
Data Audit for Hydra

Introduction
Database security has become a critical concern for organizations managing complex data ecosystems. Hydra, a powerful PostgreSQL-based database with integrated analytics capabilities, offers robust mechanisms for tracking and monitoring database activities through comprehensive audit trails.
The increasing sophistication of cyber threats underscores the importance of meticulous data tracking. According to recent cybersecurity reports, organizations face mounting challenges in protecting sensitive information and maintaining compliance across their database infrastructure.
Data Audit for Hydra with Native Capabilities
Hydra builds upon PostgreSQL's standard monitoring framework, providing basic audit trail functionality through familiar PostgreSQL logging mechanisms. The database leverages existing PostgreSQL tools to capture and track database operations.
Logging Fundamentals
At its core, Hydra relies on PostgreSQL's straightforward logging capabilities. While not revolutionary, these mechanisms offer fundamental tracking of database activities through well-established logging configurations.
Configuring Data Audit for Hydra with Native Logging
Administrators can implement basic audit logging using standard PostgreSQL settings:
-- Enable detailed statement logging
ALTER SYSTEM SET logging_collector = on;
ALTER SYSTEM SET log_statement = 'all';
ALTER SYSTEM SET log_duration = on;
-- Configure log file parameters
ALTER SYSTEM SET log_directory = '/var/log/hydra/audit';
ALTER SYSTEM SET log_filename = 'postgresql-%Y-%m-%d_audit.log';
-- Implement basic logging rules
ALTER SYSTEM SET log_min_duration_statement = '1000ms';
ALTER SYSTEM SET log_connections = on;
ALTER SYSTEM SET log_disconnections = on;
Tracking Database Operations
The audit trail captures standard database events through typical PostgreSQL activity tracking:
-- Basic database activity query
SELECT
datname,
usename,
client_addr,
backend_start,
query,
query_start,
state
FROM pg_stat_activity
WHERE state != 'idle'
ORDER BY backend_start DESC
LIMIT 50;
This query retrieves the 50 most frequently executed queries from pg_stat_statements, ordered by call count. It shows key performance metrics, including execution time, rows returned, and buffer/cache hits. The total_exec_time and avg_exec_time help identify queries that are resource-intensive, aiding in performance optimization.
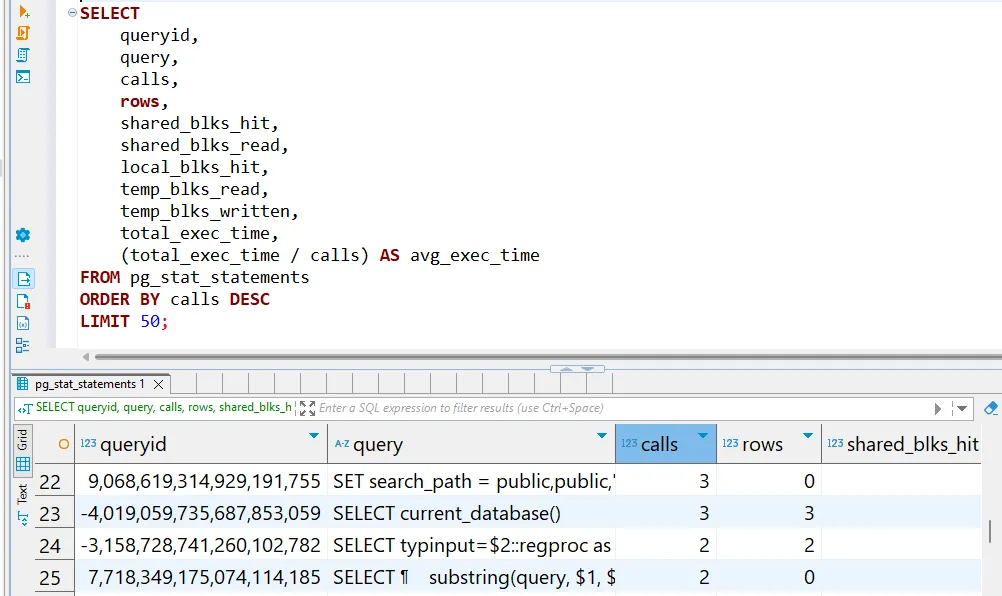
For effective audit trail management, consider these practical approaches: regularly review logs, implement access controls, and balance logging depth with system performance. While not complex, these steps provide a foundational approach to database monitoring.
