
Data Masking for Apache Impala

Introduction
Data masking for Impala is crucial when it comes to protecting sensitive data stored in Apache Impala, as many organizations do for real-time, distributed SQL queries. Impala processes structured data that often includes sensitive information, such as personally identifiable information (PII) and financial records. Implementing data masking in Impala enhances security, ensures compliance, and mitigates unauthorized access risks.
What is Data Masking?
Data masking protects sensitive information by replacing original values with obfuscated data, allowing organizations to maintain data usability for analytics and development while safeguarding confidentiality.
Common Data Masking Types:
- Static Data Masking: Alters data at rest in the database.
- Dynamic Data Masking: Masks data in real-time during query execution.
- In-Place Data Masking: Applies masking directly without moving or copying data.
Complementary Security Measures:
- Tokenization: Replaces sensitive data with tokens while preserving referential integrity.
- Encryption: Converts data into unreadable formats, reversible with decryption keys.
Implementing Data Masking for Apache Impala with Native Capabilities
Sample Table
Before diving into different masking techniques, let’s create a sample table to work with:
CREATE TABLE users (
id INT,
ssn STRING,
name STRING
);
INSERT INTO users VALUES (1, '123-45-6789', 'Alice'), (2, '987-65-4321', 'Bob');
Now, let's explore different masking strategies.
1. View-Based Data Masking for Apache Impala
One simple way to implement masking in Impala is through views, which restrict direct table access and enforce predefined transformations.
Example: Masking Social Security Numbers (SSNs)
CREATE VIEW masked_users AS
SELECT
id,
CONCAT('XXX-', RIGHT(ssn, 4)) AS masked_ssn,
name
FROM users;
SELECT * FROM masked_users;
Expected Output:
| id | masked_ssn | name |
|---|---|---|
| 1 | XXX-9012 | Charlie |
| 2 | XXX-1098 | Diana |
Views provide an easy way to hide sensitive information while keeping data readable for analytics.
2. Data Masking for Apache Impala via ETL Jobs
For organizations requiring pre-masked data before storage, ETL (Extract, Transform, Load) jobs can process and mask sensitive data before inserting it into tables.
Here's the output when running the INSERT INTO statement on the users table based on the data from the raw_users table:
Input Data from raw_users table:
| id | ssn | name |
|---|---|---|
| 1 | 123-45-9012 | Charlie |
| 2 | 987-65-1098 | Diana |
Output Data in users table:
| id | masked_ssn | name |
|---|---|---|
| 1 | XXX-9012 | Charlie |
| 2 | XXX-1098 | Diana |
The ssn values have been masked to only show the last four digits, prefixed with XXX-.
While this approach improves security, it also removes flexibility, making it harder to recover original data without a separate unmasked dataset.
3. Masking with User-Defined Functions (UDFs)
Impala does not have built-in masking UDFs like Hive does. Based on the documentation, Impala supports writing custom UDFs in C++ and Java for data transformation, but does not include pre-built masking functions. You would need to write your own UDFs to implement masking functionality, similar to what Hive provides with its built-in masking functions.
If you need masking capabilities, you could:
- Write custom C++ UDFs to implement the masking logic you need
- Use existing Hive Java UDFs for masking by importing them into Impala
- Handle masking at the application layer before loading data into Impala
Let’s assume that you’ve written a custom UDF in Impala using C++ or Java to mask Social Security Numbers (SSNs) in the ssn column. We will call this custom UDF mask_ssn for simplicity.
Here's an example of how you might query this UDF and the expected output:
Query Example with Custom UDF:
SELECT id, mask_ssn(ssn) AS masked_ssn, name
FROM users;
Expected Output:
| id | masked_ssn | name |
|---|---|---|
| 1 | XXX-9012 | Charlie |
| 2 | XXX-1098 | Diana |
Explanation:
- The
mask_ssnUDF would transform the SSNs by replacing the first five characters withXXX-, leaving the last four digits visible. - The expected result is similar to the effect of using
CONCAT('XXX-', RIGHT(ssn, 4)), but using a custom UDF allows more flexibility if you want to implement more complex masking logic.
