
Data Audit for Impala

Introduction
Before delving into the specifics of data auditing in Impala, it's essential to first consider the broader context of data auditing and compliance in general. Data audit at its core is the process of systematic monitoring and recording of database activities that affect data integrity, confidentiality, and availability. It involves setting up and maintaining detailed records of user actions and system events, including query execution, schema changes, and data access patterns. This includes capturing both successful and failed authentication attempts, DDL operations, and specific data access events based on configured audit rules and compliance requirements.
In today's data landscape, where organizations operate large-scale distributed systems, auditing plays a crucial role in database security and governance. According to Thales 2024 Data Threat Report, about 70% of enterprises are unable to classify more than 50% of their sensitive data, highlighting the critical need for robust auditing and data governance. Furthermore, organizations that passed compliance audits had a breach history in only 21% of cases, with just 3% reporting a breach in the previous 12 months, demonstrating the effectiveness of proper audit and compliance measures.
Auditing in Apache Impala
Impala, as a distributed SQL query engine for Apache Hadoop, presents unique challenges and opportunities for audit logging and compliance monitoring. Operating across distributed clusters and handling large-scale data processing, Impala requires robust audit mechanisms to track query execution, resource utilization, and data access patterns across its distributed architecture. Understanding how to effectively implement and manage audit logging in Impala is crucial for organizations that need to maintain compliance while leveraging the power of distributed SQL processing.
Understanding Impala's built-in logging capabilities provides a foundation for addressing basic audit requirements. In this context, we'll explore how these logs can be accessed and what types of information they may provide for auditing purposes.
Accessing Basic Data Audit for Impala with impalad logs
Before delving into advanced auditing capabilities, it's helpful to understand how Impala provides basic logging functionality by default. Impala's logs, accessible both through its web interface and via the file system, offer a foundational way to monitor activities such as SQL query execution and system events.
Accessing Logs via Web UI
Once Impala is up and running, you can navigate to impalad web interface and access logs under the /logs section:
https://<ip_address>:25000/logs
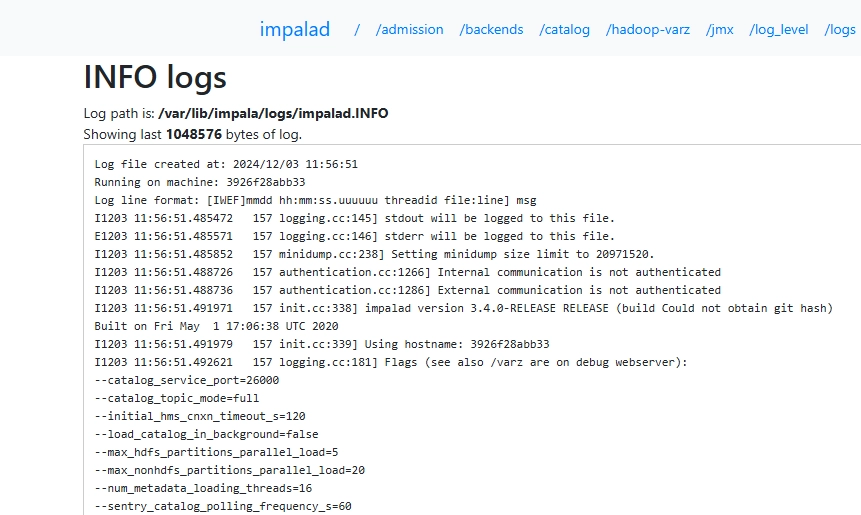
This interface provides a centralized view of system logs, including SQL queries, connection details, and internal events.
Accessing Logs via Command-Line
Logs are also accessible at the location specified in the log_path configuration. You can view the impalad.INFO by navigating to the log file directly using Linux system utilities like cat or grep:
cat /var/lib/impala/logs/impalad.INFO
This file contains mixed logs, including system messages, service statuses, and SQL queries executed on the database.
