
Compliance-Based Database Auditing

Compliance-Based Database Auditing for Healthcare
Healthcare organizations face stringent data security requirements under regulations such as the Health Insurance Portability and Accountability Act (HIPAA). Protecting patient health information (PHI) isn’t just about security—it’s about ensuring accountability through effective database auditing. With an emphasis on data auditing, organizations can meet HIPAA requirements while maintaining system performance and operational efficiency.
This article will help you set up a compliance auditing strategy using SQL and tools like DataSunrise. This will ensure your healthcare systems are secure and meet health system requirements.
Why Database Auditing is Essential in Healthcare
Healthcare organizations manage vast amounts of sensitive data, including patient medical records, billing details, and demographic information. This data, collectively referred to as Protected Health Information (PHI), forms the foundation of patient care and operational efficiency. However, it also brings important security challenges. Regulations like the Health Insurance Portability and Accountability Act (HIPAA) set strict rules for protecting PHI.
Database auditing is important for making sure healthcare systems follow HIPAA rules. It does more than just meet regulations. Auditing helps find security risks, keeps operations clear, and protects against data breaches.
Cybercriminals often target healthcare data, so strong auditing is essential. It helps build trust and ensures compliance with the law.
Key Requirements of HIPAA for Database Auditing
To understand the importance of database auditing in healthcare, it’s critical to examine HIPAA’s specific mandates:
- Access Tracking
- Activity Monitoring
- Audit Retention
- Incident Alerts
- Data Integrity and Security
Organizations must keep clear records of who accessed or changed PHI. They should also note what actions they took and when. This detail ensures accountability and helps find unauthorized access, whether it was intentional or accidental.
HIPAA requires healthcare providers to watch all activities involving important tables that hold sensitive data. These activities include SELECT (getting data), UPDATE (changing data), DELETE (removing data), and INSERT (adding data). Tracking these actions helps organizations control how they use and access their data.
Another key part of HIPAA compliance is securely storing and keeping audit logs. You must keep these records for at least six years. Laws or company policies may require you to keep them longer. Proper retention helps organizations review past data for investigations or compliance audits.
Healthcare providers are expected to implement systems that generate alerts for unauthorized access attempts or suspicious activities. If someone makes many failed login attempts or accesses restricted areas, the security team should receive immediate notification.
You must protect audit logs to stop tampering or unauthorized access. HIPAA highlights the need for encryption, access controls, and secure storage to keep these logs safe.
Customizing Auditing to Meet HIPAA Standards with native SQL Server tools
Customizing database auditing to meet HIPAA standards is important for healthcare organizations. A one-size-fits-all approach can create issues. It may fill systems with extra logs and slow down performance.
Instead, a focused strategy tracks only important data and operations. This reduces overhead and keeps compliance in check. SQL Server provides strong built-in tools such as views, stored procedures, and triggers. These tools help organizations build detailed auditing solutions.
Healthcare databases store large amounts of sensitive information, including patient records, billing data, and prescription histories. Monitoring every action in the database can create too much data and slow down the system. By customizing your auditing settings, you can track only high-risk or high-priority actions. This helps you use resources better while staying compliant with HIPAA’s strict rules.
Tailored auditing helps to focus on finding incidents more effectively. For example, instead of checking all SELECT operations, you can look at specific tables or columns with PHI. This targeted approach lowers false positives and ensures quick responses to real threats.
Identifying Data to Audit
Before you set up your auditing settings, find the data and actions that matter most for HIPAA compliance. This step is key to meeting the necessary requirements. Start by sorting database objects that hold sensitive information and checking their risk levels. Common examples include:
- Patients Table: Stores demographic and medical information.
- Prescriptions Table: Tracks medication details and prescribing history.
- MedicalRecords Table: Contains diagnostic information, treatment plans, and clinical notes.
Track the following actions:
- SELECT: Who is viewing patient data?
- INSERT/UPDATE: Who is adding or modifying information?
- DELETE: Who is removing records?
Example: Creating an Audit with SQL
Let’s say you want to monitor all SELECT operations on the Patients table.
Create an Audit Specification:
USE master; GO CREATE SERVER AUDIT PatientAccessAudit TO FILE (FILEPATH = 'C:\Audits\', MAXSIZE = 50 MB); GO ALTER SERVER AUDIT PatientAccessAudit WITH (STATE = ON); GO
Define the Audit Policy for Your Database:
USE HealthDB; GO CREATE DATABASE AUDIT SPECIFICATION PatientTableAudit FOR SERVER AUDIT PatientAccessAudit ADD (SELECT ON dbo.Patients BY public); GO ALTER DATABASE AUDIT SPECIFICATION PatientTableAudit WITH (STATE = ON);
Query the Audit Logs:
SELECT
event_time,
server_principal_name,
database_name,
object_name,
statement
FROM
sys.fn_get_audit_file ('C:\Audits\*.sqlaudit', DEFAULT, DEFAULT);
This example demonstrates how to audit table-specific activities, ensuring compliance with requirements for health systems.
