
Data Audit in ScyllaDB

Introduction
In today’s data-driven world, organizations face the challenge of managing enormous amounts of data. To ensure business sustainability, they need performant and scalable tools capable of handling large datasets. ScyllaDB, known for its high-performance capabilities, stands out as a tool that excels at managing big data with low latency and high throughput. Moreover, with its efficient utilization of modern hardware, ScyllaDB has emerged as a compelling alternative to Apache Cassandra.
While data audit in large-scale databases is undoubtedly challenging, it is a crucial aspect of database security. Specifically, data auditing refers to the process of tracking, reviewing, and logging database activities, including data modifications, security access, and system anomalies. Such audits provide organizations with several benefits, including facilitating security investigations, ensuring regulatory compliance, monitoring performance, and troubleshooting issues. Therefore, for enterprises using ScyllaDB, implementing an effective data audit mechanism is even more critical.
When it comes to data audits in ScyllaDB, a variety of solutions are available, ranging from native auditing features to advanced third-party tools offering enhanced security and monitoring functionalities. This article explores how to implement data auditing in ScyllaDB, how to improve security with third-party tools, and the best practices for setting up an optimal data audit system.
What is Data Audit?
Data audit involves systematically tracking and recording every event or change within a database. This includes activities such as who accessed the data, what changes were made, and when those changes occurred. The primary goal of data auditing is to ensure transparency, security, and accountability in data management systems.
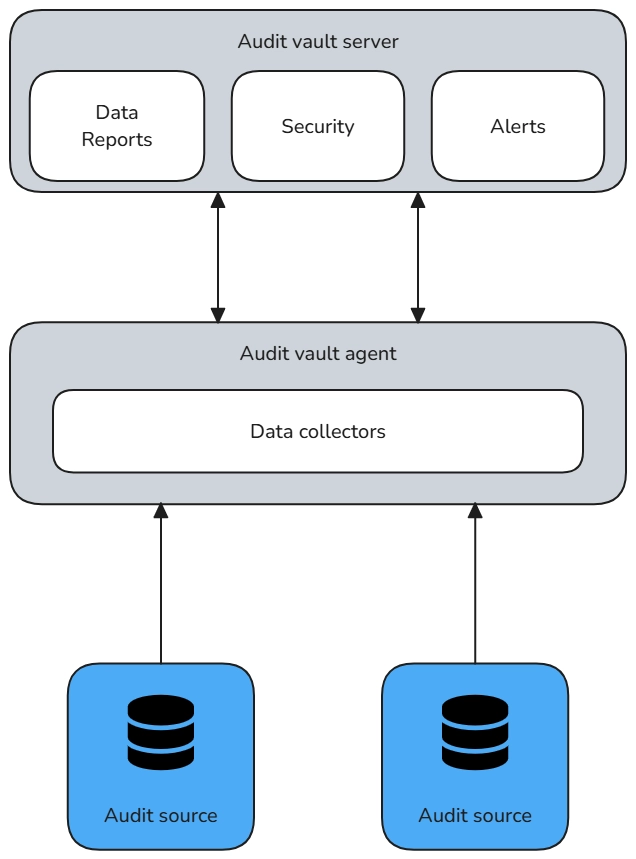
In ScyllaDB, a distributed NoSQL database, data auditing typically focuses on tracking read/write operations, user access logs, configuration changes, and system errors. These audits are essential for organizations aiming to meet regulatory compliance requirements (e.g., GDPR or HIPAA), identify malicious activity, ensure data integrity, or monitor user behavior. Without robust auditing in place, it becomes difficult to detect issues like data breaches, unauthorized access, or unexpected changes to data.
Furthermore, a comprehensive data audit system not only provides valuable insights but also strengthens your overall database security posture. Additionally, it helps organizations track performance metrics, which are crucial for diagnosing problems, optimizing system configurations, and improving operational efficiency.
Implementing Native Data Audit in ScyllaDB
ScyllaDB offers a native audit logging system designed for monitoring low-level database access and operations. While it provides basic auditing capabilities, it may lack advanced features such as rule-based auditing, enhanced security, and detailed logging, which are essential for complex audit requirements.
Enabling and Configuring Audit Logging in ScyllaDB
To enable and configure native audit logging in ScyllaDB, follow these steps:
- Edit the Configuration File: Open the
scylla.yamlconfiguration file and adjust the following parameters:
audit: Set this totableto enable logging to a specific table.audit_categories: Specify the types of database operations to audit, such asDCL,DDL, andAUTH.audit_keyspaces: Define the keyspaces for which you want to collect audit logs.
