
Ensuring Data Security with Data Audit in MariaDB

MariaDB is a popular open-source database system used by many organizations. As businesses store more sensitive information, data auditing becomes crucial. Data audit in MariaDB helps track who accesses data, what changes they make, and when these actions occur. This process is vital for maintaining data integrity, ensuring compliance, and boosting security.
Data audit in MariaDB offers several benefits. It helps detect unauthorized access attempts, monitors changes to sensitive data, and provides a trail of user activities. This information proves invaluable for troubleshooting issues, investigating security breaches, and meeting regulatory requirements.
For instance, a bank using MariaDB can use data auditing to monitor access to customer account details. This helps them comply with regulations like GDPR or PCI-DSS. Similarly, an e-commerce platform can audit its order database to spot unusual activities or potential data breaches.
Key Features and Implementation of MariaDB Data Audit
MariaDB offers several features for effective data auditing. The Server Audit plugin is a built-in tool for comprehensive auditing. It allows administrators to log various database events, including successful and failed connections, query executions, and table access. An online store can use this tool to watch customer orders, spotting any strange behavior or possible data leaks.
The Event Scheduler in MariaDB allows for the automation of database maintenance tasks. Although not directly about auditing, it can help with scheduling regular log rotations and triggering custom audit procedures.
Implementation
Implementing data audit in MariaDB either by native means or using third-party solutions involves several steps.
To use MariaDB’s own features, first, enable the Server Audit plugin by adding the following line to your MariaDB configuration file:
plugin-load-add=server_audit=server_audit.so
Next, configure it to log specific events. For example, to audit all query executions, use:
SET GLOBAL server_audit_events=’QUERY’;
Then, set up where the audit logs will be stored:
SET GLOBAL server_audit_file_path=’/path/to/audit.log’;
Ensure that the log file is stored in a secure location with proper access controls.
Now let’s review how it’s done in DataSunrise using specific example. Say we need to audit a query:
Add a MariaDB instance to the configuration:
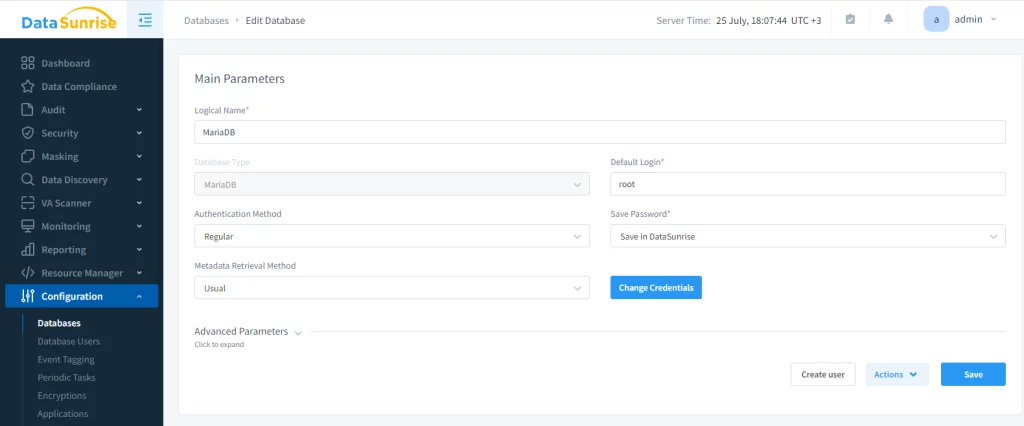
This allows to set up any auditing, security and masking to the database by using proxy. Next, create an audit rule and configure it to your needs. In our case, we choose to audit the ‘test_table’ table exclusively.
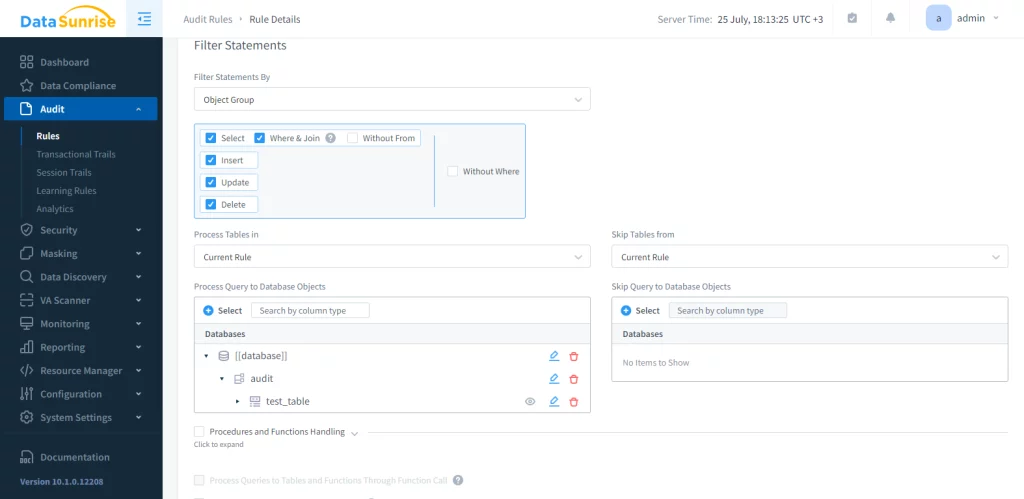
Afterwards, the system will audit all queries to the table and users can find logs in the “Transactional trails” section.