Advanced Data Audit for Hydra with DataSunrise
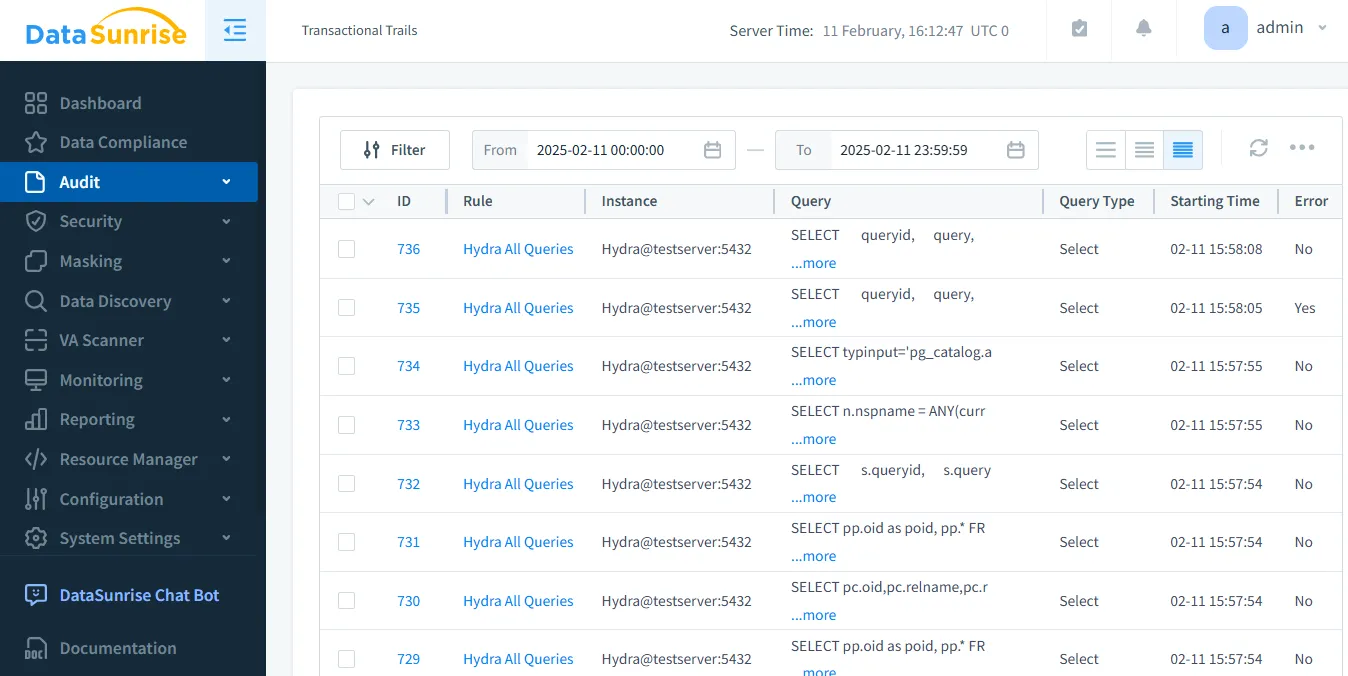
While Hydra offers some basic native auditing capabilities, DataSunrise excels in audit trail capabilities, transforming database monitoring from a passive recording process to an active, intelligent security mechanism.
