
Data Audit for Amazon DynamoDB: Best Practices, Logging, and Advanced Security Solutions

Introduction
Amazon DynamoDB, a popular NoSQL database service, offers robust performance and scalability. However, without proper auditing, you might miss critical insights into user behavior and potential security threats. This article explores the essentials of data audit for Amazon DynamoDB, focusing on why third-party audit solutions are often preferred and how to implement logging for query information.
Did you know that according to a recent cybersecurity report, 60% of data breaches involve database vulnerabilities? This startling statistic underscores the importance of comprehensive database activity monitoring and auditing.
Understanding Data Audit for Amazon DynamoDB
What is Data Auditing?
Data auditing is the process of monitoring and recording database activities. For DynamoDB, this includes tracking queries, modifications, and access patterns. Effective auditing helps maintain data integrity, detect suspicious activities, and ensure compliance with regulations.
DataSunrise allows capturing the Session Trails and Transactional Trails. They contain different information on the data access. Below is an example of Session Trails:
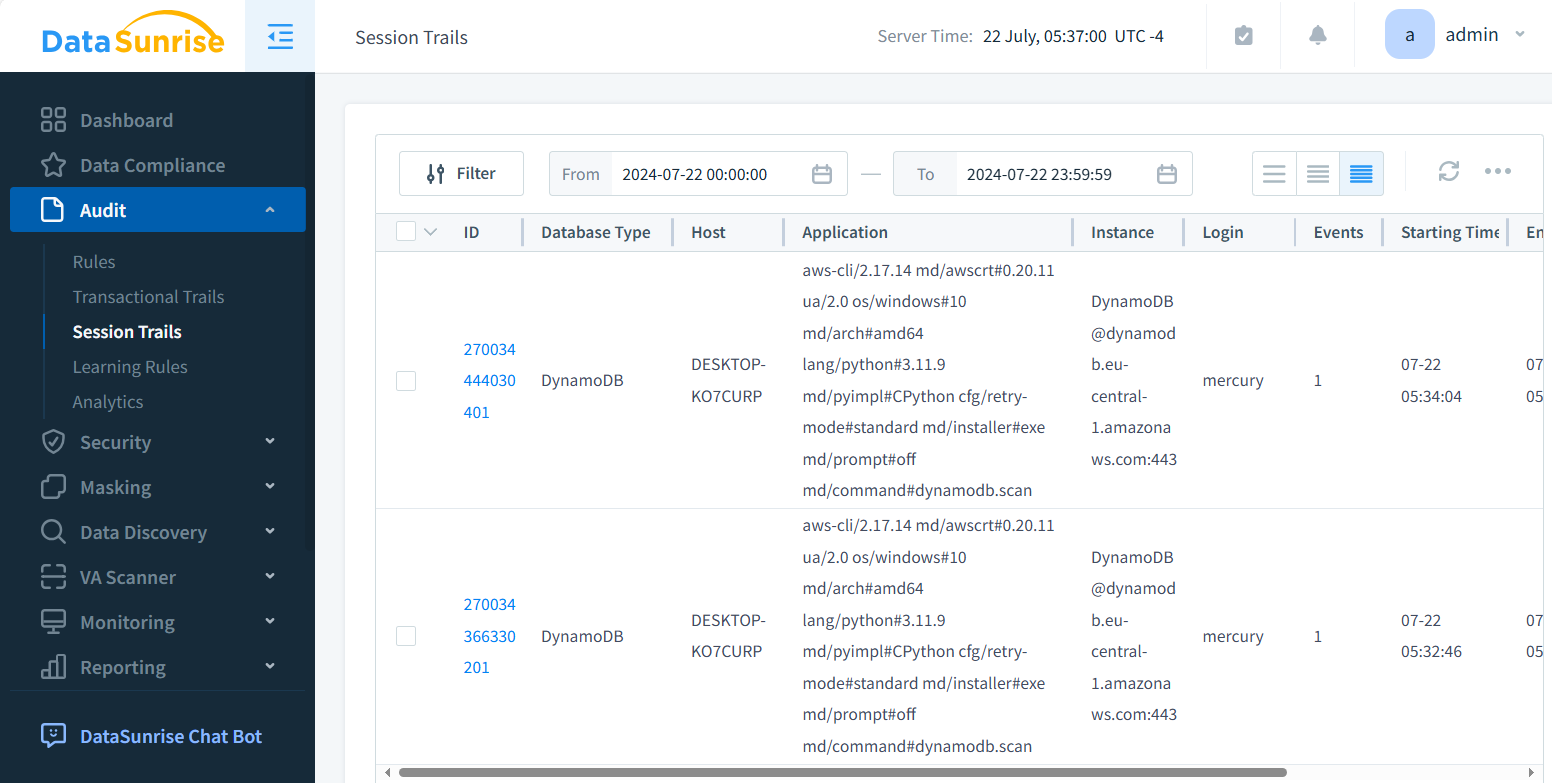
Why is Auditing Crucial for DynamoDB?
