
Data Audit in Greenplum

Implementing a data audit trail in Greenplum provides organizations with crucial visibility into database activities and modifications. As companies handle increasing volumes of sensitive data, robust auditing capabilities have become essential for data governance. Recent IBM Security research reveals that data breaches cost organizations an average of $4.45 million, highlighting the importance of comprehensive audit systems.
For businesses managing sensitive information, Greenplum Database offers systematic tracking and verification of database activities through its native auditing features. This methodical approach supports compliance requirements while providing insights into data access patterns and potential security concerns.
Understanding Greenplum’s Native Audit Features
Greenplum provides comprehensive audit functionality through its server log files. The system captures all database activities, including:
- User authentication attempts
- SQL statement execution
- System startup and shutdown events
- Segment database failures
- Query errors and execution times
Setting Up Basic Audit Trail in Greenplum
To implement basic auditing in Greenplum, follow these steps:
-- Enable connection logging log_connections = on -- Log session disconnections log_disconnections = on -- Set statement logging level log_statement = 'all' -- Configure minimum duration logging log_min_duration_statement = 1000
After configuring these settings, the server logs will capture database activities in CSV format, including:
- Timestamp
- Username
- Database name
- Client host information
- Session and transaction IDs
- SQL state codes and error messages
Querying and Managing Audit Data
Viewing Recent Activities
# Display recent log entries gplogfilter -n 10 # Filter logs for specific users gplogfilter -u admin -n 5
Analyzing Specific Time Periods
# View logs within a date range gplogfilter -b '2024-01-01 00:00:00' -e '2024-01-31 23:59:59'
Examples of SQL Audit Commands
Here are some practical examples of SQL commands for auditing in Greenplum using the clients table:
1. Tracking Data Modifications
SELECT current_user as modified_by,
action_tstamp_tx::date as modification_date,
action as operation_type,
count(*) as operation_count
FROM audit.logged_actions
WHERE table_name = 'clients'
AND schema_name = 'public'
AND database_name = 'testdb'
GROUP BY current_user, action_tstamp_tx::date, action
ORDER BY modification_date DESC;
Example output:
| modified_by | modification_date | operation_type | operation_count |
|---|---|---|---|
| admin | 2024-02-11 | UPDATE | 15 |
| etl_user | 2024-02-11 | INSERT | 8 |
| analyst | 2024-02-10 | SELECT | 45 |
| admin | 2024-02-10 | DELETE | 2 |
| etl_user | 2024-02-09 | UPDATE | 6 |
2. Monitoring Access to Sensitive Data
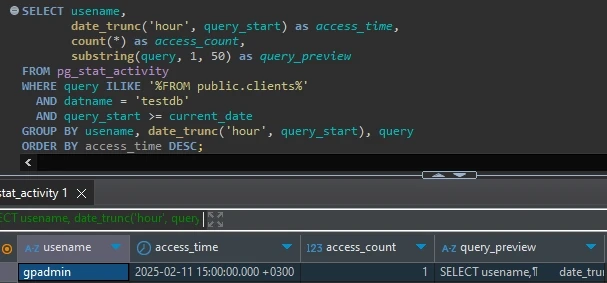
SELECT usename,
date_trunc('hour', query_start) as access_time,
count(*) as access_count,
substring(query, 1, 50) as query_preview
FROM pg_stat_activity
WHERE query ILIKE '%FROM public.clients%'
AND datname = 'testdb'
AND query_start >= current_date
GROUP BY usename, date_trunc('hour', query_start), query
ORDER BY access_time DESC;
Example output:
3. Analyzing Data Changes
SELECT a.usename,
c.first_name,
c.last_name,
date_trunc('minute', a.query_start) as operation_time,
substring(a.query, 1, 50) as operation_details
FROM pg_stat_activity a
INNER JOIN public.clients c ON a.query LIKE '%client_id = ' || c.id || '%'
WHERE a.datname = 'testdb'
AND a.query ILIKE '%UPDATE%'
AND a.query_start >= current_timestamp - interval '24 hours'
ORDER BY operation_time DESC;
Example output:
| usename | first_name | last_name | operation_time | operation_details |
|---|---|---|---|---|
| admin | Bob | Marley | 2024-02-11 15:30:00 | UPDATE public.clients SET birth_date = ‘1945-02-… |
| etl_user | Michael | Jackson | 2024-02-11 15:15:00 | UPDATE public.clients SET sex = ‘M’ WHERE clien… |
| analyst | Sharon | Stone | 2024-02-11 14:45:00 | UPDATE public.clients SET last_name = ‘Stone’ W… |
| support | David | Beckham | 2024-02-11 14:30:00 | UPDATE public.clients SET first_name = ‘David’ … |
Enhancing Greenplum with DataSunrise
While Greenplum’s native audit features are robust, organizations often need additional security measures. DataSunrise’s database security solution enhances Greenplum’s capabilities with advanced features like data masking and real-time monitoring.
