
Data Audit for Azure SQL

Data Audit for Azure SQL has become increasingly critical as organizations store sensitive information in cloud databases. Microsoft recommends database auditing as one of the fundamental security practices for Azure SQL, alongside features like Advanced Threat Protection and data encryption.
In today’s data-driven world, tracking who accesses your data, what changes they make, and when these interactions occur has become essential. Organizations need robust Data Audit for Azure SQL solutions that not only meet compliance requirements but also provide real-time insights into database activities.
This comprehensive guide will walk you through implementing effective data audit strategies in Azure SQL, covering both built-in features and advanced solutions that enhance your database security.
Understanding Data Audit for Azure SQL Database
Azure SQL Database auditing serves as your first line of defense in database security monitoring. This built-in feature tracks and logs all database activities, including user operations, security changes, and data modifications. The system automatically generates detailed records that help organizations maintain compliance with regulatory requirements like GDPR, HIPAA, and SOX.
Audit logs include crucial information such as user identity, timestamp, affected resources, and operation details. When properly configured, these logs provide invaluable insights for security analysis, forensics, and compliance reporting. Organizations can set custom retention policies and choose between multiple storage options to balance cost and accessibility.
Native Data Audit for Azure SQL
Azure SQL provides a set of native auditing features that allow database administrators to monitor and manage changes to data without relying on third-party tools. These features include:
1. SQL Language Features
SQL Server provides a number of features that enable native auditing capabilities, such as triggers, T-SQL queries, and system views. You can use SQL language to write queries that log changes to your data or track access to sensitive information.
One way to audit data at the row level is by using triggers. A trigger automatically fires in response to a particular event, such as an INSERT, UPDATE, or DELETE operation. For example, the following SQL trigger tracks any changes to the “email” column in a user table:
CREATE TRIGGER TrackEmailChanges ON Users AFTER UPDATE AS BEGIN IF UPDATE(email) BEGIN INSERT INTO AuditLog (UserID, OldEmail, NewEmail, ChangeDate) SELECT i.UserID, d.email, i.email, GETDATE() FROM inserted i JOIN deleted d ON i.UserID = d.UserID; END END;
This trigger ensures that every time an email address is updated in the “Users” table, a record is inserted into the “AuditLog” table with the old and new email values, along with the timestamp of the change.
2. Using Views for Auditing Data
You can also use views to audit sensitive data. A view is a virtual table that provides a specific subset of data from one or more tables, and you can configure it to display only the data relevant to your audit requirements.
For instance, you could create a view that aggregates changes made to user data over time, providing a historical log of data access. Here’s an example SQL query that generates a view to display changes to email addresses over the past 30 days:
CREATE VIEW RecentEmailChanges AS SELECT UserID, OldEmail, NewEmail, ChangeDate FROM AuditLog WHERE ChangeDate > DATEADD(DAY, -30, GETDATE());
This view can then be queried to retrieve a list of all recent email changes:
SELECT * FROM RecentEmailChanges;
3. Stored Procedures for Auditing
Stored procedures are another powerful tool for auditing in Azure SQL. A stored procedure is a precompiled collection of SQL statements that can be executed as a single unit. You can use stored procedures to audit complex business logic or to log database access at the transaction level.
For example, you might write a stored procedure to record every time a user accesses a sensitive table, such as the “CustomerData” table, which contains personal details. Here’s a simple stored procedure that logs such access:
CREATE PROCEDURE LogSensitiveDataAccess AS BEGIN INSERT INTO DataAccessLog (AccessTime, UserID, TableAccessed) SELECT GETDATE(), SYSTEM_USER, 'CustomerData'; END;
This stored procedure can then be executed whenever a sensitive table is queried, providing a log of who accessed the data and when.
4. Using Azure CLI for Data Auditing in Azure SQL
The Azure CLI (Command-Line Interface) is a powerful tool for managing Azure resources and can also be used for auditing purposes. Azure SQL allows you to configure auditing settings using the Azure CLI, where you can specify what kind of events to capture, how long to retain the audit logs, and where to store them (such as in an Azure storage account).
You can use the Azure CLI to enable auditing for an Azure SQL database as follows:
az sql db audit-policy update \ --resource-group MyResourceGroup \ --server MyServer \ --name MyDatabase \ --state Enabled \ --storage-account MyStorageAccount
This command will enable auditing for the specified database and store the logs in the MyStorageAccount storage account.
Enhanced Auditing with DataSunrise
While Azure SQL provides powerful native audit capabilities, third-party solutions like DataSunrise offer additional flexibility and advanced features. The platform provides real-time monitoring capabilities, allowing organizations to detect and respond to security threats as they occur. It offers sophisticated filtering options and custom rule creation that can adapt to specific security requirements.