DynamoDB’s flexibility and scalability make it a popular choice for many applications. However, these features also introduce unique challenges for security and compliance. Auditing helps address these challenges by:
| Audit Feature | Why It’s Important | Possible Open-Source Alternative |
|---|---|---|
| Tracking user behavior | Helps identify patterns and anomalies in data access | ELK Stack (Elasticsearch, Logstash, Kibana) |
| Identifying potential security breaches | Enables quick detection and response to threats | OSSEC (Open Source HIDS SECurity) |
| Ensuring regulatory compliance | Maintains adherence to industry standards and regulations | OpenAudit |
| Optimizing database performance | Identifies inefficient queries and usage patterns | pgBadger (for PostgreSQL) |
Third-Party Audit Solutions: A Preferred Choice
Advantages of Third-Party Tools
While Amazon provides basic logging through AWS CloudTrail, many organizations opt for third-party audit solutions like DataSunrise. Here’s why:
- Comprehensive coverage: Third-party tools often offer more detailed monitoring capabilities.
- User-friendly interfaces: These solutions typically provide intuitive dashboards for easy analysis.
- Advanced analytics: Many third-party tools include AI-powered anomaly detection.
- Cross-platform compatibility: They can often integrate with multiple database types. Visit our website and use the chat-bot to inquire about DataSunrise database and data warehouse coverage.
Key Features to Look For
A thorough third-party audit tool for DynamoDB should provide a range of essential features. DataSunrise has all the needed features to monitor and check your data, whether it’s on-site or in the cloud.
Real-time monitoring allows you to watch database activities as they happen. This gives you immediate insights into user behavior and potential security risks.
