
Data Masking in MySQL

Introduction
Data security is a growing concern for many organizations. MySQL, a popular database management system, offers ways to protect sensitive information.
Data masking is one effective method to secure data. By hiding or transforming data, it ensures unauthorized users cannot view sensitive details. This article covers the basics of data masking, how to implement it in MySQL using native tools and plug-ins, and how DataSunrise offers an efficient solution.
What is Data Masking?
Data masking involves altering data to make it unreadable to unauthorized users. The original data remains in the database, but the masked version is what others see. This process helps protect sensitive information such as credit card numbers, social security numbers, and email addresses.
Experts divide data masking into static and dynamic masking.
Static data masking permanently alters sensitive data in a copy of the original database. Users then utilize the masked copy for non-production purposes like testing, training, or development. In this case, someone changes and saves the data, making it impossible to reverse or restore the original values in the masked copy.
Dynamic data masking alters data in real-time as users access it, without changing the original data stored in the database. The actual data remains untouched, and only authorized users can see the unmasked data. Unauthorized users see a masked version when querying the database.
Data masking prevents data breaches and ensures compliance with privacy regulations like GDPR or HIPAA. Organizations handling sensitive data during testing, training, or development must do so without risking exposure.
How to Create Data Masking in MySQL
Native Methods
MySQL provides some built-in functions to create data masking. These methods aren’t as sophisticated as dedicated tools but offer a starting point.
- Using MySQL Functions
MySQL string functions are useful for masking data. For example, masking an email address:
SELECT CONCAT(SUBSTRING(email, 1, 3), '*****', SUBSTRING(email, INSTR(email, '@'))) AS masked_email FROM users;
This query will display an email like “joh*****@domain.com,” hiding part of the email address.
- Using Views
Create views to mask data, allowing access only to the masked version. For instance:
CREATE VIEW masked_users AS SELECT id, CONCAT(SUBSTRING(email, 1, 3), '*****@domain.com') AS email FROM users;
This view provides a masked version of email addresses, while the actual data remains unchanged in the table.
Limitations of Native Data Masking
Native MySQL functions are basic and not intended for complex data masking. They offer minimal security and require manual setup for each column. This method might not be suitable for large databases or advanced masking requirements.
Achieving Data Masking in MySQL with Plug-ins
MySQL plug-ins offer more advanced data masking features. Some popular plug-ins include:
– ProxySQL: This proxy solution allows query rewriting, including data masking.
– MySQL Enterprise Data Masking and De-Identification: This enterprise-level tool provides various masking methods such as randomization, substitution, and encryption.
Example Using MySQL Enterprise Data Masking
With MySQL Enterprise Edition, you can apply more sophisticated data masking:
SELECT id, MASKING_FUNCTION('1234-5678-9101-1121', 'XXXX-XXXX-XXXX-1121') AS masked_card_number
FROM customers;This approach offers better flexibility and control over how the data is masked.
Data Masking in MySQL Using DataSunrise
DataSunrise is a comprehensive solution that enhances data masking capabilities in MySQL. An ideal choice for businesses seeking robust data security without the complexities of manual masking methods exists.
DataSunrise offers both dynamic and static data masking.
Setting Up Data Masking in MySQL with DataSunrise
DataSunrise integrates seamlessly with MySQL databases. Once connected, you can define masking rules through a user-friendly interface. These rules specify which data to mask and how to display it to different users. You don’t need extensive SQL knowledge to set it up, making it a user-friendly option.
Static Masking Rule
A static masking rule in DataSunrise requires setting up transferred tables and selecting the target database.
