
Data Activity History
As data breaches and cyber threats become increasingly sophisticated, organizations must prioritize monitoring and managing data activity history. This process is crucial for safeguarding sensitive information, ensuring compliance with data protection regulations, and mitigating potential risks. If you work with data, it’s important to know how to monitor and manage the history of data activities.
The Basics of Data Activity History
Data activity history refers to the systematic recording of data interactions within a database or data management system. This includes tracking who accessed the data, what changes were made, and when these actions occurred. By maintaining a comprehensive log of these activities, organizations can detect unauthorized access, investigate suspicious behavior, and comply with regulatory requirements.
Why Is Data Activity History Important?
In an environment where data is constantly being accessed, modified, and transferred, keeping track of these actions is vital. The history of data activity and the data activity monitoring fulfill several crucial functions:
Security: By monitoring data access, organizations can detect and respond to potential threats in real-time.
Organizations must keep detailed records of data access and changes to follow regulations like GDPR, HIPAA, and PCI-DSS.
Compliance: A robust data activity history allows for thorough audits, ensuring transparency and accountability within the organization.
Approaches to Tracking Data Activity History
Organizations can monitor data activity history using tools provided by database systems or third-party tools designed for improved monitoring and security. These tools allow organizations to track and analyze data activity over time. Native tools are built-in features of database systems, while third-party tools are developed by external vendors. Both types of tools offer organizations the ability to enhance their data monitoring and security measures.
Triggers Approach to the Data Activity Monitoring
Monitoring data history with triggers in an SQL database involves creating triggers that automatically capture changes to a table’s data (inserts, updates, and deletes) and store these changes in an audit or history table. While this method effectively tracks data changes, it may not be the simplest or most efficient solution, especially in high-transaction environments, as triggers can add overhead and complexity. However, it is a straightforward approach when simplicity and ease of implementation are key priorities. The following code is written in PostgreSQL syntax, demonstrating how to handle triggers.
To prepare the test data, create the main table:
CREATE TABLE employees ( employee_id INT PRIMARY KEY, name VARCHAR(100), department VARCHAR(100), salary DECIMAL(10, 2) );
Next, create an audit (history) table for the test data:
CREATE TABLE employee_audit ( audit_id SERIAL PRIMARY KEY, employee_id INT, action_type VARCHAR(10), -- 'INSERT', 'UPDATE', 'DELETE' action_time TIMESTAMP DEFAULT CURRENT_TIMESTAMP, old_name VARCHAR(100), old_department VARCHAR(100), old_salary DECIMAL(10, 2), new_name VARCHAR(100), new_department VARCHAR(100), new_salary DECIMAL(10, 2) );
Create a trigger for INSERT:
CREATE OR REPLACE FUNCTION fn_employee_insert() RETURNS TRIGGER AS $$ BEGIN INSERT INTO employee_audit (employee_id, action_type, new_name, new_department, new_salary) VALUES (NEW.employee_id, 'INSERT', NEW.name, NEW.department, NEW.salary); RETURN NEW; END; $$ LANGUAGE plpgsql;
CREATE TRIGGER trg_employee_insert AFTER INSERT ON employees FOR EACH ROW EXECUTE FUNCTION fn_employee_insert();
To test an INSERT trigger in SQL, you need to perform an insert operation on the table associated with the trigger. After the insertion, you can check the corresponding audit (or history) table to ensure that the trigger executed correctly and logged the necessary data.
INSERT INTO employees (employee_id, name, department, salary) VALUES (1, 'John Doe', 'HR', 50000.00);
After performing the INSERT, query the employee_audit table to verify that the trigger correctly logged the insert operation.