You can set up alerts to get notifications for certain events or patterns. This way, we can promptly inform you about any suspicious activities.
Detailed reporting capabilities offer in-depth analysis of your database usage, helping you identify trends and anomalies over time.
Data masking features protect sensitive information by obscuring or encrypting it in audit logs, maintaining privacy and compliance.
Integration with security tools ensures DynamoDB audit works well with current security setup, creating a unified and efficient security system.
Implementing Logging in DynamoDB
Enabling CloudTrail Logging
CloudTrail offers a built-in option for logging data access events in DynamoDB. This feature provides basic auditing capabilities without additional tools. To start logging DynamoDB activities:
- Open the AWS Management Console
- Navigate to the CloudTrail service
- Create a new trail or use an existing one
- Enable logging for DynamoDB events
Note that this action incurs additional costs based on log pricing. The resulting output may resemble the following:
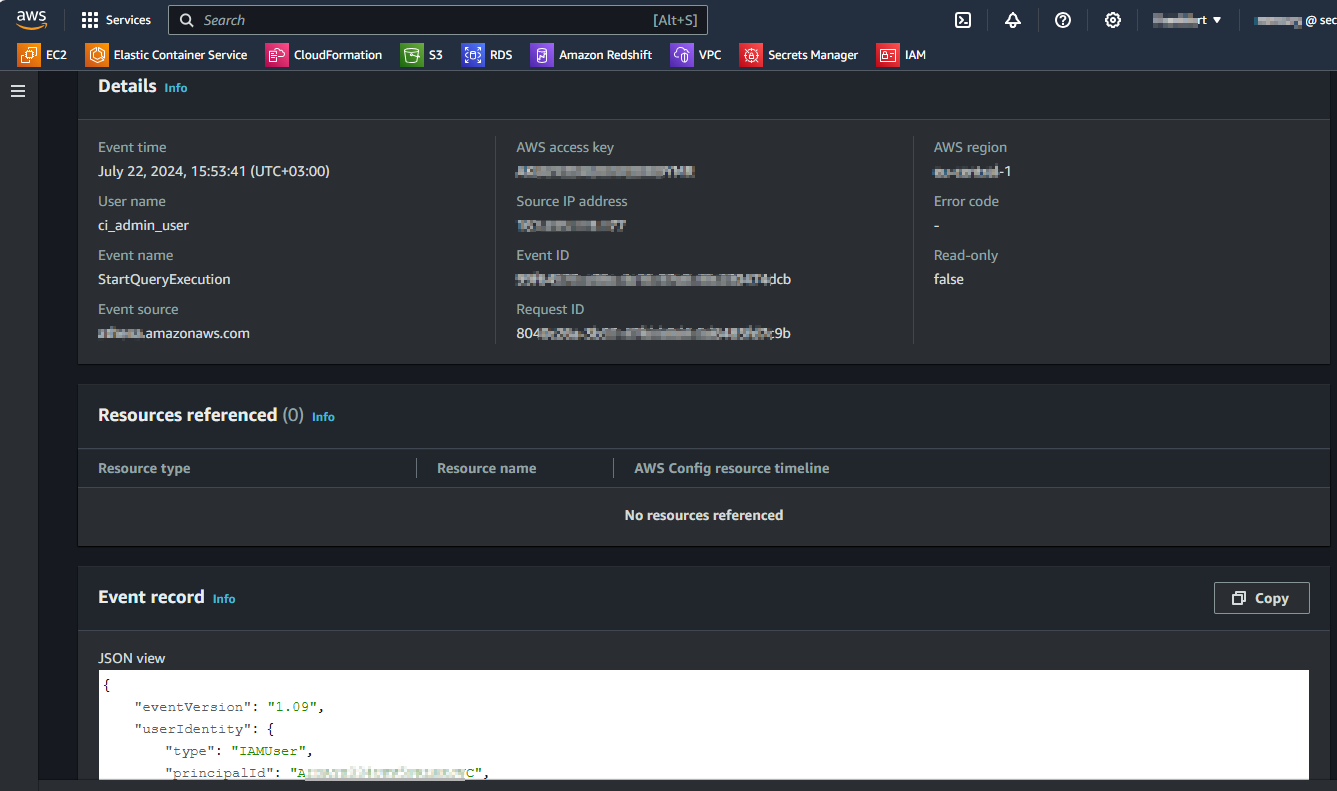
This closely resembles the session trails event details in DataSunrise Audit, with IDs, IP addresses, and supplementary information varying accordingly. However, DataSunrise Proxy offers more comprehensive logging and customizable configuration options:
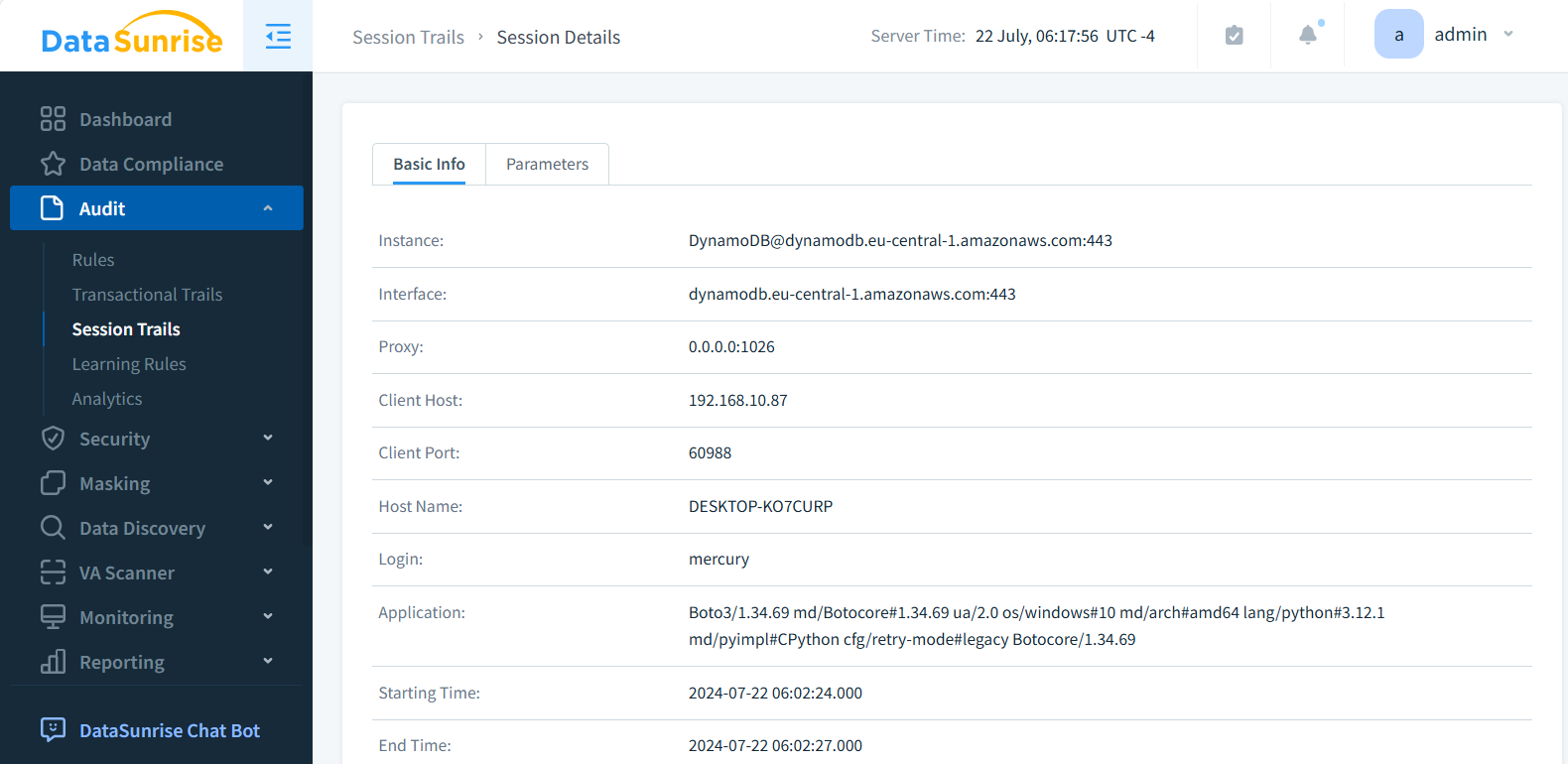
Capturing Query Information
DynamoDB’s built-in tools also enable capturing detailed query information:
- Use DynamoDB Streams (for the table) to capture data modifications
- Implement a Lambda function to process and store the stream data
- Consider using Amazon Athena for analyzing CloudTrail logs
Best Practices for DynamoDB Auditing
Continuous Monitoring
Set up real-time alerts for suspicious activities. This proactive approach helps detect potential security threats quickly.
