
Enhancing Database Audit for Amazon Aurora with DataSunrise

Introduction
Database auditing is crucial for monitoring user behavior and maintaining compliance. This article explains the basics of Database Audit for Amazon Aurora. It discusses why many people choose third-party solutions and offers tips for setting up good logging practices.
In 2023, IBM’s Cost of Data Breach report revealed a startling statistic: only 33% of breaches were identified by internal security teams. This underscores the critical need for robust data protection measures.
DataSunrise offers a market-leading solution for safeguarding your data, whether on-premises or in the cloud. Its exceptional audit capabilities, coupled with a comprehensive suite of features, provide protection that extends well beyond basic auditing. DataSunrise empowers organizations to proactively defend against data breaches and maintain stringent security standards in today’s complex digital landscape.
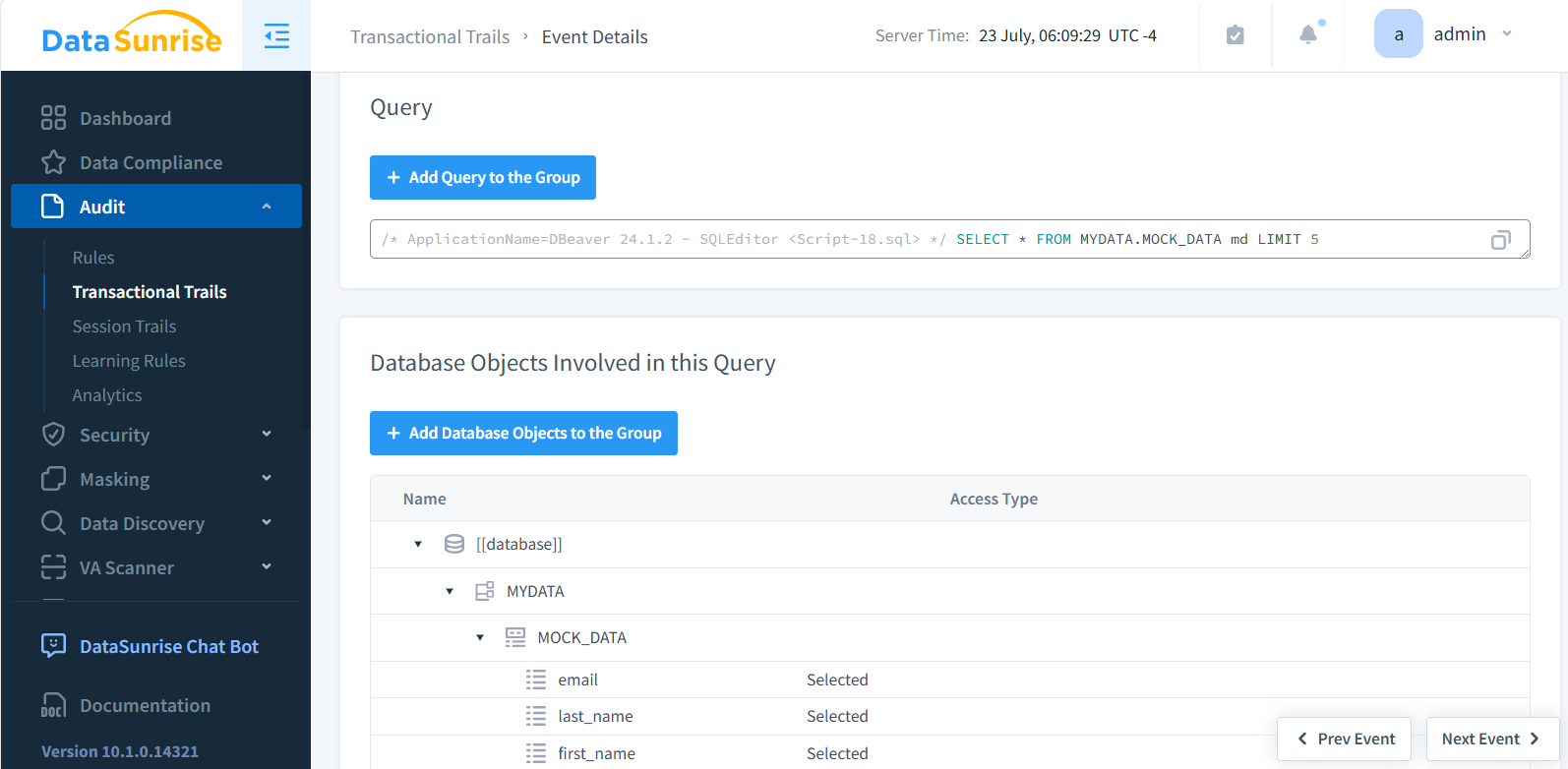
Understanding Database Audit for Amazon Aurora
Database auditing is the process of tracking and recording database activities. For Amazon Aurora, this involves monitoring user actions, query executions, and data modifications. By implementing robust auditing practices, organizations can:
- Detect suspicious activities. Auditing helps identify unusual patterns or unauthorized access attempts. This early detection is crucial for preventing data breaches and stopping malicious activities before they cause significant damage.