Example configuration:
audit: "table" audit_categories: "DCL, DDL, AUTH" audit_keyspaces: "my_keyspace"
Restart ScyllaDB: After updating the configuration, restart ScyllaDB to apply the changes.
Verify the Configuration: Perform database operations (e.g., creating or dropping tables) and query the audit logs to confirm that the operations are being recorded.
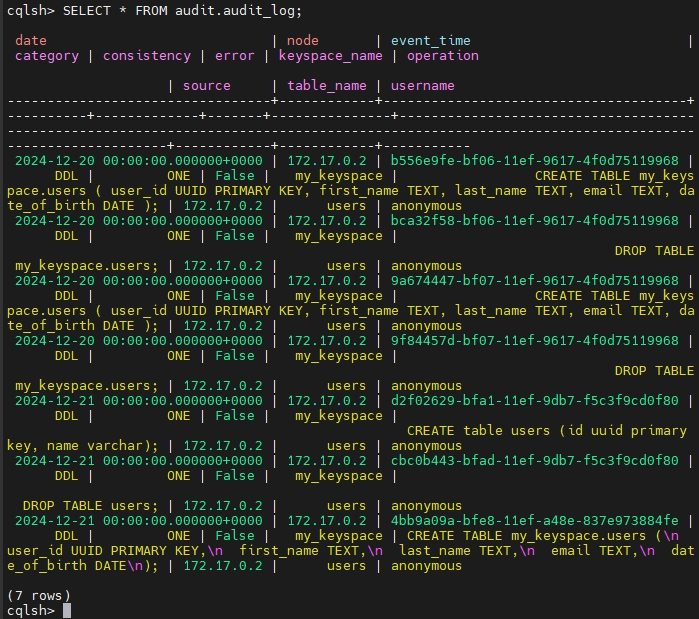
Audit Categories and Customization
ScyllaDB’s audit feature allows you to choose which database operations to log. The available audit categories include:
- DCL (Data Control Language): Logs commands related to database permissions and access control, such as
GRANTandREVOKE. - DDL (Data Definition Language): Tracks schema changes, such as
CREATE,ALTER, andDROPcommands. - AUTH (Authentication and Authorization): Logs events related to user authentication and authorization, such as login attempts and permission changes.
These categories can be customized based on your organization’s specific needs.
Audit Table Structure
Audit logs in ScyllaDB are stored in a dedicated table specified in the configuration file. The table typically includes columns for the event type, timestamp, user details, affected resource, and the operation performed. This structured logging facilitates easy querying and analysis of audit logs for detecting suspicious activity or compliance violations.
ScyllaDB + DataSunrise: Enhanced Security and Monitoring
While native solutions may suffice for basic auditing tasks, enterprises typically need more robust and scalable solutions. DataSunrise is an excellent option to extend ScyllaDB’s functionality. Specifically, DataSunrise can act as a database proxy, providing an additional layer of security to your ScyllaDB instance.
Thorough Database Activity Monitoring for ScyllaDB
DataSunrise offers advanced monitoring features for ScyllaDB, allowing organizations to track and analyze database activity in real-time. This includes monitoring read/write operations, user access logs, and system performance metrics. By integrating DataSunrise with ScyllaDB, organizations can gain deeper insights into their database operations, enabling them to identify and address issues more effectively.