Example: Logging SQL Queries
You can observe logging behavior in action by executing some basic SQL queries. Start by entering the Impala shell and executing some simple queries:
CREATE DATABASE test;
CREATE TABLE test.sample (id INT);
INSERT INTO test.sample VALUES (1), (2), (3);
SELECT * FROM test.sample;
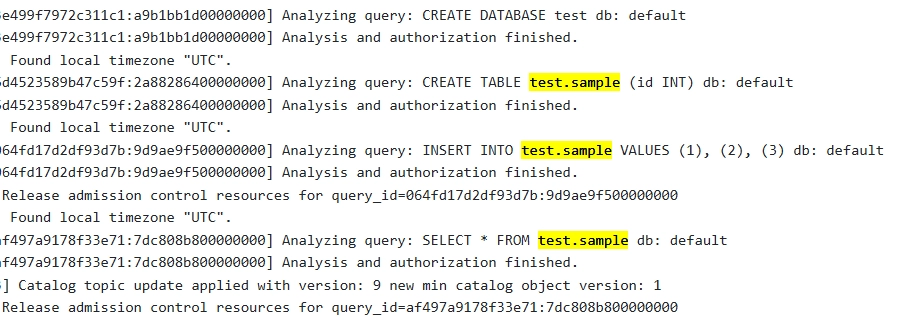
Verifying Logs in the Web Interface
Opening the web interface, you can use the search feature (e.g., Ctrl+F) to find logged queries such as queries performed on test.sample table
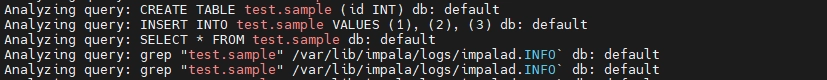
Verifying Logs via Command-Line
Similarly, you can filter queries directly from the log file with system utilities like grep. Below is an example filtering ‘test.sample’ table queries:
grep "test.sample" /var/lib/impala/logs/impalad.INFO
Understanding Log Details
By default, Impala logs everything at the ALL logging level. This includes:
- System events and status messages
- Connection and session details
- SQL query executions
Logging Levels
Impala supports various logging levels (e.g., INFO, WARN, ERROR, ALL), which can be configured to control the verbosity of logs. At the ALL level, the logs are comprehensive and include SQL queries, but still the information they provide is pretty basic. You can read more about system logging and log levels by reading official documentation on this topic.
Relevance to Auditing
The default logs are useful for:
- Tracing query execution for debugging or troubleshooting.
- Monitoring connections and session activities.
- Observing general system behavior.
Separate Audit Logs in Impala
It's also worth mentioning, that Impala provides functionality to generate separate audit logs specifically designed for detailed tracking and compliance purposes. These audit logs can be enabled by starting impalad with specific flags. For more detailed information, you can refer to Impala's official documentation.
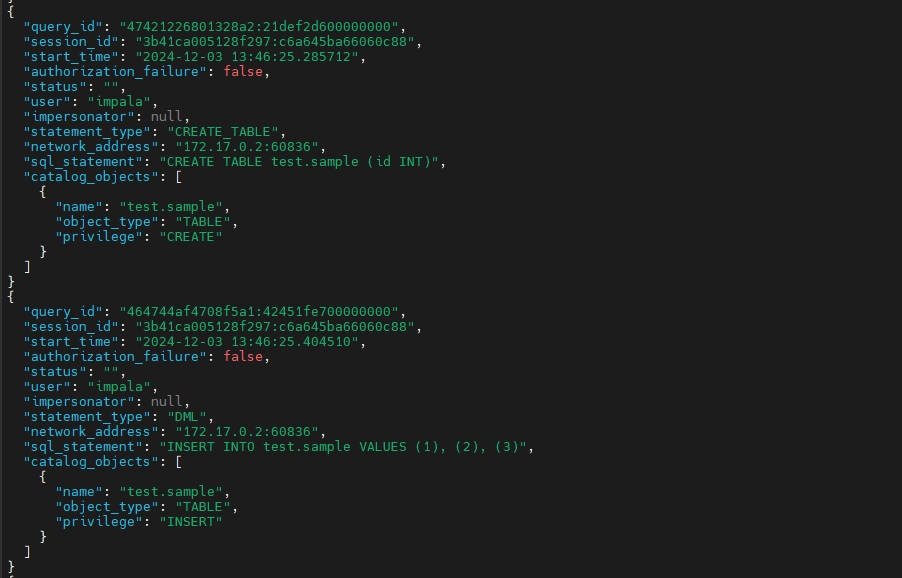
Information Captured in Audit Logs
These audit logs provide a more detailed trails of user activities, compared to system logs. Also, unlike system logs, audit logs are stored in JSON format, making them queryable using tools like jq for better output readability.
jq '.[] | select(.sql_statement | test("test.sample"))' /var/lib/impala/audit/impala_audit_event_log_1.0*
Limitations of Data Audit for Impala with Default Logs:
While Impala's default system and audit logs may provide useful insights, they both come with certain limitations, making them less viable and scalable as long-term solutions for comprehensive auditing and monitoring. These include:
No Native Query or Filtering Support: Default logs cannot be queried or filtered using SQL or built-in filter mechanisms. This limitation necessitates reliance on external tools like
jqor system utilities for viewing and analysis, which can complicate workflows and hinder seamless integration with other systems.Limited Granularity: The default logging system captures all events broadly, without the ability to define specific audit rules. This makes tracking user-specific activities or monitoring sensitive data changes less efficient.