- Ensure regulatory compliance. Many industries are subject to strict data protection regulations like GDPR, HIPAA, or PCI DSS. Comprehensive auditing provides the necessary documentation to demonstrate compliance during audits and helps avoid costly penalties.
- Optimize database performance. By tracking query patterns and resource usage, auditing can highlight inefficient queries or processes. This information enables database administrators to fine-tune performance, leading to faster response times and better resource allocation.
- Improve overall security posture. Regular auditing helps identify security gaps and vulnerabilities. It provides insights into user behavior, access patterns, and potential insider threats. This knowledge allows organizations to strengthen their security measures proactively.
- Detailed audit logs are important for investigating security incidents. They help determine the cause, extent, and impact of a breach. This information is crucial for incident response and preventing future occurrences.
- Enhance data governance. Auditing supports better data management practices by providing visibility into who accesses what data and when. This transparency is essential for maintaining data integrity and enforcing data access policies.
- Track database usage trends to plan for future resource needs. Auditing data helps allocate resources and scale infrastructure effectively, ensuring the database can handle future demands efficiently.
- Implementing these auditing practices not only safeguards data but also provides valuable insights for improving overall database management and security strategies.
Why Third-Party Audit Solutions Are Preferred
While Amazon Aurora provides basic auditing capabilities, many organizations opt for third-party audit solutions. Here’s why:
Improved Compliance Management
Many industries face strict regulatory requirements. Third-party solutions typically address these challenges by offering a range of compliance-focused features. They often come with pre-configured compliance templates, which streamline the process of meeting specific industry standards.
These solutions can create reports for regulations such as GDPR and HIPAA. This saves time and reduces the risk of errors. They offer customizable audit trails for organizations.
This helps them adjust their logging and reporting. They can tailor it to meet their specific compliance requirements.
This helps companies follow rules better and show they are following them with more confidence and ease.
Centralized Management
For organizations using multiple database platforms, third-party tools offer significant advantages in managing complex environments. These solutions provide a unified interface for managing audits across different databases, eliminating the need to juggle multiple tools or interfaces.
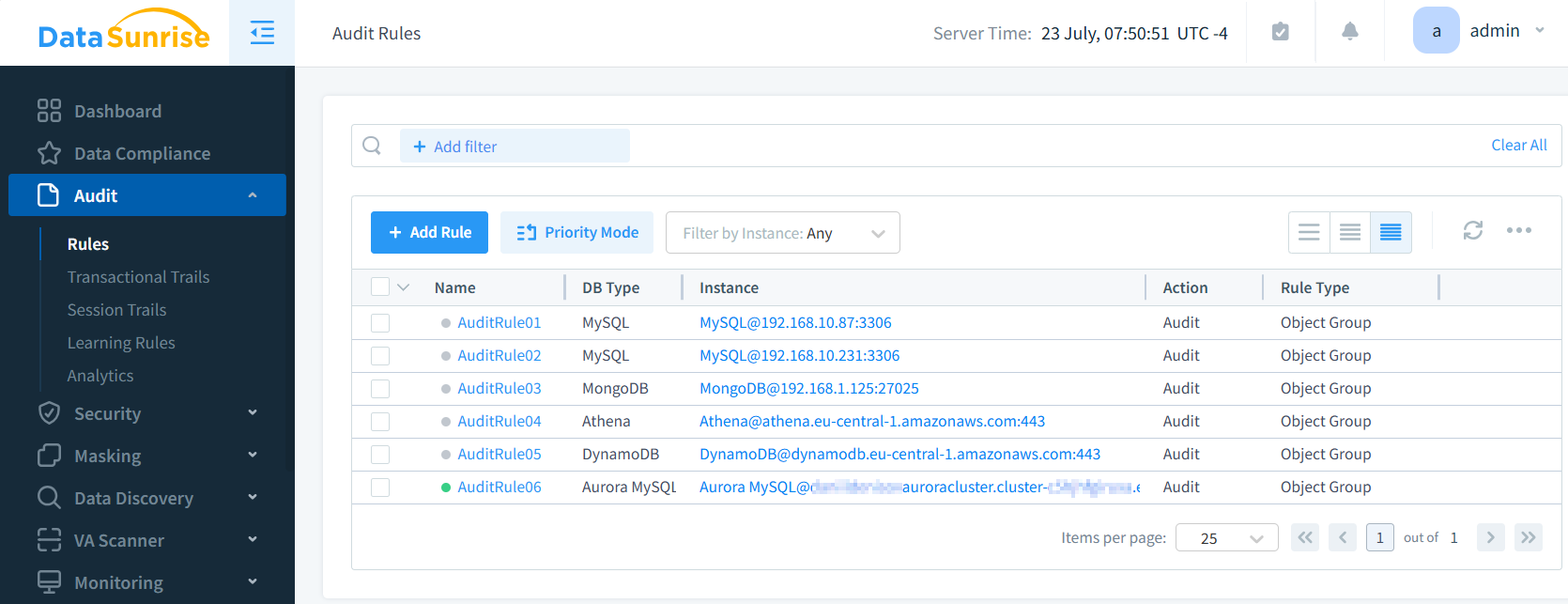
This centralized approach enables consistent policy implementation across various environments, ensuring uniform security and compliance standards regardless of the underlying database technology.
