
Database Activity History

Introduction
Database activity history serves as a crucial resource for identifying and preventing security threats. By tracking and analyzing patterns of data access and usage, organizations can detect suspicious activities early, safeguarding sensitive information.
Keeping track of database activity is crucial for maintaining security, compliance, and operational efficiency. Database activity history provides a detailed record of all actions performed within a database system. This valuable information helps organizations monitor user behavior, detect unauthorized access, and troubleshoot issues.
Data from insider threat incidents reveals that organizations successfully mitigated 68% of potential risks through proactive measures. These measures included targeted security awareness training programs and strategic updates to corporate policies.
Understanding Database Activity History
Database activity history is a log of all operations performed on a database, including:
- Data modifications (inserts, updates, deletes)
- Schema changes
- User logins and logouts
- Query executions
- Access attempts
Database Activity History plays a crucial role in several key areas. Security audits are important. They provide detailed logs that help find potential weaknesses.
These logs also track unauthorized access. This ensures the overall safety of sensitive data.
Additionally, it supports compliance requirements, as many regulations mandate the monitoring and retention of database activity to meet legal standards.
Beyond security, this history is invaluable for performance tuning, enabling administrators to analyze database behavior and optimize operations. It also facilitates troubleshooting by offering insights into database issues, helping to identify and resolve performance bottlenecks or errors efficiently.
Native Tools for Database Activity Monitoring
Most database management systems (DBMS) have tools to track activity history. These tools help administrators monitor user actions, data changes, and system events. These native solutions provide basic functionality, such as logging access times, tracking modifications, and flagging errors.
While these tools are good for regular monitoring, they may not have advanced features. They might lack real-time alerts, detailed analytics, or customizable reports.
As a result, organizations often find that these built-in tools do not meet their complex security needs. They also struggle with performance tuning and following regulatory rules. For more comprehensive insights, many turn to third-party solutions that offer enhanced capabilities tailored to specific business needs.
PostgreSQL Example
PostgreSQL, a popular open-source DBMS, includes native logging capabilities. Logs are stored by default in the data folder (Windows):
C:\Program Files\PostgreSQL\14\data\log
For Ubuntu Linux and PostgreSQL 16:
/var/log/postgresq/postgresql-16-main.log
Here’s a simple example of what database activity history might look like:
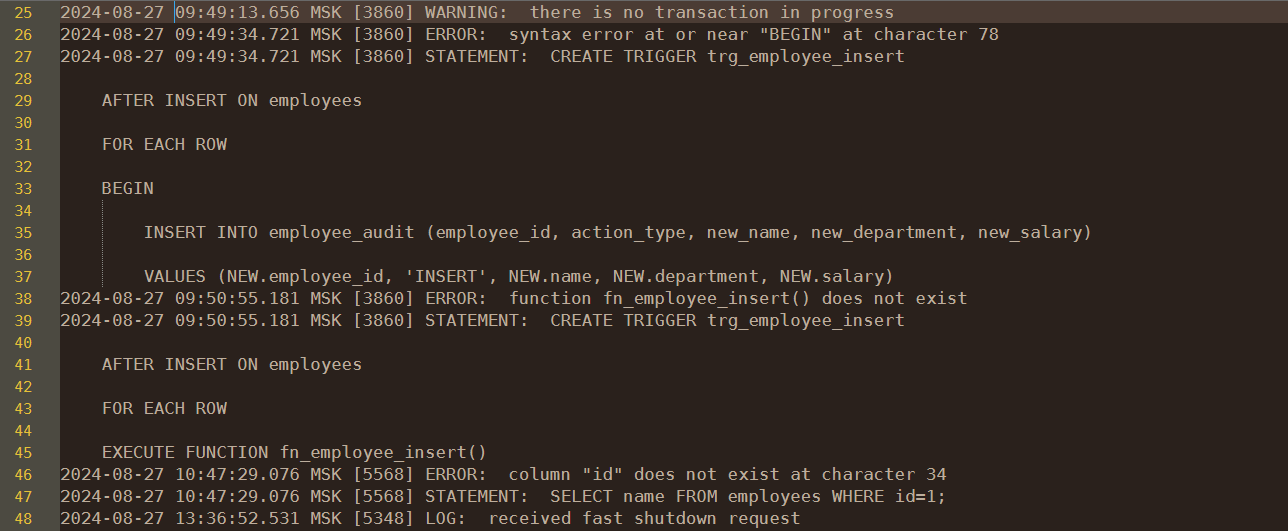
The picture illustrates the error message when the DB user tries to create a trigger.
