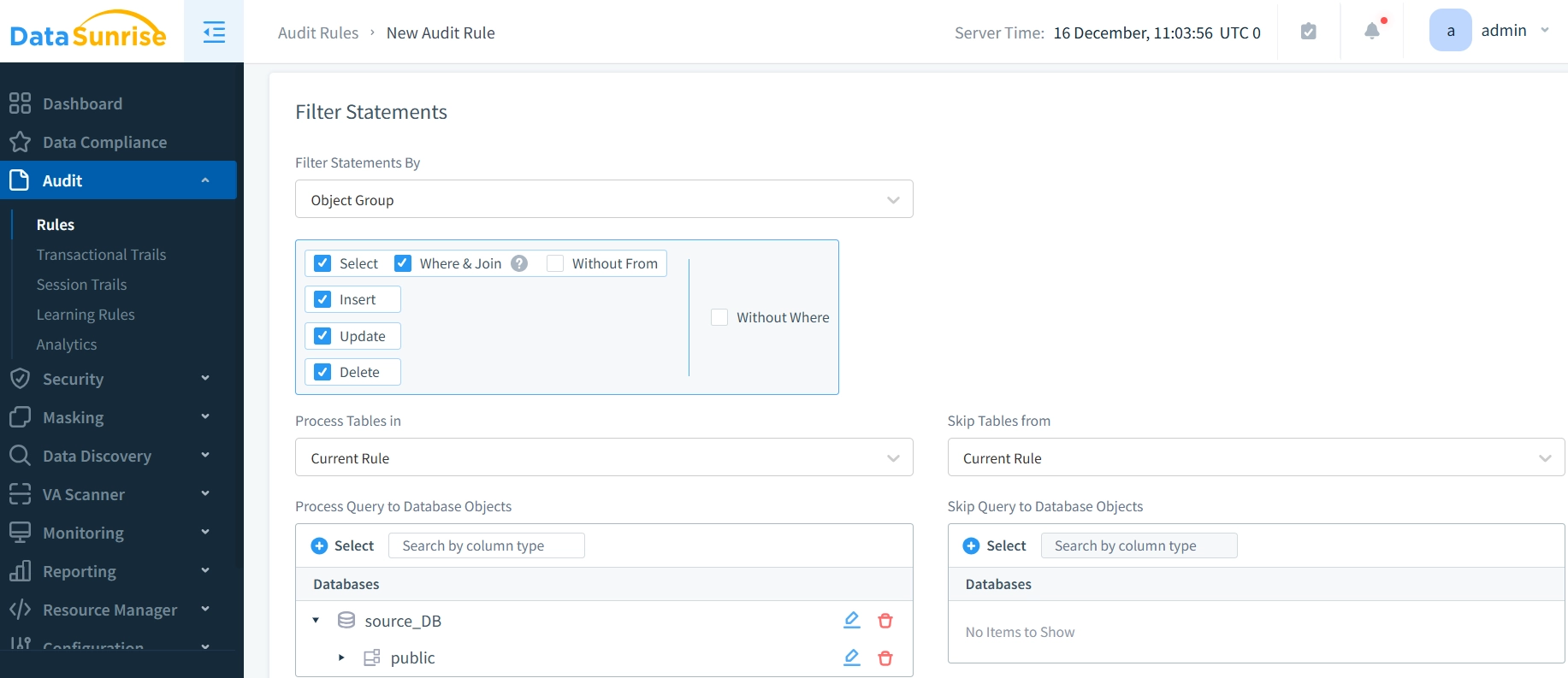
- In “Audit” create rules to specify which database events to track. Choose users, operations, and database objects to monitor
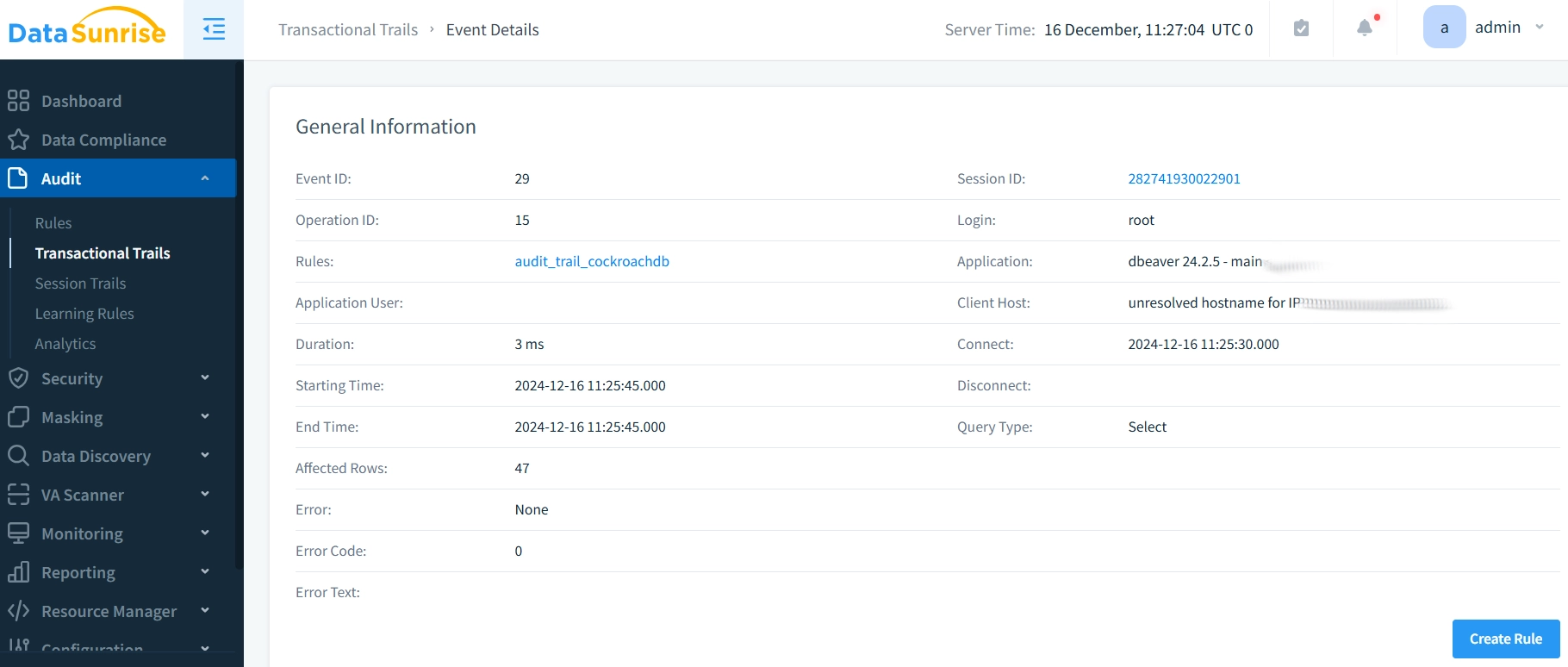
- Access the “Transactional Trails” to view real-time database operations. Filter events by time, user, or operation type to analyze specific activities. Click on one of the event to see detailed information
Benefits of Using DataSunrise
DataSunrise is a strong database security tool. It improves CockroachDB’s features, especially for monitoring and securing Database Activity History. Here are the key benefits of integrating DataSunrise:
1. Centralized Management
DataSunrise offers a single platform to manage many CockroachDB instances. This makes it easier to apply security rules and watch database activity across the whole system. This centralization helps reduce complexity and ensures uniform security practices.
2. Real-Time Activity Monitoring
With DataSunrise, administrators can monitor database activity in real time. It tracks all operations and immediately alerts you to any unauthorized or suspicious activities. This ensures timely responses to potential security issues.
3. Dynamic Data Masking
DataSunrise enables dynamic data masking, which ensures that sensitive information (like personal data or financial records) is concealed from unauthorized users. Even if someone has access to the database, they will only see masked data. This is based on set rules. It helps improve data privacy and compliance.
4. Audit and Compliance Reporting
DataSunrise simplifies the process of meeting regulatory requirements by generating detailed, customizable audit logs. These logs keep track of all database actions. They show who accessed or changed data. This helps organizations follow data protection laws like GDPR, HIPAA, and CCPA.
5. Granular Access Control
DataSunrise allows for role-based access control (RBAC), enabling administrators to restrict access to sensitive data and actions. This helps prevent unauthorized access and ensures that only authorized users can perform specific tasks on the database.
6. Seamless Integration with CockroachDB
DataSunrise integrates smoothly with CockroachDB, enhancing its native security features without complicating database performance. It works in the background to provide real-time monitoring, auditing, and data protection, ensuring secure database operations.
7. Scalability
As your CockroachDB instance grows, DataSunrise grows with it. This keeps security measures and activity monitoring effective, no matter the database size or complexity.
8. Simplified Compliance
