
Data Audit in Oracle

Understanding Data Audit in Oracle
Oracle data audit is a powerful feature that helps organizations track and monitor database activities. It records user actions, system changes, and data access patterns. This tool is crucial for maintaining data integrity, detecting security breaches, and meeting compliance requirements.
Companies store vast amounts of <sensitive information in their databases. This data often includes customer details, financial records, and proprietary business information. Oracle data audit protects this valuable asset. It acts as a watchdog, alerting administrators to suspicious activities and providing a detailed trail of database interactions.
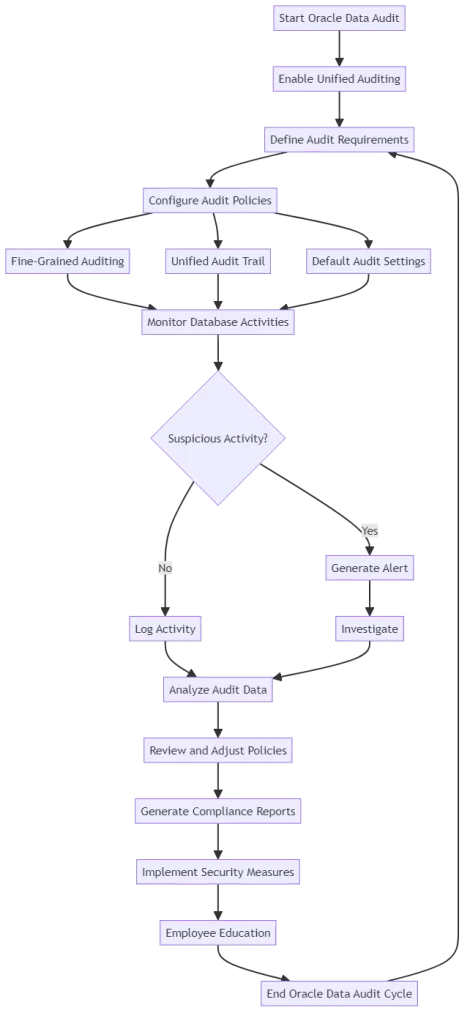
Oracle offers several robust auditing features. These tools allow organizations to create comprehensive audit strategies tailored to their specific needs. Fine-grained auditing lets you set up precise audit policies.
You can monitor specific columns, tables, or user actions. For example, you might audit all attempts to view salary information in the HR database.
The unified audit trail consolidates audit records from various sources into a single, easily accessible location. This feature simplifies the process of reviewing and analyzing audit data. Oracle also automatically audits certain critical activities, including database startup and shutdown events, and changes to audit settings.
Implementing Oracle Data Audit
Setting up an effective Oracle data audit strategy involves several steps. Start by determining what you need to audit. Consider your industry regulations and specific security concerns.
A healthcare provider might focus on auditing access to patient records. A financial institution might prioritize monitoring transactions and account changes.
Once you’ve identified your requirements, set up audit policies in Oracle. These policies define what activities to monitor and under what conditions. You might create a policy to track failed login attempts or monitor changes to critical tables. Regularly review your audit logs to spot potential issues.
Many organizations use specialized tools to automate this process. These tools can sift through large volumes of audit data and flag suspicious activities for further investigation.
Implementing a robust Oracle data audit strategy offers numerous advantages. It enhances security by helping you quickly detect and respond to potential threats. For instance, if you notice multiple failed login attempts from an unfamiliar IP address, you can take immediate action to block the suspicious activity.
Data audit in Oracle also supports compliance efforts by providing detailed records of database access and changes. You can easily generate reports showing who accessed what information and when. Furthermore, it can help you spot potential insider threats, such as a user accessing sensitive data outside of normal business hours or making unusual changes to critical tables.
Challenges and Best Practices
While Oracle data audit is extremely valuable, it does present some challenges. Extensive auditing can slow down database performance.
To mitigate this, consider a tiered approach. Implement baseline auditing for essential security events. Then, add more detailed auditing for high-risk activities or during off-peak hours.
Auditing also generates a lot of data, which can be challenging to store and analyze. Implement data retention policies to manage this issue. You might keep detailed audit data for 90 days, then archive or summarize older data for long-term storage.
Not every flagged activity in an audit log represents a real threat. Dealing with false alarms can be time-consuming. To address this, continually refine your audit policies. You might also use AI tools to establish normal activity patterns and flag significant deviations.
To get the most out of your Oracle data audit strategy, consider these best practices. Review and adjust your audit policies regularly. As your organization evolves, so should your auditing strategy.
You might check your policies quarterly to ensure they still meet your needs. Protect your audit logs from tampering. Implement strong access controls for audit data. Consider using write-once media for storage or implementing digital signatures to detect unauthorized changes.
Set up automated alerts for critical audit events. This allows for quick response to potential security incidents. You might configure an alert to notify your security team immediately if someone attempts to modify a critical system table.
Lastly, educate your employees about data auditing and its importance. When users understand that their actions are being monitored, they’re more likely to follow security policies. This can help prevent accidental data breaches and deter intentional misuse.
Conclusion
Oracle data audit is a powerful tool for protecting your valuable database assets. It enhances security, supports compliance efforts, and provides crucial insights into database usage patterns. While implementing an effective audit strategy requires effort, the benefits far outweigh the challenges. By leveraging Oracle’s robust auditing features and following best practices, you can significantly strengthen your data security posture.
Remember, Oracle data audit isn’t a one-time setup. It requires ongoing attention and refinement to remain effective. Regularly review and update your audit strategies to keep pace with evolving security threats and changing business needs. With diligent use of Oracle data audit, you can ensure the security and integrity of your critical data assets.