SELECT * FROM employee_audit;
Here is the audit record retrieved from the employee_audit table using DBeaver:
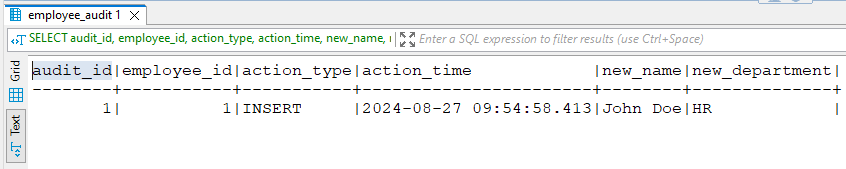
Advanced Native Tools
Using triggers to monitor data changes provides a way to capture the history of changes automatically without requiring changes to application code. However, this method can be complex to maintain and may impact performance due to the overhead introduced by triggers. Alternative approaches, like using database change data capture (CDC) mechanisms or application-level auditing, might be simpler or more efficient, depending on the use case.
Most modern database systems come equipped with built-in tools for tracking data activity. These tools offer basic functionality, such as logging data access events, recording changes to records, and generating audit trails. Examples include:
SQL Server Audit: Allows administrators to track and log events at the server and database levels.
Oracle Audit Vault: Provides comprehensive auditing capabilities, including the ability to monitor user activities and database changes.
Native tools are useful, but they may lack advanced features required for comprehensive data monitoring. This is especially true in complex or multi-database environments.
Third-Party Tools
Organizations can use third-party tools like DataSunrise for better data monitoring with a variety of features. These tools provide advanced capabilities, such as real-time alerts, detailed reporting, and centralized management across multiple databases.
Why Choose DataSunrise?