Unparalleled Monitoring Capabilities
DataSunrise doesn't just track database activities; it provides a comprehensive security ecosystem that goes far beyond traditional audit trail solutions. The platform's intelligent monitoring system offers:
Intelligent Audit Trail Management
- Real-time, detailed transaction logging
- Comprehensive event tracking across multiple database platforms
- Forensic-grade audit trails with granular visibility Learn More About Database Auditing
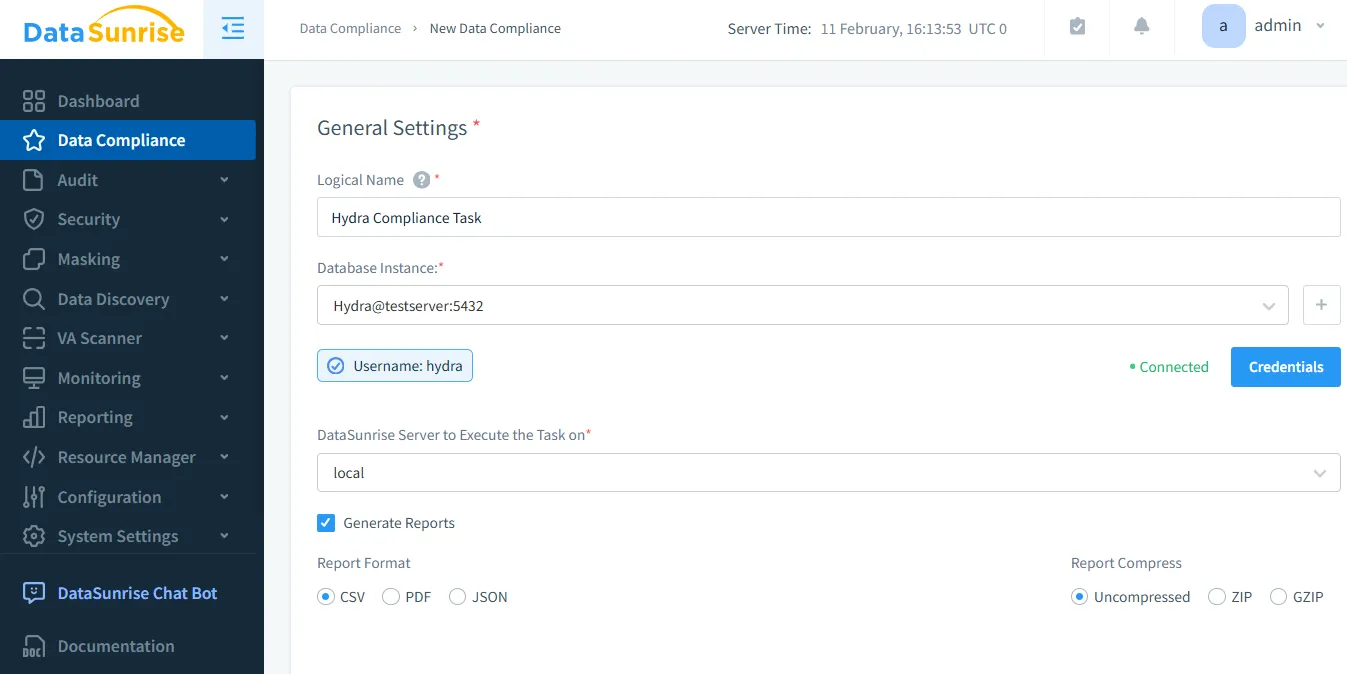
Advanced Compliance and Reporting
- Automated compliance reporting for GDPR, HIPAA, PCI DSS, SOX
- Customizable compliance dashboards
- Seamless evidence collection for regulatory requirements Explore Compliance Solutions
Dynamic Data Masking and Protection
- Intelligent sensitive data discovery
- Context-aware data masking techniques
- Real-time data obfuscation to prevent unauthorized exposure Discover Data Masking Capabilities
Advanced Feature Set
| Feature | Description | Unique Benefit |
|---|---|---|
| Real-time Monitoring | Continuous, instantaneous tracking | Immediate threat identification |
| Behavioral Analytics | AI-powered user activity analysis | Predictive security insights |
| Compliance Automation | Automated reporting and tracking | Simplified regulatory adherence |
| Sensitive Data Discovery | Automatic confidential data identification | Enhanced data protection |
| Custom Security Rules | Flexible, granular access controls | Tailored security strategy |
Transformative Security Approach
What sets DataSunrise apart is its holistic approach to database security. Rather than treating audit trails as a mere compliance checkbox, the platform transforms them into a strategic security asset. Its advanced analytics provide not just a record of past activities, but actionable insights that can prevent potential security breaches before they occur.
Conclusion
Hydra's native audit capabilities provide a solid foundation, but DataSunrise elevates database monitoring to an art form. By integrating this advanced solution, organizations can transform their approach to database security, moving from reactive logging to proactive, intelligent protection.
Ready to revolutionize your database security strategy? Schedule a demonstration to see how it can transform your Hydra database monitoring approach.
