
Data Audit in SQL Server: Strengthening Security & Compliance with Advanced Monitoring

Understanding SQL Server Data Audit
SQL Server data audit is a crucial feature that helps organizations monitor and track database activities. It keeps track of what users do, changes to the system, and how data is accessed. This is important for keeping data safe, finding security issues, and following rules.
Many companies store sensitive information in their SQL Server databases, including customer details, financial records, and critical business data. SQL Server audit acts as a protective measure for these valuable assets. It serves as a vigilant monitor, alerting administrators to suspicious activities and providing a detailed trail of database interactions.
Microsoft SQL Server offers robust auditing capabilities that allow organizations to create comprehensive audit strategies tailored to their specific needs. You can use data audit to track specific columns, tables, or user actions with detailed audit policies.
For instance, you might implement data audit in SQL Server to track all attempts to view sensitive financial information. SQL Server’s audit feature consolidates audit records from various sources into a centralized location, simplifying the process of reviewing and analyzing audit data.
Additionally, solutions like DataSunrise extend SQL Server’s auditing capabilities. DataSunrise offers deep and customizable auditing across multiple database types, making it an invaluable tool for organizations with diverse IT infrastructures.
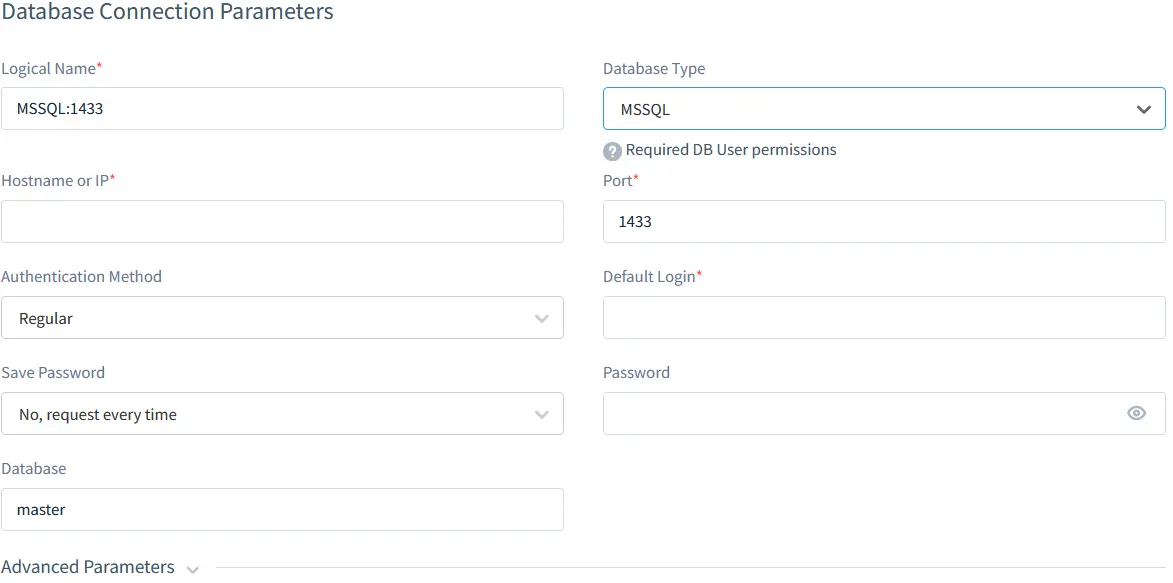
Creating a database server instance in DataSunrise
Enhancing SQL Server Data Audit with DataSunrise
While SQL Server offers built-in auditing features, tools like DataSunrise take database auditing to the next level. DataSunrise provides a comprehensive platform for database security and compliance, with robust features for real-time data auditing, masking, and protection. This makes it particularly valuable for organizations handling sensitive data.