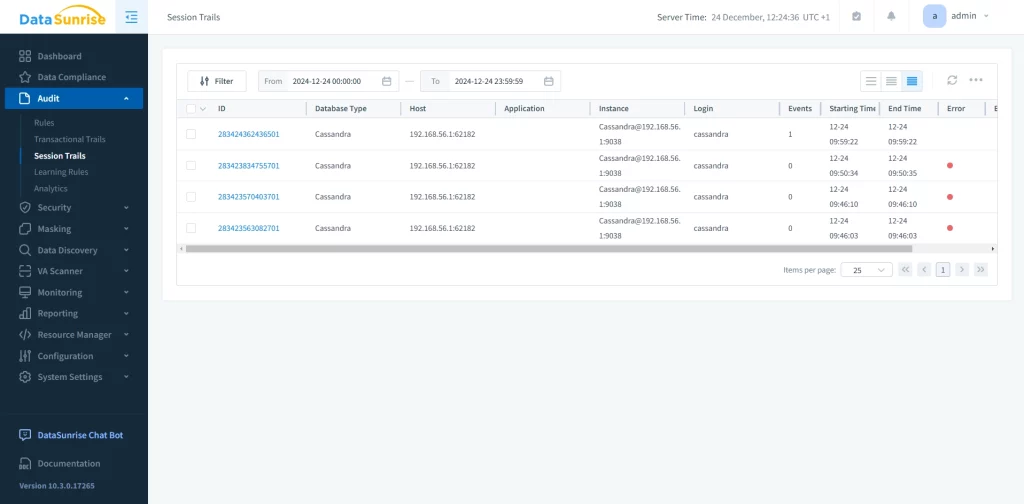
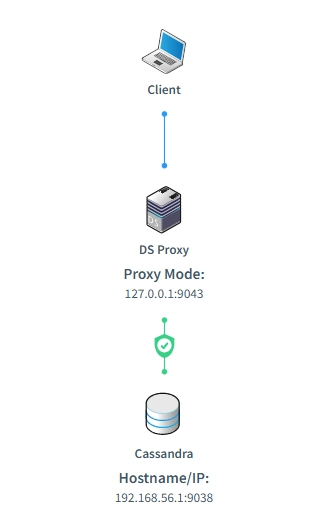
Enhanced Security with DataSunrise Database Proxy
DataSunrise offers advanced security features. As a database proxy, DataSunrise sits between your ScyllaDB instance and users or applications accessing it. This intermediary layer provides enhanced security controls, including encryption, IP filtering, and fine-grained access controls.
With the proxy in place, DataSunrise can monitor all access to ScyllaDB, ensuring that only authorized users interact with the database. It also records login sessions, allowing you to audit not only data operations but also user authentication events, login attempts, and session information.
We can block queries to the database with a query error. If we enable such a rule in DataSunrise, we’ll get a query is blocked error whenever we try to connect to the database because every major database client performs a bunch of queries right after establishing a connection to get the metadata about the database. Here’s the error message I’ve got after trying to connect with the rule enabled:
com.datastax.oss.driver.api.core.AllNodesFailedException: Could not reach any contact point, make sure you've provided valid addresses (showing first 1 nodes, use getAllErrors() for more): Node(endPoint=192.168.56.104/ :9042, hostId=null, hashCode=7a541097): [java.lang.IllegalArgumentException: [s1|control|id: 0x3973db9b, L:/192.168.56.1:54683 - R:/192.168.56.104:9042] Protocol initialization request, step 3 (QUERY (SELECT cluster_name FROM system.local)): server replied with unexpected error code [PROTOCOL_ERROR]: The query is blocked]
Key Features of DataSunrise Security Integration:
- Real-time Access Control: Define rules that limit access to ScyllaDB based on IP address, user roles, or authentication credentials.
- Session Logging: Track every login session to identify who accessed the database, when, and for how long.
- Audit of Login Events: Log both successful and failed login attempts to detect unauthorized access or brute-force attacks.
- Encryption: Secure all data passing through the DataSunrise proxy with encryption, ensuring safe communication between users and ScyllaDB.
DataSunrise’s database proxy functionality not only enhances monitoring but also improves overall security, making it an ideal choice for organizations seeking both advanced monitoring and robust security features.
Best Practices for Implementing Data Audit
- Define Clear Audit Objectives: Before setting up an audit system, clearly define your objectives. Are you auditing for compliance, security, or performance monitoring? This will guide your configuration and tool selection.
- Regularly Review Audit Logs: Schedule regular reviews of audit logs to identify anomalies, track user behavior, and ensure compliance with regulations.
- Automate Monitoring: Use tools like DataSunrise to automate monitoring and alerting, reducing the manual effort required to track database activity.
- Secure Audit Logs: Ensure that audit logs are stored securely and are accessible only to authorized personnel. Encrypt logs if necessary to prevent unauthorized access.
- Test and Validate: Regularly test your audit system to ensure it is functioning correctly and capturing all necessary data.
Conclusion
In the world of distributed databases, data audit plays a vital role in ensuring transparency, security, and compliance. While ScyllaDB provides basic audit functionality, third-party tools like DataSunrise can significantly enhance your monitoring and security capabilities. With advanced features like real-time event tracking, session logging, and a security proxy, DataSunrise offers a comprehensive solution for ScyllaDB users who need a robust and scalable monitoring system.
By following best practices and leveraging the right tools, organizations can maintain high levels of performance, security, and compliance, ensuring their data remains secure and their operations transparent. Whether you aim to improve security, monitor performance, or meet compliance standards, implementing a solid data audit system is crucial for maintaining control over your data environment.
