
CSPM: Cloud Security Posture Management and Its Benefits

Cloud computing has changed the way businesses operate, offering scaling, flexibility, and cost-effectiveness. However, the rapid adoption of cloud services has also introduced new security challenges. Organizations must ensure that their cloud infrastructure remains secure and compliant with industry standards and regulations. This is where Cloud Security Posture Management (CSPM) comes into play.
What is Cloud Security Posture Management?
CSPM helps organizations monitor and fix security risks in their cloud environments using tools and practices. It provides a comprehensive view of cloud security posture, enabling them to detect misconfigurations, vulnerabilities, and compliance issues across multiple cloud platforms.
CSPM tools scan cloud infrastructure to identify potential security weaknesses. They compare the current configuration against best practices and industry standards. This helps organizations maintain a strong security posture and ensure that their cloud environments remain secure and compliant.
CSPM Structure
The Need for CSPM in the Cloud Era
The adoption of cloud services has grown in recent years. Organizations are moving their critical workloads and sensitive data to the cloud to take advantage of its benefits. In cloud security, organizations are responsible for securing their data and applications.
Misconfigurations and human errors are among the leading causes of cloud security breaches. A single misconfigured setting can expose sensitive data to unauthorized access, leading to data breaches and compliance violations. CSPM helps organizations identify and remediate these misconfigurations before attackers can exploit them.
Moreover, the dynamic nature of cloud environments makes it challenging to maintain a consistent security posture. Setting up, changing, or taking down cloud resources quickly can make managing security settings difficult. CSPM allows organizations to monitor their cloud infrastructure in real-time. This helps them to promptly identify and resolve security issues.
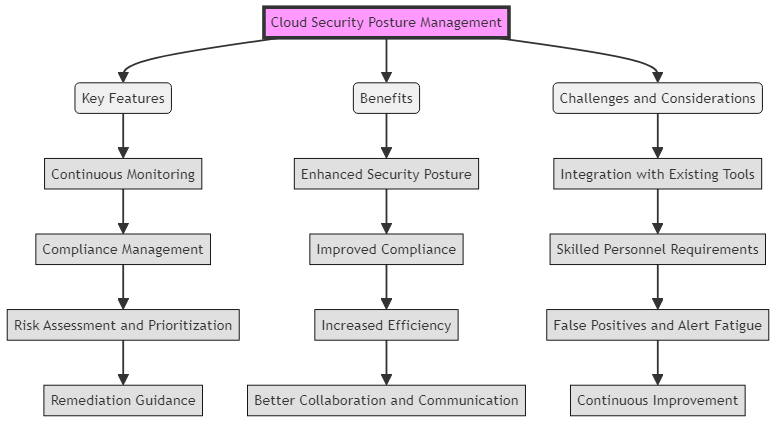
Key Features of CSPM Solutions
CSPM solutions offer a range of features that help organizations strengthen their cloud security posture. Some of the key features include:
- Continuous Monitoring:
CSPM tools monitor cloud environments for security risks and misconfigurations. They scan cloud resources, including virtual machines, storage buckets, and network settings, to identify potential weaknesses. This helps organizations find and fix security problems quickly, lowering the chance of data breaches and compliance issues.
- Compliance Management:
CSPM solutions help organizations ensure compliance with industry standards and regulations, such as HIPAA, PCI DSS, and GDPR. They provide pre-built compliance templates and alert organizations to any deviations from the required security controls. This helps organizations maintain a strong compliance posture and avoid costly penalties and damage.
- Risk Assessment and Priority:
CSPM tools assess security risks based on data sensitivity and likelihood of exploitation. The tools take into account factors such as the sensitivity of the data. They also consider the probability of the data being exploited. They prioritize risks based on their criticality, enabling organizations to focus their remediation efforts on the most significant threats.
- Remediation Guidance:
CSPM solutions provide actionable remediation guidance for identified security issues. They provide detailed guidance for fixing mistakes and weaknesses, helping security teams quickly and effectively address security threats. Some CSPM tools even offer automated remediation capabilities, enabling organizations to fix security issues with minimal manual intervention.
Benefits of Implementing CSPM
Implementing CSPM offers several benefits for organizations that are leveraging cloud services. Some of the key benefits include:
Enhanced Security Posture:
CSPM helps organizations strengthen their overall security posture by providing continuous monitoring and risk assessment of their cloud environments. It enables organizations to identify and remediate security risks proactively, reducing the likelihood of data breaches and cyber attacks. Organizations can protect data and maintain trust by having strong security measures in place for customers and stakeholders.
Improved Compliance:
CSPM solutions help organizations ensure compliance with industry standards and regulations. They provide pre-built compliance templates and alert organizations to any deviations from the required security controls. This helps organizations avoid costly penalties and damage associated with non-compliance. Organizations can show they value protection of data and earn trust from customers and partners by staying compliant.
Increased Efficiency:
CSPM tools help automate tasks like security assessments and compliance checks for cloud security management. This frees up security teams to focus on more strategic initiatives and reduces the risk of human errors. By streamlining security operations, organizations can improve their overall efficiency and reduce the cost of managing cloud security.
Better Collaboration and Communication:
CSPM solutions provide a centralized view of cloud security posture, enabling security teams to collaborate more effectively. They offer dashboards and reports that provide a clear understanding of the security risks and compliance status. This helps security teams communicate effectively with app owners and business leaders. It ensures that everyone collaborates to maintain strong security.
Challenges and Considerations
CSPM has benefits, but organizations should also consider challenges when implementing CSPM solutions. Some of the key challenges include:
- Integration with Existing Tools and Processes:
Organizations may have security tools like scanners and response procedures already in place to protect against threats. Integrating CSPM solutions with these existing tools and processes can be challenging and may require significant effort and resources.
Organizations should assess their current security measures. They should ensure they can seamlessly integrate CSPM solutions without duplicating efforts. This will help in maintaining a cohesive security strategy.
Skilled Personnel:
Implementing and managing CSPM solutions requires specialized skills and knowledge. Organizations may need to invest in training and hiring personnel with expertise in cloud security and CSPM tools. This can be a significant investment, particularly for smaller organizations with limited resources. Companies should assess their abilities and think about teaming up with MSSPs or other experts for help with CSPM projects.
This collaboration can enhance the effectiveness of their security measures. By working with outside experts, companies can leverage their specialized knowledge and experience in security. This partnership helps companies stay safe from changing threats and protect their systems and data.
- False Positives and Alert Fatigue:
CSPM tools can generate a large number of alerts and notifications, some of which may be false positives. This can cause alert overload and make it hard for security teams to focus on and address real security threats. Organizations should carefully configure their CSPM solutions to minimize false alerts and ensure that alerts are valuable to them.
- Continuous Improvement:
Maintaining a strong cloud security posture is an ongoing process that requires continuous improvement and adaptation. Organizations need to regularly update their CSPM strategies and tools. This is important to stay current with changes in cloud environments and new threats.
Conclusion
Cloud Security Posture Management is a critical component of any company’s cloud security strategy. It helps organizations protect their cloud systems by watching for problems, evaluating risks, and advising on how to solve issues. This ensures compliance with industry standards and regulations.
Implementing CSPM offers several benefits, including enhanced security, improved compliance, increased efficiency, and better collaboration and communication. Organizations must be aware of challenges when using CSPM. These challenges include integrating with current tools, having skilled staff, dealing with false alarms, alert fatigue, and constantly improving.
Investing in CSPM and addressing challenges helps organizations keep their cloud environments secure and compliant. This allows them to fully benefit from cloud computing while reducing the risk of security breaches and compliance issues.
