
Data Audit for Snowflake

Introduction
Organizations handle massive amounts of sensitive information through cloud data platforms. Snowflake, as a leading cloud data warehouse, processes critical business data daily. Organizations must ensure proper data auditing and security measures. Recent statistics show that data breaches cost companies an average of $4.35 million in 2023, highlighting the importance of robust practices in data audit for Snowflake.
Understanding Privacy Risks in Snowflake Connections
Database security starts with understanding potential vulnerabilities. When users connect to Snowflake, they face several privacy risks:
User authentication breaches pose a significant threat. Unauthorized access attempts can compromise sensitive data. Moreover, SQL injection attacks through malformed queries can expose database contents. Network sniffing during data transmission represents another critical risk.
Additionally, insider threats from privileged users require attention. Without proper auditing, malicious activities might go undetected. Therefore, implementing comprehensive audit trails becomes essential for security.
Native Audit Tools in Snowflake
Snowflake provides built-in capabilities for tracking user activities. The QUERY_HISTORY and LOGIN_HISTORY views serve as primary tools for monitoring database operations.
To access query history, administrators can use Login History:
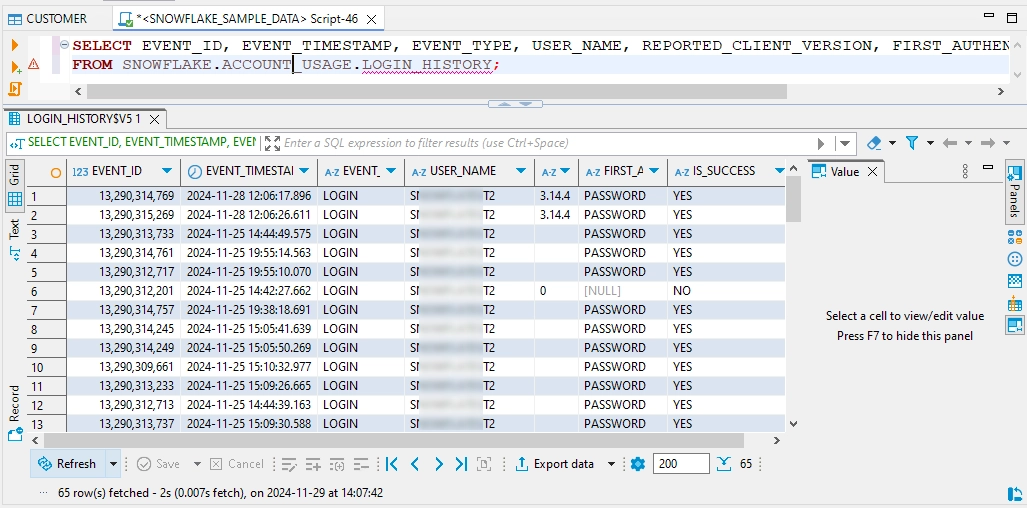
Note the failed login at line 6. This view provides essential information about executed queries, including:
- User name
- Login attempt timestamp
- Success status
Login attempts and authentication events are tracked through LOGIN_HISTORY. Error logging helps identify potential security incidents or system issues.
Query Auditing with Query History
Auditing provides an additional security layer while requiring minimal changes to existing infrastructure – systems need only connect through a proxy rather than directly to the database. Here’s an example of implementing data request using Python and ODBC:
import pyodbc
# Connection string
conn_str = (
"Driver={SnowflakeDSIIDriver};"
"Server=<sf_account>.snowflakecomputing.com;"
"Database=SNOWFLAKE_SAMPLE_DATA;"
"Schema=TPCH_SF1;"
"UID=<user_ID>;"
"PWD=<password>;"
"Proxy=192.168.10.56:1024;" # DataSunrise Proxy IP and port number.
"CABundleFile=C:\\TmpDataSnowflake\\certificate-key.txt" # Downloaded from DataSunrise Proxy.