Storage and Performance Overhead: Continuous logging at a detailed level, especially in high-traffic environments, can lead to significant storage use and performance degradation, requiring careful resource management and periodic log rotation.
DataSunrise: Enhanced Data Audit for Impala
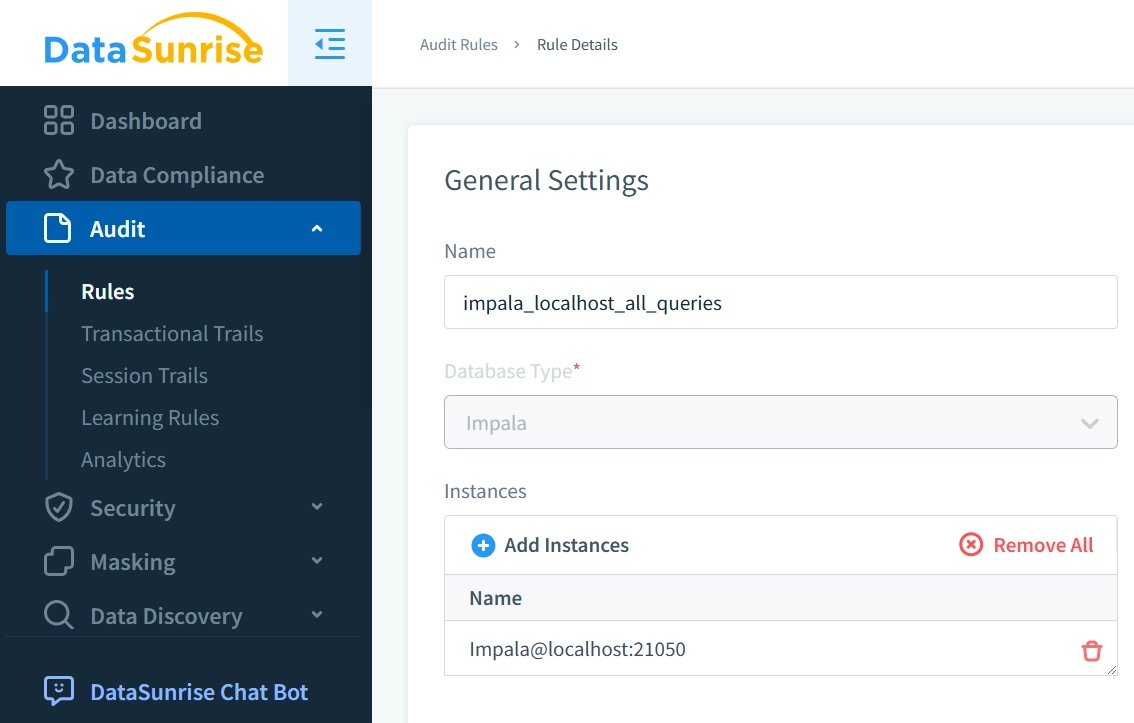
While Impala's native logging serves basic needs regarding data audit for impala, its constraints highlight the need for specialized audit solutions, especially in large enterprise environments. DataSunrise addresses these limitations by providing comprehensive monitoring and analysis capabilities, offering enhanced queryability, granular control, and optimized resource management.
DataSunrise Advantages for Impala Auditing
- Easy Implementation: Quick deployment options and intuitive interface mean faster time-to-value compared to configuring native logs. Teams can start monitoring database activities with minimal setup time.