Regular Review and Analysis
Schedule periodic reviews of audit logs. Look for patterns in user behavior and database activity that might indicate areas for optimization or security concerns.
Compliance Alignment
Ensure your auditing practices align with relevant regulatory requirements such as GDPR, HIPAA, or PCI DSS.
Challenges and Considerations
Performance Impact
Extensive logging can impact database performance. Strike a balance between comprehensive auditing and maintaining optimal database speed.
DataSunrise offers four operation modes, allowing you to choose one with minimal or no impact on performance. Sniffer mode affects performance the least. Ask in this topic for our website chat-bot for further details.
Data Privacy
Be mindful of data privacy regulations when capturing and storing audit logs. Implement data masking techniques to protect sensitive information.
Storage Costs
Audit logs can accumulate quickly. Plan for adequate storage and consider log rotation policies to manage costs effectively.
Conclusion
Implementing a robust data audit strategy for Amazon DynamoDB is essential for maintaining security, ensuring compliance, and optimizing performance. While native AWS tools provide basic functionality, third-party audit solutions offer more comprehensive features for database activity monitoring and user behavior analysis.
By following best practices and choosing the right tools, you can significantly enhance your DynamoDB security posture and gain valuable insights into your database operations.
For a user-friendly and flexible solution to database security, including audit, masking, and data generation features, consider DataSunrise. Our tools offer comprehensive protection for your DynamoDB environments and beyond. Visit our website for an online demo and experience firsthand how DataSunrise can elevate your database security strategy.
