
Database Activity History in Greenplum

In today’s data-driven environment, maintaining detailed database activity history has become crucial for organizations using Greenplum Database. According to Check Point Research, organizations faced a 30% surge in cyber attacks in Q2 2024 compared to the previous year, marking the highest increase in two years. This concerning trend underscores the importance of implementing robust database activity monitoring.
Greenplum Database provides sophisticated tools for tracking and analyzing database activities through its comprehensive logging and monitoring infrastructure. By leveraging these capabilities effectively, organizations can maintain detailed records of database operations while ensuring both security and compliance efficiency.
Understanding Database Activity History in Greenplum
Core Components
Greenplum’s activity history system comprises several interconnected components:
- Server Log Files: Each database instance (coordinator and segments) maintains its own server log file with detailed activity records
- System Catalogs: Tables storing metadata about database objects and operations
- Statistics Collector: Process that aggregates activity data across all segments
- Performance Monitor: Tracks resource utilization and query execution metrics
Key Features of Activity History Tracking
The Greenplum activity history system captures various types of information:
- Query execution details and duration
- User authentication attempts
- Session connection information
- Resource utilization metrics
- System configuration changes
- Schema modification events
- Data manipulation operations
Implementing Activity History Tracking
Basic Configuration
To enable comprehensive activity history tracking in Greenplum, implement these essential settings:
-- Enable basic activity tracking
ALTER SYSTEM SET logging_collector = on;
ALTER SYSTEM SET log_destination = 'csvlog';
-- Configure logging parameters
ALTER SYSTEM SET log_statement = 'all';
ALTER SYSTEM SET log_min_duration_statement = 1000;
ALTER SYSTEM SET log_connections = on;
ALTER SYSTEM SET log_disconnections = on;
Advanced Configuration
For enhanced activity tracking capabilities:
-- Enable detailed query logging
ALTER SYSTEM SET log_error_verbosity = 'verbose';
ALTER SYSTEM SET log_line_prefix = '%t [%p]: [%l-1] user=%u,db=%d,app=%a,client=%h ';
-- Configure activity retention
ALTER SYSTEM SET log_rotation_age = '1d';
ALTER SYSTEM SET log_rotation_size = '100MB';
ALTER SYSTEM SET log_truncate_on_rotation = on;
Practical Implementation Examples
1. Monitoring Query Patterns
Track query execution patterns across the database:
SELECT usename,
date_trunc('hour', query_start) as query_hour,
count(*) as query_count,
avg(extract(epoch from (clock_timestamp() - query_start))) as avg_duration,
sum(case when state = 'active' then 1 else 0 end) as active_queries
FROM pg_stat_activity
WHERE datname = 'testdb'
AND query ILIKE '%public.clients%'
AND query_start >= current_timestamp - interval '24 hours'
GROUP BY usename, date_trunc('hour', query_start)
ORDER BY query_hour DESC;
Example output:
| usename | query_hour | query_count | avg_duration | active_queries |
|---|---|---|---|---|
| admin | 2024-02-13 15:00:00 | 245 | 12.5 | 3 |
| etl_user | 2024-02-13 15:00:00 | 1842 | 8.2 | 15 |
| analyst | 2024-02-13 14:00:00 | 523 | 5.4 | 8 |
| developer | 2024-02-13 14:00:00 | 128 | 3.2 | 2 |
2. Resource Utilization Analysis
Monitor system resource usage patterns:
SELECT datname,
usename,
client_addr,
state,
wait_event_type,
wait_event,
count(*) as session_count
FROM pg_stat_activity
WHERE state != 'idle'
AND datname = 'testdb'
AND query ILIKE '%public.clients%'
GROUP BY datname, usename, client_addr, state, wait_event_type, wait_event
ORDER BY session_count DESC;
Example output:
| datname | usename | client_addr | state | wait_event_type | wait_event | session_count |
|---|---|---|---|---|---|---|
| testdb | admin | 10.0.1.100 | active | Client | ClientRead | 12 |
| testdb | etl_user | 10.0.1.101 | active | IO | DataFileRead | 8 |
| testdb | analyst | 10.0.1.102 | active | Lock | relation | 5 |
| testdb | developer | 10.0.1.103 | active | Client | ClientWrite | 3 |
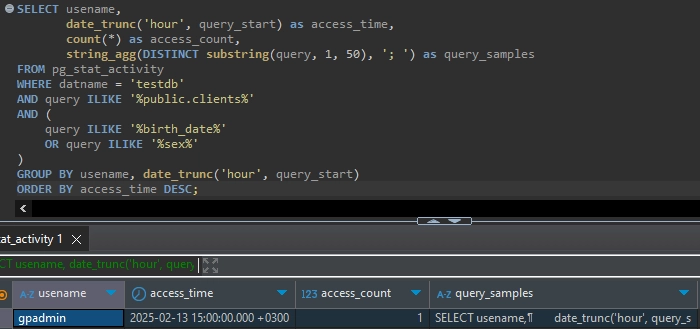
3. Sensitive Data Access Monitoring
Track access patterns for sensitive personal information:
SELECT usename,
date_trunc('hour', query_start) as access_time,
count(*) as access_count,
string_agg(DISTINCT substring(query, 1, 50), '; ') as query_samples
FROM pg_stat_activity
WHERE datname = 'testdb'
AND query ILIKE '%public.clients%'
AND (
query ILIKE '%birth_date%'
OR query ILIKE '%sex%'
)
GROUP BY usename, date_trunc('hour', query_start)
ORDER BY access_time DESC;
Example output:
Enhancing Activity History with DataSunrise
While Greenplum’s native activity tracking provides essential functionality, DataSunrise extends these capabilities through advanced security features and real-time monitoring tools.
