
Data Audit in YugabyteDB

Introduction
In today’s data-driven landscape, implementing robust data audit mechanisms is essential for maintaining data integrity and meeting compliance mandates. YugabyteDB offers native capabilities for tracking data access patterns and modifications. Additionally, third-party solutions like DataSunrise enhance these features for enterprise needs.
With increasing regulatory focus on data protection (GDPR, HIPAA, CCPA) and rising security threats, organizations must implement granular audit trails that track who accessed what data and when. This guide explores both native and enhanced data auditing approaches for YugabyteDB environments.
Native Features for Data Audit in YugabyteDB
YugabyteDB, built on a PostgreSQL foundation, provides robust data auditing through the pgaudit extension. This extension enables comprehensive tracking of data modifications, schema changes, and permission updates. By leveraging pgaudit, organizations can generate detailed logs for compliance and forensic analysis.
1. Tracking Data Modifications
To capture all INSERT, UPDATE, and DELETE operations, enable DML auditing:
-- Enable DML auditing to track data modifications
SET pgaudit.log='DML';Example: Capturing Data Modifications
After enabling auditing, modifying a table generates an audit log.
Table: customer_data
| customer_id | name | balance | |
|---|---|---|---|
| 101 | Alice | alice@email.com | 1500.00 |
| 102 | Bob | bob@email.com | 2300.50 |
User performs an update operation:
UPDATE customer_data SET balance = balance - 500 WHERE customer_id = 101;Generated Audit Log Output:
| log_time | user_name | database | command | relation | statement |
|---|---|---|---|---|---|
| 2025-02-11 10:15 | admin | yugabyte | UPDATE | customer_data | UPDATE customer_data SET balance = balance – 500 WHERE customer_id = 101; |
2. Monitoring Schema Changes
To track table schema changes, enable DDL logging:
-- Enable DDL auditing to track structural modifications
SET pgaudit.log='DDL';Example: Capturing Schema Changes
A developer modifies the customer_data table by adding a
new column:
ALTER TABLE customer_data ADD COLUMN last_login TIMESTAMP;Generated Audit Log Output:
| log_time | user_name | database | command | relation | statement |
|---|---|---|---|---|---|
| 2025-02-11 11:00 | dev_user | yugabyte | ALTER | customer_data | ALTER TABLE customer_data ADD COLUMN last_login TIMESTAMP; |
3. Tracking Permission Changes
To track GRANT/REVOKE operations:
SET pgaudit.log='ROLE';Example: Tracking Permission Changes
An admin grants SELECT permission to a new analyst
role:
GRANT SELECT ON customer_data TO analyst;Generated Audit Log Output:
| log_time | user_name | database | command | relation | statement |
|---|---|---|---|---|---|
| 2025-02-11 12:30 | dba_admin | yugabyte | GRANT | customer_data | GRANT SELECT ON customer_data TO analyst; |
4. Enabling Comprehensive Audit Logging
To enable a full audit trail for DML, DDL, and permission
changes, configure pgaudit globally:
CREATE EXTENSION IF NOT EXISTS pgaudit;
ALTER DATABASE yugabyte SET pgaudit.log='WRITE, DDL, ROLE';This ensures that all critical operations—data modifications, schema alterations, and user permission changes—are logged for compliance and security purposes.