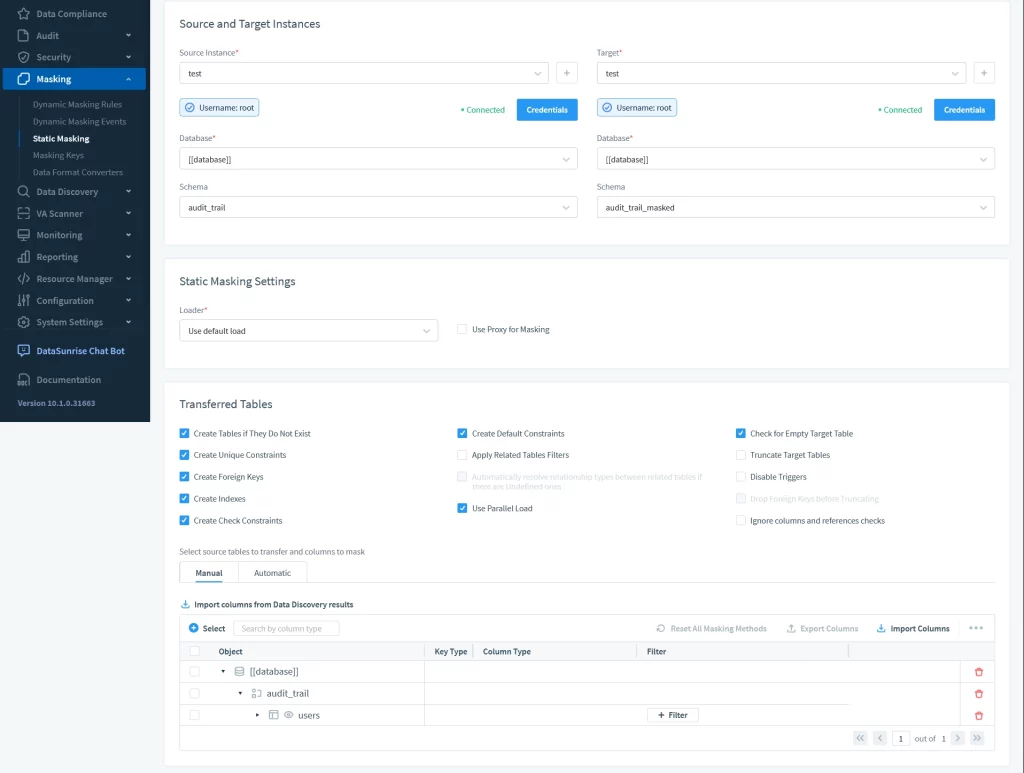
Data can be altered in-place or in the dedicated schema.
Dynamic Masking Rule
In the following example, the system will replace all the values in the password column with the ‘masked’ string.
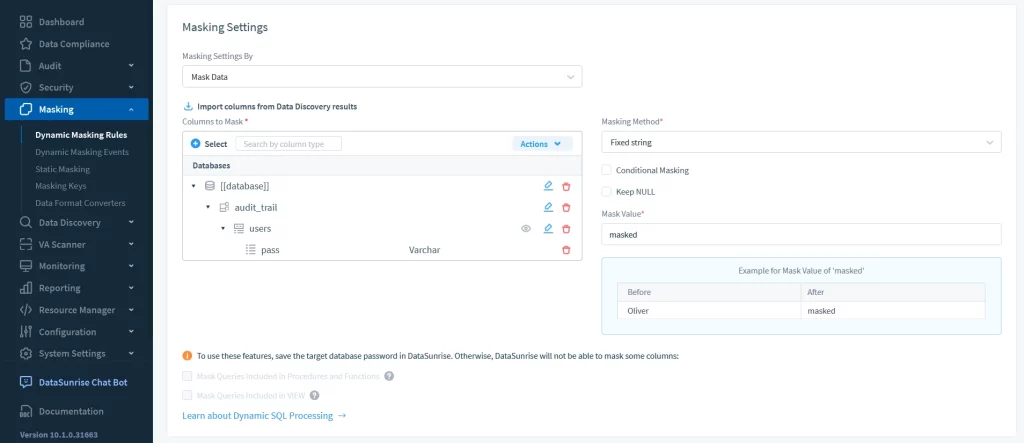
How Does MySQL Data Masking Look in DataSunrise?
DataSunrise’s intuitive dashboard makes managing masked data easy. You can monitor which data you mask, review user access, and adjust rules as needed. The platform provides real-time feedback on how masked data appears to different users, ensuring that your settings are effective.
