Data Audit for Teradata
Introduction
In today’s data-driven world, securing sensitive information is more critical than ever, especially within complex database ecosystems. A data audit is an essential practice for businesses aiming to maintain the integrity, confidentiality, and accessibility of their data assets. Teradata, renowned for its high-performance analytics and data warehousing capabilities, offers powerful native features to monitor and track database activity effectively. This article explores the built-in audit functionalities of Teradata and how external solutions that can elevate your database security strategy.
Native Data Audit for Teradata
Teradata provides comprehensive native auditing features designed to track database activities, enforce compliance, and detect unauthorized access attempts. The data audit for Teradata relies on its built-in Database Auditing Facility (DBAF), which logs various activities at the system level. These logs help database administrators (DBAs) monitor user actions, track changes, and identify potential security breaches.
Setting Up Audit Rules
You can enable auditing in Teradata using the BEGIN LOGGING statement, which creates logging rules stored in
the DBC.AccLogRuleTbl table. These rules determine which
privilege checks generate log entries in the DBC.AccLogTbl table.
Here are some examples of setting up audit rules:
1. Logging Specific Actions on a Table
To log specific actions like SELECT, INSERT, UPDATE, and DELETE on a particular table, you can
use the following command:
BEGIN LOGGING ON EACH SELECT, INSERT, UPDATE, DELETE ON database_name.table_name; This command ensures that every SELECT, INSERT, UPDATE, and DELETE operation on the specified table
is logged.
2. Logging Denied Access Attempts
To log all denied access attempts, you can use the DENIALS keyword:
BEGIN LOGGING DENIALS ON EACH ALL;This command logs every denied access attempt across the database, helping you identify unauthorized access attempts.
3. Logging Administrative Actions
To log actions performed by administrative users, you can specify the usernames of the administrators:
BEGIN LOGGING ON EACH ALL BY "DBADMIN", "SECADMIN", "admin1";This command logs all actions performed by the specified administrative users, ensuring that their activities are monitored.
4. Logging Creation and Deletion of System-Level Objects
To log the creation and deletion of system-level objects, such as tables, views, and databases, you can use the following command:
BEGIN LOGGING ON EACH CREATE TABLE, DROP TABLE, CREATE VIEW, DROP VIEW, CREATE DATABASE, DROP DATABASE ON DATABASE "DBC"; This command logs all CREATE and DROP operations on
tables, views, and databases within the DBC database.
5. Logging Access to Audit Trails
To log access attempts to audit trails, you can use the following commands:
LOGGING ON EACH ALL ON TABLE DBC.AccessLogTbl;
BEGIN LOGGING ON EACH ALL ON VIEW DBC.AccessLog;
BEGIN LOGGING ON EACH ALL ON VIEW DBC.DeleteAccessLog;
BEGIN LOGGING ON EACH ALL ON TABLE DBC.EventLog;
BEGIN LOGGING ON EACH ALL ON VIEW DBC.LogOnOff;These commands log all access attempts to the audit-related tables and views, ensuring that any attempts to view or modify audit logs are recorded.
Querying Audit Logs
Teradata stores audit logs in the DBC.AccLogTbl table. You can
query this table to retrieve audit logs based on specific criteria. For
example, to retrieve all log entries for a specific user:
SELECT * FROM DBC.AccLogTbl WHERE LogonUser = 'username';This query fetches all log entries for the specified user, allowing you to monitor their activities.
To retrieve all denied access attempts:
SELECT * FROM DBC.AccLogTbl WHERE AccessResult = 'Denied';This query fetches all log entries where access was denied, helping you identify potential security breaches.
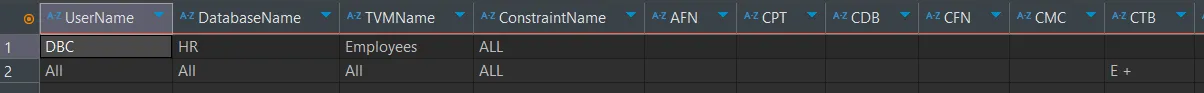
Verifying Audit Rules
After setting up audit rules, you can verify them by querying the DBC.AccLogRulesV view:
SELECT * FROM DBC.AccLogRulesV;This query displays all active logging rules, allowing you to ensure that the rules are correctly configured:
For more detailed information on Teradata native audit capabilities consult the Teradata official documentation.
Data Audit for Teradata with DataSunrise
For organizations seeking a more robust and flexible auditing framework, integrating Data Audit for Teradata with DataSunrise is an excellent choice. DataSunrise is an all-in-one database security solution designed to enhance auditing, monitoring, and data masking capabilities across various database environments.
DataSunrise Audit Capabilities
One of the standout features of DataSunrise is its real-time activity monitoring, which provides in-depth visibility into all database operations. It enables:
- Real-time alerts on unauthorized access attempts: DataSunrise can instantly notify administrators of suspicious activities, such as unauthorized access attempts or unusual query patterns.
- Detailed reporting of user activity: The platform generates comprehensive reports that provide insights into user behavior, helping organizations identify potential security risks.
- Comprehensive auditing of both structured and unstructured data: DataSunrise supports auditing across a wide range of data types, ensuring that no sensitive information goes unmonitored.
Advantages of using DataSunrise for Teradata auditing:
- Granular Access Control: Allows defining user-specific permissions for various actions, ensuring that only authorized users can access sensitive data.
- Advanced Reporting: Generates detailed audit logs and visual dashboards, making it easier to analyze and interpret audit data.
- Compliance Ready: Helps meet industry standards like GDPR, HIPAA, and PCI DSS by providing the necessary tools to track and report on data access and usage.
- Automated Alerts: Sends real-time notifications on security incidents, enabling quick response to potential threats.
- Data Masking: Protects sensitive data without affecting database functionality, ensuring that sensitive information remains secure even during testing or development.
Conclusion
Conducting a thorough data audit for Teradata is essential for ensuring that your enterprise data remains secure, compliant, and accessible. While Teradata offers solid native auditing capabilities, integrating an advanced solution like DataSunrise can take your security posture to the next level. From real-time monitoring to advanced reporting and compliance support, DataSunrise addresses the growing needs of modern businesses.
If you’re ready to enhance your database auditing capabilities, try DataSunrise by booking a personal demo or downloading the tool today. A robust and comprehensive auditing solution is just a step away from fortifying your data security strategy.
