
Data Masking for IBM DB2

Data masking for IBM DB2 plays an essential role in modern database security. IBM’s 2024 Cost of a Data Breach Report shows that companies using data masking solutions saved an average of $390,000.
We compare this to companies that did not use this protection. Organizations using security AI and automation realized additional cost savings, averaging $1.76 million less in breach-related expenses. These findings show why data masking is important for IBM DB2 environments. It is a key part of good database security.
IBM DB2 databases typically contain sensitive information including customer data, financial records, and business intelligence. Implementing comprehensive data masking strategies helps organizations meet compliance requirements while maintaining data security throughout their operations.
What is Data Masking and Why Is It Important?
Data masking means replacing sensitive information with fake but realistic data. This keeps real data safe from unauthorized users. It is very useful in testing, development, and analytics. These areas need access to production data, but privacy must be kept. By masking data, organizations can comply with regulations like GDPR, HIPAA, and PCI-DSS while still allowing users to work with data without revealing sensitive details.
In the case of IBM DB2, data masking can be done using built-in SQL features, allowing users to protect sensitive fields in a secure and efficient manner.
IBM DB2 Native Data Masking Capabilities
IBM DB2 provides several ways to mask data natively. This includes using SQL language features, views, and stored procedures. IBM DB2 does not have a direct data masking feature like some other database platforms. However, it does support several ways to achieve data masking.
Using Views for Data Masking in IBM DB2
One common approach to masking data in IBM DB2 is by creating views. A view is like a virtual table. It shows masked data to users. This happens without changing the real data in the database. By defining a view that masks sensitive fields, you ensure that users querying the view only see the masked data.
Example of Creating a Masked View
Let’s consider the following test data table:
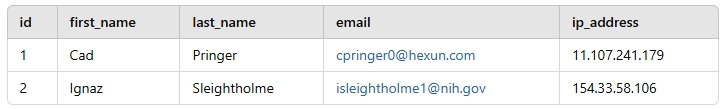
To mask the email and IP address fields, you can create a view like this:
CREATE VIEW masked_customer_data AS
SELECT
id,
first_name,
last_name,
CONCAT('xxx@xxx.com') AS email,
'xxx.xxx.xxx.xxx' AS ip_address
FROM customer_data;In this example:
- The email field is replaced with a generic masked email address.
- The ip_address field is replaced with a generic masked IP address.
Now, any user who looks at the masked_customer_data view will see only the masked data. The real sensitive data stays in the underlying table.
Using IBM DB2 Web Console for Data Masking
IBM DB2 offers a web-based user interface for interacting with the database. You can use these tools to execute SQL queries or run stored procedures that handle data masking. To mask data using the web console:
- Log into the IBM DB2 web console.
- Navigate to the SQL editor or stored procedure execution section.
- Run the necessary masking SQL commands or stored procedures.
This interface helps you work with your DB2 instance. You can perform data masking tasks without just using command-line tools.
DataSunrise: A Powerful Data Masking Solution for IBM DB2
While IBM DB2’s native capabilities provide a solid foundation for data masking, advanced solutions like DataSunrise can significantly enhance this process. DataSunrise is a comprehensive database security suite that includes powerful features for data masking, encryption, auditing, and compliance management.
Benefits of Using DataSunrise for IBM DB2
- Centralized Control: DataSunrise helps you manage and apply the same data masking rules across your IBM DB2 system. This reduces human error and ensures consistent protection for sensitive data.
- Real-Time Masking: Unlike static masking methods like views or stored procedures, DataSunrise can mask data in real-time. This offers more flexibility and security.
- Compliance: DataSunrise has built-in auditing and compliance features. These help you meet important rules like GDPR, HIPAA, and PCI-DSS. They also keep sensitive information safe.
- Enhanced Security: DataSunrise can mask data without altering the underlying database schema, ensuring that your applications continue to function without disruption.
How to Mask Data with DataSunrise for IBM DB2
To get started with DataSunrise, first install the tool in your environment. Once DataSunrise is running, you can set it up to apply data masking rules. You can do this in the DataSunrise management interface for your IBM DB2 database.
Steps for Data Masking with DataSunrise:- Create a DataSunrise Instance: This can be done via the web-based UI provided by DataSunrise. Connect to your IBM DB2 database by entering the required details. You need to provide the hostname, database name, username, and password.
- Define Masking Rules: DataSunrise offers an intuitive interface for defining masking rules. You can specify which columns in your IBM DB2 tables you want to mask and how you want the masking to occur.
- View Masked Data: Once the masking rules are applied, you can query the data as usual. The sensitive fields will appear in their masked form, while the original data remains unchanged in the database.