Setting Up DataSunrise for Greenplum
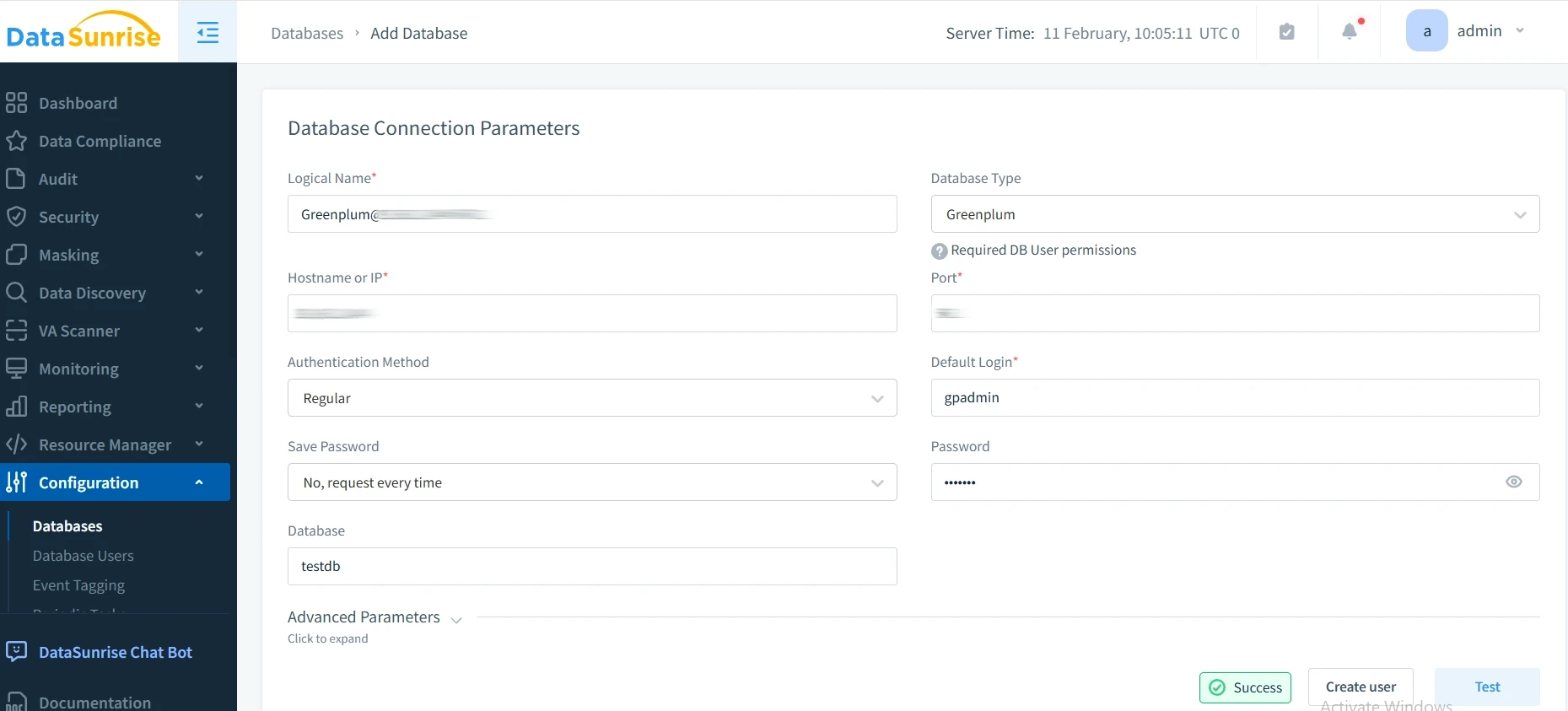
- Install DataSunrise: Begin with DataSunrise installation, following the provided documentation.