Find more on PostgreSQL audit in our dedicated article.
Third-Party Tools: Enhancing Database Activity Monitoring
While native tools are useful, third-party solutions like DataSunrise offer more comprehensive features for managing database activity history.
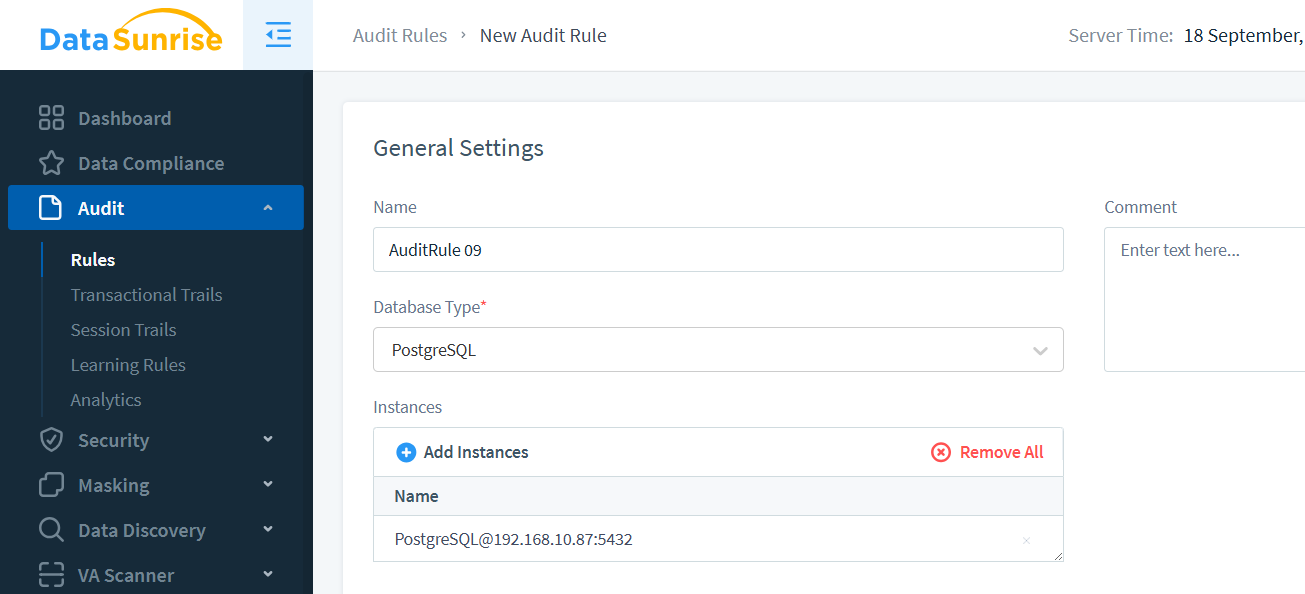
Creating a DataSunrise Instance and Viewing Audit Trails
Assuming DataSunrise is already installed, here’s how to create an instance and view audit trails:
- Log in to the DataSunrise dashboard
- Navigate to “Instances” and click “+ Add New Database”
- Configure the instance settings (database type, connection details, etc.)