The centralized management console simplifies audit administration across multiple databases and platforms. Advanced reporting features help organizations meet complex compliance requirements and generate detailed activity reports for stakeholders.
DataSunrise enhances your security posture through:
- Centralized Control: Manage all your audit rules in one place for consistent security practices across your databases.
- Advanced Security: DataSunrise’s dynamic data masking and auditing features provide an additional layer of protection for sensitive data.
- Compliance: Ensure that your Azure SQL databases comply with industry regulations and internal security policies.
To view audit data in DataSunrise (assuming it’s installed):
- Connect a Database to your DataSunrise instance
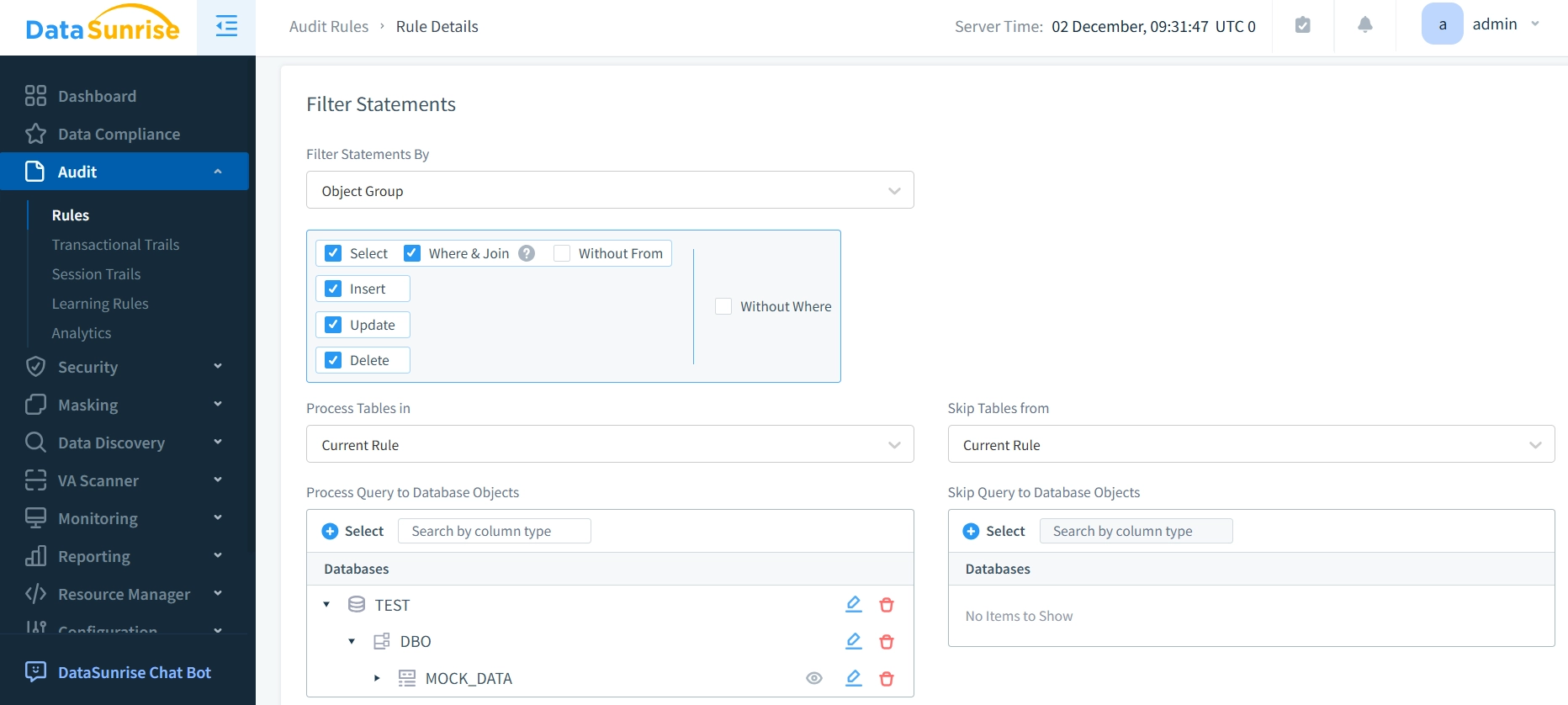
- Navigate to the Audit section and set up a new audit rule
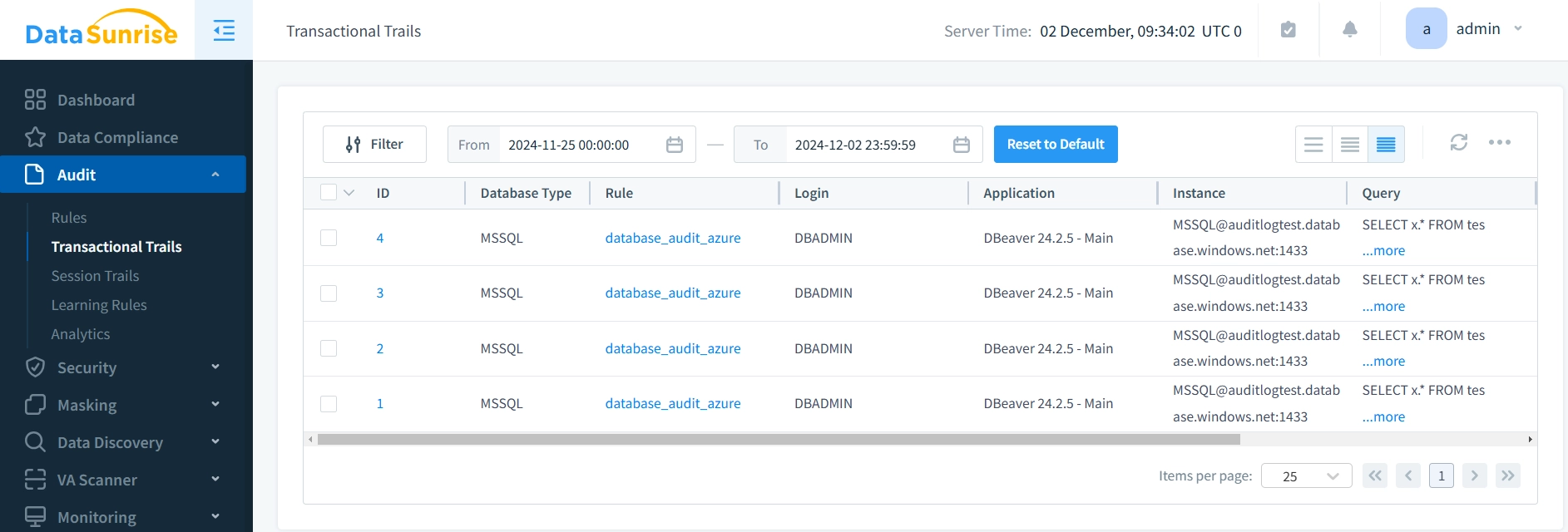
- Click on “Transaction Trails” to check the Audit Trails
Best Practices for Data Auditing
Successful data auditing requires a well-planned strategy that balances security needs with operational efficiency. Organizations should establish clear audit objectives aligned with their security and compliance requirements. Regular review cycles ensure that audit policies remain effective and relevant.
Performance impact should be carefully considered when implementing audit policies. While comprehensive auditing provides better security visibility, it can affect database performance and generate significant storage costs. Organizations should optimize their audit configurations to focus on critical activities while maintaining acceptable performance levels.
To maximize the effectiveness of your audit strategy:
- Establish regular audit log review schedules. Dedicate time to analyze audit trails for suspicious patterns or unauthorized access attempts. This proactive approach helps identify potential security issues early.
- Implement detailed retention policies that align with your compliance requirements. Consider factors like storage costs, regulatory mandates, and investigation needs when setting retention periods for audit data.