Advanced Data Masking for Impala with DataSunrise
DataSunrise offers dynamic and static masking without modifying original data. It ensures:
- Role-based data masking.
- Seamless integration with Impala.
- Minimal performance impact.
Steps to Implement:
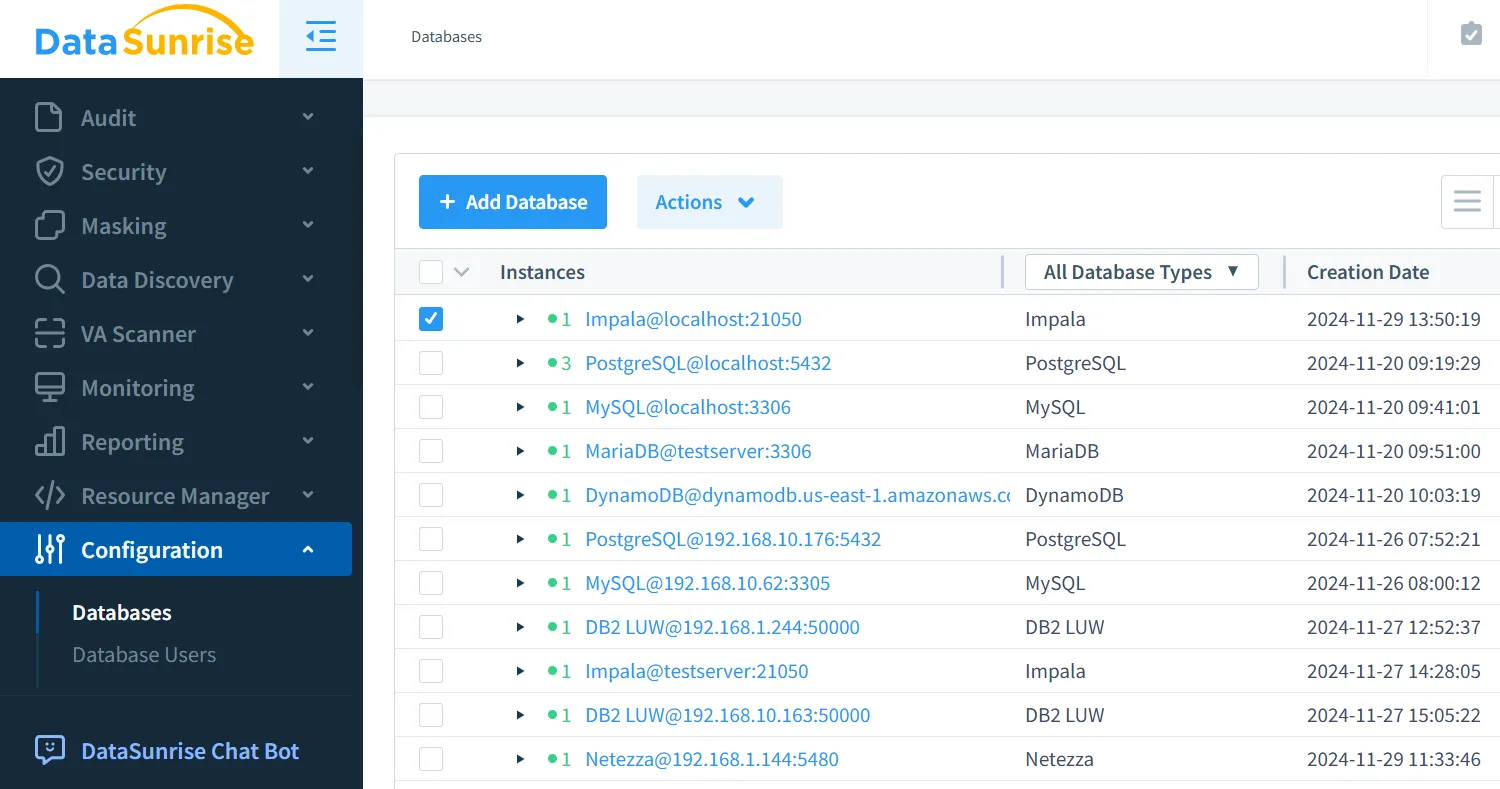
- Connect your Impala instance to DataSunrise.