- Save the instance configuration
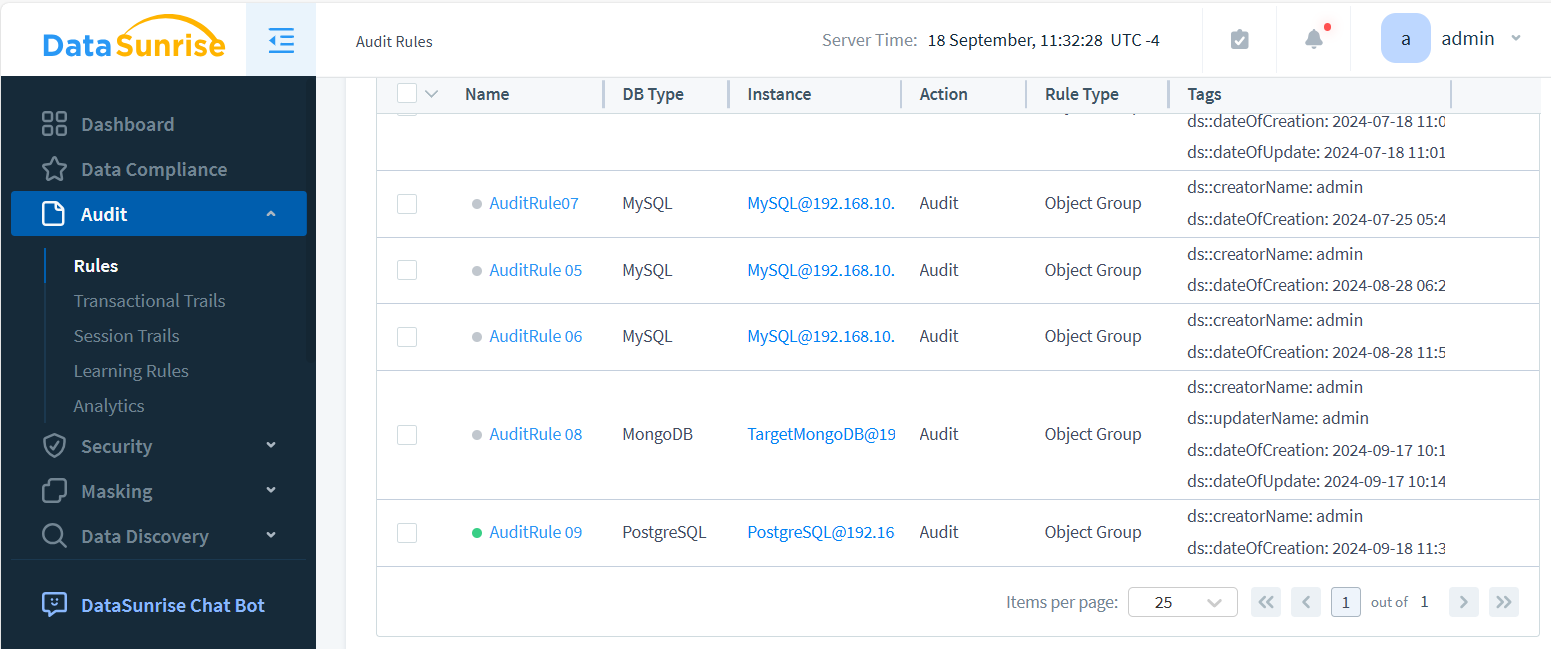
- Go to “Audit” section in the main menu. Create Rule and activate it.
The Audit Rules page lists all the rules.
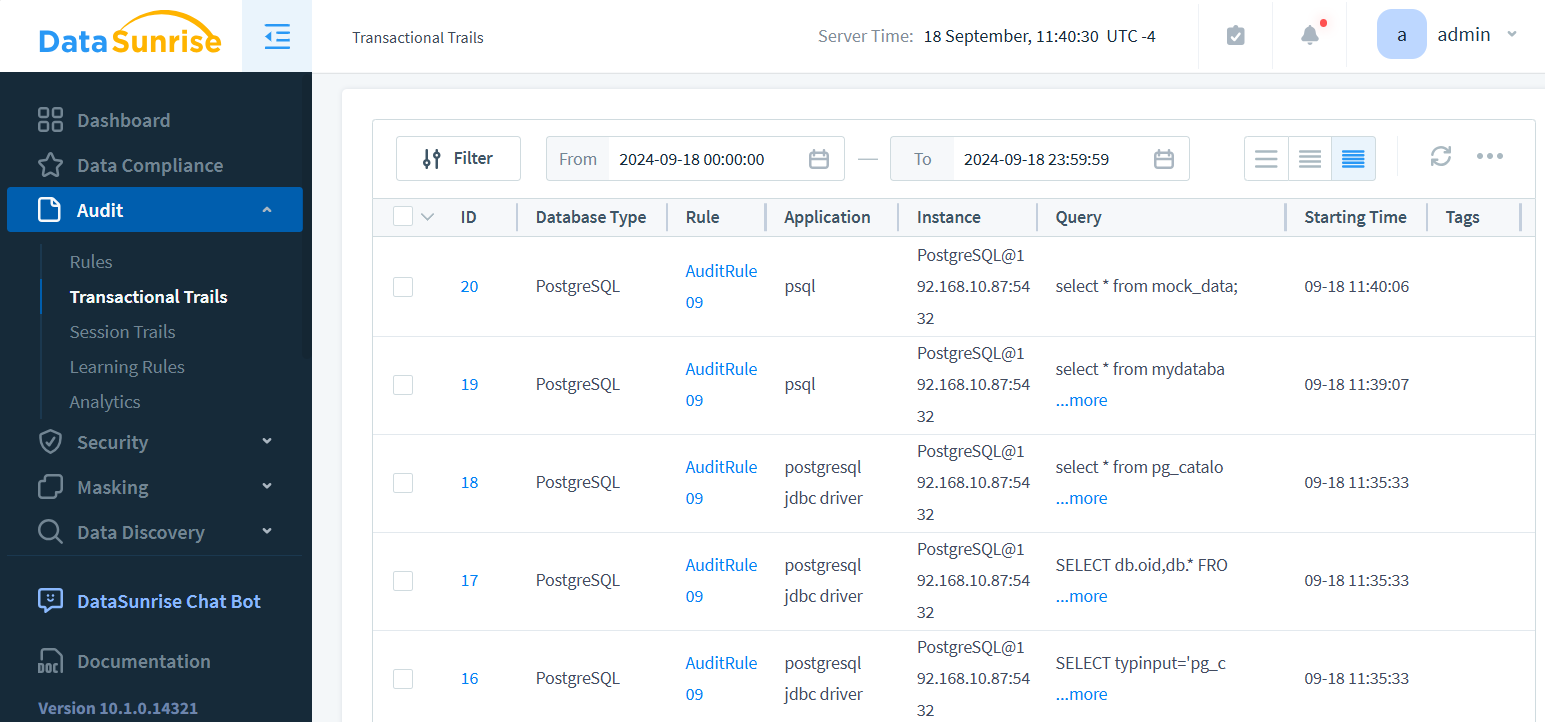
- Select the desired instance and time range.
- View the detailed audit trail, including SQL queries, user actions, and more in Transactional Trails:
Benefits of Using DataSunrise for Database Activity History
DataSunrise offers several advantages for managing database activity history:
- Centralized control: Manage audit rules for multiple databases from a single interface
- Uniform approach: Consistent monitoring across various database types and environments
- Advanced filtering: Easily search and analyze specific activities or patterns
- Real-time alerts: Get notified of suspicious actions immediately
- Compliance reporting: Generate reports for regulatory requirements like GDPR or HIPAA
Cloud and On-Premises Support
One of DataSunrise’s main features is its ability to track data activity history in a consistent way. This works for databases in the cloud or on-premises. This flexibility allows organizations to maintain consistent security and compliance standards across their entire data infrastructure.
Importance of Database Activity History in Data Management
Effective data management relies heavily on understanding and controlling database activities. By leveraging database activity history, organizations can:
- Enhance sensitive data security. To enhance sensitive data security, organizations must implement robust monitoring systems that track all database activity and immediately flag unauthorized access or suspicious behavior. By keeping a detailed log of database interactions, organizations can improve their defenses. This helps reduce the risk of data breaches. Ultimately, it protects sensitive information from both outside and inside threats.
- Improve overall data management practices. Regularly analyzing database activity improves overall data management practices by streamlining data storage, retrieval, and archiving processes. By understanding how data is used and improving workflows, organizations can manage their data better. This reduces redundancy and keeps data accurate, current, and easy to access.