DataSunrise’s data audit capabilities integrate seamlessly with SQL Server, allowing administrators to monitor database activities without impacting performance. Its advanced auditing tools offer detailed insights into user activities, such as who accessed sensitive data, what changes were made, and when specific actions occurred. For instance, you can use DataSunrise to track user access to critical financial tables and generate real-time alerts for suspicious activities.
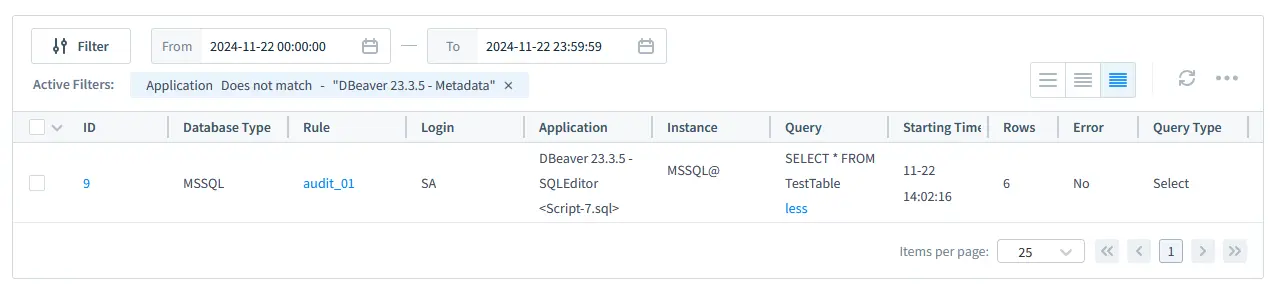
DataSunrise dashboard showing real-time audit logs for a SQL Server database.
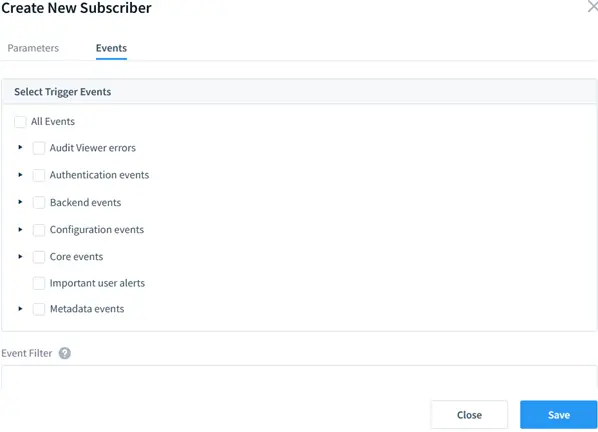
Create a new subscriber Datasunrise audit.
Implementing SQL Server Data Audit
Setting up an effective SQL Server data audit strategy involves several key steps. Begin by identifying what you need to audit, considering your industry regulations and specific security concerns. A healthcare provider checks who sees patient records, while a bank watches transactions and account changes.
Once you’ve determined your requirements, set up audit specifications in SQL Server. These specifications define what activities to monitor and under what conditions. You might create a specification to track failed login attempts or monitor changes to critical tables.
With DataSunrise, this process becomes even more efficient. It simplifies the creation of audit rules and provides pre-configured templates for common audit requirements, such as tracking failed logins or monitoring specific tables.
Regularly review your audit logs to identify potential issues. Many organizations use specialized tools to automate this process, sifting through large volumes of audit data and flagging suspicious activities for further investigation.
DataSunrise enhances this by offering customizable dashboards and detailed reports, making it easier to spot trends and anomalies in database usage patterns.
Implementing a robust SQL Server data audit strategy offers numerous benefits. It enhances security by helping you quickly detect and respond to potential threats. If you notice multiple unsuccessful login attempts from an unfamiliar IP address, you can promptly block the suspicious activity.
Data audit in SQL Server also supports compliance efforts by providing detailed records of database access and changes. You can easily generate reports showing who accessed what information and when, helping you identify potential insider threats.