)
# Establish connection
conn = pyodbc.connect(conn_str)
# Create cursor
cursor = conn.cursor()
try:
# Execute SQL query
cursor.execute("SELECT * FROM SNOWFLAKE_SAMPLE_DATA.TPCH_SF1.CUSTOMER LIMIT 10;")
# Fetch all rows
rows = cursor.fetchall()
# Print column names
print([column[0] for column in cursor.description])
# Print data
for row in rows:
print(row)
finally:
# Close cursor and connection
cursor.close()
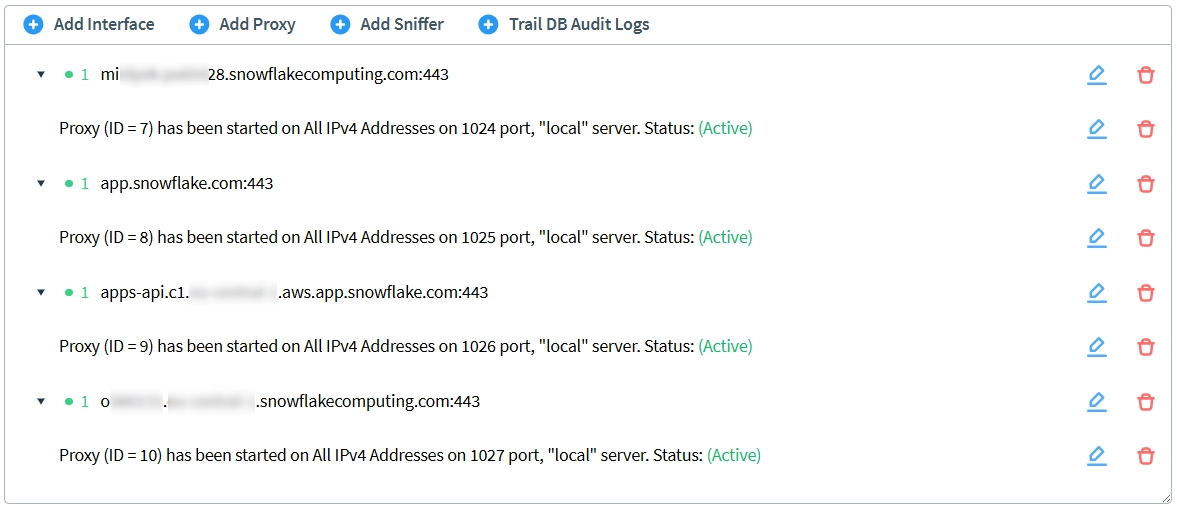
conn.close()Please note that the connection port is 1024, not the default 443, due to the proxied connection to Snowflake. By default, DataSunrise creates four proxies per instance to support full Snowflake functionality and ensure proper Web UI proxying:
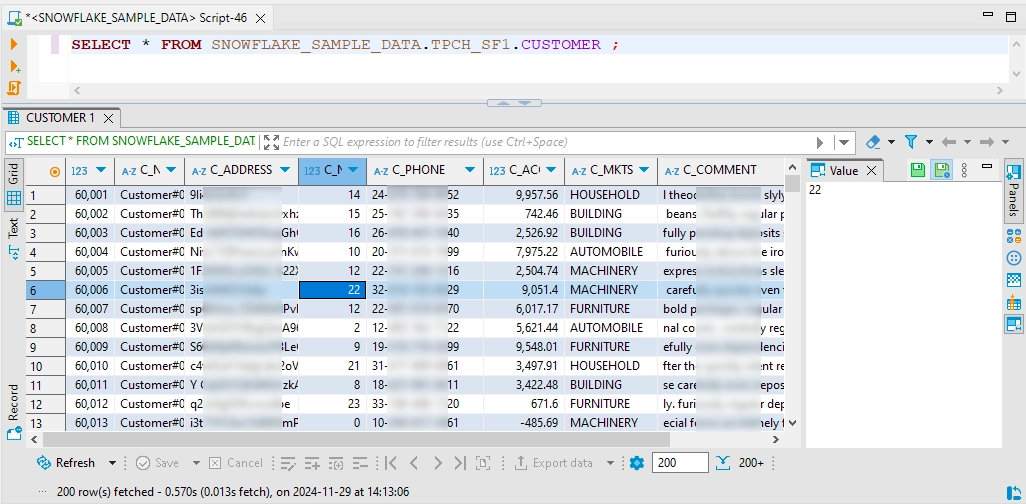
Data Audit for Snowflake: Query History Audit Results
Query
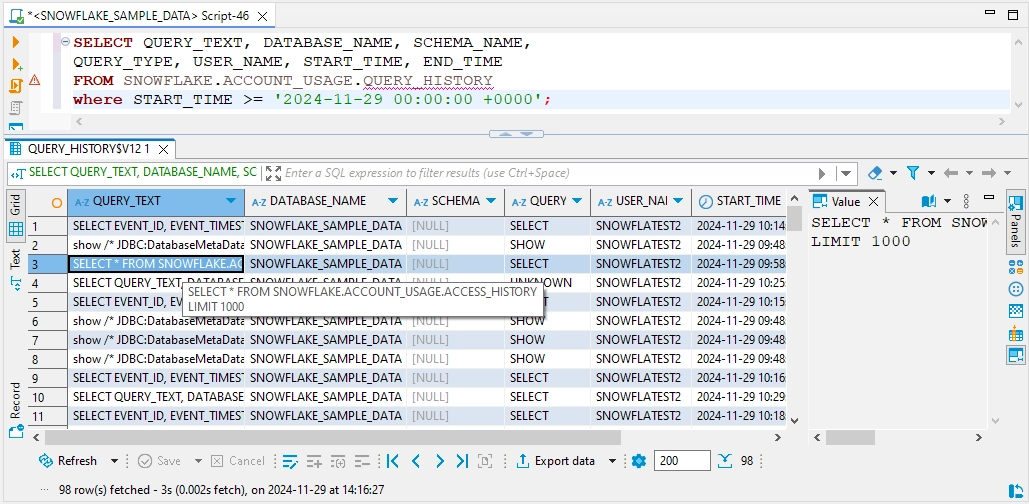
Audit results selected from QUERY_HISTORY:
Enhanced Security with Third-Party Tools
While native tools provide basic auditing, third-party solutions offer advanced features. These tools help organizations:
- Monitor real-time database activities.
- Detect suspicious patterns automatically.
- Generate comprehensive audit reports. Furthermore, they ensure compliance with regulations like HIPAA and GDPR.
Third-party solutions integrate with Snowflake’s native security features. This creates a multi-layered security approach. Advanced tools provide:
- Automated threat detection
- Custom alert configurations