- Use parameterized queries exclusively in your applications. This practice prevents SQL injection attacks and ensures accurate audit trails by maintaining clear records of actual query intentions.
- Maintain thorough documentation of your audit configurations. Keep detailed records of what’s being audited, why certain choices were made, and how the audit system is configured to help with troubleshooting and knowledge transfer.
- Consider using third-party solutions like DataSunrise to enhance your audit capabilities. These tools often provide centralized management, advanced reporting features, and automated compliance monitoring that extend beyond native Azure SQL functionality.
- Create clear procedures for audit log review and incident response. Define who is responsible for reviewing logs, how often reviews should occur, and what actions to take when suspicious activities are detected.
- Keep your audit configurations under version control. Track changes to audit settings and rules to maintain an accurate history of your security posture and ensure proper governance.
- Focusing on these practices helps create a robust audit framework that supports both security and compliance objectives while remaining manageable and effective.
Conclusion
Effective data auditing is crucial for maintaining the security and integrity of your databases. Azure SQL offers powerful native tools for auditing data, such as triggers, views, stored procedures, and the Azure CLI. These features enable you to monitor changes to sensitive data and ensure compliance with regulatory requirements.
For more advanced auditing needs, DataSunrise provides dynamic data auditing tools that can complement Azure SQL’s native capabilities, offering enhanced security and centralized control. To learn more about DataSunrise’s audit and compliance features, visit our website and schedule an online demo.
By implementing a robust data audit strategy in your Azure SQL databases, you can ensure the security of your sensitive data, detect unauthorized access, and meet compliance standards.