Example: Setting Up SQL Server Data Audit with Native Tools
Let’s walk through a practical example of setting up data audit. We’ll create an audit that tracks all SELECT operations on a sensitive table.
First, create a server audit:
USE master; GO CREATE SERVER AUDIT DataAccessAudit TO FILE ( FILEPATH = 'C:\SQLAudit\', MAXSIZE = 100 MB, MAX_ROLLOVER_FILES = 5 ) WITH (QUEUE_DELAY = 1000, ON_FAILURE = CONTINUE) GO ALTER SERVER AUDIT DataAccessAudit WITH (STATE = ON) GO
This creates a server audit that writes to files in the C:\SQLAudit\ directory.
Next, create a database audit specification:
USE YourDatabaseName; GO CREATE DATABASE AUDIT SPECIFICATION SensitiveTableAudit FOR SERVER AUDIT DataAccessAudit ADD (SELECT ON dbo.SensitiveTable BY public) WITH (STATE = ON); GO
This specification audits all SELECT operations on the SensitiveTable.
To view the audit data, you can use the following query:
SELECT
event_time,
server_principal_name,
database_name,
object_name,
statement
FROM
sys.fn_get_audit_file ('C:\SQLAudit\*.sqlaudit', DEFAULT, DEFAULT);
This query retrieves audit data from the audit files, showing when each event occurred, who performed it, in which database, on which object, and what SQL statement was executed.
By implementing this audit, you’ll be able to track all attempts to view data in the SensitiveTable, helping you monitor data access and detect potential security breaches.
Challenges and Best Practices
While SQL Server data audit is invaluable, it does present some challenges. Extensive auditing can impact database performance. To mitigate this, consider a tiered approach. Start with basic security event auditing, then increase detail for high-risk activities or off-peak times for better security measures.
With tools like DataSunrise, organizations can significantly reduce performance bottlenecks. Its smart resource management ensures audits are conducted efficiently, even on high-traffic databases.
Auditing also generates substantial data, which can be challenging to store and analyze. Implement data retention policies to manage this issue. You can save detailed audit data for a period of time. After that, you can choose to either archive or summarize the older data for long-term storage.
DataSunrise simplifies this with built-in storage optimization options and automated archive features. You can set retention policies directly in the tool, ensuring compliance and efficient use of resources.
