
Data Audit for Amazon Athena

Introduction
As data becomes critical to business, organizations face mounting pressure to secure and maintain data integrity. Amazon Athena, a popular serverless query service for large-scale data processing, requires robust auditing. We’ll explore data audit for Amazon Athena and compare implementation strategies.
In 2023 data breaches cost $4.5M on average. 51% of organizations increase security spending after a breach. Data auditing is crucial in today’s digital world.
What is a Data Audit for Amazon Athena?
Understanding the Basics
Data audit for Amazon Athena is a systematic process of monitoring, recording, and analyzing database activities. It helps organizations track who accessed what data, when, and how. This practice is essential for maintaining database security and ensuring compliance with various regulations.
Set up Amazon Athena connection (Instance) in DataSunrise with a single click to begin comprehensive auditing instantly. Make sure you select the right AWS region for Athena Instance.
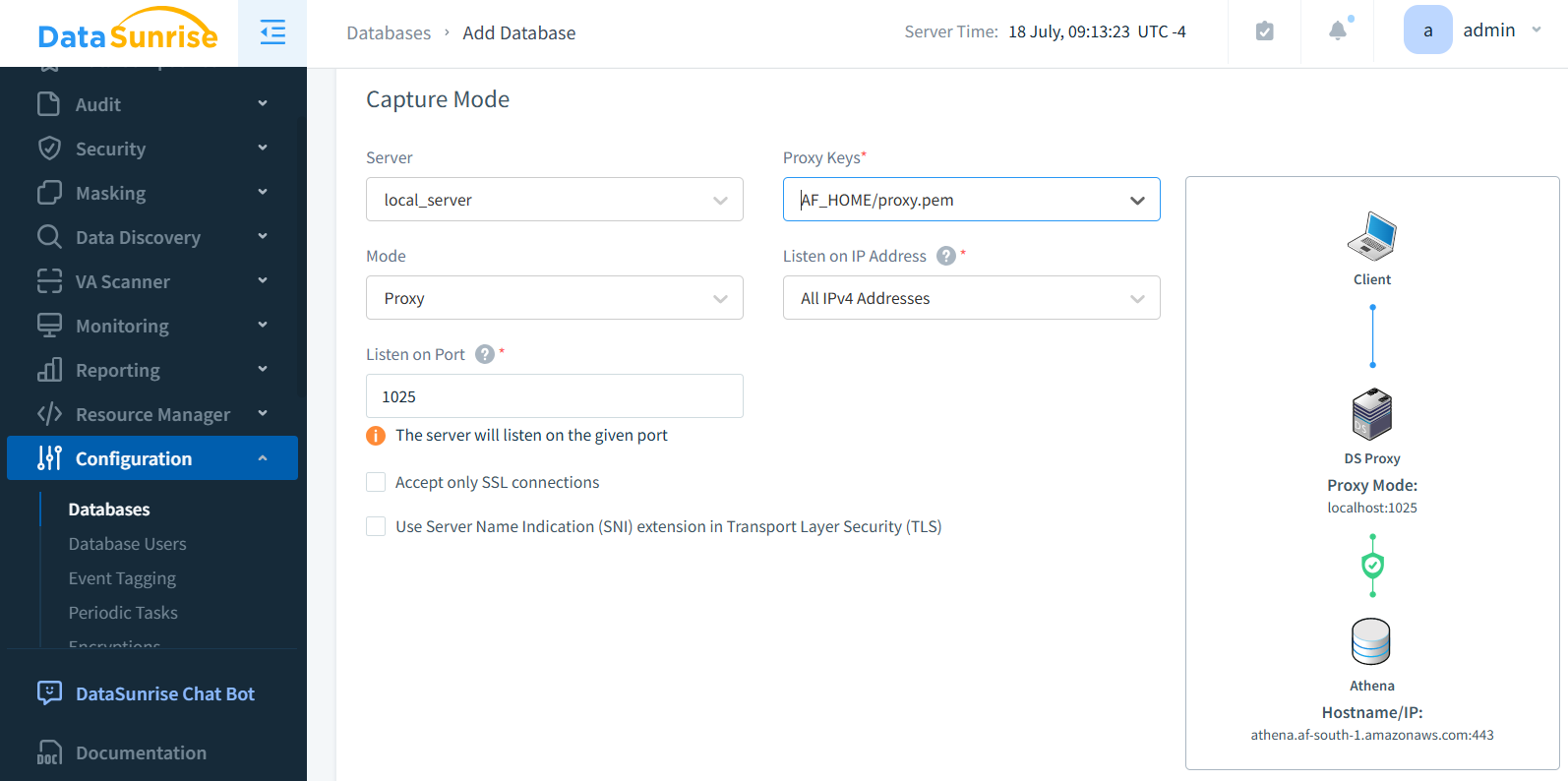
Key Components of Data Auditing
- Access monitoring
- Query logging
- User activity tracking
- Data modification records
By implementing these components, organizations can gain valuable insights into their data usage patterns and potential security risks.