- Configure Connection: Connect DataSunrise to your Greenplum instance.
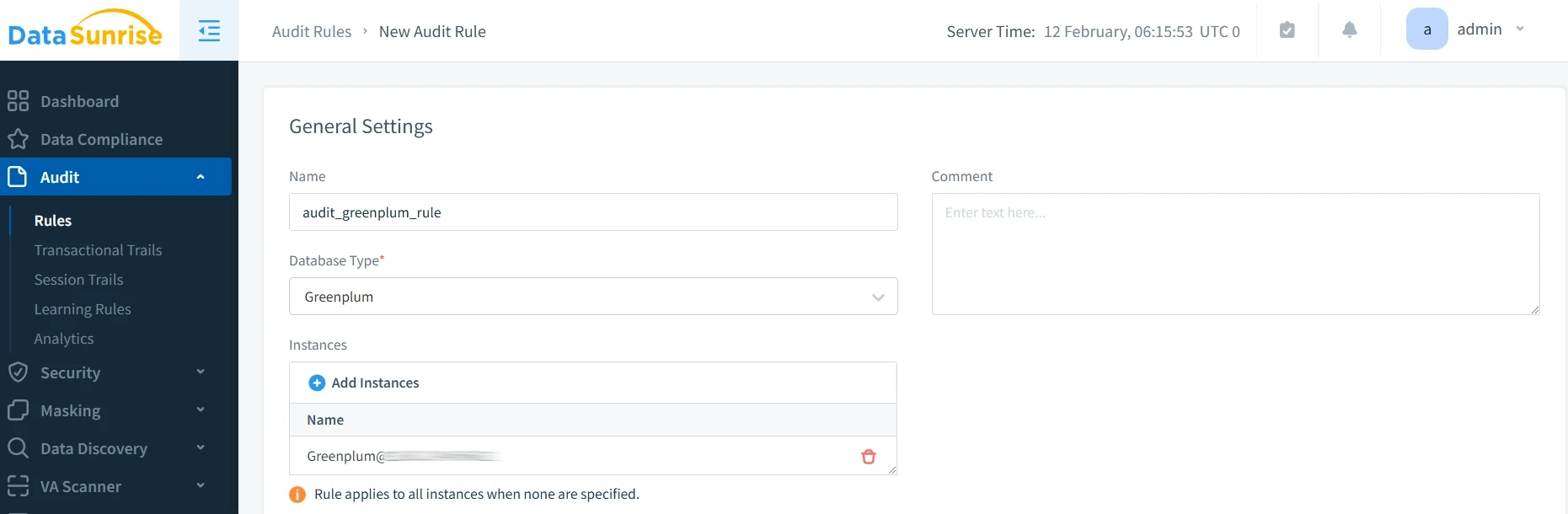
- Set Audit Rules: Define specific tracking rules for sensitive data and operations.