- Define masking rules via the DataSunrise interface.
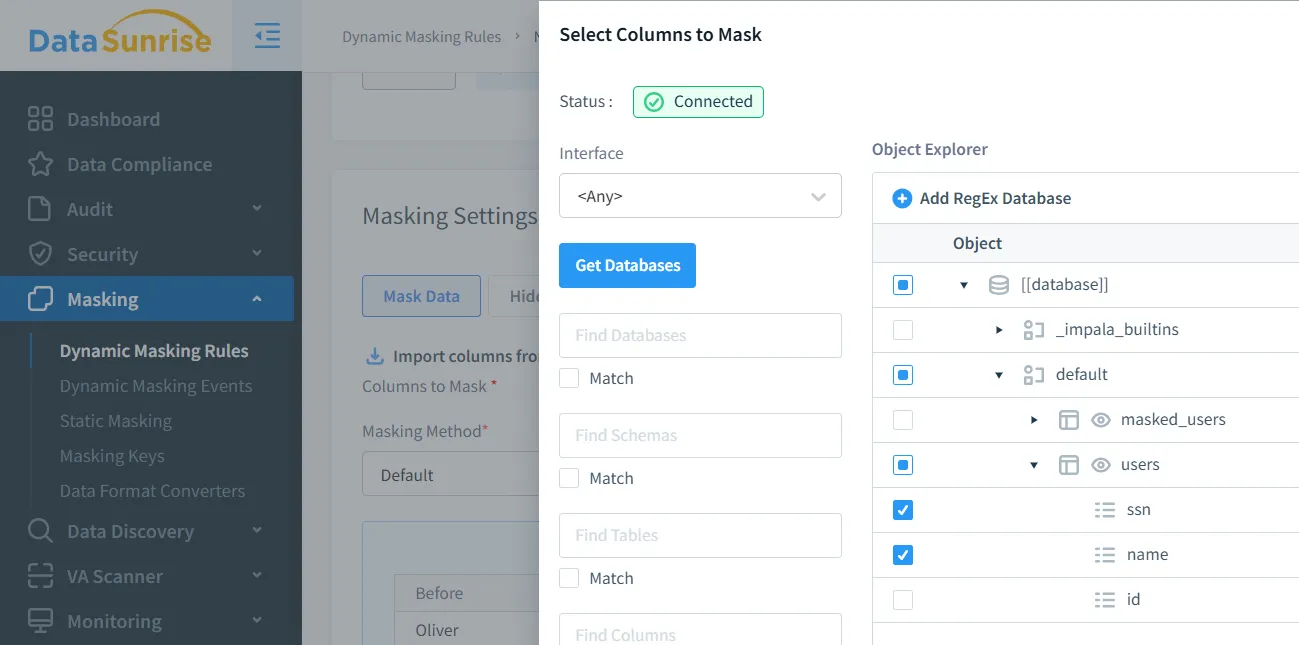
- Validate data masking by executing test queries.

Conclusion
Data masking is crucial for protecting sensitive data in Impala and ensuring regulatory compliance. While views and UDFs offer basic solutions, ETL masking provides a more permanent approach. DataSunrise enhances security further by offering flexible, scalable, and minimal-impact data masking solutions.
Schedule a DataSunrise demo to explore advanced data security for your Impala environment.