The Importance of Compliance
Regulatory Landscape
Compliance with data protection regulations is non-negotiable in today’s business environment. Various laws and standards, such as GDPR, HIPAA, and PCI DSS, require organizations to maintain strict control over their data access and usage.
Benefits of Compliance
- Avoid hefty fines
- Build trust with customers
- Protect sensitive information
- Maintain a competitive edge
Data auditing helps organizations meet these compliance requirements by providing a clear audit trail of all database activities.
Database Activity Monitoring
Real-time Surveillance
Database activity monitoring (DAM) is a critical aspect of data auditing. It involves real-time surveillance of database actions, allowing organizations to detect and respond to potential threats quickly.
Key Features of DAM
Let’s start with possible implementation with Open-source software:
| DAM Feature | Description | Open-Source Software |
|---|---|---|
| Real-time Monitoring | Continuous surveillance of database activities as they occur | pgAudit, MySQL Enterprise Audit |
| Anomaly Detection | Identifying unusual patterns or behaviors in database access | OSSEC, Wazuh |
| Alert Mechanisms | Automated notifications for suspicious activities or policy violations | Nagios, Zabbix |
| Comprehensive Reporting | Detailed logs and reports of all database activities | ELK Stack (Elasticsearch, Logstash, Kibana) |
| User Behavior Analysis | Tracking and analyzing patterns in user interactions with the database | Apache Spot, OSSIM |
DataSunrise integrates all these features into a single, comprehensive solution, offering broad database compatibility with minimal performance impact.
- Anomaly detection (Advanced visualization tools for pattern recognition)
- Alert mechanisms (Real-time notifications via multiple channels)
- Comprehensive reporting (Actionable insights from aggregated data)
- User behavior analysis (DataSunrise’s ML-driven profiling and risk assessment)
These features work together to create a robust defense against unauthorized access and data breaches. DataSunrise’s comprehensive security suite covers all key components, offering robust tools beyond just activity monitoring. Our integrated AI-powered assistant streamlines data security management through an intuitive interface.