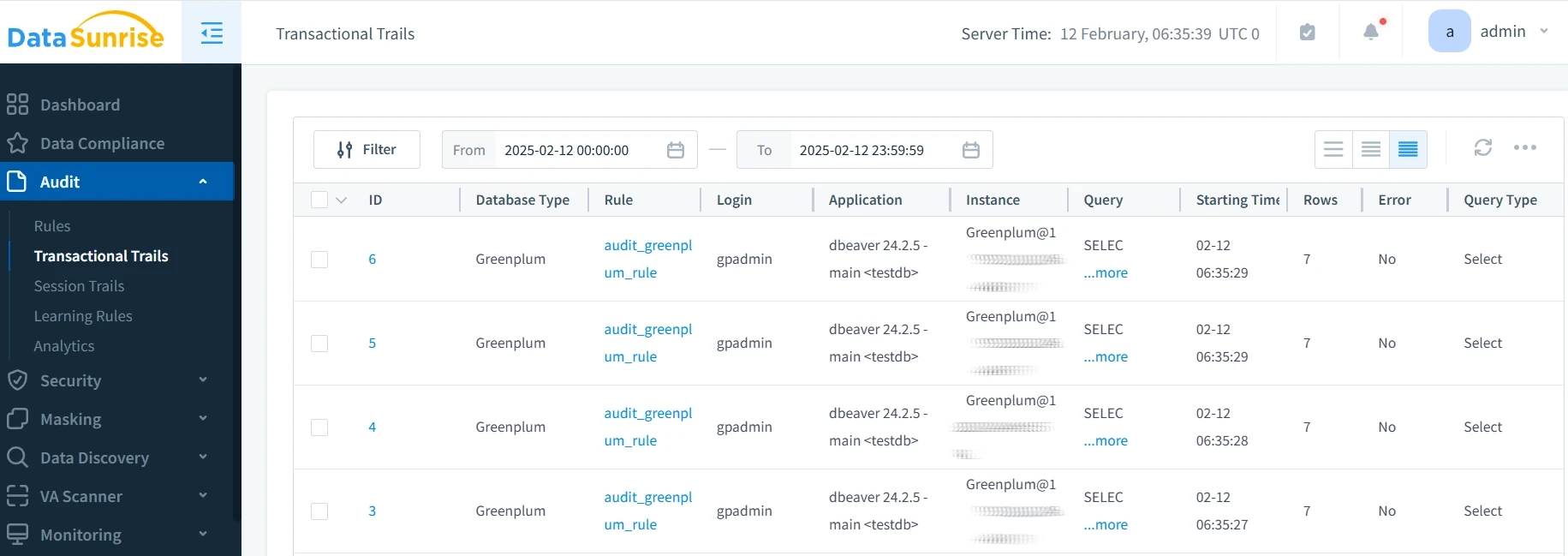
- Review Audit Trails: Monitor database activities through DataSunrise’s dashboard.
Benefits of DataSunrise’s Security Suite
- Centralized Control: Manage all audit rules from a single interface
- Regulatory Compliance: Meet requirements for GDPR, HIPAA, and other regulations
- Enhanced Security: Protect sensitive data with advanced masking and monitoring
- Real-time Alerts: Receive immediate notifications of suspicious activities
Best Practices for Audit Trail Management
Regular Monitoring and Review
Effective audit trail management demands a systematic approach to monitoring database activities. Organizations should establish consistent schedules for audit log reviews, typically conducting them weekly or bi-weekly depending on data sensitivity and regulatory requirements. These reviews should focus on identifying unusual patterns, unauthorized access attempts, and unexpected data modifications.
Performance Management
Performance considerations play a crucial role in maintaining an efficient audit system. Implementing audit log rotation prevents the audit tables from growing unnecessarily large and impacting database performance. Organizations should establish data retention policies that balance compliance requirements with system performance. Regularly archiving older audit data to separate storage helps maintain optimal database operation while preserving historical records.
Documentation and Compliance
Documentation procedures require particular attention in audit trail management. Teams should maintain comprehensive records of audit policies, including the scope of audited operations, retention periods, and access controls. These policies should be reviewed and updated regularly to reflect changing business needs and regulatory requirements.
Security Controls
Protecting the integrity of audit trails requires robust security controls. Access to audit logs should be strictly limited to authorized personnel, with all access attempts logged and monitored. Organizations should implement encryption for sensitive audit data, especially when it contains personally identifiable information or other protected data types.
Third-Party Integration
Integration with third-party solutions like DataSunrise can enhance audit capabilities beyond native features. These tools provide additional layers of security through advanced data masking, centralized audit management, and specialized compliance reporting. When implementing such solutions, organizations should ensure seamless integration with existing audit processes and maintain consistent policies across all tools.
Conclusion
Greenplum’s native audit capabilities provide essential database security features. However, organizations requiring advanced protection can enhance their setup with DataSunrise’s comprehensive security suite.
Learn more about strengthening your Greenplum database security by scheduling an online demo of DataSunrise’s advanced features.
