
Data Audit for Amazon Redshift

Introduction
Amazon Redshift, a popular cloud data warehouse, handles vast amounts of data daily. But how can organizations guarantee this data remains protected and compliant? The answer lies in data auditing. This article explores the essentials of data audit for Amazon Redshift, covering native capabilities and advanced solutions.
Did you know that data breaches cost companies an average of $4.45 million in 2023? This staggering figure underscores the critical importance of robust data auditing practices. Let’s dive into how Amazon Redshift can help safeguard your valuable data assets.
Understanding Amazon Redshift’s Audit Capabilities
Native Audit Features
Amazon Redshift offers several built-in features for data auditing and query monitoring. These tools help track database activity, user actions, and system performance.
System Tables and Views
Redshift provides system tables and views that store valuable audit information. For example:
- STL_QUERY: Records details of executed queries
- STL_CONNECTION_LOG: Tracks authentication attempts and connections
To query these tables, use standard SQL commands:
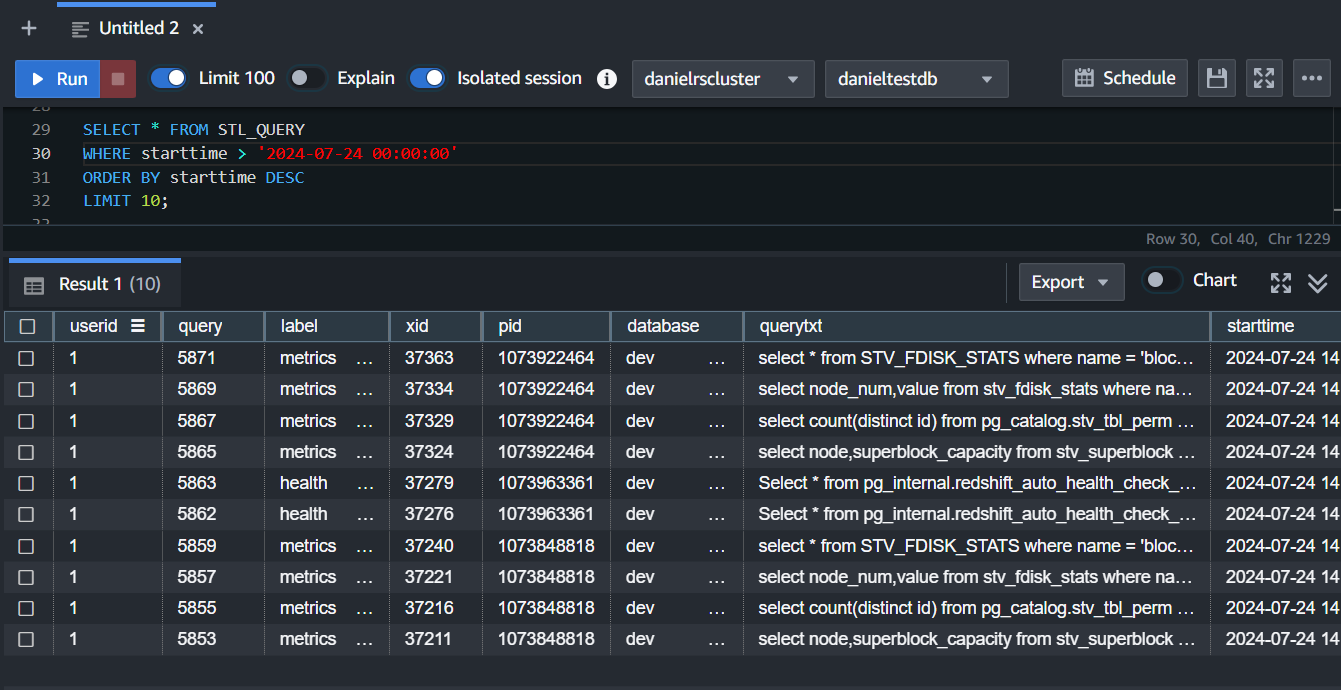
SELECT * FROM STL_QUERY WHERE starttime > '2024-07-24 00:00:00' ORDER BY starttime DESC LIMIT 10;
This query retrieves the ten most recent queries executed after July 24, 2024.