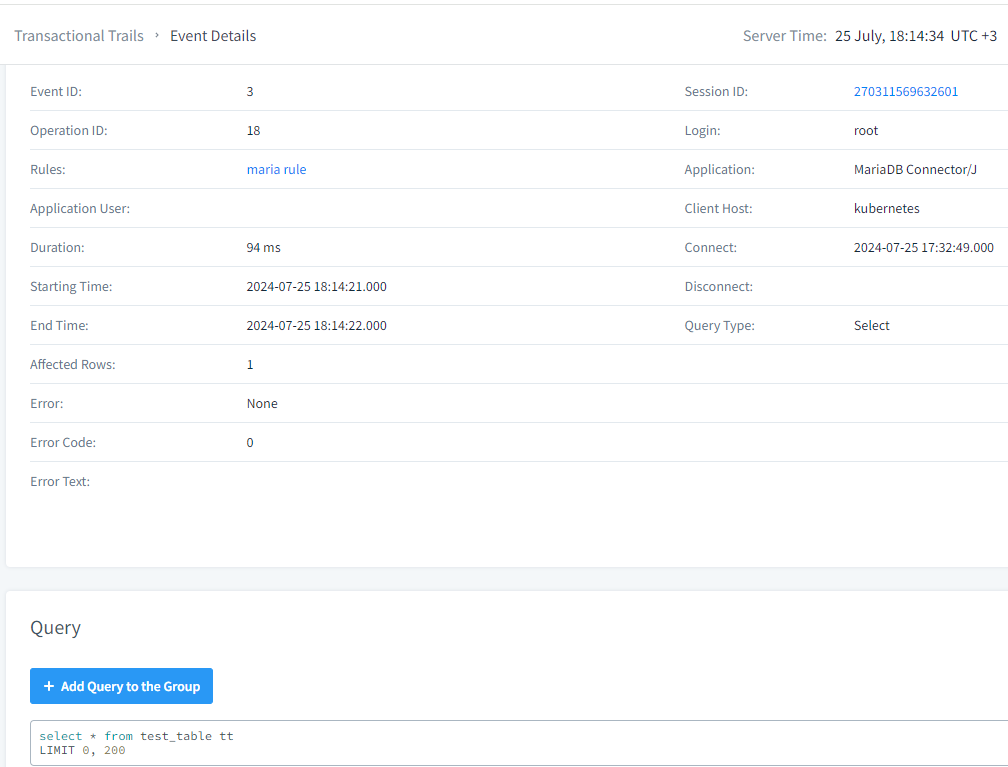
You can create custom audit rules to focus on specific tables or types of queries. For instance, to audit all actions on a sensitive customer_data table, you might use:
Best Practices and Challenges
To get the most out of your MariaDB data audit, consider these best practices. Set up a schedule to review audit logs regularly. This helps identify potential issues early and ensures your audit process works as expected.
Store audit logs in a secure location, separate from the database server if possible. This prevents unauthorized access and tampering of audit records.
Implement log rotation to manage the size of audit logs. This ensures that logs don’t consume too much disk space while retaining important audit data. Configure audit policies based on your specific needs. Focus on auditing critical tables, sensitive data access, and high-privilege user actions.
Consider integrating your MariaDB audit logs with security information and event management (SIEM) tools. This provides a centralized view of all security events across your infrastructure.
Audit logs may contain many routine events, making it challenging to identify genuine security issues. Develop strategies to filter and prioritize audit events effectively.
Real-world Examples of MariaDB Data Audit
Let’s look at some real-world examples of how organizations use data audit in MariaDB. A large bank uses MariaDB to store customer transaction data. They implement data auditing to track all access to customer accounts. This helps them detect fraudulent activities and comply with financial regulations.
An online marketplace audits its MariaDB database to monitor product price changes. This helps them identify and investigate any unauthorized price redaction, ensuring fair pricing for customers and sellers.
A hospital network uses MariaDB data audit to track access to patient records. They established custom audit rules to log every instance of viewing or modifying patient data. This helps them maintain patient privacy and comply with healthcare regulations.
Conclusion
Data audit in MariaDB is a powerful tool for enhancing security, ensuring compliance, and maintaining data integrity. By leveraging MariaDB’s built-in auditing features and following best practices, organizations can effectively monitor and protect their valuable data assets.
Data is becoming more valuable and abundant. This means that the need for strong auditing in database systems like MariaDB will increase. By practicing good data audit techniques now, you are protecting your current assets. Additionally, you are also securing your data for the future.