DataSunrise helps you follow global data privacy rules. It offers tools for auditing, masking, and tracking sensitive data in your CockroachDB system. This is important for meeting regulatory requirements.
Best Practices for Database Activity History
Effective database activity monitoring requires a multi-faceted approach across four key areas:
- Activity Monitoring: Start with establishing a robust monitoring routine by scheduling daily log reviews and implementing automated alerts for any suspicious patterns. Performance monitoring should be part of this process to ensure tracking mechanisms don’t impact database operations.
- Data Retention: Organizations need clear policies that balance compliance requirements with system performance. This involves regular archiving of historical data while maintaining easy access to recent activity logs. Consider implementing automated archival processes to maintain consistent record-keeping without manual intervention.
- Security Integration: This forms another crucial aspect of activity history management. It includes implementing proper access controls and following the principle of least privilege for all database operations. Third-party solutions like DataSunrise can enhance these security measures by providing additional layers of protection and centralized management of security policies.
- Regular Audits: Security audits help make sure all monitoring systems work properly. They also ensure compliance with important regulations. These audits should examine both the effectiveness of native CockroachDB tracking features and any integrated security tools.
Conclusion
Database Activity History represents a cornerstone of modern database security and compliance strategies. CockroachDB’s native capabilities provide organizations with fundamental tools for tracking, monitoring, and auditing database operations effectively. From SQL-based activity tracking to comprehensive web UI monitoring, these features establish a strong foundation for maintaining data security and operational visibility.
As organizations grow and security requirements become more complex, specialized tools like DataSunrise complement CockroachDB’s native capabilities. DataSunrise’s comprehensive security suite enhances activity monitoring with features such as dynamic data masking, sophisticated audit trails, and centralized security management. This integrated approach helps organizations meet regulatory requirements while maintaining operational efficiency.
To explore these capabilities firsthand, visit DataSunrise’s website and schedule an online demo of our database security platform.
Next