Query Monitoring Rules
Redshift’s Workload Management (WLM) feature includes Query Monitoring Rules (QMR). These rules help identify and manage long-running or resource-intensive queries.
To create a QMR:
CREATE QUERY MONITORING RULE rule_name WITH (query_execution_time = 300000, query_cpu_time = 60000) THEN ABORT, LOG;
This rule aborts queries running longer than 5 minutes or consuming more than 1 minute of CPU time.
Advanced Data Auditing with DataSunrise
While Redshift’s native capabilities provide a solid foundation, organizations often require more comprehensive auditing solutions. This is where third-party tools like DataSunrise come into play.
Creating a DataSunrise Instance
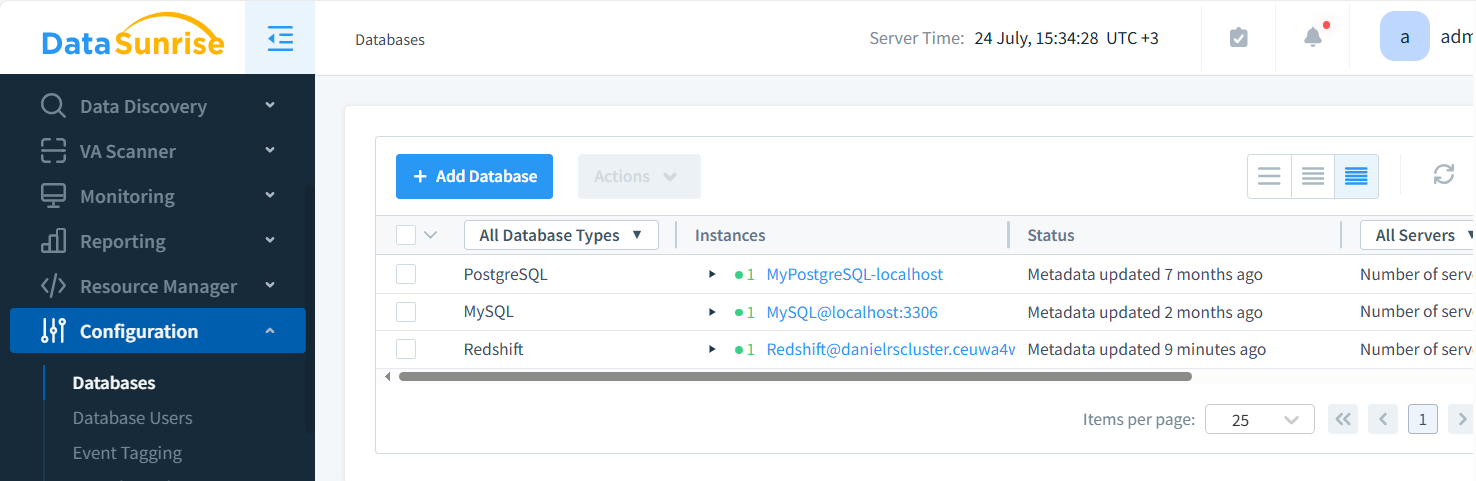
To set up a DataSunrise instance for Redshift auditing follow two simple steps:
- Configure the connection to your Redshift cluster (create Instance)
- Set up audit rules and policies
The figure illustrates three distinct instances. These databases (PostgreSQL and MySQL) and the Redshift data warehouse are now safeguarded by a leading data security solution in the industry.