Connecting to the Database for Auditing
The key to a good auditing strategy is a secure connection to your database. This connection lets administrators and scripts monitor, query, and manage audit logs. It also helps enforce compliance rules.
To connect to a SQL Server database, you can use tools like SQL Server Management Studio (SSMS). You can also connect using programming languages such as Python.
A secure connection keeps communication safe between your system and the database. It prevents unauthorized access and tampering.
For healthcare systems that manage sensitive patient data, encrypted connections are crucial. Strong authentication methods are also essential. These steps help protect data integrity and confidentiality. They ensure compliance with HIPAA requirements.
SSMS provides an intuitive interface for managing databases and auditing configurations. Here’s how to establish a connection:
- Launch SSMS: Open the SQL Server Management Studio application.
- Enter Server Details: Input your server name, authentication type (Windows or SQL Server Authentication), and credentials.
- Connect to the Database: Select the target database (e.g., HealthDB) to start managing tables, views, and audit logs.
Once connected, you can easily navigate the database structure, execute queries, and configure auditing specifications.
Programmatic Connections with Python: Many developers prefer to connect to the database programmatically for better automation and auditing. Python has useful libraries like pyodbc that make it easy to connect to databases.
Example: Python Connection to SQL Server
Here’s a simple Python script to connect to a SQL Server database:
import pyodbc
# Connection details
connection = pyodbc.connect(
'DRIVER={SQL Server};'
'SERVER=your_server;'
'DATABASE=HealthDB;'
'UID=your_user;'
'PWD=your_password;'
)
print("Connected to the database.")
You can integrate this connection into scripts that regularly query audit logs or enforce compliance rules.
Enhancing SQL Auditing with DataSunrise
SQL Server possesses robust in-built auditing mechanisms. Yet, the auditing enhancements from DataSunrise elevate these features, streamlining compliance and boosting efficiency.
Creating a DataSunrise Instance
- Launch DataSunrise: Assuming it is installed, log in to the web interface.
- Add Your Database: Navigate to the “Database Connection” tab and input your server details.
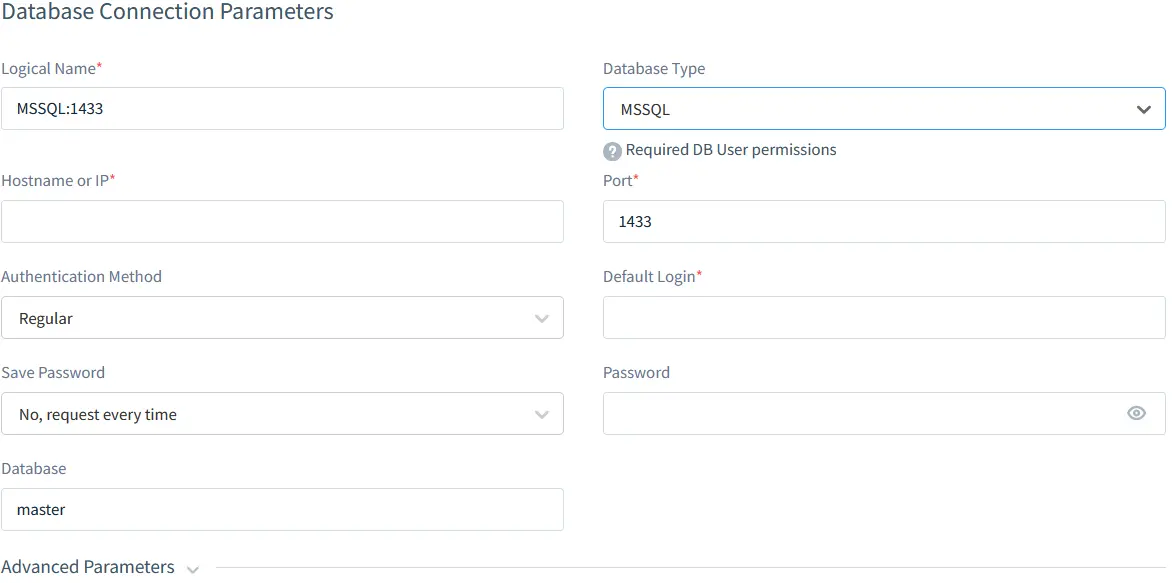
Creating a database server instance in DataSunrise
- Set Up Auditing Policies: Choose ready-made templates or make your own policies. You can track actions like SELECT, INSERT, or failed logins.