These tools help manage databases by combining tasks, streamlining workflows, and providing a central control point. This reduces administrative work and costs. This integrated approach not only enhances efficiency but also improves overall visibility and control across the organization’s entire database landscape.
Performance
Dedicated audit solutions are designed to handle large-scale environments without impacting database performance. Engineers design these specialized tools to efficiently manage the demands of extensive auditing processes.
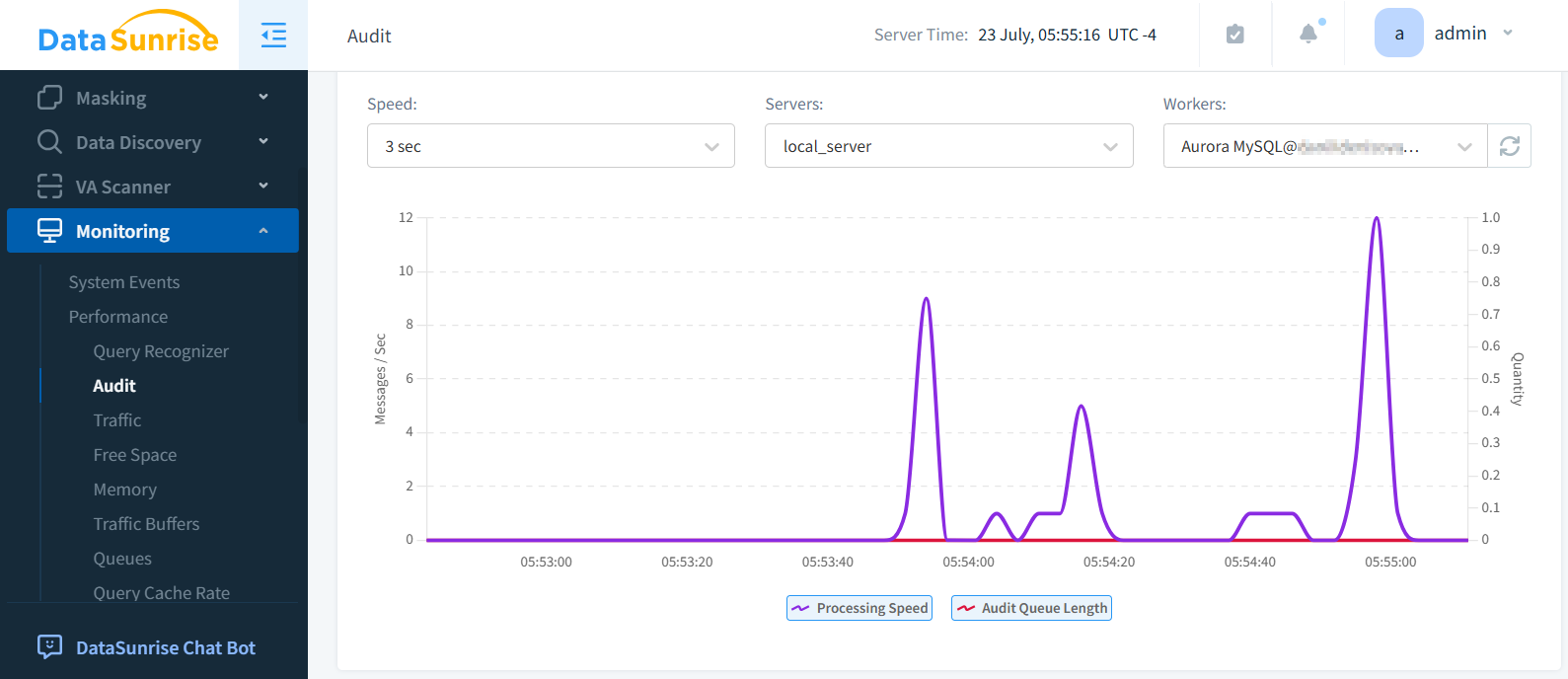
They often provide sophisticated log storage and analysis capabilities, allowing for rapid processing and retrieval of audit data without bogging down systems. Many solutions incorporate load balancing features, distributing the auditing workload across multiple nodes to prevent bottlenecks. Furthermore, these tools optimize to have minimal impact on database resources, ensuring that critical business operations continue unimpeded while comprehensive auditing takes place.