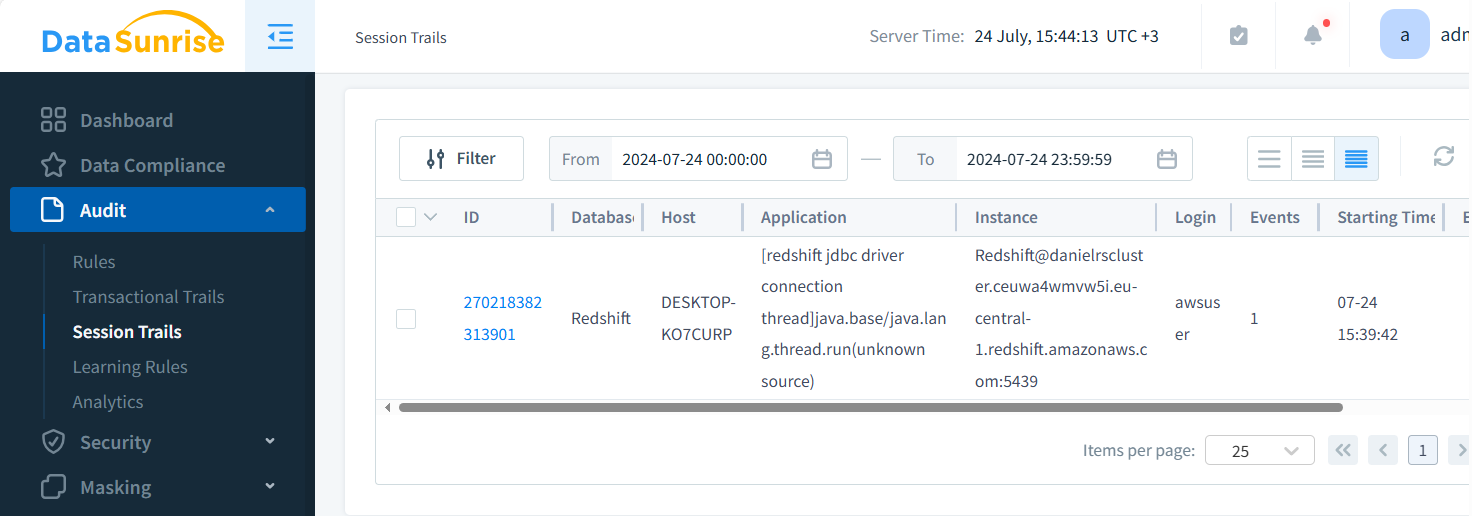
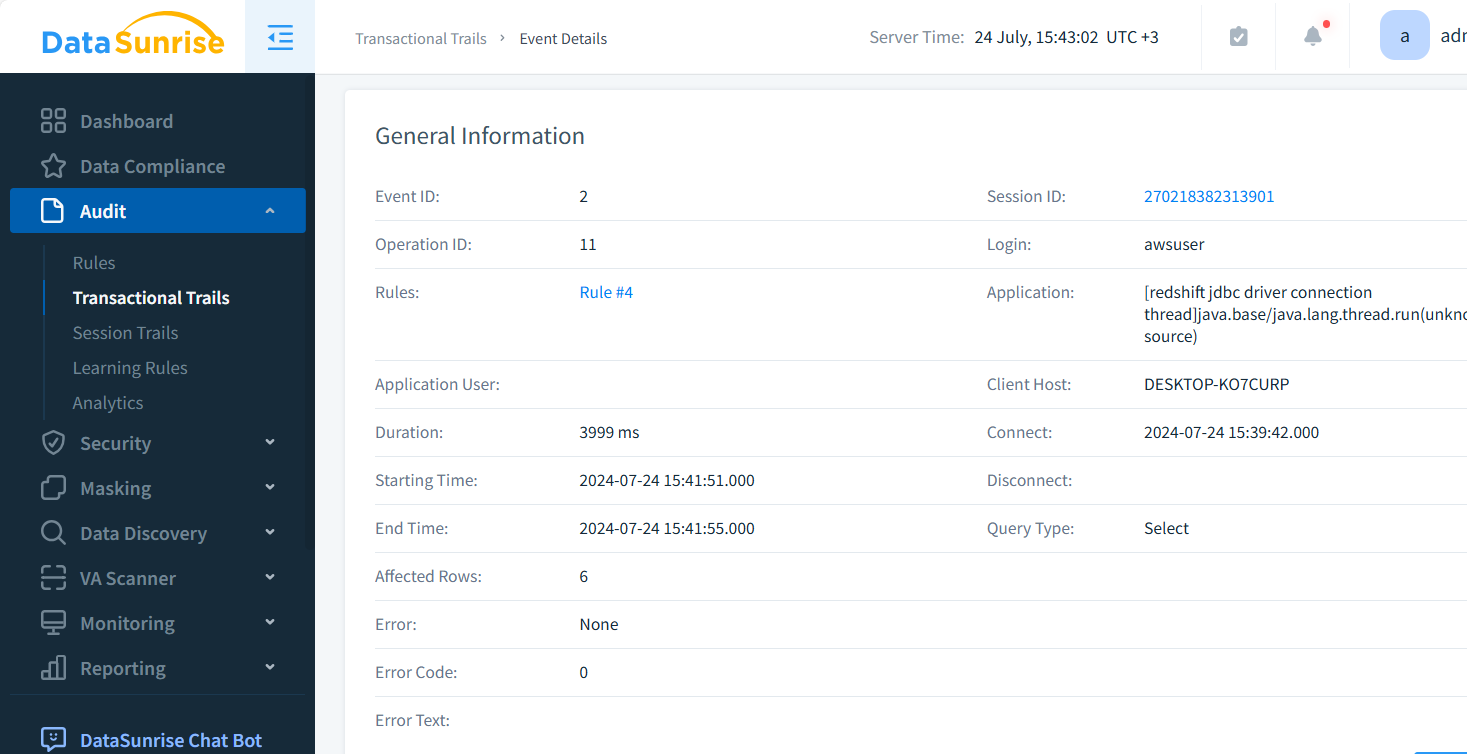
For each instance, you can set up Audit Rules and access valuable information in Transactional and Session Trails. The picture below shows details. DataSunrise may log queries, bind variables, logins, affected rows, and numerous other logged data points. You can also generate CSV or JSON reports for use in your own ML pipelines.
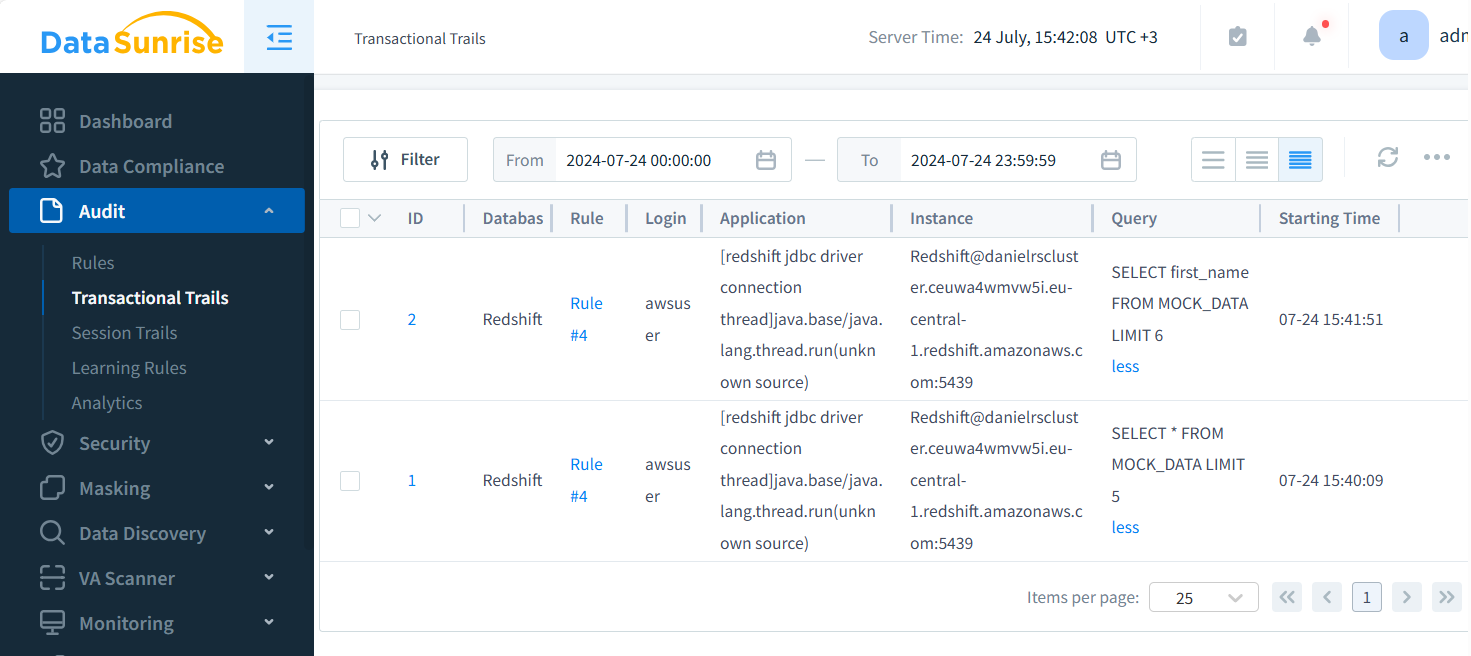
Detailed Event Descriptions
DataSunrise offers granular event logging for Redshift, including:
- Query execution details
- Data access patterns
- User authentication events
- Schema changes
These detailed logs provide a comprehensive view of database activity, enhancing security and compliance efforts.
Benefits of Comprehensive Data Auditing
Enhancing Security
Thorough data auditing helps detect and prevent unauthorized access attempts. By monitoring user activities and query patterns, organizations can identify potential security threats early.
Ensuring Compliance
Many industries face strict regulatory requirements. Comprehensive auditing helps meet these standards by providing detailed records of data access and modifications.
Optimizing Performance