DataSunrise stands out as a leading solution for data security and monitoring. It offers a centralized and uniform approach to tracking data activity history across diverse environments. DataSunrise provides a robust platform for monitoring and protecting your data. This can be done whether the data is stored on-premises, in the cloud, or across various databases.
Database Instance and Data Activity History
Assuming you have already installed DataSunrise, setting up a database instance and viewing data activity history is straightforward. Here’s a step-by-step guide:
Step 1: Access the Console
Log in to the DataSunrise management console using your credentials. The console is the central hub where you can configure, monitor, and manage all aspects of data security. The Dashboard view opens as you logged in the DataSunrise:
Step 2: Configure Data Sources
Once logged in, the first step is to configure your data sources or instances. DataSunrise supports various databases, including SQL Server, Oracle, MySQL, and more. To add a data source:
- Navigate to the “Configuration – Databases” tab.
- Click “+ Add Database.”
- Enter the necessary details, such as database type, connection string, and authentication credentials.
- Save the configuration.
The image below illustrates the PostgreSQL Instance setup:
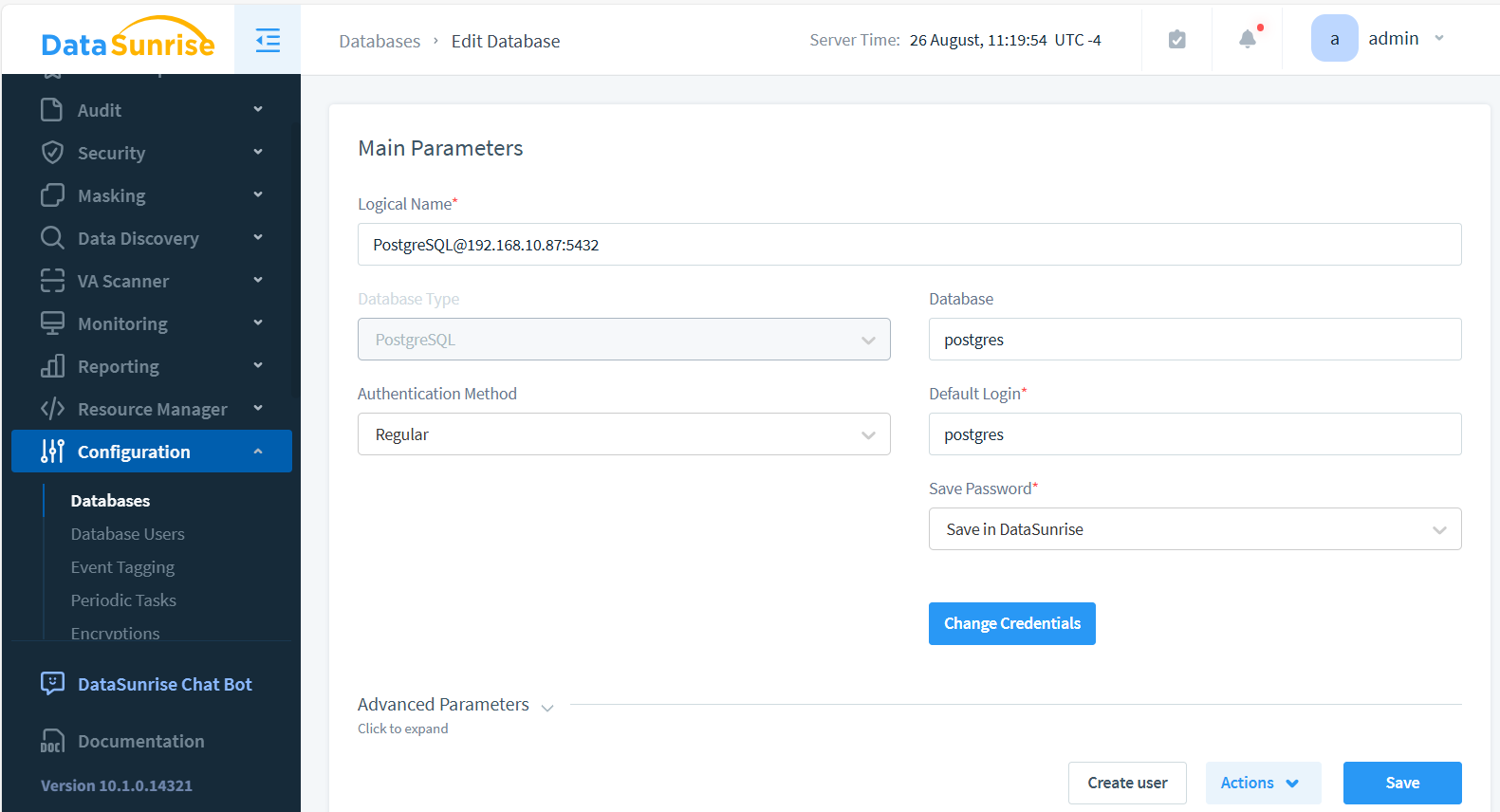
Step 3: Enable Data Activity Monitoring
With your data sources configured, you can now enable data activity monitoring:
- Go to the “Audit” section of the console.
- Create new Audit Rule.
- Select the instance you want to monitor and select objects to monitor.
- Save the Rule.
The image below showcases four rules for various on-premise databases and one for AWS Athena Service. All these rules are integrated into a single data security solution, allowing you to manage and control them uniformly from one centralized platform.