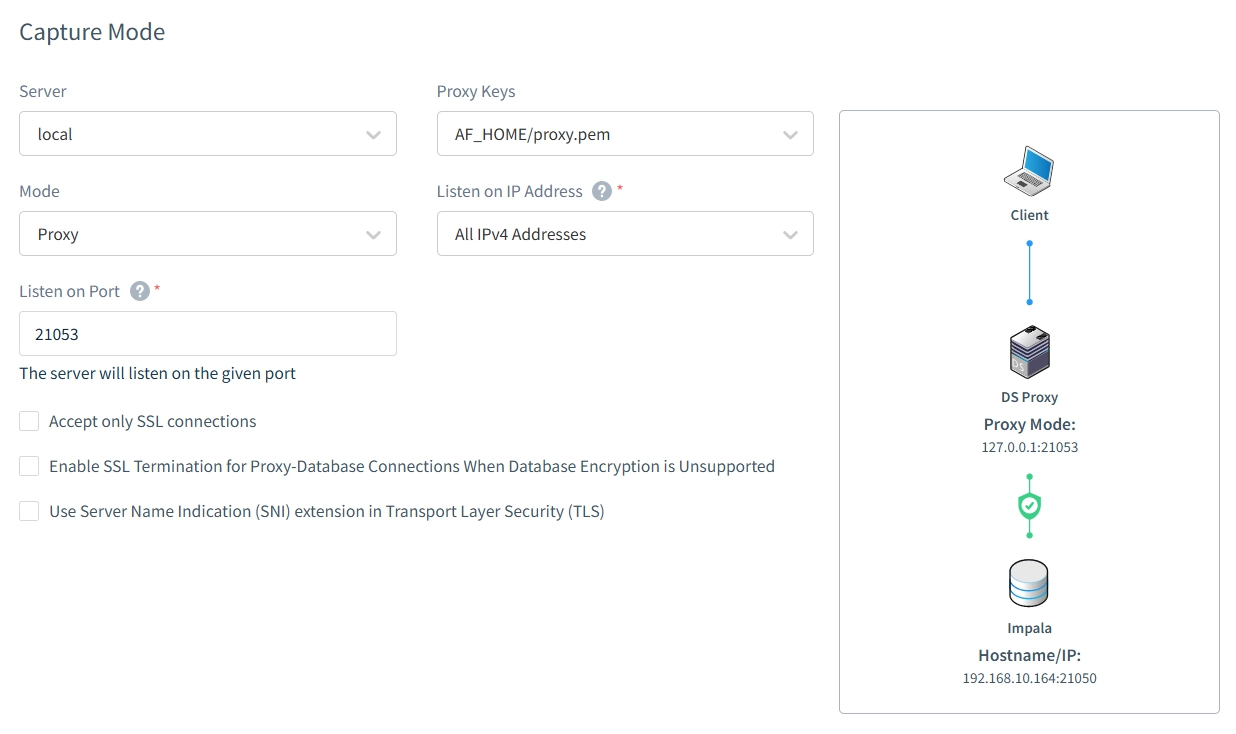
- Automated Compliance: DataSunrise streamlines audit processes through automation of compliance reporting and monitoring tasks. This automation significantly reduces manual effort compared to traditional log analysis.
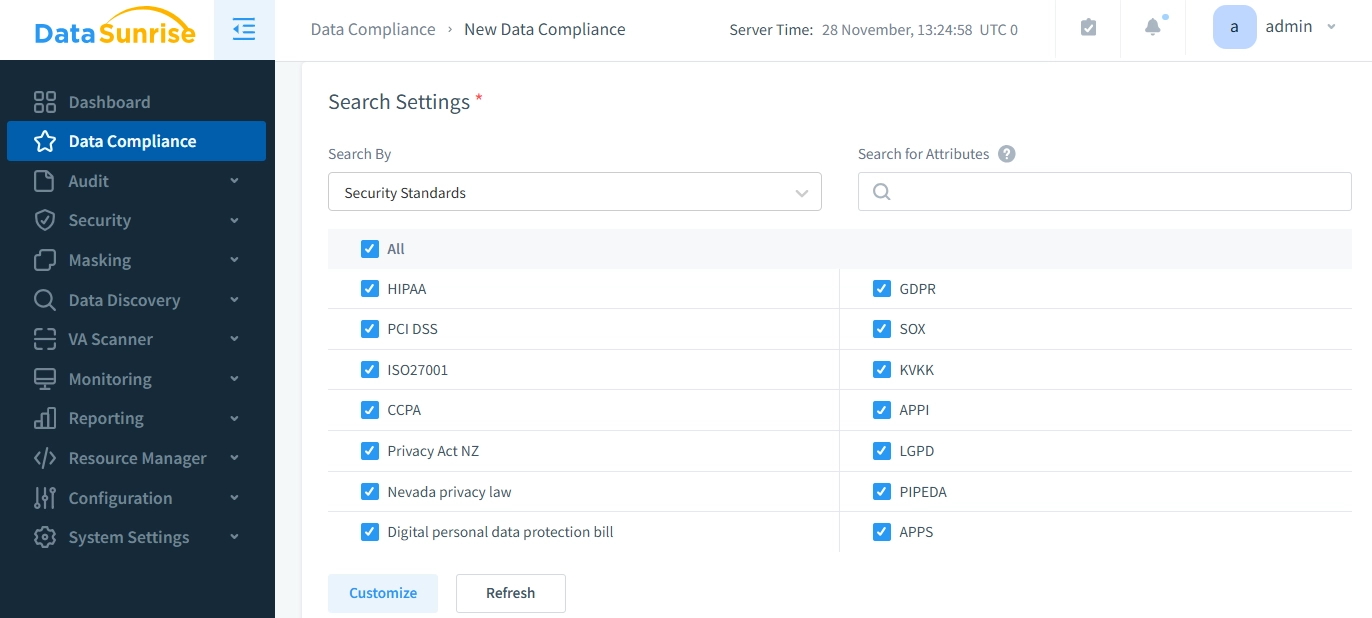
- Advanced Security Tools: Going beyond just basic logging and auditing, DataSunrise offers sophisticated features including instant notifications, highly customizable security policies, and pattern analysis for security threats.