Compare DAM implementation approaches in this concise table:
| Aspect | Develop Own Stack | Open-Source Solutions | Third-Party Solution (e.g., DataSunrise) |
|---|---|---|---|
| Initial Cost | High | Low | Medium to High |
| Time to Implement | Long | Medium | Short |
| Customization | High | Medium | Low to Medium |
| Maintenance | High effort | Medium effort | Low effort |
| Support | Self-supported | Community support | Professional support |
| Scalability | Depends on design | Varies by solution | Usually high |
| Compliance Readiness | Requires effort | May require additional work | Often built-in |
| Feature Set | Custom to needs | Basic to advanced | Comprehensive |
| Best For | Unique requirements | Budget constraints | Quick implementation, robust features |
Implementing Data Audit for Amazon Athena
Best Practices
To effectively implement data auditing for Amazon Athena, consider the following best practices:
- Define clear audit objectives
- Establish a consistent auditing schedule
Streamline first two steps of setup by configuring Audit Rules directly. Begin Data Audit for Amazon Athena by selecting your DataSunrise database instance:
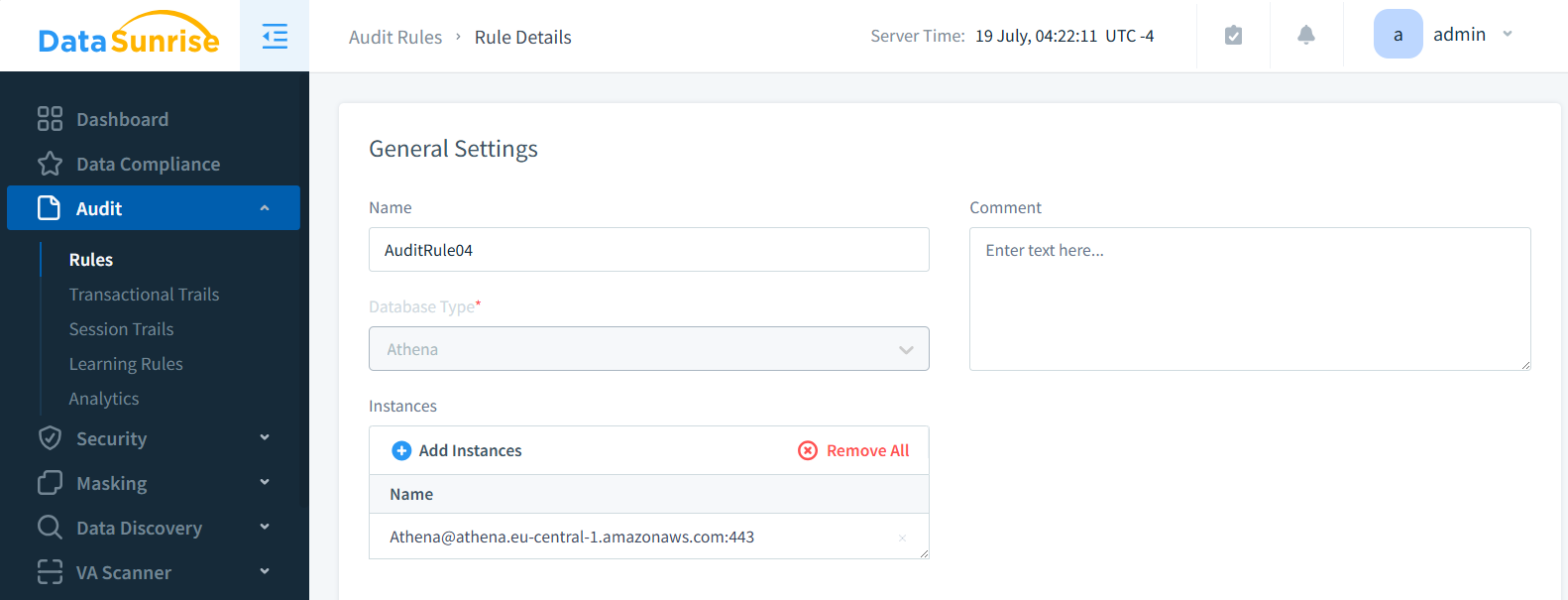
- Use automated tools for efficiency
DataSunrise’s Compliance feature simplifies the creation of complex rule sets with a streamlined setup process.