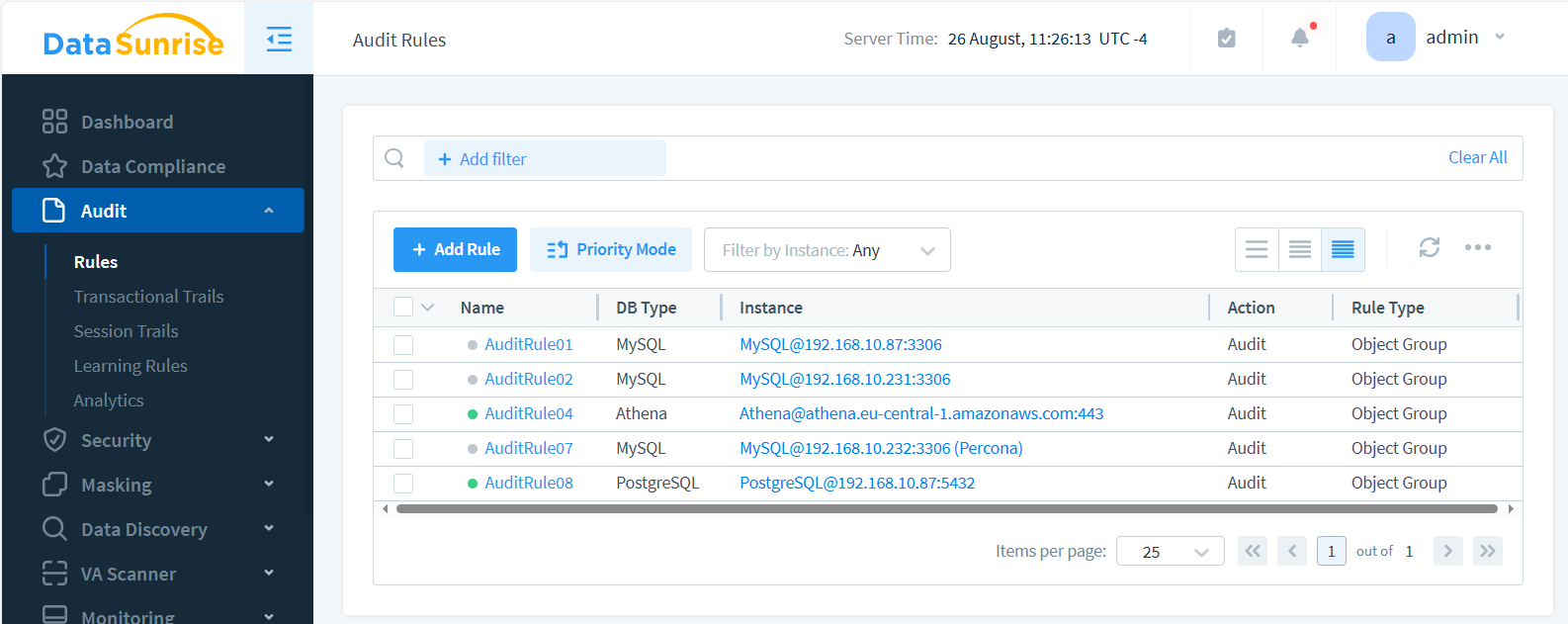
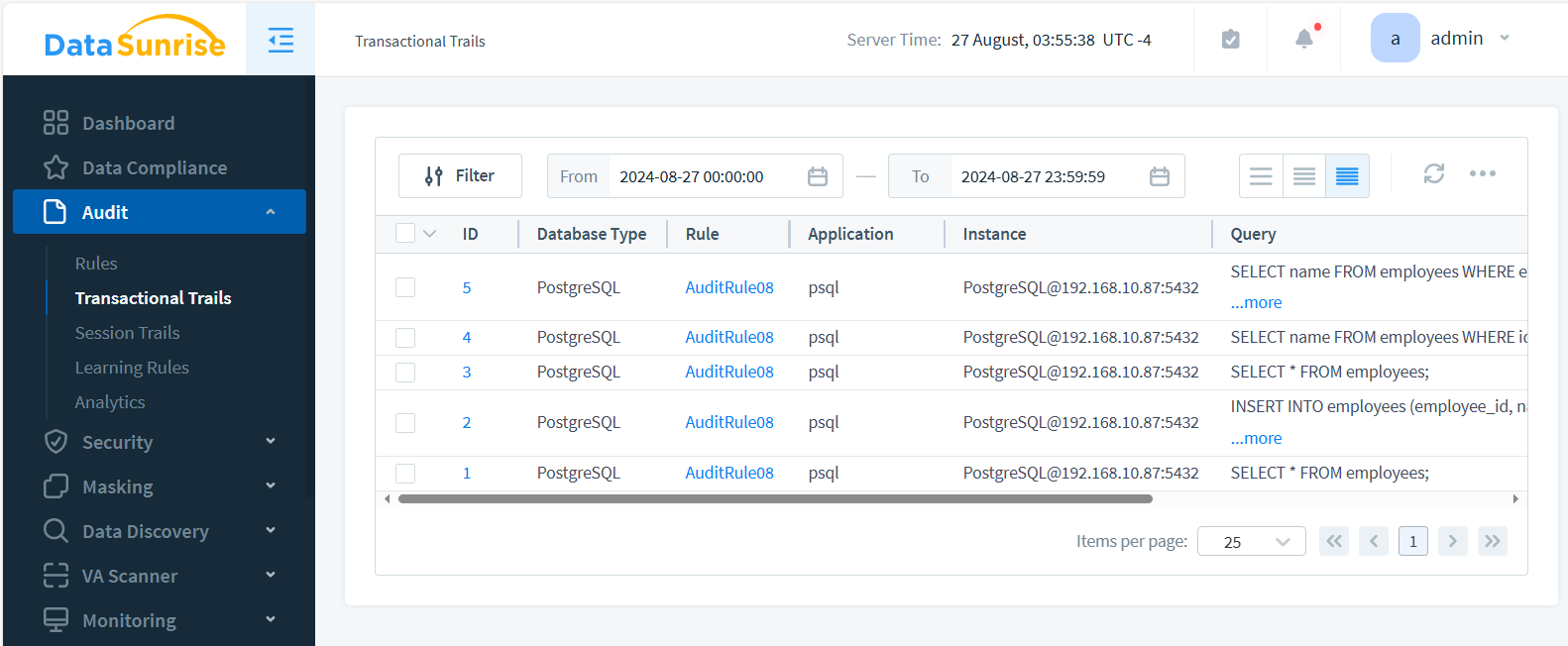
Step 4: View Data Activity History
Once monitoring is enabled, you can view the data activity history in real-time:
- Configure your data-consuming clients to connect through the DataSunrise instance proxy and perform several test requests to ensure proper functionality in Proxy mode. For instructions on setting up audits in other modes, please refer to the User Guide.
- Navigate to the “Audit” page.
- Select the desired trail (Session or Transactional Trails) in the drop-down menu.
- Export the logs if necessary for further analysis or compliance reporting.
Benefits of Using DataSunrise for Centralized Monitoring
Using DataSunrise for monitoring offers several significant benefits:
It lets you control and watch over all data activity in your organization from one place.
Uniform Approach: With our solution, you can apply consistent monitoring rules and policies across different databases and environments.
DataSunrise offers strong security with real-time alerts and reports to help you prevent potential threats effectively.
Compliance: Our Compliance Manager simplifies the process of maintaining compliance with regulatory requirements by providing comprehensive logs and audit trails.
Ensuring Data Compliance with DataSunrise
Maintaining data compliance is a critical aspect of data management, especially with the increasing number of regulations governing data privacy and protection. DataSunrise offers a suite of tools designed to help organizations meet these regulatory requirements. By using DataSunrise, you can:
Automate Compliance Reporting: Generate detailed reports that demonstrate compliance with regulations like GDPR and HIPAA.
Implement Access Controls: Ensure that only authorized users have access to sensitive data.
Audit Data Access: Keep a detailed record of who accessed what data and when. This makes it easier to respond to audits or investigations.
Summary and Conclusion
Keeping track of data activity is important for managing data effectively. It helps organizations protect their data, follow rules, and address security risks.
It’s important to monitor data activity. You can use built-in tools or advanced solutions like DataSunrise. A strong monitoring system is essential.
By leveraging DataSunrise’s advanced features, you can centralize your monitoring efforts, apply uniform rules across all data sources, and enhance your organization’s security posture. Tracking, analyzing, and reporting data activity in real-time helps protect your data. It also shows compliance with data protection rules.
DataSunrise provides flexible and user-friendly tools for database security, including data activity history, data masking, and other essential features. To try DataSunrise and improve your data security, visit our website to schedule a demo. Get a hands-on experience and see how it can help you.
Ensure your data is protected, compliant, and monitored effectively with DataSunrise. Visit our website to learn more.