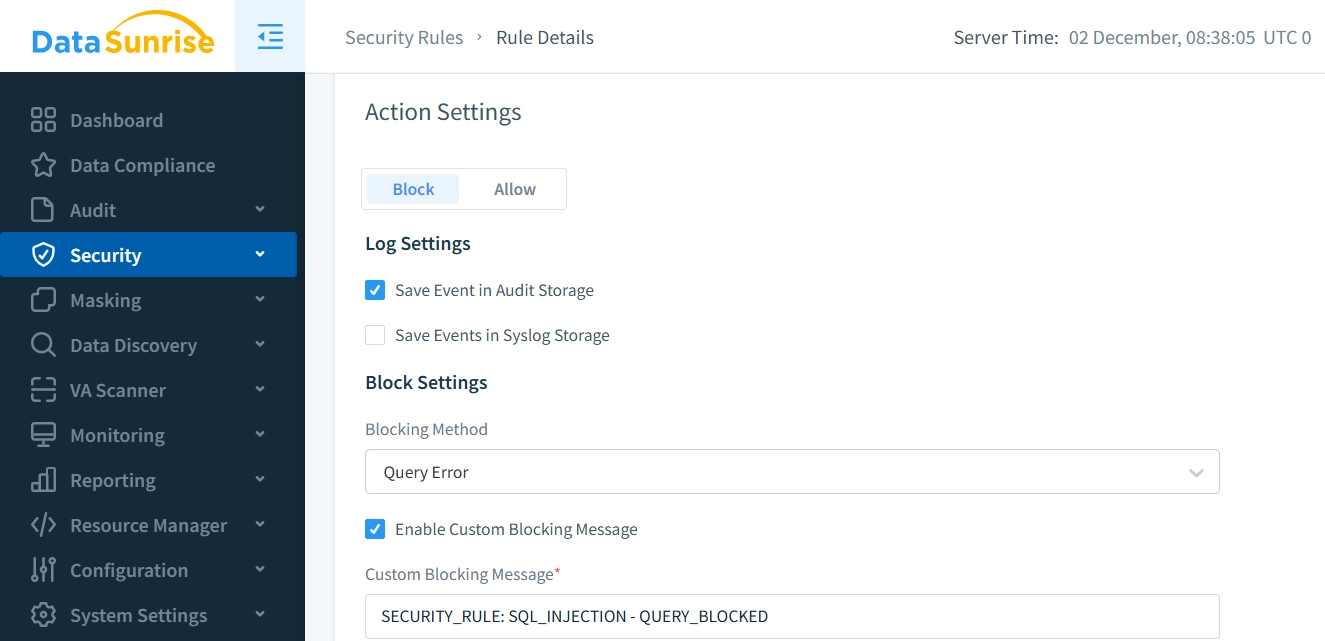
- Cross-Platform Integration: With support extending to over 40 database systems alongside Impala, DataSunrise enables standardized database activity monitoring across diverse database environments.
Moving Forward with DataSunrise
DataSunrise offers a powerful alternative to data audit for Impala using native tools by providing faster deployment, enhanced features, and reduced operational complexity. With real-time activity monitoring, advanced analytics, and broad platform support, DataSunrise helps organizations meet compliance requirements and secure their databases effectively.
Choose DataSunrise to transform how you manage audits and security in Impala, ensuring scalability, compliance, and simplicity. To explore how DataSunrise can optimize auditing in Impala and strengthen database security, schedule an online demo and discover its advanced features and streamlined approach.