- Regularly review and analyze audit logs
DataSunrise’s interface provides both overview and detailed event logs through Transactional and Session Trails:
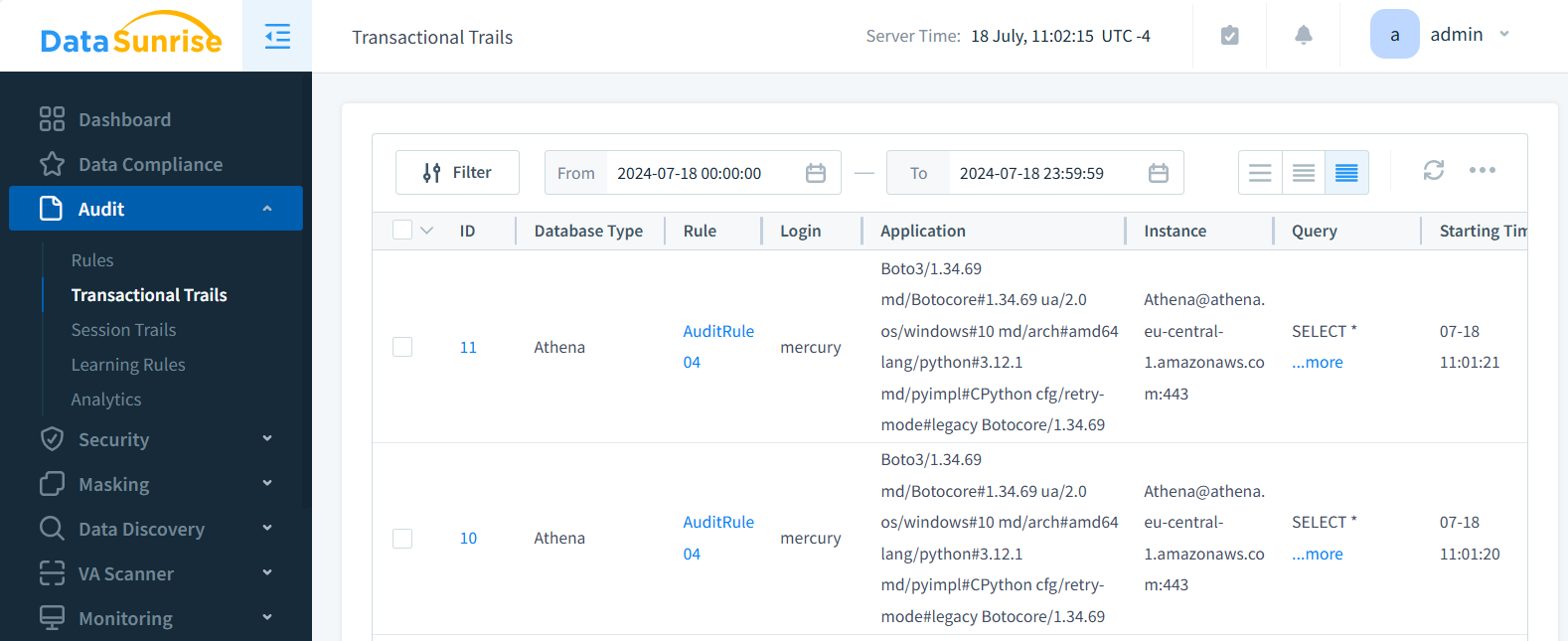
The powerful reporting tool provides instant insights into key session metrics, including application usage and IP address patterns.
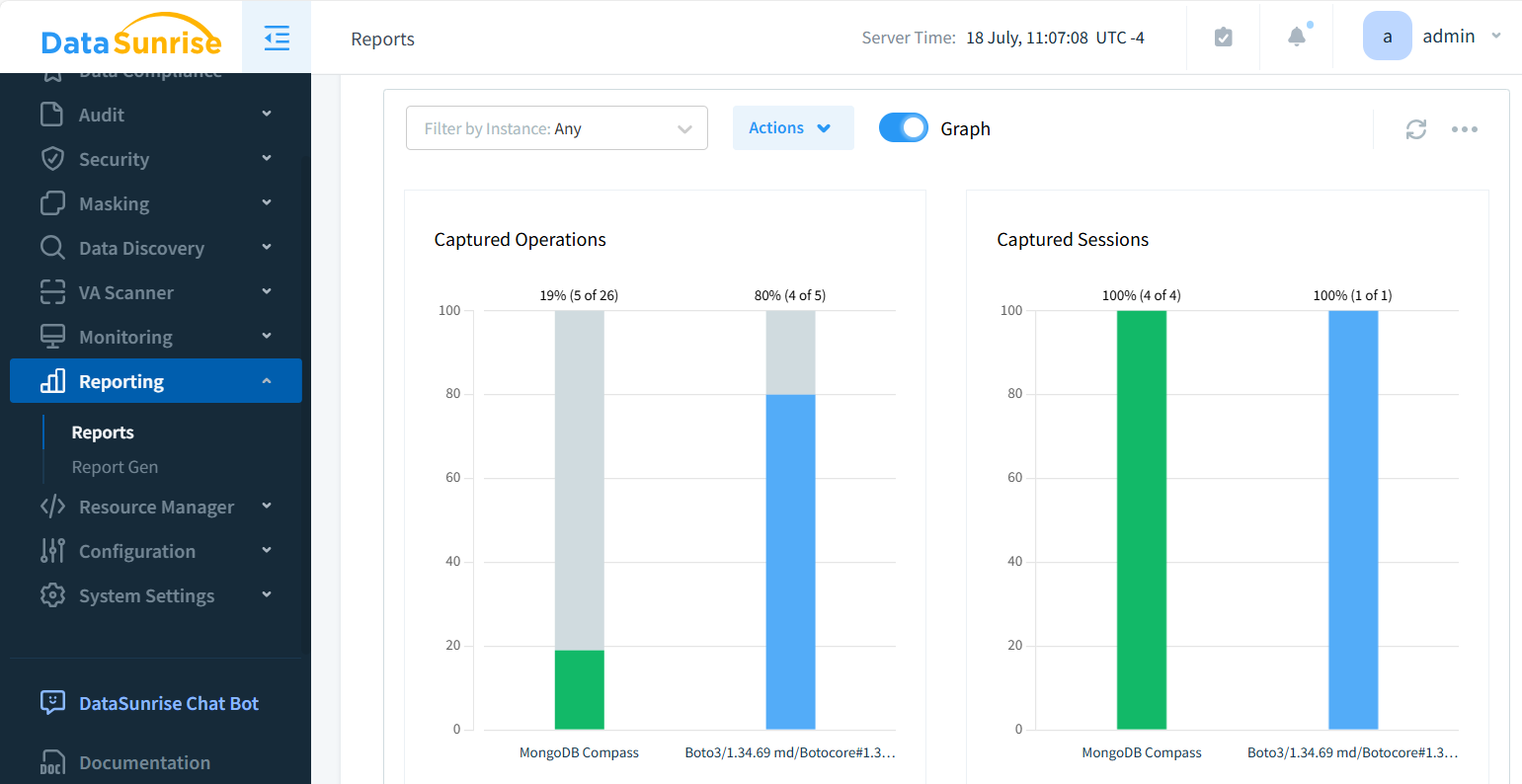
- Train staff on auditing procedures
By following these guidelines, organizations can create a strong foundation for their data auditing efforts.
Challenges and Solutions
Implementing data auditing can present challenges, such as:
- Large volumes of audit data
- Performance impact on database systems
- Complexity of compliance requirements
To address these challenges, organizations can:
- Use data compression techniques
- Implement selective auditing
- Leverage cloud-based auditing solutions
These strategies can help overcome common obstacles in the auditing process.
The Role of Data Audit in Security
Threat Detection
Data auditing serves as a crucial line of defense against security threats. By monitoring database activities, organizations can:
- Identify suspicious behavior
- Detect unauthorized access attempts
- Prevent data exfiltration
This proactive approach to security can significantly reduce the risk of data breaches and cyber attacks.
Incident Response
In the event of a security incident, data audit logs provide valuable information for:
- Investigating the breach
- Assessing the damage
- Implementing corrective measures
This information is crucial for organizations to respond effectively and prevent future incidents.
Conclusion
Data audit for Amazon Athena is a critical component of modern database security and compliance strategies. By using strong auditing practices, companies can keep their important information safe, follow rules, and keep their customers’ trust.
As data continues to grow in volume and importance, the role of data auditing will only become more crucial. Organizations that prioritize this practice will be better equipped to face the challenges of the digital age. They will also be able to safeguard their most valuable asset, which is their data.
DataSunrise offers user-friendly and flexible tools for database security, including comprehensive audit, masking, and data discovery features. Visit our website to see how DataSunrise can improve your data security and compliance. Watch an online demo to learn about advanced database protection.