Real-Time Activity Monitoring
DataSunrise provides immediate visibility into database operations through its monitoring interface. Security teams can track user sessions, query execution, and resource utilization as they occur.
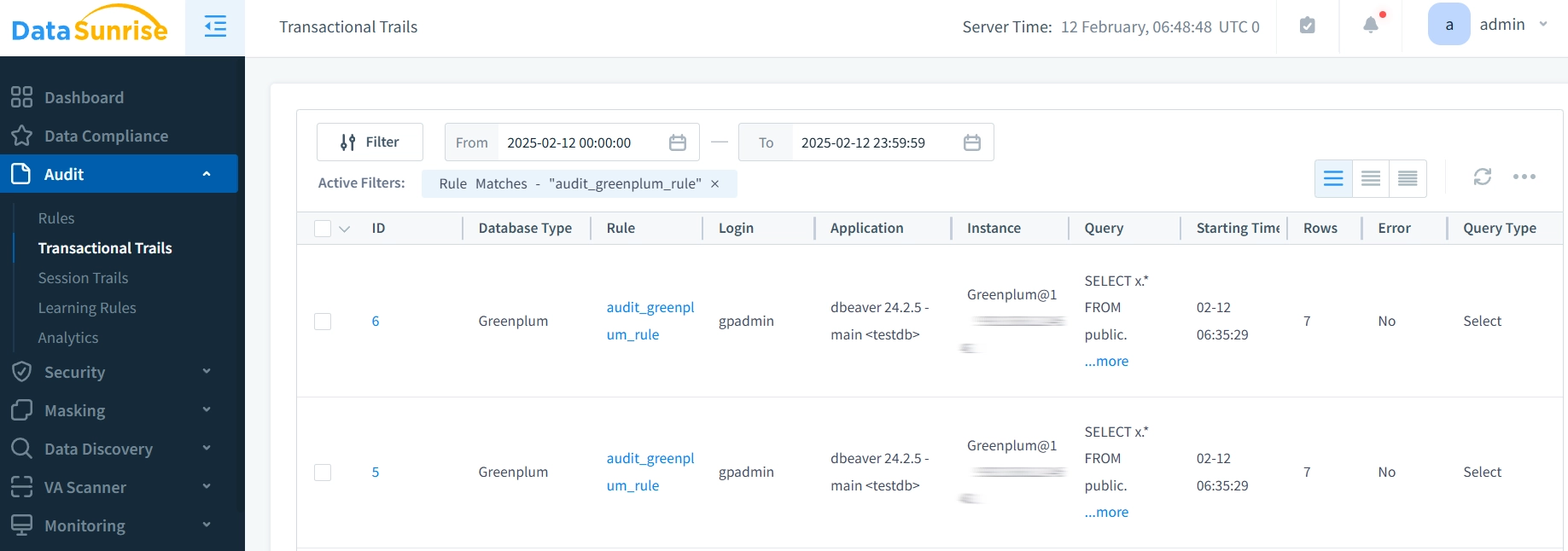
The platform allows administrators to set up custom monitoring rules for specific database objects or user activities:
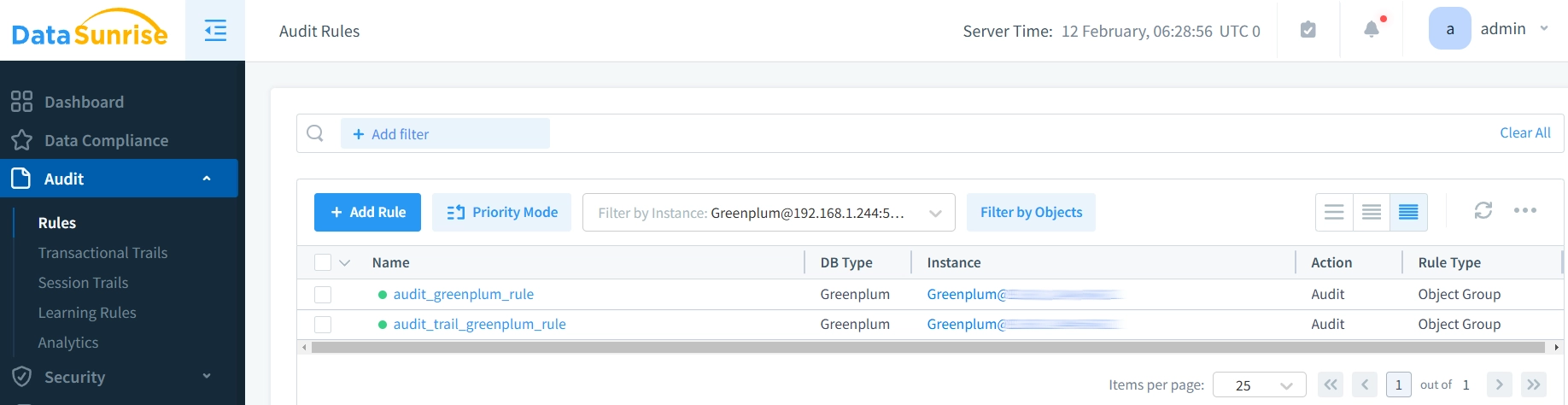
Key Features
- Pattern recognition and behavioral analysis for threat detection
- Automated compliance reporting and audit trail maintenance
- Fine-grained access control and query analysis
- Efficient log management with minimal performance impact
Through these capabilities, DataSunrise helps organizations maintain comprehensive activity tracking while balancing security requirements and system performance.
Best Practices for Activity History Management
Implement selective logging and monitoring to optimize system performance while maintaining comprehensive oversight. Focus logging efforts on business-critical operations and sensitive data access patterns, rather than tracking every database action. This targeted approach helps minimize performance impact while ensuring adequate coverage of essential activities. Configure appropriate log rotation policies and regularly archive older logs to manage storage efficiently.
Establish robust security controls for activity history data. Implement role-based access controls to ensure only authorized personnel can view and manage activity logs. Use encryption for sensitive activity data, particularly when storing personally identifiable information or other protected data types. Regular vulnerability assessment of the tracking infrastructure helps maintain the confidentiality and integrity of activity history data.