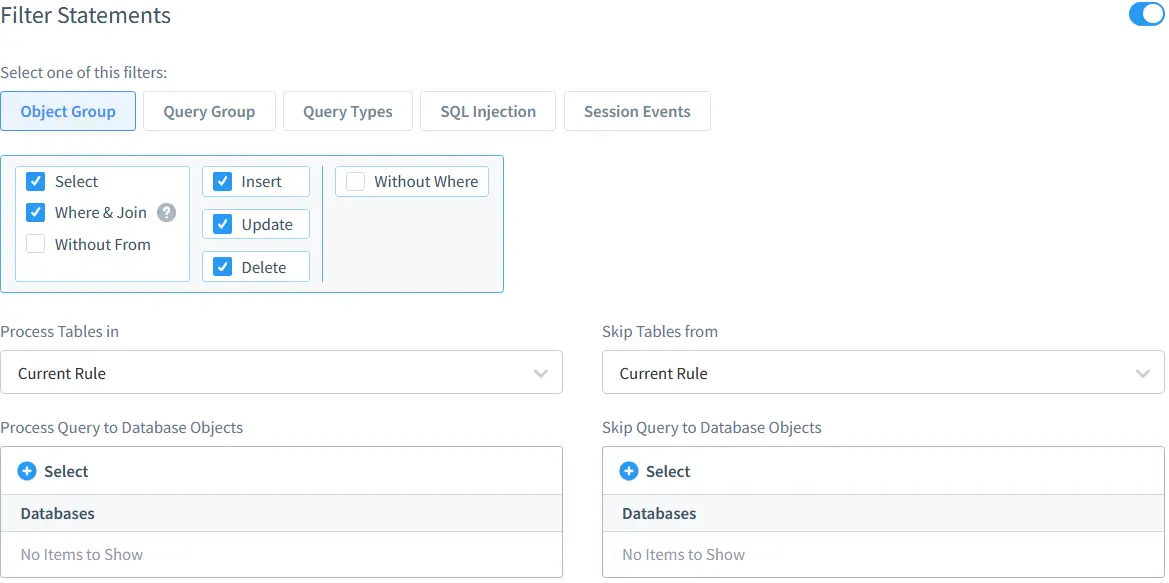
DataSunrise audit configuration screen
Viewing Audit Data in DataSunrise
DataSunrise provides intuitive dashboards where you can:
- Monitor real-time user activities.
- Configure alerts for suspicious events.
- Generate detailed compliance reports with a few clicks.
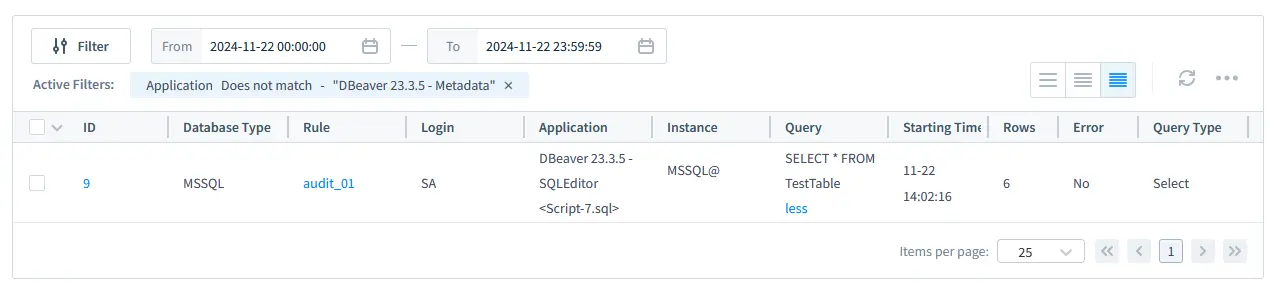
Transactional Trails event listing
Benefits of Centralized Auditing with DataSunrise
DataSunrise’s security suite brings together and standardizes control over all auditing rules. This offers great flexibility and is easy to use.
Advantages include:
- Customizable Policies: Tailor rules for specific tables or actions.
- Enhanced Performance: Offload resource-intensive auditing from your database server.
- Cross-Database Auditing: Monitor diverse database platforms from a single interface.
- Compliance Reporting: Quickly generate HIPAA-aligned audit logs.
Example: You can configure DataSunrise to alert administrators about unauthorized access to the MedicalRecords table, helping you respond proactively to potential breaches.
Challenges and Best Practices
Challenges
- Performance Impact: Extensive auditing may slow down systems. Mitigate this by auditing only high-risk activities.
- Log Management: Large audit logs can strain storage. Use retention policies to archive or summarize old logs.
Best Practices
- Review Audit Rules Regularly: Ensure policies align with evolving regulatory standards.
- Secure Audit Logs: Restrict access and encrypt logs to prevent tampering.
- Train Staff: Educate employees on the importance of data auditing and compliance.
Conclusion
Implementing database auditing for healthcare systems is important to protect sensitive data and meet HIPAA requirements. It also helps ensure accountability.
Organizations can use SQL’s powerful features and tools like DataSunrise auditing. This helps them create effective solutions. You can also scale these solutions to meet your needs.
DataSunrise’s flexible security suite makes auditing easier. It provides centralized control, real-time monitoring, and user-friendly dashboards. This helps ensure compliance while maintaining good performance.
Learn how DataSunrise can improve your database security. Go to DataSunrise.com for an online demo. See how we can boost your data protection plan.