- Ensuring regulatory compliance is critical for avoiding hefty fines and legal repercussions. Keeping a detailed record of database activities helps organizations follow legal rules and industry standards. This includes laws like GDPR and HIPAA. It shows that someone manages data according to set guidelines and best practices.
- Optimizing database performance requires continuous monitoring of activity to identify and address inefficiencies. By tracking queries, resource use, and response times, database administrators can improve operations. This helps reduce delays and keeps the system running well. As a result, both user experience and productivity increase.
- Detecting and preventing insider threats is crucial to maintaining the security of a database. By watching database activity for strange patterns or unauthorized access, organizations can find possible insider threats or mistakes. This helps prevent data leaks and ensures that only authorized people handle sensitive information.
Conclusion
Database activity history is an essential component of modern data management and security strategies. While native tools provide basic functionality, third-party solutions like DataSunrise offer more comprehensive features for monitoring, analyzing, and securing database activities. By implementing robust activity tracking, organizations can better protect their sensitive data, ensure compliance, and maintain optimal database performance.
DataSunrise provides easy-to-use tools for database security. These tools include advanced audit and masking features. They work for both cloud and on-premise storage solutions.
The suite includes AI-based parts and AI-governance features. These can hide sensitive data in or out of Large Language Models (LLMs). To see these powerful features for yourself, we invite you to visit the DataSunrise website. There, you can take an online demo and learn how our solutions can improve your organization’s data security.
Next