Deploy third-party solutions like DataSunrise to enhance native Greenplum capabilities. While Greenplum provides essential activity tracking features, specialized tools can offer advanced functionality such as real-time monitoring, automated threat detection, and streamlined compliance reporting. These solutions can significantly improve visibility into database operations and simplify security management tasks.
Define clear retention policies that align with regulatory requirements and business needs. Document retention schedules for different types of activity data and implement automated archiving processes. Consider industry-specific regulations and local data protection laws when establishing retention periods. Regular reviews of retention policies ensure continued compliance with evolving requirements.
Monitor system resource impact of activity history tracking. Regularly assess the performance overhead of logging and monitoring activities. Implement efficient archiving strategies to prevent performance degradation from excessive historical data accumulation. Use monitoring tools to track system metrics and adjust tracking parameters based on observed resource utilization patterns.
Conclusion
Effective database activity history management in Greenplum requires a balanced approach combining native capabilities with specialized tools. While Greenplum provides essential features for tracking database activities, organizations often need additional functionality to meet complex monitoring and compliance requirements.
By implementing comprehensive activity tracking strategies and leveraging advanced tools like DataSunrise, organizations can maintain detailed visibility into their database operations while ensuring security and compliance requirements are met.
For more information about enhancing your Greenplum database activity monitoring capabilities, visit DataSunrise website and schedule an online demo to see these features in action.
