
Data Breach: An Important Threat To Consider

Introduction
Data breaches have become an all too common occurrence in today’s digital world. Hardly a week goes by without news of another major security breach exposing sensitive customer data. Data breaches can cause serious harm to people and businesses. They can lead to the exposure of sensitive information like credit card numbers, medical records, and corporate secrets.
This article will discuss data breaches. Data breaches involve the leaking of information. We will address the costs of data breaches. We will also discuss common reasons for data breaches.
By knowing these basics, you can safeguard your data and know what to do if there is a security breach.
What Is a Data Breach?
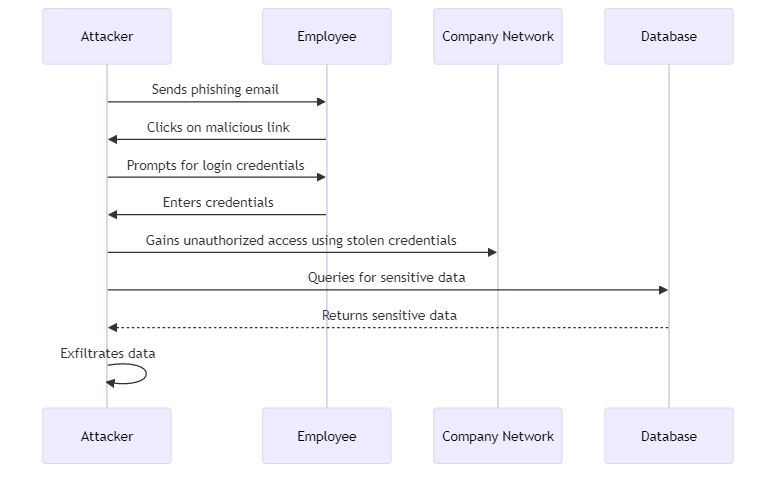
A data breach occurs when unauthorized individuals view, take, or use important information. Data leaks can occur when hackers gain access to an organization’s databases, systems, or networks. Breaches can also happen because of insider threats from employees, whether accidental or malicious.
The exposed data often includes information that identity thieves or financial fraudsters can use, such as:
- Names and addresses
- Social security numbers
- Credit card or bank account details
- Usernames and passwords
- Protected health information
Data breaches are extremely costly for affected organizations. According to IBM’s Cost of a Data Breach Report, the average total cost of a breach in 2022 was $4.35 million. Breaches also erode customer trust and can result in regulatory fines and legal action.
Data Breach : Types of Information Leaked
The specific data exposed in a breach depends on what information the affected organization collects and stores. However, some of the most common types of sensitive information leaked in data breaches include:
- Personal Identifiable Information (PII): This information can help identify a person. It includes their name, address, birthdate, social security number, driver’s license number, and passport number.
- Financial data: Credit card numbers, bank account details, and other financial information are frequent targets for hackers. This data enables them to make fraudulent purchases or withdraw money from accounts.
- Login credentials: Usernames and passwords for email, banking, shopping, and other online accounts are highly valuable to attackers. With this information, criminals can access accounts, make unauthorized changes, or steal additional data.
- Protected Health Information (PHI): Laws like HIPAA require keeping health information, such as medical records and insurance claims, safe. However, data breaches frequently expose it. Individuals can use PHI for medical identity theft and insurance fraud.
- Hackers may try to steal important business information like product designs, source code, or strategic plans. Competitors can buy this information or use it for corporate espionage.
In 2017, hackers got into Equifax’s system and stole personal information from 147 million people. This included names, social security numbers, birth dates, addresses, and driver’s license numbers. The breach cost Equifax over $575 million in fines and settlements.
The High Costs of Data Breaches
Security breaches are incredibly expensive for victim organizations. Costs typically include:
- Investigating and fixing the security holes that allowed the breach
- Setting up credit monitoring and identity theft protection for affected customers
- Compensating customers for any fraudulent charges or money stolen
- Paying regulatory fines for violating data protection laws
- Facing lawsuits and legal fees
- Losing business because of reputational damage
Security breaches damage customer trust, causing many clients to take their business elsewhere when a breach occurs.
In 2013, Target had a data breach that affected 40 million customers’ debit and credit card information. The breach ended up costing Target over $300 million when factoring in legal fees, lawsuit settlements, and lost sales. The company’s profit dropped by more than 40% in the quarter following the announcement of the breach.
Causes of Information Leakage
What precisely causes data breaches to occur? Attackers can get into sensitive information in many ways, but common causes include unauthorized access.
- Phishing and social engineering: Hackers can trick employees by pretending to be a legitimate business or IT support person. They do this through email or phone to obtain login information or other sensitive data. Phishing is one of the top causes of breaches.
- Malware: Attackers can infect an organization’s systems with malicious software designed to steal data. Malware typically spreads via email attachments, software downloads, or infected websites.
- Unpatched software flaws: Hackers take advantage of weaknesses in software that organizations don’t update or fix. A known flaw in a web application framework breached Equifax, for example.
- Misconfigured databases and cloud storage: If databases or cloud storage aren’t secure, anyone can access the data easily using a web browser. Misconfigurations have led to the exposure of hundreds of millions of records.
- Insider threats: Inside attackers cause some leaks, not all outside attackers cause them. Employees or contractors may intentionally steal data for personal gain or accidentally expose it because of careless security practices. A recent example is a Twitter employee caught selling user data on the dark web.
To illustrate, in 2020, the Marriott hotel chain suffered a data breach via social engineering. Hackers tricked two employees at a franchise location into giving them their login information. This allowed the hackers to access the personal information of 5.2 million guests. The leaked data included names, addresses, phone numbers, loyalty account info, and more.
Minimizing the Risk of a Data Breach
Every organization faces the risk of data breaches. However, companies can take steps to reduce this risk and minimize the impact of any breaches.
- Implement strong access controls and least privilege principles to ensure only authorized employees can view sensitive data
- Encrypt data both in transit and at rest
- Keep all systems and software up-to-date and patched against known vulnerabilities
- Provide thorough security awareness training for employees to recognize threats like phishing
- Use tools to monitor systems and databases for suspicious activity
- Have an incident response plan to quickly investigate and remediate if a breach occurs
One company that provides comprehensive solutions for data and database security is DataSunrise. Their tools assist companies in finding, monitoring, and protecting valuable information. They also ensure compliance with regulations like GDPR and HIPAA.
In addition, they enable quick responses to potential security breaches. Key capabilities include database activity monitoring, data masking, OCR scanning, and sensitive data discovery.
The team at DataSunrise makes it easier to begin using their intuitive, adaptable security and compliance instruments. Visit site to schedule a demo and see how they can keep your organization’s data safe from breaches.
Summary and Conclusion
Data breaches pose a massive risk to organizations of all sizes and industries. Companies can avoid data leaks and security breaches by knowing what they are, their costs, and how they occur. This includes implementing strong access controls, encrypting sensitive data, updating systems against vulnerabilities, training employees, and leveraging data security solutions from experts like DataSunrise.
Data breaches are a growing threat. Organizations that focus on security and have a response plan will protect their data and keep customer trust. Avoid waiting for a security breach to happen before you act. Invest in data protection today to secure your most valuable assets.