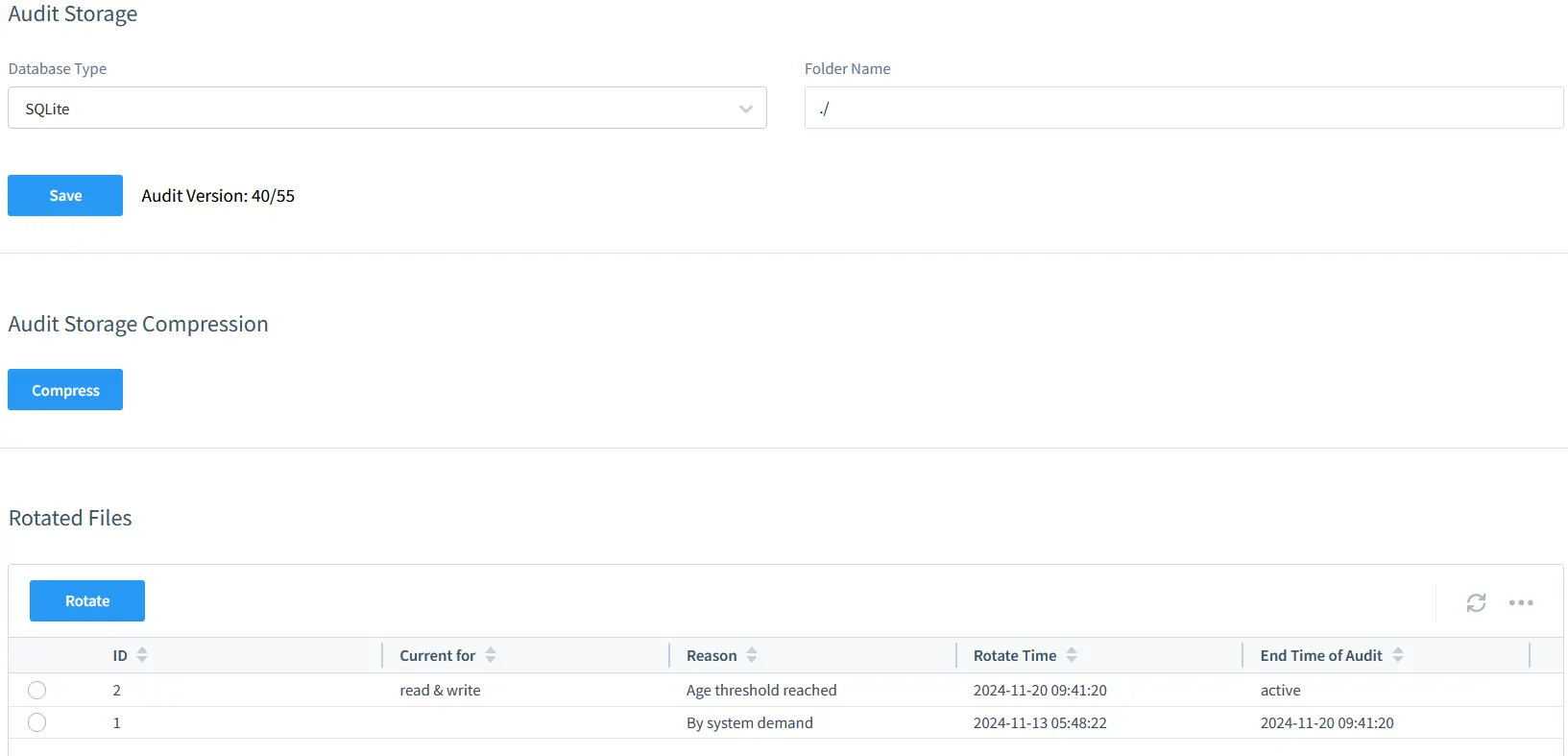
DataSunrise’s data storage optimization, highlighting archival settings and compression ratios.
To maximize the benefits of your SQL Server data audit strategy, consider these best practices. Review and adjust your audit specifications regularly as your organization evolves. Protect your audit logs from tampering by implementing strong access controls for audit data.
Set up automated alerts for critical audit events to allow for quick response to potential security incidents. You can create an alert to notify your security team if someone tries to change an important system table.
With DataSunrise, you can easily configure real-time alerts based on specific audit events, ensuring that your team is notified instantly about suspicious activities.
DataSunrise audit configuration screen, showing rule creation.
Educate your employees about data auditing and its importance. When people know they are being watched, they are more likely to follow security rules. This helps stop accidental data leaks and discourages intentional misuse.
Conclusion
SQL Server data audit is a powerful tool for protecting your valuable database assets. It enhances security, supports compliance efforts, and provides crucial insights into database usage patterns. While implementing an effective audit strategy requires effort, the benefits far outweigh the challenges.
By integrating SQL Server’s native features with advanced tools like DataSunrise, organizations can achieve a seamless and robust data auditing strategy. DataSunrise offers unparalleled flexibility, from intuitive dashboards to real-time monitoring and compliance reporting.
By leveraging SQL Server’s robust auditing features and following best practices, you can significantly strengthen your data security posture. Don’t forget, keeping track of SQL Server data is an ongoing process that needs regular attention and improvements to work well.
Regularly review and update your audit strategies to keep pace with evolving security threats and changing business needs. With diligent use of data audit in SQL Server, you can ensure the security and integrity of your critical data assets.
Discover how DataSunrise can enhance your database security. Visit DataSunrise.com for an online demo and see how we can strengthen your data protection strategy.