This combination of efficiency, scalability, and resource management makes dedicated audit solutions particularly valuable for organizations dealing with high-volume, performance-sensitive database environments.
Implementing Database Activity Monitoring
Effective database activity monitoring is crucial for maintaining security. Here are some best practices:
- Define clear audit objectives
- Implement granular logging policies
- Regularly review and analyze audit logs
- Establish automated alerting for suspicious activities
- Ensure proper log retention and archiving
Logging Queries in Amazon Aurora
| Built-in Approach | Pros | Cons |
|---|---|---|
| Performance Insights | – Monitors database load and performance – Captures frequently executed queries | – Doesn’t log all queries – Limited query details |
| Aurora Database Activity Streams | – Near real-time monitoring – Streams to AWS Kinesis | – Limited bind parameter capture – Requires additional processing |
| General Query Log | – Comprehensive query logging – Useful for debugging | – May impact performance – Not recommended for production |
| Slow Query Log | – Identifies performance issues – Logs queries exceeding time threshold | – Doesn’t capture all queries – Limited to slow queries only |
| CloudWatch Logs | – Centralized log management – Integrates with AWS services | – Requires additional setup – May incur additional costs |
| AWS CloudTrail | – Logs API calls – Useful for administrative auditing | – Doesn’t capture SQL queries – Limited to API-level actions |
While Aurora offers several query logging approaches, each has its limitations. Some require enabling paid features, while others demand expertise in AWS configuration. DataSunrise simplifies this process by providing comprehensive audit and monitoring capabilities in a single, user-friendly package.
Our solution offers:
- Centralized logging: Capture all query activities in one place (Transactional Trails or Session Trails)
- Intuitive web-based UI: Easy access to audit data and reports. Take advantage of our integrated LLM-based assistant for instant guidance on navigating the user interface or optimizing your audit workflow. This AI-powered tool is ready to help you maximize DataSunrise’s capabilities, ensuring a smooth and efficient auditing experience.
- Cost-effective: No need for multiple paid AWS features
- Seamless integration: Works effortlessly with your Aurora setup as well as with dozens of other data storage systems.
Challenges in Database Auditing
Despite its importance, database auditing comes with several significant challenges. Organizations must grapple with the potential performance impact on production databases, as comprehensive auditing can introduce additional processing overhead.
The storage requirements for audit logs can be substantial, especially for high-traffic databases, necessitating careful capacity planning. One challenge is analyzing a large amount of audit data. This task can be overwhelming without the proper tools and knowledge. DataSunrise leverages advanced machine learning through its Learning Rules and Suspicious User Behavior features, enhancing database security with intelligent, adaptive monitoring.
Additionally, organizations face the delicate task of balancing stringent security needs with privacy concerns, particularly in light of data protection regulations. Addressing these challenges often requires a combination of robust tools, well-defined processes, and skilled personnel.
Companies must invest in efficient auditing solutions, implement smart data retention policies, and employ advanced analytics to extract meaningful insights from audit data. Moreover, they need to develop clear guidelines that maintain security without compromising user privacy. Ultimately, successful database auditing demands a holistic approach that combines technology, strategy, and human expertise to navigate these complex issues effectively.
Conclusion
Database audit for Amazon Aurora is a critical component of a comprehensive security strategy. By using good auditing and the right tools, organizations can keep their data safe, follow rules, and keep their users’ trust. While native auditing capabilities provide a starting point, third-party solutions offer enhanced features and flexibility that many organizations find invaluable.
As data continues to grow in importance and volume, the need for robust database auditing will only increase. Be proactive about database security and consider advanced solutions to stay ahead of threats.
For a user-friendly and flexible solution to database security, including audit, masking, and data generation features, consider exploring DataSunrise. Visit our website for an online demo and discover how we can help enhance your database security posture.