Enhanced Data Audit with DataSunrise
DataSunrise extends YugabyteDB’s native capabilities with purpose-built data audit features. These enhancements focus on three critical aspects:
1. Sensitive Data Access Tracking
- Column-level auditing for PII/PHI fields
- Data retrieval pattern analysis
- Dynamic data masking integration
2. Data Change Auditing
- Before/after value comparisons
- Transaction rollback analysis
- Bulk data modification tracking
3. Compliance-Centric Reporting
- Pre-built reports for PCI DSS Requirement 10
- Data access timelines for GDPR Right to Erasure
- Audit log integrity protection with cryptographic hashing
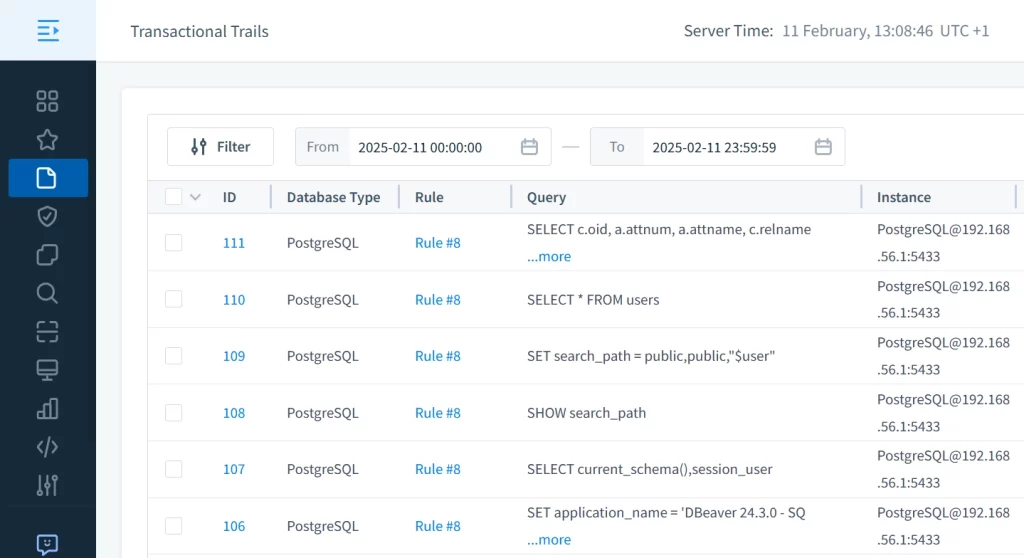
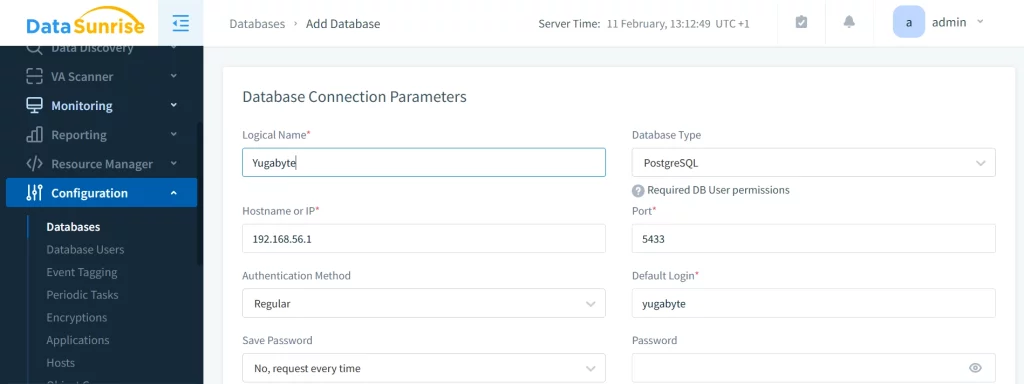
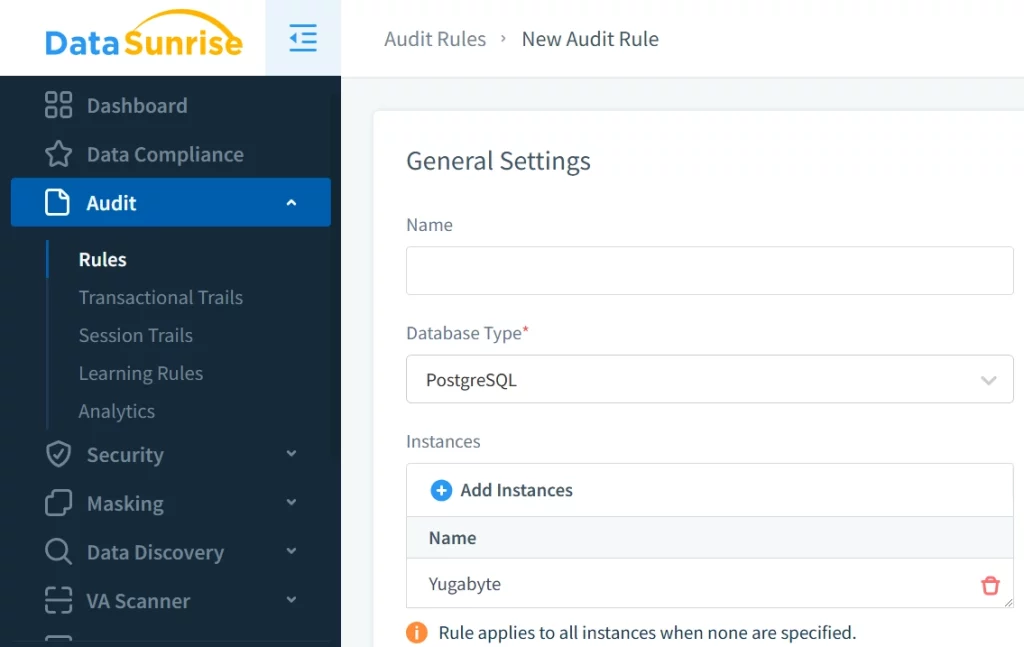
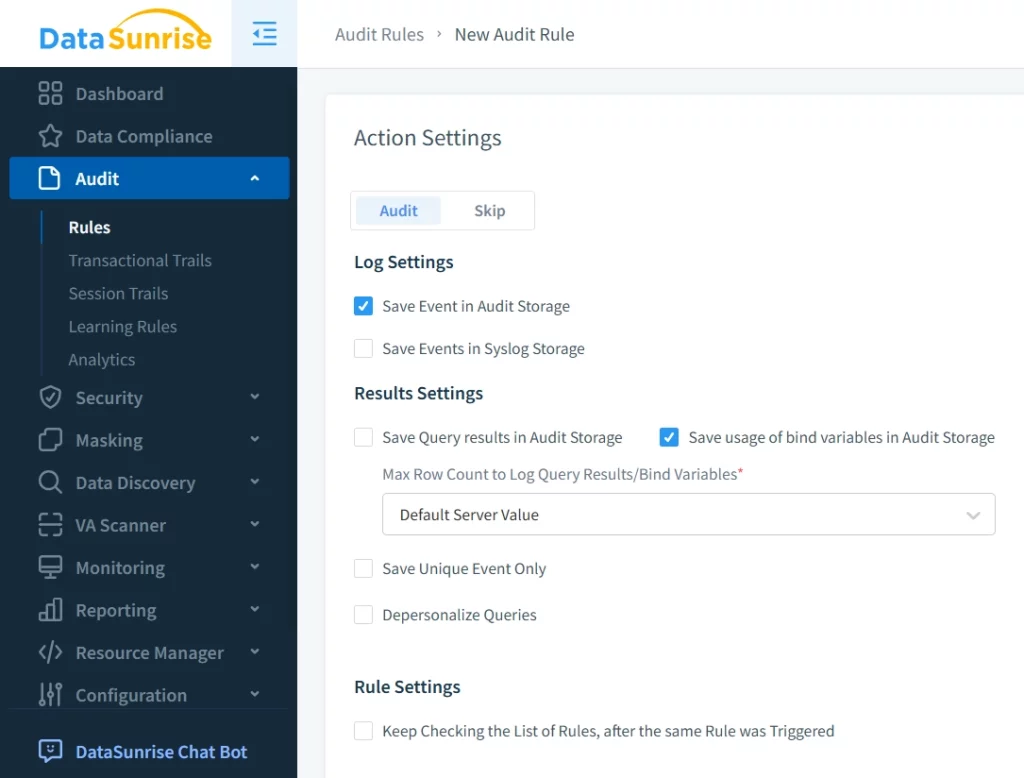
Implementation Workflow:
- Add your YuabyteDB instance to DataSunrise:
- Then create audit rule to see real-time audit logs:
- Finally, establish advanced action settings to fine-tune real-time aleritng:
Best Practices
1. Data-Centric Audit Configuration
- Map audit rules to sensitive data classifications
- Enable parameter logging for financial transactions
- Implement dual control for audit policy changes
2. Security & Integrity Measures
- Encrypt audit logs containing sensitive field access
- Implement HMAC validation for log files
- Restrict audit log access to security personnel
3. Performance Optimization
- Use sampling rates for high-volume data tables
- Separate audit storage from operational databases
- Compress historical audit data
4. Compliance Alignment
- Maintain 90-day rolling audit logs for PCI DSS
- Implement immutable audit storage for legal requirements
- Regularly validate audit completeness through penetration tests
Conclusion
Implementing an effective data audit strategy in YugabyteDB requires careful consideration of both native capabilities and enhanced solutions. While YugabyteDB’s built-in audit features provide essential tracking capabilities through pgaudit, organizations with complex compliance requirements may benefit from advanced solutions like DataSunrise.
The key to successful audit implementation lies in balancing comprehensive monitoring with system performance, while ensuring all regulatory requirements are met. Whether using native tools or enhanced solutions, organizations should focus on creating a robust audit framework that captures critical data interactions without compromising system efficiency.
Whether using YugabyteDB’s native capabilities or augmenting with DataSunrise’s solution, a well-structured data audit strategy should focus on tracking critical data interactions while maintaining system performance. The choice between native and enhanced solutions depends on the organization’s data sensitivity, compliance requirements, and resource constraints.
If you want to learn more about comprehensive data audit in YugabyteDB with DataSunrise, we highly recommend scheduling our online demo or downloading the tool to explore it yourself.