Audit logs offer insights into query performance and resource usage. This information helps database administrators optimize Redshift configurations and improve overall system efficiency.
Best Practices for Data Auditing in Redshift
Regular Review of Audit Logs
Set up a routine for reviewing audit logs. This practice helps identify unusual patterns or potential security issues promptly.
Implement Least Privilege Access
Grant users only the permissions they need. This principle minimizes the risk of unauthorized data access or modifications.
Use Data Masking for Sensitive Information
Implement data masking techniques to protect sensitive data during auditing processes. This ensures that audit logs don’t become a security risk themselves.
Automate Alerting
Set up automated alerts for specific events or thresholds. This proactive approach helps quickly respond to potential security incidents or compliance violations.
DataSunrise supports numerous methods to inform you on the data events like Slack, CloudTrails or email:
Challenges in Data Auditing
Balancing Performance and Thoroughness
Extensive auditing can impact system performance. Strike a balance between comprehensive logging and maintaining optimal database performance.
Managing Large Volumes of Audit Data
As audit logs grow, managing and analyzing this data becomes challenging. Consider implementing log rotation and archiving strategies.
Keeping Up with Evolving Compliance Requirements
Regulatory landscapes change frequently. Regularly review and update your auditing practices to ensure ongoing compliance.
Conclusion
Data audit for Amazon Redshift is crucial for maintaining data security, ensuring compliance, and optimizing performance. While Redshift offers robust native auditing capabilities, tools like DataSunrise provide flexible enhanced features for comprehensive database activity monitoring.
By using the best methods and advanced tools, companies can keep their important data safe, follow rules, and learn more about their Redshift systems.
Remember, effective data auditing is not a one-time task but an ongoing process. Stay alert, update your auditing strategies, and use the right tools to protect your important data.
DataSunrise offers user-friendly and flexible tools for database security, including audit, masking, and data discovery among other features. Visit our website at DataSunrise.com for an online demo and to explore how our solutions can enhance your Redshift data auditing capabilities.