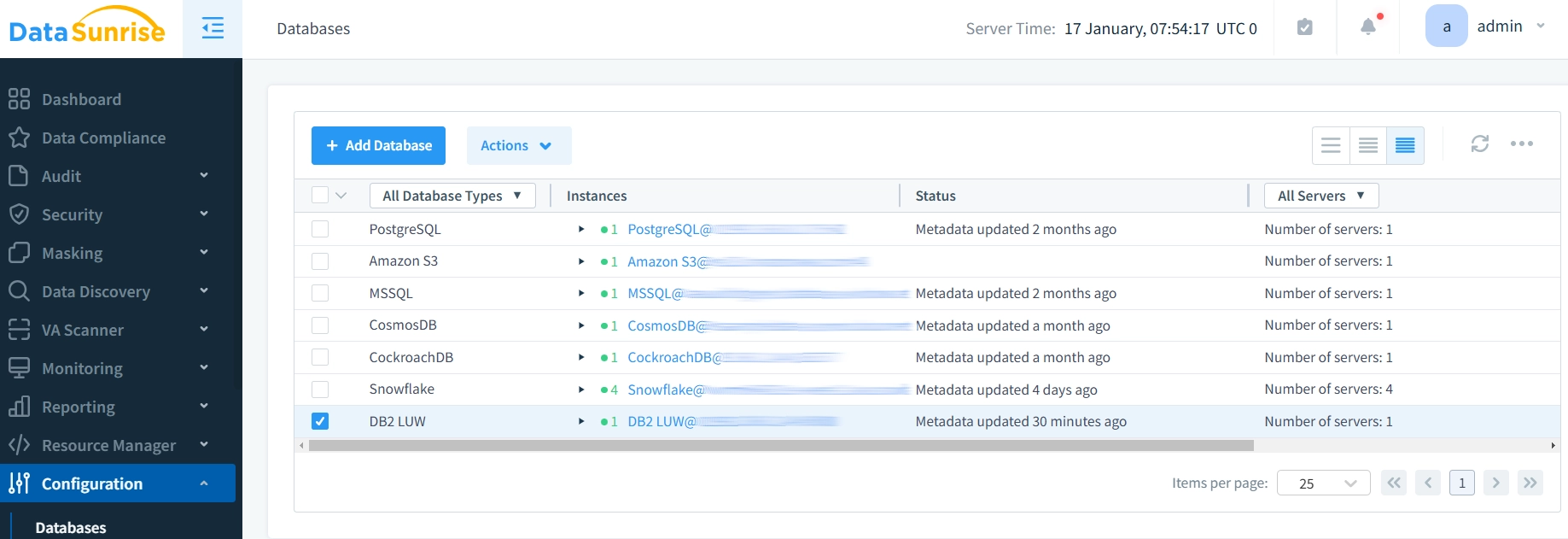
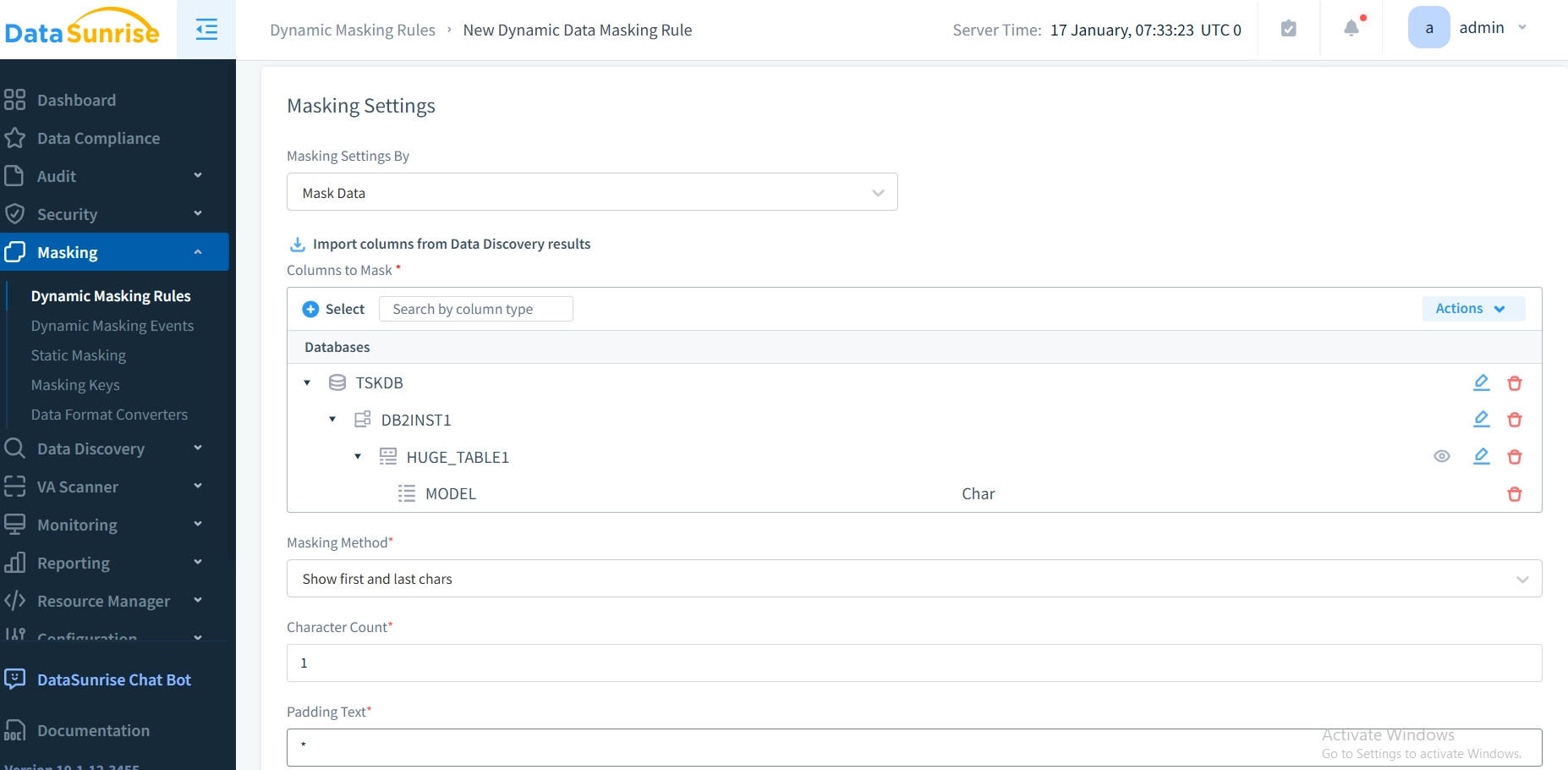
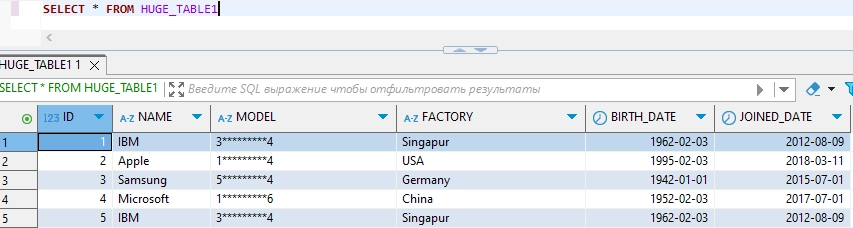
With DataSunrise, organizations benefit from a centralized approach to data security, making it easier to maintain consistent, compliance-ready data masking policies.
Essential Guidelines for DB2 Data Protection
Testing and Validation: Regular testing forms the foundation of any masking strategy. Implement systematic validation processes to ensure masking rules consistently protect sensitive data while maintaining data usability. This includes comprehensive testing across different user roles and access scenarios to verify that masking policies work as intended.
Security Monitoring: Establish comprehensive audit trails to track all interactions with masked data. Monitor changes to masking policies and masked data access to maintain compliance and quickly identify potential security issues. Integrate this monitoring with existing security infrastructure to provide a complete view of data protection efforts.
Third-Party Integration: Leverage solutions like DataSunrise to complement DB2’s native capabilities. These specialized tools provide advanced features such as sophisticated masking algorithms, streamlined policy management, and enhanced monitoring capabilities that extend beyond built-in options. The combination creates a robust security framework that adapts to evolving data protection needs.
Access Control: Implement detailed role-based access control alongside masking rules. Ensure that data exposure aligns with user responsibilities and department needs. Conduct regular reviews of these policies to maintain their effectiveness and relevance as business requirements evolve.
Backup Management: Develop comprehensive backup strategies specifically for masked data environments. Maintain secure backups of both masked and unmasked data, with clear procedures for data recovery that preserve security integrity. Establish separate backup policies for different data sensitivity levels while ensuring that backup processes themselves don’t introduce new vulnerabilities.
Conclusion
Data masking for IBM DB2 uses built-in database features and third-party tools like DataSunrise. This creates a strong security plan. DB2 provides basic protection with SQL views and stored procedures. Its web console makes it easy to set up and manage masking.
DataSunrise extends these capabilities by providing advanced masking features and centralized control across database environments. The effectiveness of data masking relies on both proper initial setup and consistent maintenance, including regular testing and monitoring of security measures.
For organizations looking to enhance their DB2 data security, DataSunrise offers database security tools including advanced masking capabilities and compliance features. Visit the DataSunrise website and schedule an online demo to learn more about our DB2 security solutions.