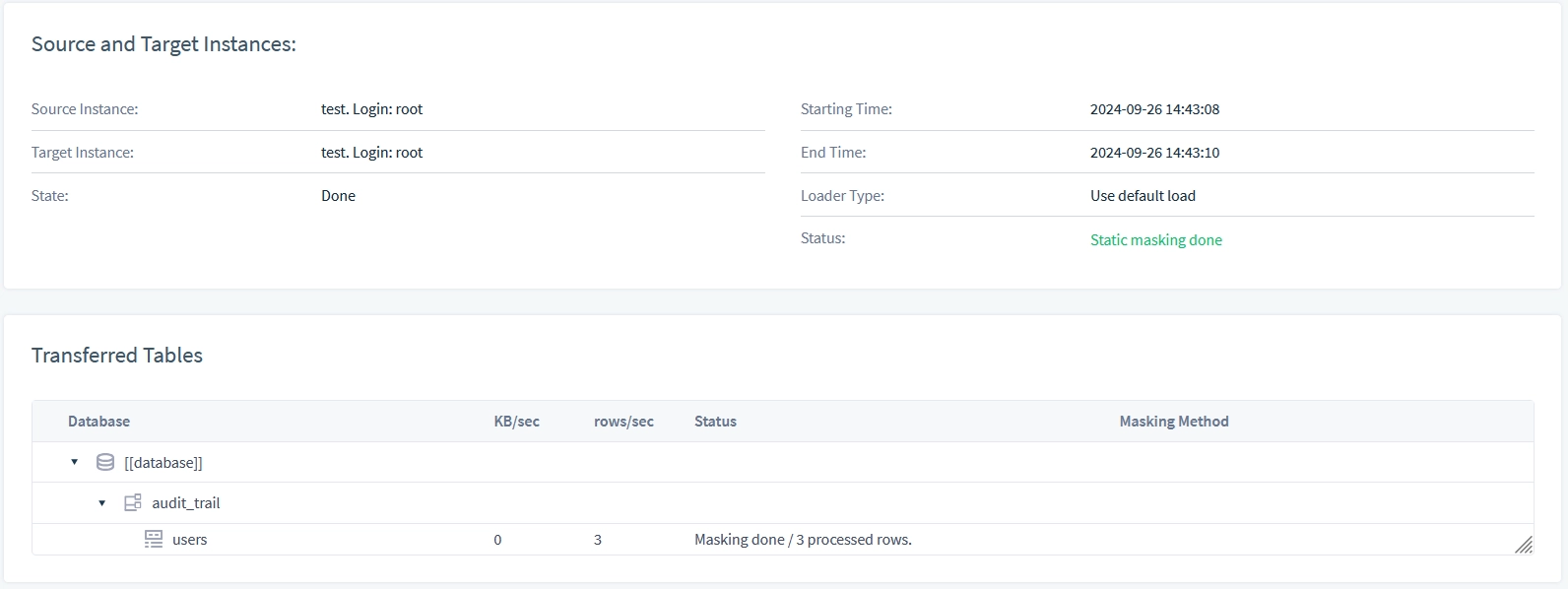
Static masking
Static masking results are available within DataSunrise in human-readable format.
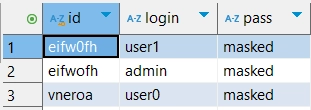
Dynamic masking
Dynamic masking changes data on the run and does not save results anywhere. You can see the results in the database.
Conclusion
Data masking is crucial for protecting sensitive information in MySQL databases. While native MySQL functions provide a basic way to mask data, they lack advanced features. Plug-ins and enterprise solutions offer more sophisticated methods but can be complex to manage.
DataSunrise, however, stands out for its user-friendly approach and dynamic masking capabilities. It provides a robust solution that fits various business needs, making it an excellent choice for securing MySQL databases.
DataSunrise offers flexible tools for database security, including audit, masking, and data discovery. Its user-friendly platform ensures that data masking is both easy to implement and highly effective. You can visit our website to schedule an online demo with our specialists and see DataSunrise in action.
When you invest in DataSunrise, you gain a powerful ally in data security that protects your MySQL databases while allowing access to those who need it.
