
Implementing Data Auditing for SAP HANA: Best Practices and Solutions

Introduction
SAP HANA, a powerful in-memory database platform, handles vast amounts of critical data. This makes data audit in SAP HANA essential for maintaining security and compliance.
Did you know that 77% of organizations experienced a data breach in 2022? This startling statistic highlights the importance of robust data auditing practices.
This article will explore the fundamentals of data audit for SAP HANA, covering native capabilities and advanced solutions. We will explore the features of SAP HANA and see how other tools can improve your data protection plan.
Data Audit for SAP HANA Capabilities
Native Auditing Features
SAP HANA offers several built-in auditing capabilities. These features allow organizations to track database activities and monitor user actions. Here’s a brief overview of key native auditing functions:
- Audit Policies: Administrators can create custom audit policies to track specific events.
- Audit Logs: SAP HANA generates detailed logs of audited activities.
- System Views: Special views provide access to audit information.
To enable auditing, use the following command:
ALTER SYSTEM ALTER CONFIGURATION ('global.ini', 'SYSTEM') SET ('auditing configuration', 'global_auditing_state') = 'true' WITH RECONFIGURE;This activates global auditing in SAP HANA.
Configuring Audit Policies
Creating effective audit policies is crucial for monitoring database activity. Here’s a basic example of how to create an audit policy:
CREATE AUDIT POLICY sample_policy AUDITING ALL STATEMENTS LEVEL INFO TRAIL TABLE;
This policy audits all statements at the INFO level and stores results in a table.
Native Data Audit Capabilities for SAP HANA
SAP HANA provides several built-in options for data auditing. These tools help organizations monitor database activities without additional software. Let’s explore some key native auditing features:
System Views for Auditing
SAP HANA offers system views that provide valuable audit information. Here are some important views:
- AUDIT_LOG: Contains all audit entries.
- CONFIGURED_OBJECTS: Shows objects configured for auditing.
To query the audit log, use:
SELECT * FROM SYS.AUDIT_LOG WHERE TIMESTAMP > ADD_DAYS(CURRENT_TIMESTAMP, -1);
This retrieves audit entries from the last 24 hours.
Audit Trails
SAP HANA supports different types of audit trails:
- Table-based: Stores audit data in database tables.
- File-based: Writes audit information to files.
To switch to file-based auditing, use:
ALTER SYSTEM ALTER CONFIGURATION ('global.ini', 'SYSTEM') SET ('auditing configuration', 'audit_trail_type') = 'FILE' WITH RECONFIGURE;This command changes the audit trail type to file-based storage.
Enhanced Data Audit for SAP HANA with DataSunrise
While SAP HANA’s native auditing capabilities are useful, they may not meet all compliance requirements. This is where third-party solutions like DataSunrise come in handy.
Creating a DataSunrise Instance
To set up DataSunrise for SAP HANA auditing:
- Download and install DataSunrise software.
- Configure connection to your SAP HANA database.
- Set up auditing rules and policies.
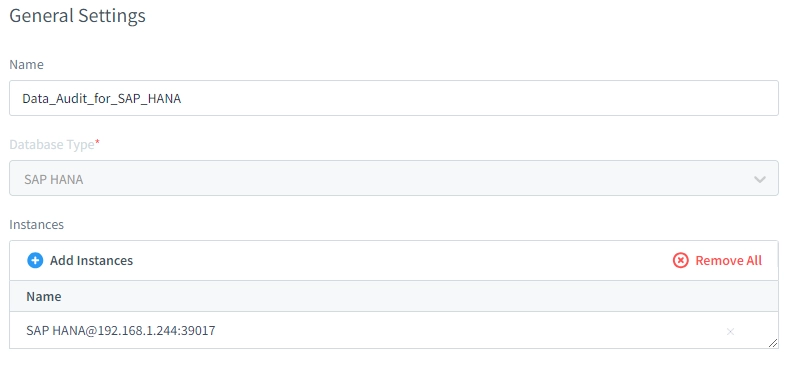
DataSunrise offers a user-friendly interface for easy configuration and management.
Detailed Event Descriptions
DataSunrise provides comprehensive event descriptions for SAP HANA data auditing. These descriptions include:
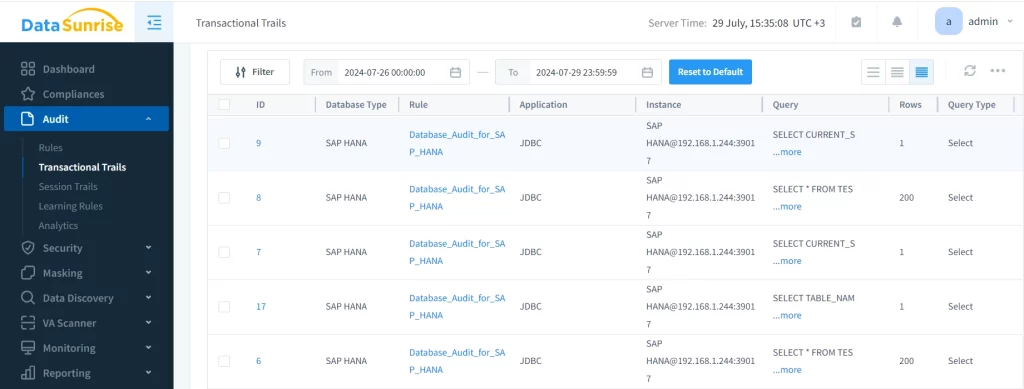
- User information
- Query details
- Accessed objects
- Timestamp data
This level of detail aids in forensically analyzing and compliance reporting.
Key Benefits of Advanced Data Auditing
Implementing robust data auditing for SAP HANA offers several advantages:
- Enhanced Security: Detect and prevent unauthorized access attempts.
- Compliance: Meet regulatory requirements like GDPR and HIPAA.
- Performance Optimization: Identify inefficient queries and optimize database performance.
- Forensic Analysis: Investigate security incidents with detailed audit trails.
Best Practices for SAP HANA Data Auditing
To maximize the effectiveness of your data audit strategy:
- Define Clear Objectives: Determine what data and activities to audit.
- Use Targeted Policies: Create specific audit policies for sensitive data.
- Regular Review: Analyze audit logs frequently to identify anomalies.
- Combine Native and Third-Party Tools: Leverage both SAP HANA’s built-in features and advanced solutions like DataSunrise.
Database Activity Monitoring
Continuous database activity monitoring is crucial for maintaining data security. It helps organizations:
- Detect suspicious behavior in real-time
- Prevent data breaches before they occur
- Ensure compliance with data protection regulations
Advanced tools offer real-time alerts and customizable dashboards for efficient monitoring.
Protecting Sensitive Data
Identifying and safeguarding sensitive data is a critical aspect of data auditing. Consider these steps:
- Data Discovery: Use automated tools to locate sensitive information.
- Classification: Categorize data based on sensitivity levels.
- Access Control: Implement strict access policies for sensitive data.
- Encryption: Use encryption to protect data at rest and in transit.
Conclusion
Data audit for SAP HANA is essential for maintaining data security and compliance. While SAP HANA offers native auditing capabilities, advanced solutions like DataSunrise provide more comprehensive features. By combining native tools with third-party solutions, organizations can create a robust data auditing strategy. Visit our website at DataSunrise.com for an online demo and to explore how our solutions can enhance your SAP HANA data auditing capabilities.
Remember, effective data auditing is not just about tools. It requires a combination of technology, processes, and people working together to protect sensitive information.