- Detailed audit trails
- Compliance reporting
Regulatory Compliance and Audit Requirements
HIPAA and GDPR mandate strict data protection measures. Organizations must maintain detailed audit trails of data access. They need to demonstrate:
- Access control implementation.
- Data encryption methods.
- Regular security assessments. Moreover, they must prove their ability to detect and report breaches promptly.
The Role of DataSunrise in Snowflake Auditing
DataSunrise offers comprehensive Snowflake audit capabilities. Our solution utilizes proxy technology to monitor database sessions effectively. This approach provides:
- Real-time activity monitoring
- Detailed transaction logs
- Security policy enforcement
- Compliance reporting tools
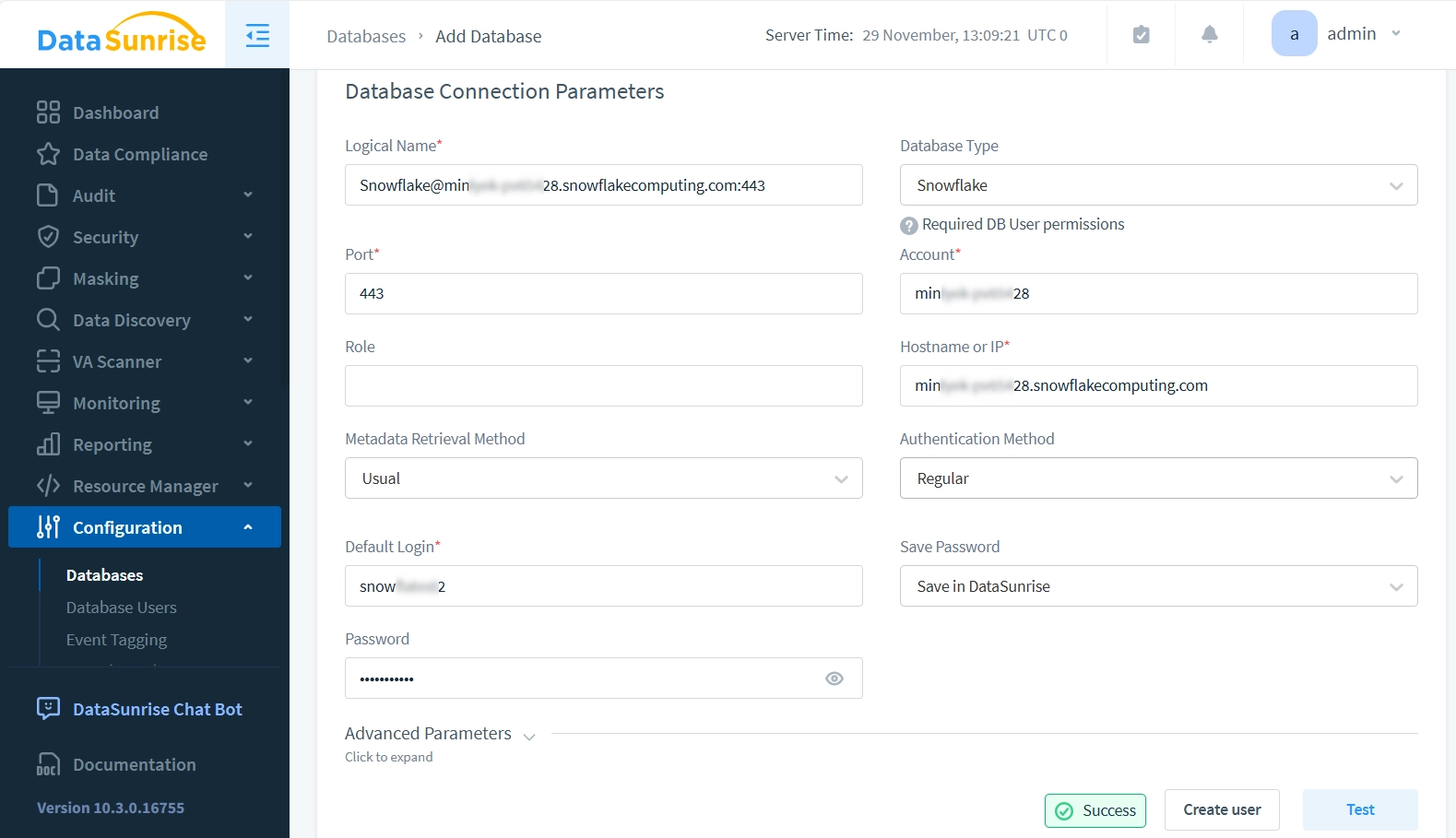
Follow these straightforward steps to implement DataSunrise Proxy (should be installed in Proxy Mode), starting with instance creation:
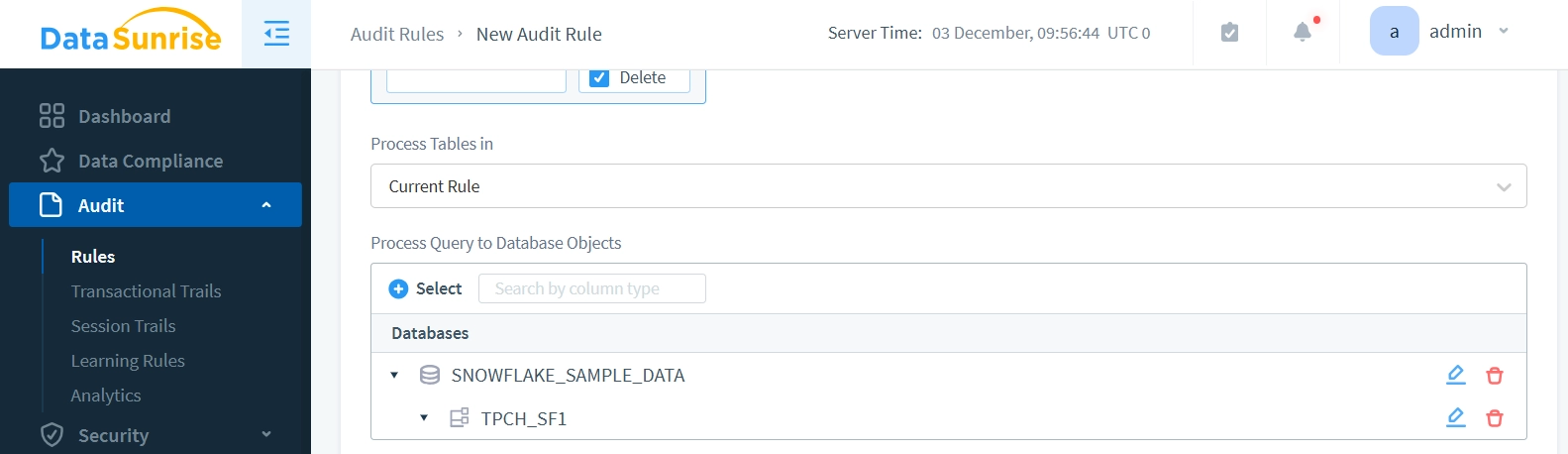
Create an Audit Rule with selection of proper components as below (‘tpch_sf1’ schema is selected):
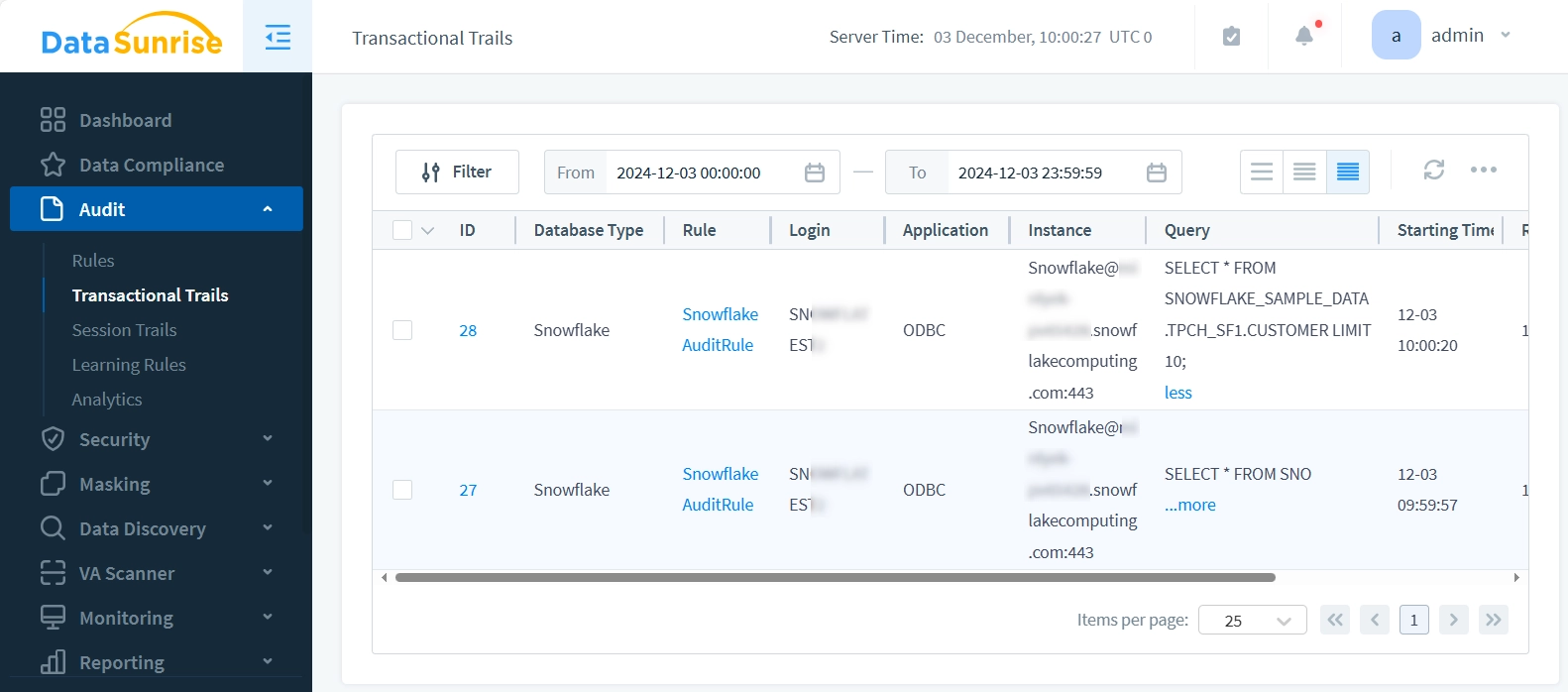
Now as the data requested using Python script, we see the logged audit entry in the Transactional Trails:
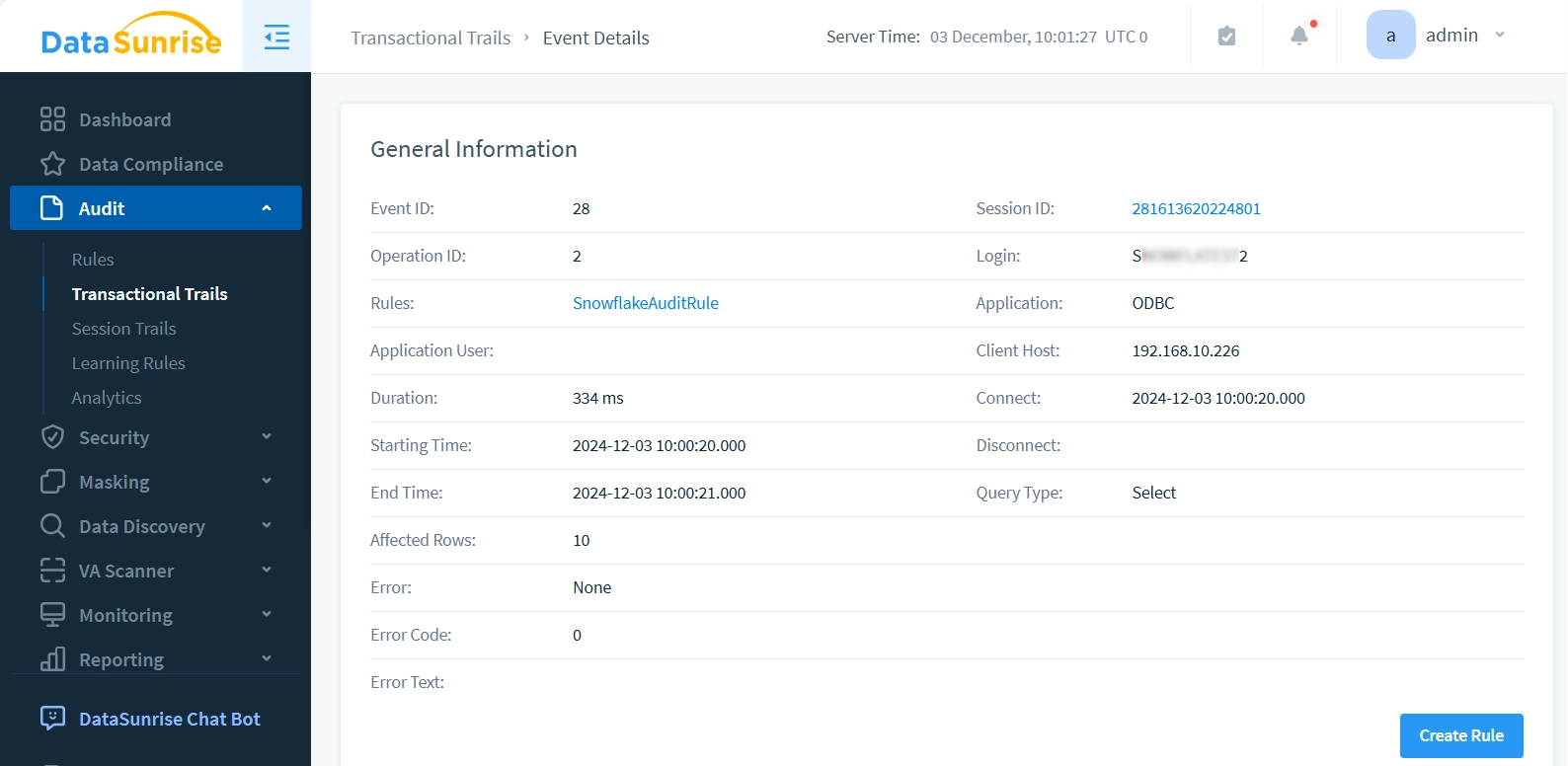
DataSunrise enables you to analyze user behavior through detailed transaction logs, which can be exported to your machine learning pipelines or analyzed directly within the platform. Each logged event is interactive and contains comprehensive information when clicked, providing valuable insights into user activities:
Conclusion
Effective data auditing in Snowflake requires a comprehensive approach. Native tools provide essential monitoring capabilities. However, third-party solutions enhance security significantly. Organizations should implement both for optimal protection.
Additional Note on DataSunrise
DataSunrise leads in database security innovation. Our platform offers flexible, cutting-edge tools including:
- Advanced activity monitoring
- Vulnerability assessment
- Dynamic data masking
- Access control management
Experience these capabilities firsthand through our online demo at DataSunrise’s website.
